On-line privateness is a rising concern amongst these browsing the web. When surveyed in Could of 2023, 81% of on-line customers mentioned they have been very involved about their on-line privateness and the way firms use their collected information.
With these rising considerations, on-line customers flip to totally different strategies of software program similar to proxy websites, alternate browsers or non-public networks. Selecting may be robust, so we created a information evaluating the professionals and cons of two of the most well-liked choices: Tor and VPN.
Bounce to:
What Is Tor?

Tor, brief for “The Onion Router,” is a non-profit group that researches and develops on-line privateness instruments. The Tor browser is a software that anybody can obtain for Linux, Mac, Home windows and cellular gadgets.
The Tor browser is primarily used to guard your id on-line. It routes your web connection by means of a sequence of servers and encrypts it, making it troublesome for anybody to hint the place your information is coming from or establish you. Tor additionally protects your on-line privateness by stopping web sites and companies from monitoring your IP handle and placement, making it much less seemingly for advertisers and information brokers to trace details about your on-line conduct whereas utilizing Tor.
Benefits of Tor
Tor stands other than different on-line privateness options as a free and easy-to-use possibility. Different benefits embrace:
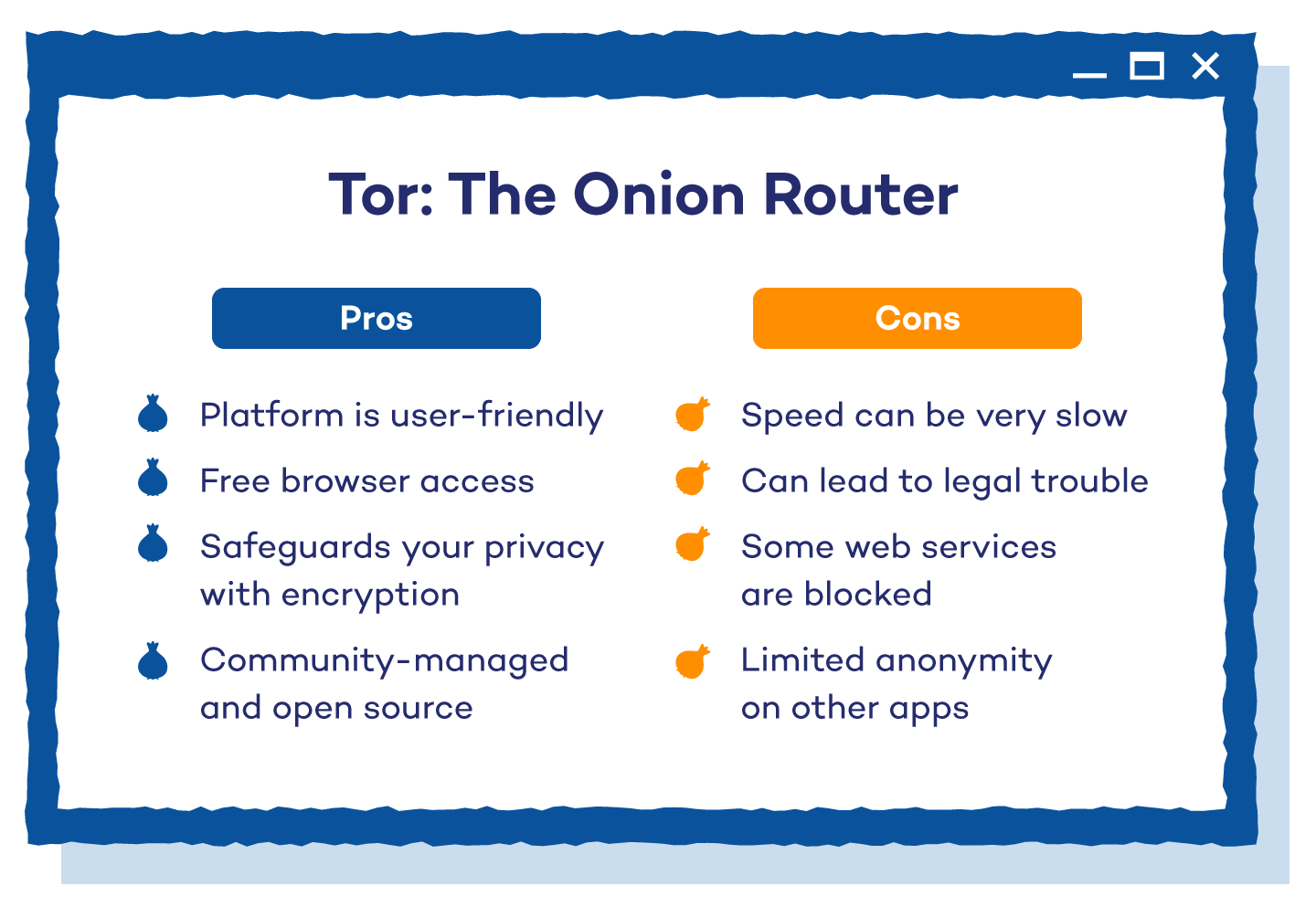
- Person-Pleasant: The Tor browser is just like most browsers you’ve used earlier than. It’s accessible to many individuals and is user-friendly, making it simple to make use of.
