12
Safeguarding delicate pupil information was simple pre-technology. I needed to drop a file folder in a desk drawer, not overlook to lock it, and that was it. At the moment, safeguarding delicate information is a multi-million greenback enterprise that also manages to fall brief. Again then, defending information was the job of some devoted professionals. Now, it’s a world effort—governments, non-profits, firms, and other people like us. Knowledge Privateness Day, on January 28, calls us to guard private information. In ed tech, privateness is a day by day process. This present day warns us: the subsequent breach might begin with a phishing e mail you click on or a vendor you belief.
“Knowledge privateness isn’t only a checkbox—it’s a tradition.”
– Unknown
In gentle of current breaches just like the PowerSchool incident, which uncovered delicate pupil and dad or mum info, proactive measures should be taken. Please discover seven methods for Knowledge Privateness Day. Chances are you’ll really feel such efforts are inconsequential towards the worldwide backdrop of ransomware assaults, however they don’t seem to be. Take the time to safeguard your personal, your college students’ information privateness.
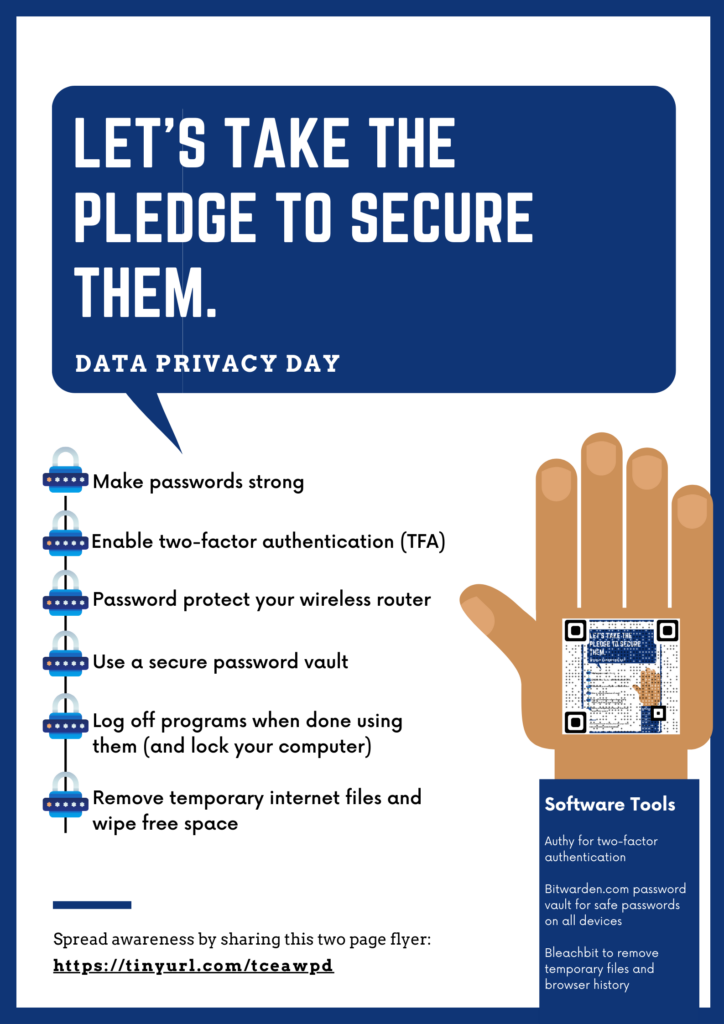
1. Begin with Consciousness
“You may’t defend what you don’t perceive.”
— Nuala O’Connor
At the moment, college students entry and share extra information than I did as a expertise director. The reason being that they’re maker and creators sharing info on social media, collaborating in DDOS assaults (as two highschool college students did in my expertise, knocking the community offline for a number of hours on take a look at day). With such informal entry to info, it’s vital to help college students in placing information privateness proper up there with substance abuse, bullying, and different felony acts. Clarify what private information is, why it’s priceless, and the way they will defend it.
- Classroom Exercise: Use real-world examples just like the PowerSchool breach to spark a category dialogue on dangers and tasks.

2. Educate College students to Acknowledge Phishing
“One of the best protection is a skeptic with a mouse.”
— Kevin Mitnick
I grew up as a Gen Xer studying tales of Kevin Mitnick and different hackers working to liberate info from company gatekeepers. At the moment, these hackers will not be liberators however blackmailers and extortioners. Their purpose with that little bit of ransomware is to compromise pupil information when they’re younger, promoting information and utilizing it inappropriately to earn cash. Phishing, suspicious hyperlinks, and attachments are a number of the methods into the walled fortresses faculty networks have develop into. If a pupil willingly helps an unknown stranger breach the fortress’s backdoor, all are in danger.
