Utilizing public Wi-Fi networks can pose vital safety dangers, together with publicity to evil twin assaults. An evil twin assault is harmful as a result of hackers can get hold of delicate info like your monetary accounts, passwords, bank card transactions and extra. A hacker can use this info to steal cash, commit identification theft or open a fraudulent account in your title.
Learn on to learn the way an evil twin assault works, ideas for shielding your self and what you are able to do for those who fall sufferer to an assault.
What Is an Evil Twin Assault?
An evil twin assault is a spoofing cyberattack that tips customers into connecting to a pretend Wi-Fi entry level that mimics a authentic community. As soon as a consumer is linked to an evil twin entry level, hackers can entry every thing from their community visitors to non-public login credentials.
Evil twin assaults get their title from their skill to mimic authentic Wi-Fi networks to the extent that they’re indistinguishable from each other. Hackers create these false networks to trick unsuspecting customers into logging in and accessing consumer knowledge to steal private info and commit crimes. That is particularly harmful for customers who use the identical username and password for a number of accounts because the hacker might achieve entry to all of them by monitoring only one login try. What’s worse, these assaults are almost inconceivable to establish.
How an Evil Twin Assault Works
Essentially the most harmful evil twin assaults work by tricking victims into considering that they’re connecting to a dependable public Wi-Fi community. To make the assault as plausible as doable, hackers usually use the next steps.
Step 1: Selecting a Location With Free Wi-Fi
Hackers select a busy location with free, well-liked Wi-Fi, like an airport, library or espresso store, to execute their assault. These locations usually have a number of entry factors with the identical title, making it simpler for a hacker’s pretend community to go unnoticed.
Step 2: Setting Up a Wi-Fi Entry Level
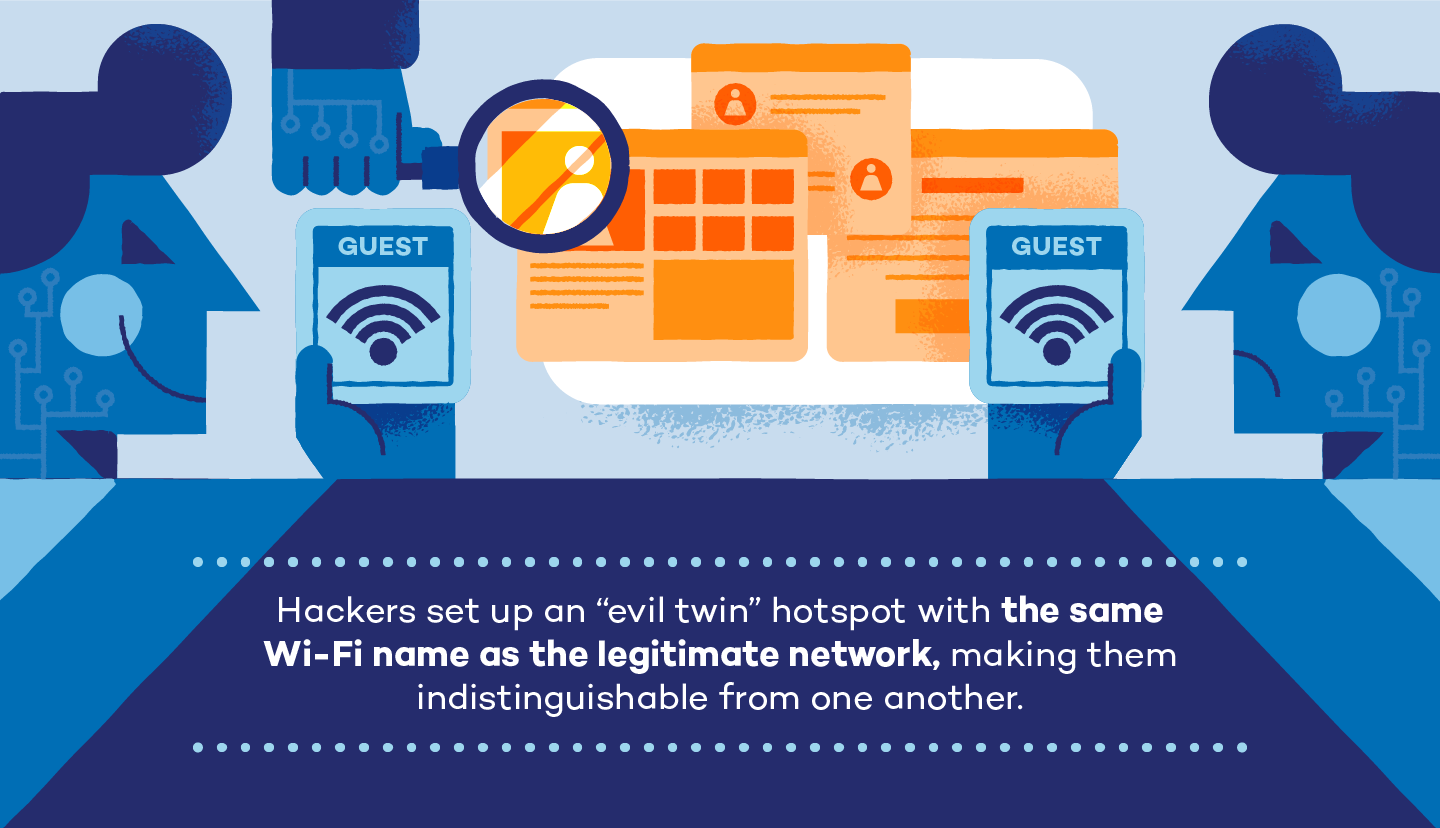
Subsequent, the hacker creates a brand new hotspot utilizing the identical Service Set Identifier (SSID) title because the authentic community. They will use nearly any gadget to do that, together with telephones, laptops, transportable routers and tablets. Some hackers could even use a Wi-Fi Pineapple to attain a broader vary.
Step 3: Making a Faux Captive Portal Web page
If you happen to’ve ever logged right into a public Wi-Fi community, you’ve most likely encountered a captive portal web page. These usually require you to enter a password or different primary info to entry the community.
Whereas many authentic networks use these, hackers can simply replicate them to trick customers into sending over their login info. Sadly, it may be almost inconceivable to inform the distinction between a authentic and pretend captive portal web page if the hacker is aware of what they’re doing.
Step 4: Setting Up Nearer to Potential Victims