- It’s Free: The Tor browser is free to obtain and use. Extra superior customers are additionally capable of obtain the open-source venture and make modifications to the coding as they’d like.
- Safeguard Your Privateness: Tor protects your privateness by not revealing your IP handle to the web sites you go to. Anybody from journalists and political rebels to your common Joe can use this platform to maintain their info secure from repressive governments or large companies.
- Neighborhood and open supply: Tor gives transparency that facilitates peer evaluate and helps hold the community safe. It is because it’s a community-managed browser — the servers it makes use of to route your connection are all volunteer-operated. It’s additionally open-source, which means its authentic code is accessible for everybody to entry and modify. This implies Tor could be very simple to work with, customise and study on a technical degree.
- Appropriate: You need to use Tor with different internet browsers and functions like prompt messaging, WeeChat, Thunderbird and Mumble, to call just a few. This versatility uniquely positions it as a product that a variety of customers can profit from.
- Nameless: Along with your information visitors routed by means of a number of servers, you’ll be very arduous to trace, establish and purchase info from. The layer of encryption Tor provides makes its customers nameless web dwellers.
 Disadvantages of Tor
Disadvantages of Tor
Whereas it’s an revolutionary answer for on-line safety, Tor nonetheless has some shortcomings to think about:
- Sluggish pace: Since visitors goes by means of so many relays, there may be typically a delay in content material. Particularly, pictures and movies have hassle loading. The extra customers who aren’t internet hosting a relay, the slower it turns into.
- Net companies blocked: Many bigger internet companies block entry to Tor. When visited, these websites return an error message like a 404. Others enable entry however embrace a maze of CAPTCHAs which can be wanted to enter the positioning.
- Authorized hassle: The Tor browser can be utilized by anybody. If somebody is collaborating in criminality and also you’re the exit relay, the visitors shall be tracked to you. Governments are additionally very cautious of Tor customers and hold a detailed eye on them. Just by being a Tor person, you may be marked as a prison and have all of your actions monitored.
- Restricted anonymity with non-Tor visitors: Whereas very efficient at sustaining anonymity for its personal visitors, Tor doesn’t have an effect on different functions that aren’t configured to make use of it. Your exercise on non-Tor visitors, similar to utilizing totally different apps and browsers that aren’t configured, gained’t be as safe or nameless and will create a “leakage” of knowledge. The configuration course of may be complicated, which is why it’s vital to observe the Torification information rigorously.
Configuring sure functions to work with Tor means your on-line exercise on that app will profit from the identical anonymity and privateness. Functions that aren’t configured to work with Tor don’t profit from its privateness options.
How Tor Works
The Tor browser is ready to disguise your id on-line by transferring your visitors throughout totally different Tor servers. As your visitors runs by means of these different pc servers, the info is encrypted in order that no person will have the ability to monitor your actions.
Tor has layers of privateness just like the layers of an onion, therefore its title. The extra Tor customers that make the most of these servers, the extra hidden your visitors turns into. These layers of safety are created by a maze of center relays, finish relays and bridges.