Present college students the right way to establish suspicious emails, hyperlinks, or attachments.
- Classroom Exercise: Conduct a “spot the phishing try” problem, presenting actual and pretend emails for college students to investigate.
You may discover a number of examples on this Google Doc. My favourite? This one:
| #7 | Unclaimed Bundle Supply | Topic: Motion Required: Unclaimed BundleFrom: Supply Service notification@fedx.com Expensive Buyer,We tried to ship your package deal however had been unsuccessful. Please click on the hyperlink beneath to reschedule supply:Reschedule SupplyIf not claimed inside 3 days, the package deal can be returned to sender.Regards,FedEx Supply Group | – Misspelled Area: ‘fedx.com’ as an alternative of ‘fedex.com’. – Phishing Hyperlink: Hover reveals suspicious URL. – Urgency: Risk of returning package deal. – Generic Greeting: ‘Expensive Buyer’ as an alternative of customized title. |
|---|

“Passwords are like underwear: don’t share them, don’t go away them mendacity round, and alter them typically.”
— Chris Pirillo
Our brains make horrible password managers. The times of three to 5 passwords is now not doable. At the moment, college students want to pay attention to safe password turbines and managers. For youthful college students, single sign-on options abound. For older college students, supply options like Keepass they will run on their system, or Bitwarden that works throughout units. My son relied on Keepass by means of highschool to maintain monitor of his passwords. Encourage college students to make use of distinctive, sturdy passwords.
Listed below are a few of my favourite password turbines:
A fast classroom exercise can get college students occupied with their passwords quite than counting on what’s handy.
Listed below are three different video games you’ll be able to attempt:
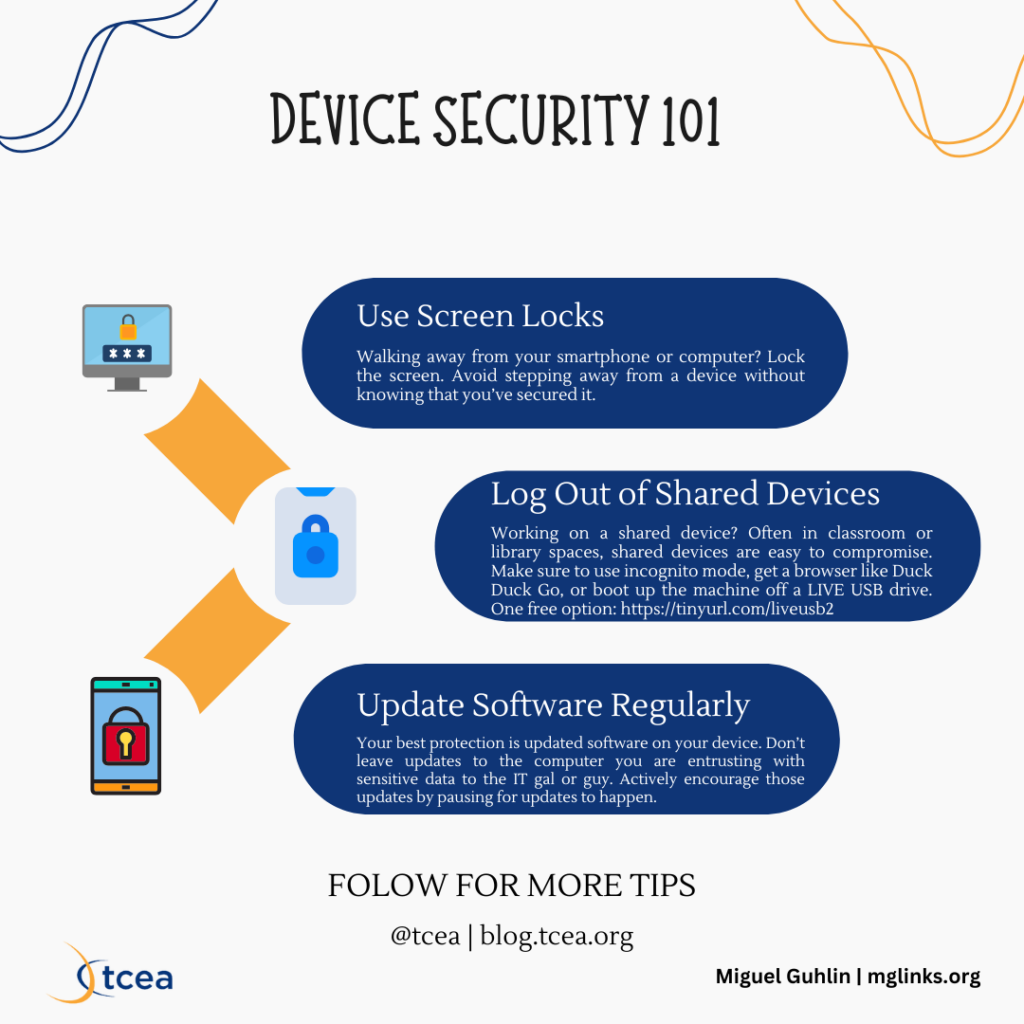
4. Safe Classroom Gadgets
“A safe system is a protected pupil.”