As soon as a hacker has completed establishing the evil twin entry level and pretend captive portal web page, they might transfer their gadget or router nearer to potential victims to create a stronger sign. This convinces folks to decide on their community over the weaker ones and forces some gadgets to attach robotically.
Step 5: Monitoring and Stealing Person Knowledge

As soon as a sufferer has linked their gadget to an evil twin community, the hacker can monitor every thing they do on-line, from scrolling by social media accounts to checking financial institution statements. If a consumer logs into any of their accounts whereas linked to the community, the hacker can acquire their login credentials. That is particularly harmful if the consumer makes use of the identical credentials for a number of delicate accounts.
Rogue Entry Level vs. Evil Twin: Key Variations
A rogue entry level may be thought of an evil twin; nevertheless, the phrases should not interchangeable. A rogue entry level is an unapproved wi-fi connection level added to a community with out the community administrator’s consciousness or consent. An evil twin is basically a duplicate of an actual Wi-Fi community connection. Examples of rogue entry factors embody unauthorized Wi-Fi routers, incorrectly arrange gadgets and even forgotten gadgets with wi-fi connectivity.
To know the distinction between rogue entry factors and evil twin assaults, think about this state of affairs:
Let’s say a employee installs a private wi-fi router of their workspace with out authorization from administration. This gadget could be thought of a rogue entry level as a result of it operates with out the correct authorization to be there. But when the employee had been to clone the corporate’s Wi-Fi and use that pretend copy to steal delicate info from the individuals who hook up with it, that might be thought of an evil twin assault.
You may set up software program like Wi-Fi safety and community monitoring instruments to assist detect rogue entry factors.
Evil Twin Assault Instance
Let’s say {that a} consumer decides to connect with a public Wi-Fi community at a neighborhood espresso store. They’ve linked to the entry level there earlier than, so that they assume it’s protected and dependable. This time, nevertheless, a hacker has arrange an evil twin community with an equivalent SSID title and a stronger sign than the authentic entry level. The consumer connects to it regardless of it being listed as “Unsecure.”
Whereas linked to the community, the consumer logs into their checking account to verify their steadiness and later accesses their firm’s portal to make amends for work. As a result of the consumer has not arrange a digital personal community (VPN) to encrypt their knowledge, the evil twin community permits the hacker to entry their banking info and firm web site.
Defend Your self From an Evil Twin Assault
Evil twin assaults may be tough to establish, however there are a number of steps you may take to guard your self when connecting to public Wi-Fi networks.
Use Your Personal Hotspot
The best solution to defend your self from an evil twin assault is to make use of a private hotspot as an alternative of public Wi-Fi every time doable. This ensures that you just at all times hook up with a dependable community in public areas and prevents hackers from accessing your knowledge. Simply bear in mind to set a password to maintain your entry level personal.
Keep away from Unsecured Wi-Fi Networks
If it’s worthwhile to hook up with a public community, attempt to keep away from any entry factors marked “Unsecure.” Unsecured networks lack authentic safety features, and evil twin networks nearly at all times have this designation. Hackers usually depend on folks brushing this off and connecting to their community with out realizing the dangers.
Disable Auto Join
When you’ve got auto join enabled in your gadget, it’s going to robotically hook up with any networks that you’ve used earlier than when you’re in vary. This may be harmful in public locations, particularly you probably have unknowingly linked to an evil twin community previously. To make sure that you at all times hook up with the community you need, disable auto join any time you allow your property or workplace.
By no means Log Into Personal Accounts on Public Wi-Fi
It’s best to keep away from logging into personal accounts every time doable when utilizing public Wi-Fi. Hackers can solely entry your login info for those who use it whereas linked to their evil twin community, so remaining signed out might help defend your personal info.
Use a VPN to Encrypt Visitors

A VPN might help defend you from an evil twin assault by encrypting your knowledge earlier than a hacker sees it. Whenever you obtain a dependable VPN app to your gadget, it encrypts or scrambles your on-line exercise earlier than sending it to the community, making it inconceivable for a hacker to learn and perceive.
Stick with HTTPS Web sites
When utilizing a public community, make sure you solely go to HTTPS web sites. These websites supply end-to-end encryption, stopping hackers from monitoring your exercise when you use them.
Use Two-Issue Authentication
Including two-factor authentication to your personal accounts is an effective way to stop hackers from accessing them. Even when a hacker features entry to your login credentials, the two-factor authentication will stop them from efficiently accessing your account.
Use Personal Search Engines and Browsers
Personal engines like google like DuckDuckGo and privacy-focused browsers like Firefox can stop monitoring and knowledge assortment whereas searching the web. If you happen to unintentionally hook up with an evil twin community, these browsers have built-in options like pop-ups that warn towards malicious websites and malware. They will additionally search for a website’s IP handle to make sure it’s safe.
Though personal browsers cut back the possibility of unveiling private info to hackers, they don’t seem to be particularly designed to detect or stop connections to evil twin networks.
Allow WPA3 Encryption
WPA3 is the most recent Wi-Fi safety protocol. It defends towards brute drive and evil twin assaults by encrypting your knowledge. WPA3-Enterprise is a mode of WPA3 that improves safety for public Wi-Fi networks and stops hackers from monitoring your on-line interactions.
Whereas WPA3 considerably improves Wi-Fi safety and guards towards evil twin assaults, not all Wi-Fi networks assist WPA3, and a few older gadgets is probably not appropriate. Affirm yours is appropriate earlier than making an attempt to allow it, as you could have to accept WPA or WPA2 (that are nonetheless much better than nothing).
Replace Software program Repeatedly
Replace your working system, browsers and safety extensions recurrently to stop safety breaches from outdated software program. Software program updates usually embody patches for recognized vulnerabilities hackers might exploit. Updating your safety software program month-to-month or as updates develop into accessible ensures steady safety.
Monitor Your Community
Use community monitoring instruments to scan for close by Wi-Fi networks recurrently. Search for any sudden or suspicious networks, particularly these with names much like recognized public networks. Keep away from connecting to any unusual networks and notify the community administrator in individual or by emailing an in depth message in regards to the suspected menace, time and site of any unusual community habits you seen. Time is of the essence in these conditions, so notify them as quickly as doable.
What to Do If You Fall Sufferer to an Assault
If you happen to uncover {that a} hacker has breached your knowledge by an evil twin assault, you may file a criticism with the FCC Client Criticism Middle. You must also contact your native police division and your financial institution or bank card firm if the hacker stole cash or gained entry to your banking info in the course of the assault.
Defend Your Community With Panda Safety
Evil twin assaults are only one methodology hackers use to realize entry to delicate info on-line. To additional defend your self from cyberattacks, take into account studying up on essentially the most frequent varieties of hackers and downloading respected antivirus software program. Contact our specialists on-line to debate methods to maintain your knowledge safe.