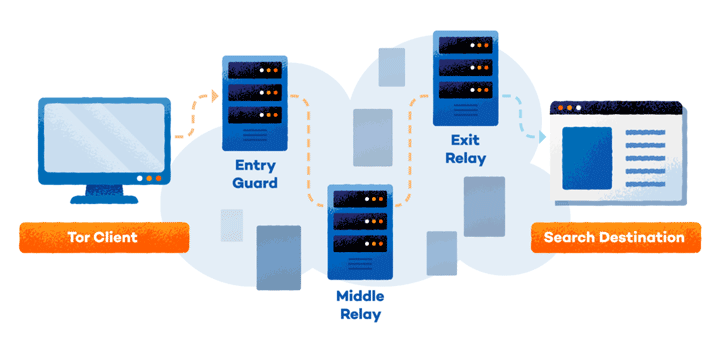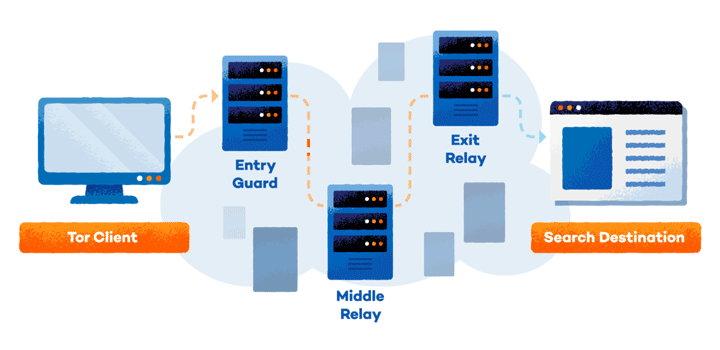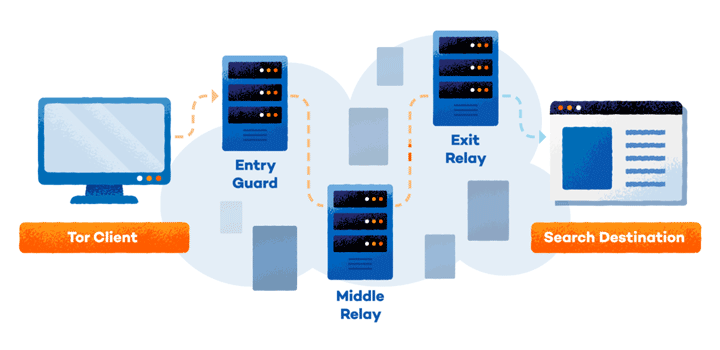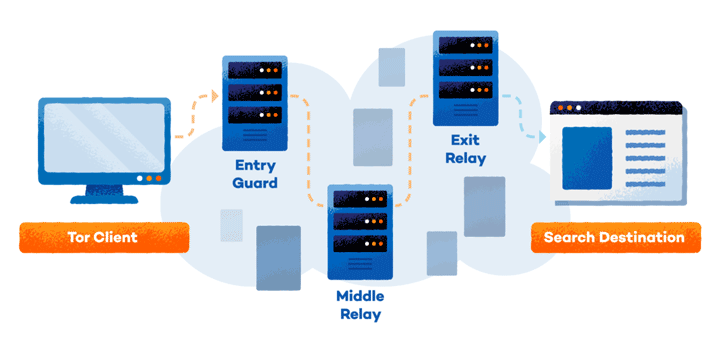
Center relays are routers that deal with the visitors alongside the best way and may be created by anybody at dwelling. Finish relays are the ultimate relay within the chain and that is the IP handle or numerical identification your connection will look like coming from. The hosts of those are liable to targets by police and copyright holders if there may be any criminality detected. Bridges are Tor routers that aren’t publicly listed and are shielded by IP blockers. These make encryption attainable, even in nations that frequently block all publicly listed Tor relays.
Every relay solely is aware of the IP handle of the router earlier than it. As your visitors passes by means of the relay, your authentic IP handle is misplaced and the tip relay replaces it.
Not everybody who makes use of Tor has to run a relay, however the software program relies on a neighborhood of individuals which can be keen to. The extra relays which can be working, the sooner the browser will work and the safer it is going to be.
What Is a VPN?