— Unknown
Talk about the significance of locking units and logging out of accounts. My very own kids safe their units earlier than they go away the room or stroll away from them. That behavior might have developed to stop snooping classmates or mother and father from sneaking a take a look at what they had been doing. It’s the equal of Boomers and Gen Xers locking doorways once they acquired right into a automotive or stepped right into a home. The one individuals who have issues with this? Nation of us who go away their doorways unlocked. A minimum of, that’s my metropolis mouse perspective. At the moment, securing units when not in use is vital. With theft of cellular units rampant, that digital lock with a high secret password, encrypted onerous drive, or smartphone app vault could also be all that stands between scandal, monetary destroy and also you questioning, “The place can I convert money to bitcoin?”
- Classroom Exercise: Function-play situations the place college students study what to do in the event that they discover an unlocked system.
5. Restrict Knowledge Assortment
“Much less is extra—particularly in relation to information.”
— Privateness Worldwide
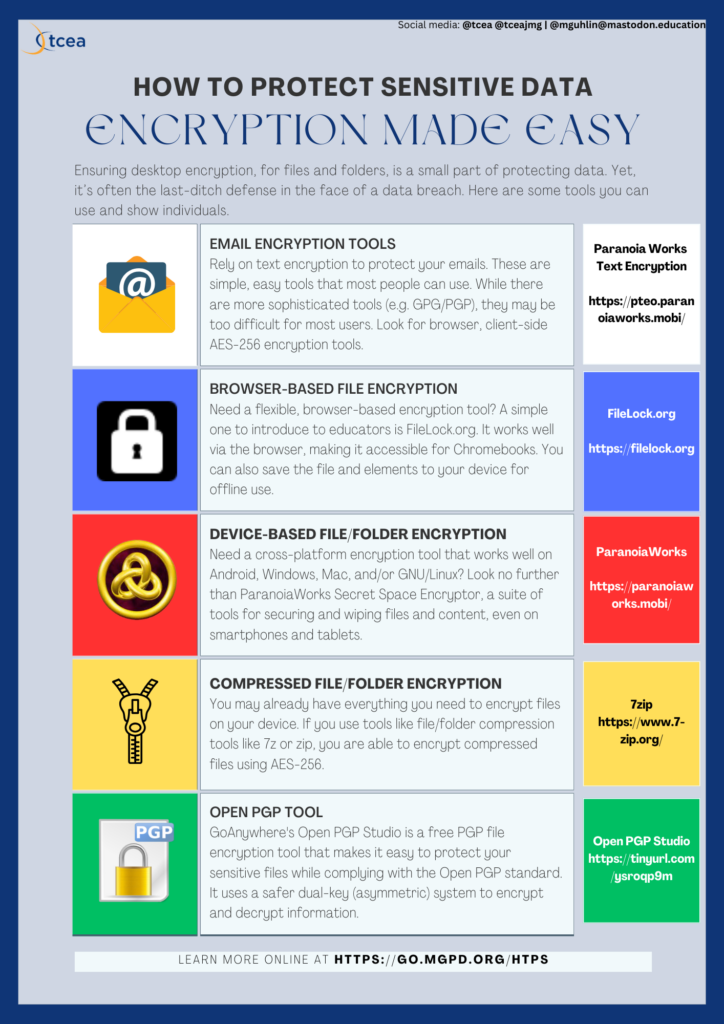
One option to restrict information assortment? Encrypt it. On this manner, you and your college students have to take the time to decrypt it. It’s a ache however can present that priceless second of readability while you ask your self, “Ought to I decrypt this? What am I actually going to make use of this for?” Some consumer oriented encryption instruments that each pupil and instructor must be utilizing:
- Paranoia Works Textual content Encryption. Safeguard any e mail correspondence or the contents of a textual content message or doc.
- FileLock. A simple to make use of, browser-based answer. Chromebook surroundings? No downside. Do this as a substitute.
- 7-zip. Presents file encryption throughout platform that’s AES-256. It could not cease a international energy, nevertheless it ought to work for run of the mill hackers.
Solely acquire information you want for studying. Educate college students to keep away from oversharing.
- Classroom Exercise: Have college students assessment permissions for apps they use and establish pointless requests.
Discover the Encryption Made Simple instruments:
“Knowledge privateness begins with good selections.”
