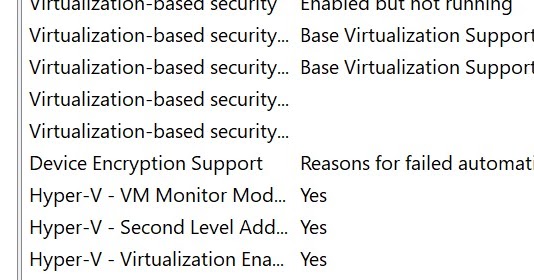
On an affected system, open System Info (as admin) and discover the Gadget Encryption Help merchandise. The worth ought to match what’s proven beneath.
This standing, as famous on this MS doc, “means Home windows detected no less than one potential exterior DMA succesful bus or gadget which will expose a DMA menace.“
The doc may even stroll you thru how one can add the affected element to the whitelist. The onerous half is monitoring down the element(s) so as to add. Within the Whiskey Lake technology, fortuitously just one element must be added.
The next pattern script can be utilized to perform this:
$regPath = "SYSTEMCurrentControlSetControlDmaSecurityAllowedBuses" $keys = @{ 'PCI Categorical Upstream Change Port' = 'PCIVEN_8086&DEV_15C0' } if (!(Get-PSDrive HKLM -ErrorAction SilentlyContinue)) Out-Null foreach ($key in $keys.GetEnumerator()) Out-Null
This can must be run within the SYSTEM context. Upon execution, you possibly can examine within the registry to verify the element has been added.
Now, should you refresh System Info, the worth ought to change to Meets Conditions
As soon as the system restarts, gadget encryption ought to routinely set off so long as the signed in consumer is related to a Microsoft account or Azure Energetic Listing account.
UPDATE 5/28/20
A buyer requested how one can get this engaged on X1 Excessive 2nd Gen. This is the registry values wanted:
‘PCI Categorical Upstream Change Port’ = ‘PCIVEN_8086&DEV_15C0’
‘C240 Collection Chipset Household LPC Controller (CM246) – A30E’ = ‘PCIVEN_8086&DEV_A30E’
‘PCI Categorical DownStream Change Port (Thunderbolt)’ = ‘PCIVEN_8086&DEV_15EA’
‘Intel PCI Categorical Root Port #1 – A338’ = ‘PCIVEN_8086&DEV_A338’
‘Intel PCI Categorical Root Port #9 – A330’ = ‘PCIVEN_8086&DEV_A330’
‘Intel PCI Categorical Root Port #15 – A336’ = ‘PCIVEN_8086&DEV_A336’
‘Intel PCI Categorical Root Port #17 – A340’ = ‘PCIVEN_8086&DEV_A340’
‘Intel PCI Categorical Root Port #21 – A32C’ = ‘PCIVEN_8086&DEV_A32C’