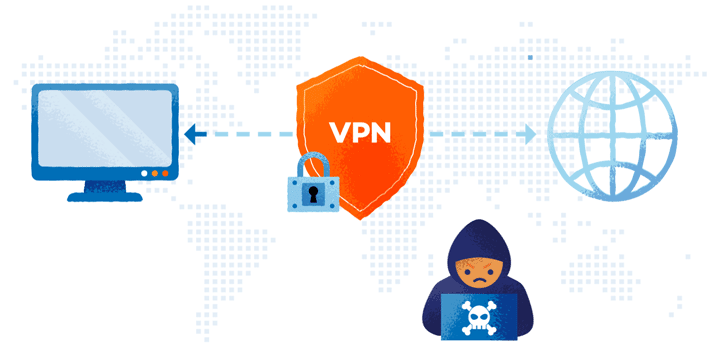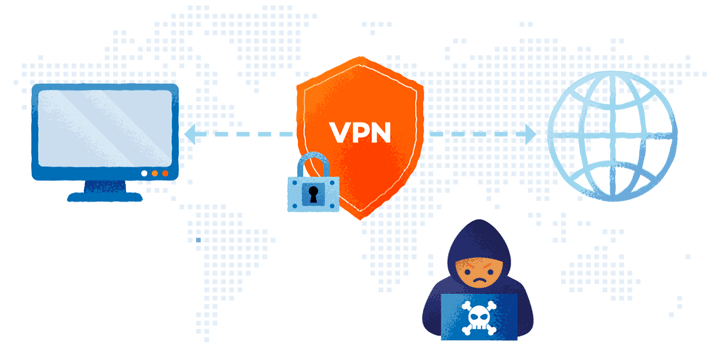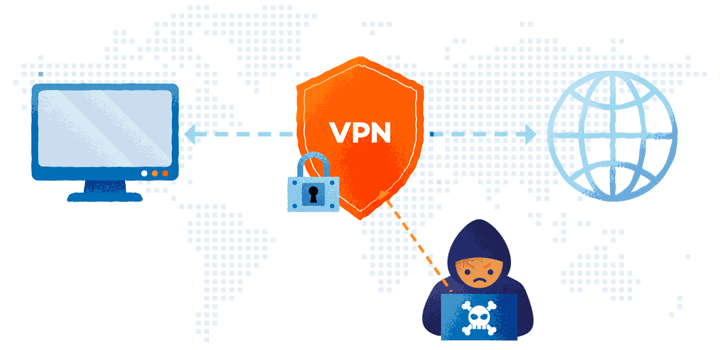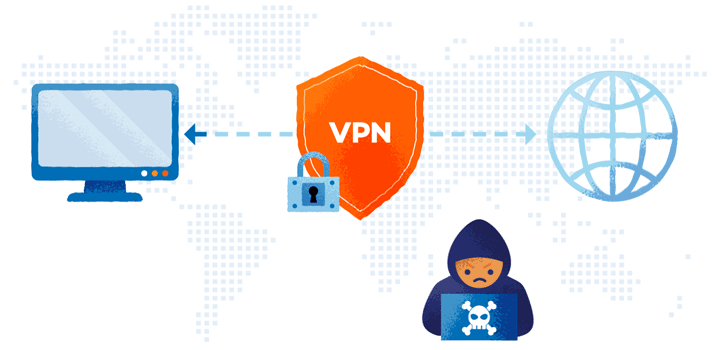
A VPN, brief for Digital Personal Community, is software program that is ready to change your IP handle and encrypt your Web visitors. Initially, a majority of VPNs have been used at companies, permitting all staff of the enterprise community to privately entry delicate info. It has now developed to maintain a person’s on-line exercise non-public from hackers, authorities censorship and every other risks lurking on the Web.
Benefits of a VPN
VPNs supply a set of benefits that make them distinctive and have set them aside as one of many main choices for on-line safety and anonymity.
- Velocity: Because you’re solely connecting to 1 server, the web connection is simply as quick as you’re used to. You don’t normally have to attend any extra time for pictures or movies to load.
- Accessibility: Irrespective of your geographical location, you’ve full entry to the web. Even when a website or service is blocked or modified in your nation, you possibly can connect with the model that others see in different nations.
- Management of IP handle: A VPN protects the way you’re seen on-line. Gadgets are recognized with an Web Protocol (IP) handle that tells their system kind, location and on-line exercise. By controlling your IP handle, you make it tougher for folks to establish you.