— Knowledge Safety Fee
Anybody can verify to see if apps adjust to FERPA and COPPA. To perform that, use the TCEA PROTECT rubric. It’s obtainable as a paper evaluation (beneath), however it’s possible you’ll be higher off dropping that shiny new app’s privateness coverage and phrases of service into the TCEA PROTECT GPT to double-check.
- Classroom Exercise: Create a guidelines for evaluating apps’ privateness insurance policies together with your class.
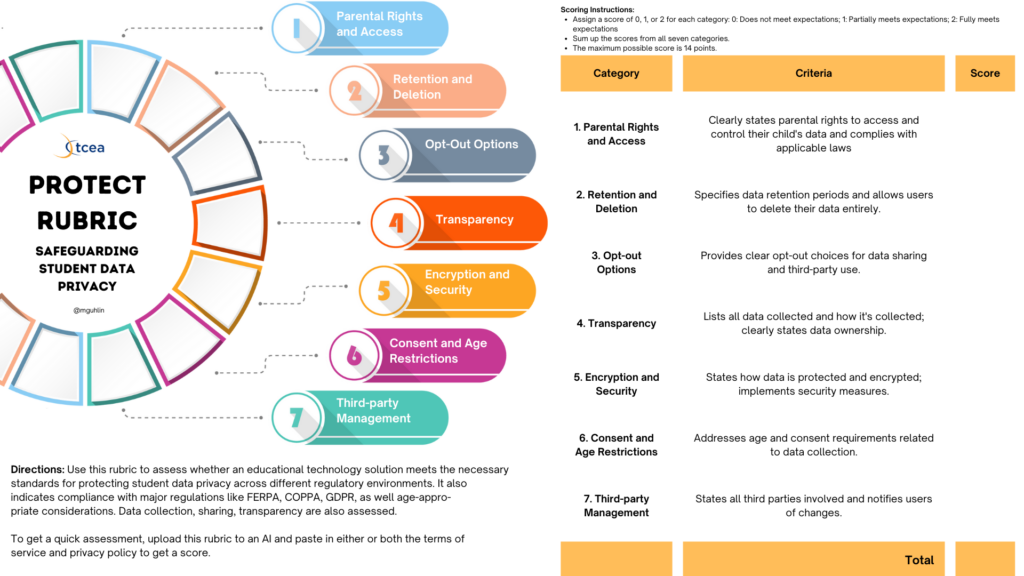
Give the AI model of TCEA PROTECT a whirl.
7. Interact Dad and mom in Privateness Practices
“It takes a village to guard a toddler’s digital footprint.”
— Widespread Sense Media
Host workshops to teach mother and father on defending kids’s information at dwelling. Many efforts at involving mother and father take a “Scared straight” strategy. Extra useful are actions that search to encourage mother and father to construct relationships that enable for sincere, genuine conversations with their kids. Having shared values that maintain all folks have dignity, can decide proper from flawed, the equality of all folks, and skeptical considering can go a protracted option to constructing these relationships. These values draw upon cultural, familial, and faith-based values widespread to a wide range of conditions. It by no means hurts to strengthen kindness to all, tolerance for many who consider and/or assume in a different way, too.
Think about these Knowledge Privateness Ideas for Dad and mom:
Construct a Privateness-First Tradition
Knowledge Privateness Day calls us to behave. Educate college students, employees, and fogeys to worth privateness. Use ideas and actions to guard information and construct lasting digital habits. At the moment shouldn’t be for reflection alone—take steps to safe the long run.
However Wait, There’s Extra!
In case your faculty suffers an information breach, take into account these 5 steps to coping with an information breach:
- Acknowledge the Incident Instantly and Share Insights. Upon discovering a breach, notify all stakeholders in regards to the subject. Elaborate on the steps being taken, utilizing clear, concise language to get the information on the market. Keep away from jargon which may confuse readers unfamiliar with the subject. You’ve realized quite a bit by means of this course of. To rebuild belief, be accountable, be clear about what has occurred, the place you failed, and what you’re doing to ensure it doesn’t occur once more.
- Include the Breach. Do your finest to restrict the injury to affected programs. You are able to do that by isolating them, disconnecting from the native or broad space community. Guarantee unauthorized entry is stopped.
- Conduct a forensic evaluation. You need to examine and discover out what occurred. Contain an exterior, third social gathering to assemble information and make suggestions.
- Notify and Help the Affected. Was instructor personally identifiable info uncovered? What about others, together with college students? Clarify what occurred, together with the dangers. Then, present sources to safeguard private info, together with credit score monitoring and id theft safety if needed.
- Reassess Your CyberSecurity Insurance policies. Reap the benefits of information minimization, implement safety audits, and decrease third social gathering vendor associate dangers.
These are a number of of the steps you’ll be able to take. TCEA can help you with district expertise audits. Request one at present through Lori Gracey (lgracey@tcea.org).



