Our current analysis has highlighted the presence of the MedusaLocker ransomware, which first surfaced in mid-2019. Its major targets are the Hospital and Healthcare industries. MedusaLocker employs AES and RSA encryption strategies to encrypt victims’ knowledge.
Technical Evaluation
At the beginning, it performs a test for the presence of a Mutex. If the Mutex doesn’t exist, it proceeds to create the Mutex utilizing the CreateMutexW() perform, as proven within the beneath fig:
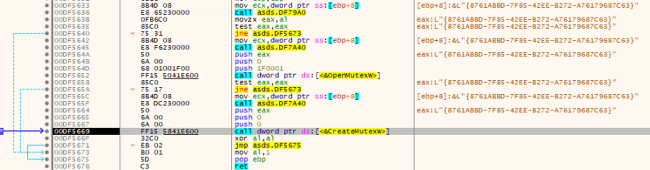
Creating the Mutex
MedusaLocker checks to find out whether or not the present course of runs with administrative privileges. If it detects that the method lacks admin privileges, it employs a Person Account Management (UAC) bypass approach to realize elevated privileges.
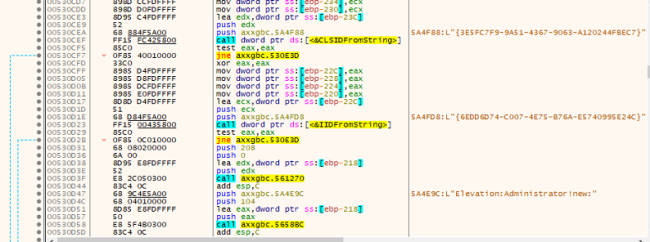
Elevating Administrator Privelege
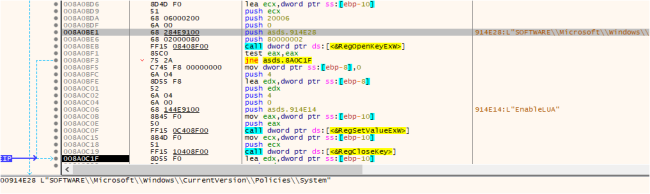
UAC Bypass
It provides the registry key HKEY_CURRENT_USERSOFTWAREMDSLK with the title “self” and knowledge as the applying title, designating the system being contaminated by MDuSaLocker.
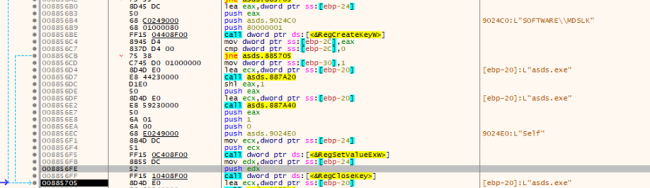
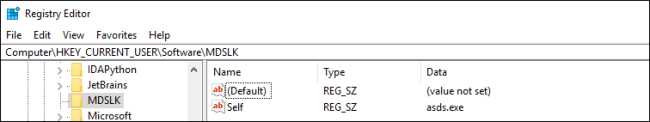
Registry Entry
Disables the Providers and Terminates the Processes:
Like different ransomware, MedusaLocker additionally terminates particular companies by referencing a hardcoded checklist of companies. It compares this checklist with the presently working companies, and if any of the hardcoded companies are discovered to be working, it stops them utilizing the CloseServiceHandle(), as proven within the beneath fig:
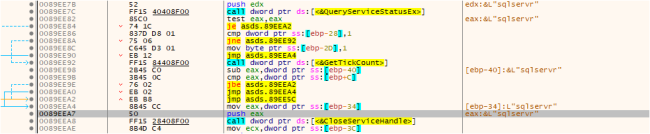
Disables the Operating House
Record of Hardcoded companies:
wrapper, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, sqlservr, sqlagent, sqladhlp, Culserver, RTVscan, sqlbrowser, SQLADHLP, QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, sqlwriter, msmdsrv, tomcat6, zhudongfangyu, SQLADHLP, vmware-usbarbitator64, vmware-converter, dbsrv12, dbeng8
Ransomware makes use of CreateToolhelp32Snapshot() to retrieve the working processes. It compares with a predefined checklist of hardcoded processes. If any of the hardcoded processes are detected as working, the ransomware proceeds to terminate these processes utilizing the TerminateProcess, as proven within the beneath fig:
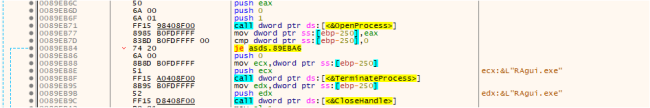
Terminating the Operating Course of
Record of Hardcoded Course of:
wxServer.exe, wxServerView, sqlservr.exe, sqlmangr.exe, RAgui.exe, supervise.exe, Tradition.exe, RTVscan.exe, Defwatch.exe, sqlbrowser.exe, winword.exe, QBW32.exe, QBDBMgr.exe, qbupdate.exe, QBCFMonitorService.exe, axlbridge.exe, QBIDPService.exe, httpd.exe, fdlauncher.exe, MsDtSrvr.exe, tomcat6.exe, java.exe, 360se.exe, 360doctor.exe, wdswfsafe.exe, fdlauncher.exe, fdhost.exe, GDscan.exe, ZhuDongFangYu.exe
Deleting Shadow Copy and Disabling Knowledge Restoration:
MedusaLocker makes use of hardcoded instructions to take away backups, delete the shadow copy, and so on.
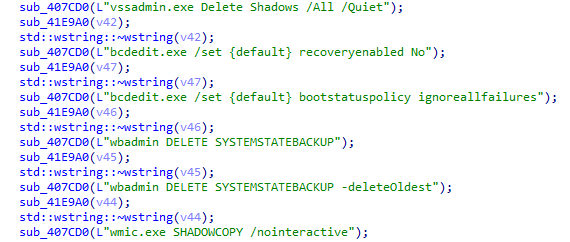
Hardcoded Instructions
PERSISTENCE
Medusa Locker ransomware duplicates its malicious executable as both “svhost.exe” or “svchostt.exe” inside the consumer’s roaming utility knowledge listing (%AppDatapercentRoaming) to determine persistence and make sure the malware runs throughout system start-up, permitting it to proceed encrypting information.
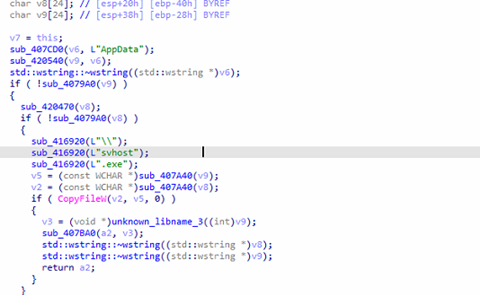
Persistence Mechanism
ENCRYPTION
Within the encryption course of like different ransomware, it additionally excludes the checklist of information, folders, and hardcoded extensions from the encryption course of.
The ransomware makes use of each AES+RSA encryption keys. The ransomware employs AES 256 encryption to lock the sufferer’s information, creating a novel AES encryption key. This AES secret is then encrypted utilizing an embedded RSA public key, ensuing within the ciphertext. The RSA encryption ensures that with out the corresponding personal key, decryption of the AES secret is virtually inconceivable.
The AES secret is important for unlocking the sufferer’s information, making entry contingent on acquiring the personal key from the attackers.
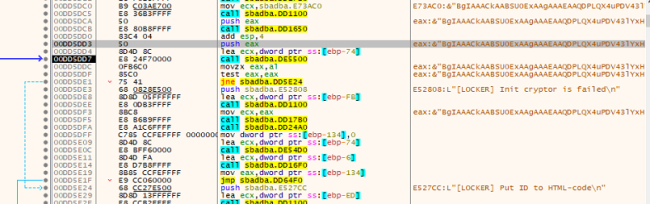
RSA-KEY
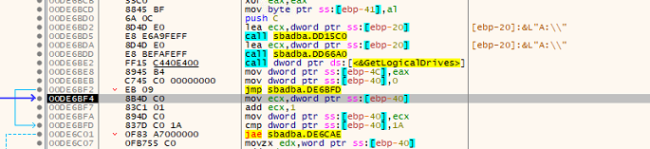
Iteration of Drive
The ransomware tries to retrieve the logical drives utilizing the API name GetLogicalDrives to encrypt the system.
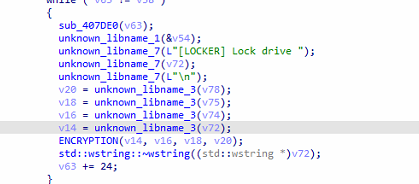
Calling Encryption Operate
It drops the Ransom notice in an HTML file which comprises the non-public ID, Tor hyperlink, and emails of attackers.
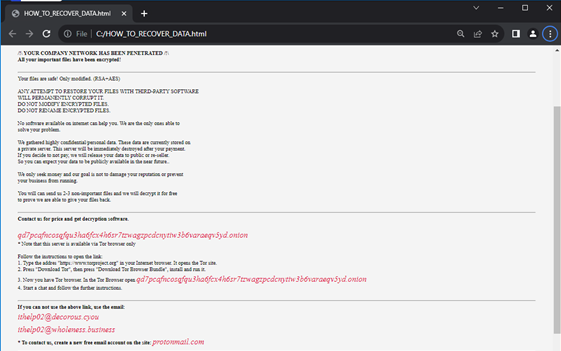
Ransom Word Dropped by Medusa Ransomware
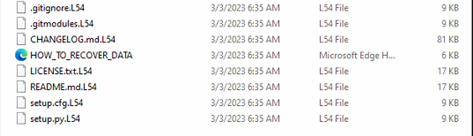
Encrypted Recordsdata with Extension “L54”
Community An infection:
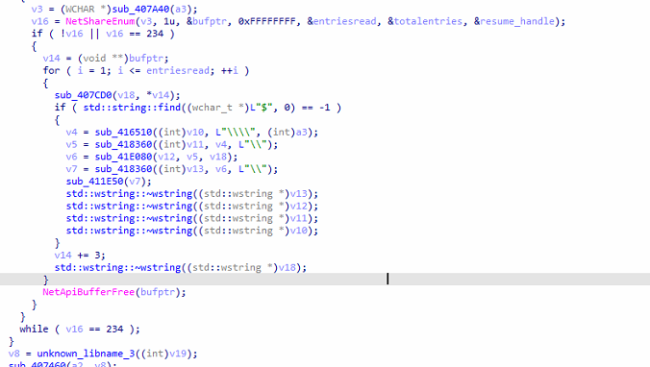
Community Enumeration
After Encryption, the ransomware makes use of Home windows Community API NetShareEnum to enumerate community share. It processes share names, performs string manipulations, and checks for the presence of “$” in share names.
It seeks to unfold to different gadgets on the identical community, making an attempt to contaminate them like a digital contagion.
How can we forestall such sorts of assaults?
· Don’t obtain and open any attachments from unknown sources.
· Keep away from clicking on any unverified hyperlink. The main reason for ransomware assaults is clicking on untrusted hyperlinks and attachments.
· Frequently replace your working system, functions, and software program to repair recognized vulnerabilities, usually exploited by ransomware.
· Again up your knowledge in order that it may be recovered in case of a ransomware assault.
Conclusion
Medusa Locker ransomware is a infamous pressure of malicious software program that encrypts victims’ information, rendering them inaccessible till a ransom is paid. This harmful malware has prompted widespread injury to people and organizations alike. As cybercriminals regularly evolve their techniques, the specter of Medusa Locker stays ever-present.
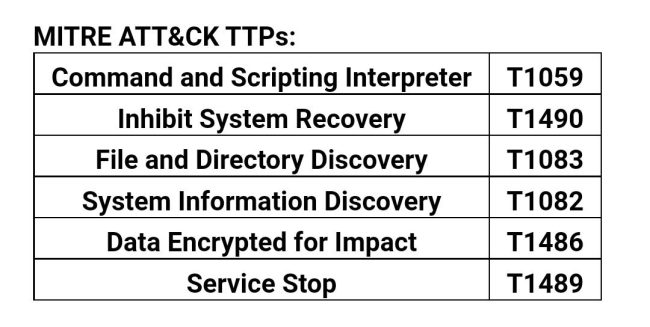
Fast Heal Safety:
· Generic Signature names:
· Ransom.Medusa.S27286013
· Ransom.Medusa.S13913779
· Ransom.MedusaLock.S9836707
· Trojan.YakbeexMSIL.ZZ4
· Ransom.Medusa.S10272352
IOCs:
6da9c76a6e319c17f1d39e0ae2eaf2af
4ef811b784b985769645e03bc0b9cd24
61b0906f31ce772130b0ee9c4b86dc92
Writer – Soumen Burma
Co-Writer – Vaibhav Krushna Billade



