Zero-day vulnerabilities symbolize an imminent menace to cybersecurity, and on this case, two such vulnerabilities, CVE-2023-38831 and CVE-2023-40477, have been recognized within the broadly utilized WinRAR software program. These vulnerabilities pose a grave concern on account of their potential for distant code execution, presenting a extreme menace danger.
WinRAR is a well-liked compression device with half a –billion customers worldwide and performs an integral function in numerous digital operations. This truth heightens the possible influence of those vulnerabilities, as any exploitation might severely have an effect on the digital panorama.
These vulnerabilities require person interplay for exploitation. Distant attackers, with malicious intent, can execute arbitrary code on methods the place WinRAR is put in. The software program’s performance, which incorporates archive creation in RAR or ZIP file codecs, shows and unpacks quite a few archive file codecs. This additional amplifies the potential for compromise as WinRAR’s skill to assist the creation of encrypted archives, multi-part information, and self-extraction provides to the complexity of the scenario. Moreover, file integrity is verified utilizing CRC32 or BLAKE2 checksums for every file inside an archive, highlighting the importance of those gaps within the system.
This advisory is our detailed evaluation and report of the above findings.
Why is Fast Motion Required towards theseAgainst These Vulnerabilities?
Customers utilizing WinRAR model older than 6.23 are in danger. These vulnerabilities permit customers to execute arbitrary code when trying to view a benign file in a ZIP archive. The problem happens when a ZIP archive might embody a benign file (akin to an unusual .JPG file), and a folder with the identical title because the benign file. The folder’s contents (which can embody executable content material) are processed whereas trying to entry solely the benign file.
This was the hole being exploited within the wild from April by way of August 2023 by menace actors. Breach makes an attempt have been made on on-line cryptocurrency buying and selling accounts by way of these vulnerabilities.
CVE-2023-40477 => Restoration Quantity, Improper Validation of Array Index: Distant Code Execution Vulnerability
Customers who open specifically crafted WinRAR archives on their units might fall prey to the assault. The downloading of such a specifically crafted archive and the opening of it on the person’s system is enough to permit attackers to execute arbitrary code on the gadget.
The problem, recognized as CVE-2023-40477, is a high-severity vulnerability that exists within the processing of restoration volumes. A buffer overflow is feasible when processing restoration quantity names within the previous RAR 3.0 format. To set off this vulnerability, the person should begin unpacking a RAR file in the identical folder as a restoration archive file with a malformed title.
The vulnerability exists within the processing of restoration volumes and outcomes from a scarcity of correct validation of user-supplied knowledge. This may result in reminiscence entry past the tip of an allotted buffer.
Software program utilizing WinRAR libraries was additionally affected
The libraries unrar.dll and unrar64.dl are susceptible. The libraries “unrar.dll” and “unrar64.dll” utilized by WinRAR are utilized in many software program merchandise (together with virus scanners). If previous variations of the libraries are used there, the vulnerabilities talked about above additionally exist there. And inIn the case of virus scanners, that is much more vital than with WinRAR since the anti-virus software program often runs with elevated privileges.
CVE-2023-38831 => File Extension Spoofing Vulnerability
On opening the archives, customers can’t differentiate the innocent information hiding the malicious payload.
Right here, we see a pdf file and a folder with the identical title.
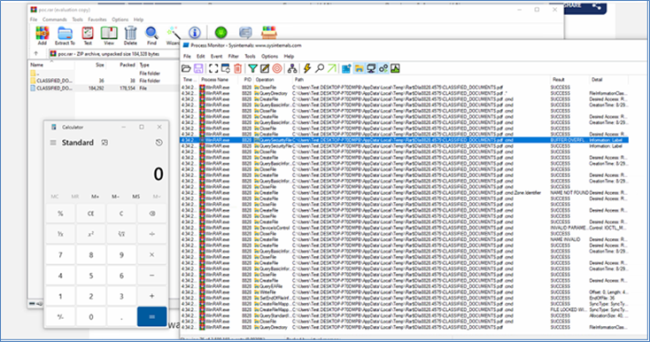
Determine 1: Opening the crafted archive outcomes whereas launching the calculator earlier than the precise pdf file is opened.
Nonetheless, when the person double-clicks on the PDF, the CVE-2023-38831 vulnerability will quietly launch a script within the folder to put in malware on the gadget (because the calculator is launched). On the similar time, these scripts may even load the decoy doc in order to not arouse suspicion.
The vulnerability is triggered by creating specifically crafted archives with a barely modified construction in comparison with protected information, which causes WinRAR’s ShellExecute perform to obtain an incorrect parameter when it makes an attempt to open the decoy file.
This ends in this system skipping the innocent file and as an alternative finding and executing a batch or CMD script, so whereas the person assumes they open a protected file, this system launches a distinct one.
An infection Chain:
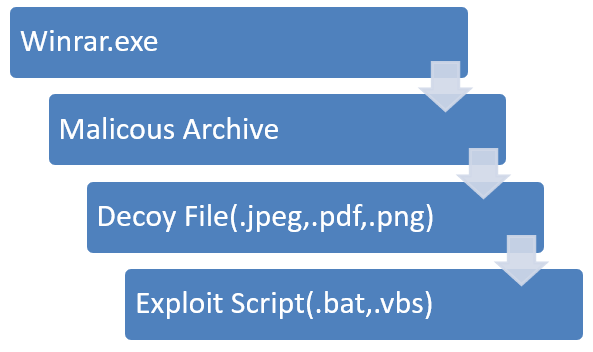
IOC:
| FileName | SHA-2 Hash |
| Trading_Strategy_2023.rar | 763df8b2db7f2f2fa0c8adb8c1cc05ff15b59e6a9756cbe9fc4a1c12329b62af |
| Cryptocurrencies2023_mpgh.internet.rar | 0860e09e529fc6ccbbffebafedc27497fbbcaff57b5376fb4cc732c331d1f591 |
| Screenshot_19_04_2023.rar | 18129626041b90558607eec67616ba6d2b1ea28a280c7ba5b2bd30ebb1e2438b |
| TSG_Strategies.rar | 5a387ee6d0dcbbf2cd97379c68d8e3398d01a920873ddd45ff21dbfccb19e2ee |
| New Settlement.rar | 0059121d725a818e453e29492e78762d0a87087fcb11e484cf5ad663c1eba2bc |
Mitigation
RARLAB launched WinRAR model 6.23 on August 2nd, 2023, and one other replace on August 24, 2023, successfully resolving CVE-2023-40477 and CVE-2023-38831. It’s suggested that WinRAR customers apply this safety patch with instant impact.
Launch notes: https://www.win-rar.com/singlenewsview.html?&L=0
This model additionally fixes one other vital subject associated to specifically crafted archives, which helps in incorrect file initialization whereas extracting specifically crafted archives.
Authors:
Adrip Mukherjee
Amruta Wagh