- Encryption: In contrast to Tor, which solely encrypts requests whereas utilizing the browser, VPNs are capable of encrypt all of the visitors coming out of your pc. This makes them safer.
- Safety towards ISP throttling: Some ISPs (web service suppliers) throttle or restrict web speeds and bandwidth for particular on-line actions like streaming. A VPN can bypass these limitations and enhance your on-line expertise.
- Versatility: VPNs are versatile sufficient to be utilized on a community degree, making them usable with totally different gadgets starting from computer systems and smartphones to tablets and routers. Some VPNs additionally present browser extensions and devoted platform apps for extra customization.
 Disadvantages of a VPN
Disadvantages of a VPN
Regardless of its many benefits and large person base, VPN nonetheless has just a few shortcomings that it is best to think about.
- Software program failures: For a VPN to work, it must run correctly. VPN leaks are widespread if the software program isn’t put in and examined correctly.
- Prices cash: Whereas some VPNs have free choices, the safer variations price cash. There’s normally a month-to-month charge to maintain your exercise safe.
- VPN supplier can see your exercise: Some VPN firms log your historical past whereas utilizing their service. Search for an announcement in your VPN’s web site to make sure they aren’t gathering, storing or sharing any everlasting identifiers of you.
How a VPN Works
A VPN has a community of servers positioned everywhere in the world. When your Web request is made, it goes by means of one of many VPN servers earlier than reaching the Web. When it passes by means of this alternate server, your IP handle is modified. Not solely does this shield your id, however your system will appear as if it’s in a unique place, permitting you to securely entry the native community’s sources.
For example, if you happen to’re visiting China and wish to entry Fb, you gained’t have the ability to by means of their Web connection as a result of the positioning is banned by the Chinese language authorities. Nonetheless, utilizing a VPN that connects your system to an Web server in a rustic the place Fb is allowed will allow you to entry the positioning in China.
Tor vs. VPN: Which Is Higher?
Whereas each Tor and VPNs work to guard your on-line anonymity, VPNs are probably the most safe selection if used correctly. Tor is a free browser that may encrypt your requests, however it’s gradual, doesn’t have entry to all websites and might result in authorized hassle. In the meantime, VPNs are quick, encrypt all of your visitors, offer you entry to any Web website and put you in command of your meant location.
The selection is in the end depending on what you want. Every of those instruments prioritizes a unique factor, although they work towards the identical aim. It’s vital to match every function and go along with the choice that most closely fits your on-line privateness wants.
FAQ: Tor vs. VPN
Neither of those two choices offers you all one of the best options for on-line privateness and safety. Every one excels in numerous areas, and the selection comes all the way down to understanding precisely what you want and which of the 2 works greatest to supply that.
Is Tor Higher Than VPN?
Tor is healthier than a VPN by way of on-line privateness and anonymity. The 2 instruments supply a measure of safety however excel in numerous areas. Tor is healthier for customers who’re after the very best degree of on-line anonymity, who don’t use it for data-intensive functions and who’re keen to commerce pace for privateness.
Is VPN Sooner Than Tor?
VPNs are sooner than Tor as a result of Tor makes use of a number of servers/relays to route your connection, whereas VPNs supply a single-hop connection to the server. This implies VPNs normally present a sooner web connection and are extra environment friendly at bypassing ISP throttling.
Is Tor Nameless?
Whereas Tor isn’t assured to be fully nameless, it’s designed to supply the very best degree of safety and anonymity whereas shopping the online. It’s extraordinarily troublesome to trace Tor person information and visitors, making it the perfect possibility for on-line privateness. It’s vital to notice that many apps and browsers should be configured to Tor earlier than they’re safe.
Can I Use Each Tor and VPN?
Sure, Tor and VPN can be utilized concurrently. There are two configuration approaches: Tor over VPN and VPN over Tor. utilizing the 2 concurrently can probably enhance the net privateness options each options supply.
Defend Your Information With Panda Safety
When trying to find the appropriate VPN, be certain you put in it correctly and understand how the corporate protects your information. For example, the Panda VPN doesn’t hold logs and walks you thru correct set up. Attempt it out in the present day — at no cost! For extra assist and recommendation about staying secure on-line, check out the information and tips on the Panda Safety weblog.
References:



