Beware! Behind the face of advancing know-how lies a darkish underbelly – that of evolving cyber crime. Right here, perpetrators regularly adapt their methods, exploiting present occasions, authorities web sites, and even trusted organizations’ respectable functions to deceive customers. This subtle method entails the usage of trusted names and logos to entice people into downloading pretend apps with malicious intent. As cyber criminals develop into more proficient at social engineering, it turns into crucial for people and companies to stay vigilant towards evolving threats. The continual seek for new avenues to focus on victims and collect delicate data highlights the significance of proactive safety.
To make sure digital security and safety, Seqrite Labs actively screens cybersecurity information and boards, staying abreast of the most recent developments and threats. This proactive stance is important for safeguarding our customers towards the dynamic panorama of cyber threats. On this weblog, we can be delving into the anatomy of faux apps, their malicious distribution, and the way vigilant manufacturers can defend themselves towards the damaging impression of those misleading digital doppelgängers.
Faux Apps: The Persistent Surge and How they Work
The pattern of faux apps is one offshoot of evolving know-how, and reveals no indicators of receding even when Google had taken steps to purge 36 counterfeit Android safety apps from the Google Play Retailer in 2018. These impostors, whether or not on Android or iOS, replicate the looks and performance of respectable functions. Their insidious function? To deceive unsuspecting customers into unknowingly welcoming them into their gadgets. As soon as they succeed with infiltration, these misleading functions are able to critical malicious actions, from aggressive advert shows for income, to unlawful gathering and distribution of consumer’s credentials and delicate information.
Rise of ChatGPT and its Undesirable Exploitation
ChatGPT is likely one of the most quickly increasing shopper web apps in historical past, and has develop into a drive to be reckoned with, charming a weekly viewers of 100 million customers as per The Verge. Ever since its unveiling a 12 months in the past, ChatGPT has develop into a game-changer within the AI panorama, enhancing content material high quality, offering digital tutoring for training and coaching, and guaranteeing swift response instances for customers. Its 24/7 availability, multilingual help, and personalised interactions contribute to a seamless expertise.
With scalability, pure language understanding, and a concentrate on digital accessibility, ChatGPT is not only a software; it’s a catalyst for innovation, revolutionizing how we have interaction with data and help. Sadly, the simplicity and user-friendly interface of ChatGPT, obtainable across the clock, are exploited by menace actors who distribute Android malware disguised as pretend ChatGPT functions with dangerous spyware and adware capabilities. Researchers at Fast Heal have recognized such misleading functions, emphasizing the necessity for heightened consciousness and protecting measures towards these insidious ways.

Upon evaluation, the Faux ChatGPT app requires some dangerous permissions, as proven in Fig 01:
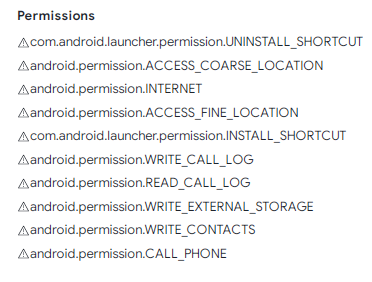
Fig 01. Advanced permissions sought by the malware software
Faux ChatGPT App : The way it Works
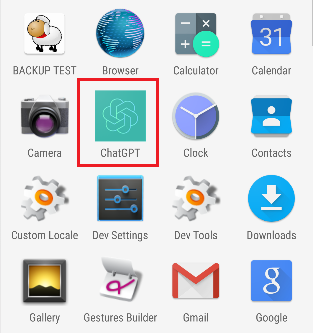
Fig 02. Faux App within the title of ChatGPT
When clicking on the appliance icon to launch, customers are redirected to the accessibility web page the place they’re prompted to offer accessibility permission to the pretend software.
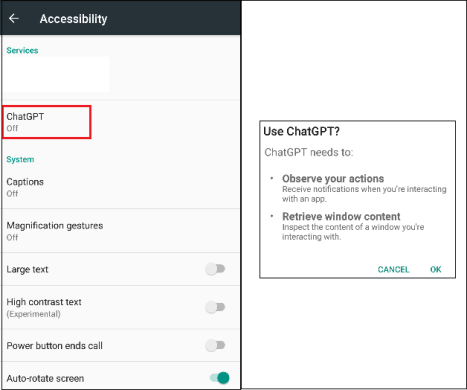
Fig 03. Grant of Accessibility permission
Upon offering accessibility permissions, the appliance hides its icon and runs it within the background.
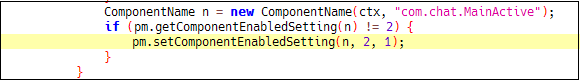
Fig 04. Icon Hiding the Code
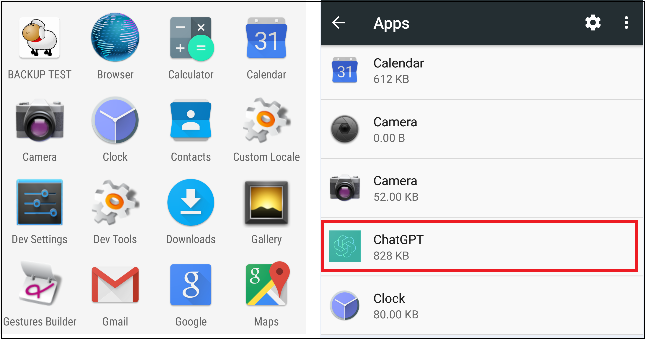
Fig 05. Software will not be obtainable in appdrawer
This app collects location-related information.
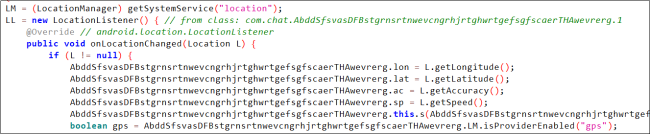
Fig 06. Amassing location associated data
Moreover, it screens incoming calls to system.
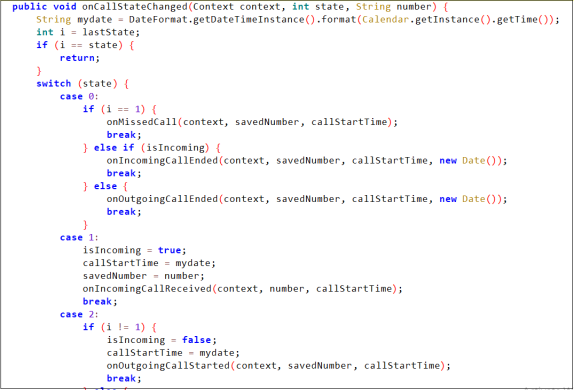
Fig 07. Screens incoming calls
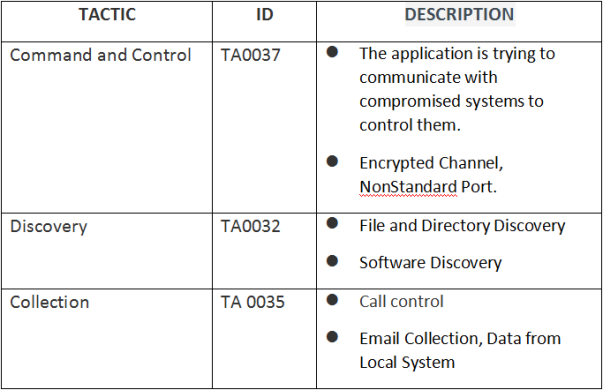
MITRE ATT&CK methods:
Fast Heal Detection
Fast Heal can detect such malicious functions with variants of “Android.SpyNote.GEN.”
It is strongly recommended that every one cellular customers ought to set up a trusted Anti-Virus like “Fast Heal Cellular Safety for Android” to mitigate such threats and keep protected. Our antivirus software program restricts customers from downloading malicious functions on their cellular gadgets. Obtain your Android safety right here
CONCLUSION:
As depicted above, malicious actors lure customers by using icons resembling these of respectable functions. These SpyNote functions may cause important hurt to the contaminated gadgets. Customers ought to concentrate on such ongoing cyber scams when downloading and putting in functions from untrusted sources.
TIPS TO STAY SAFE:
- Obtain functions solely from trusted sources like Google Play Retailer.
- Don’t click on on any hyperlinks obtained by way of messages or some other social media platforms as they might be deliberately or inadvertently pointing to malicious websites.
- Learn the pop-up messages you get from the Android system earlier than accepting or/permitting any new permissions.
- Be extraordinarily cautious about what functions you obtain in your cellphone, as malware authors can simply spoof the unique functions’ names, icons, and developer particulars.
- For enhanced safety of your cellphone, at all times use a great antivirus like Fast Heal Cellular Safety for Android.



