Touring is thrilling, however it will probably additionally expose your smartphone to numerous safety threats. Whether or not you are on a enterprise journey or trip, retaining your telephone safe needs to be a prime precedence.
See additionally – Samsung Galaxy S23 Bluetooth Points
1. Replace Your Software program
Earlier than you hit the street, be sure that your smartphone’s working system and apps are updated. Software program updates usually embody safety patches that repair vulnerabilities hackers might exploit.
2. Use Robust Passwords and Biometrics
Set a powerful password or use biometric authentication (like fingerprint or facial recognition) to lock your telephone. Keep away from utilizing easy patterns or simply guessable passwords. A mix of letters, numbers, and symbols is greatest.
3. Allow Two-Issue Authentication
Activate two-factor authentication (2FA) on your essential accounts. This provides an additional layer of safety by requiring a second type of verification, like a code despatched to your telephone, along with your password.

4. Be Cautious with Public Wi-Fi
Public Wi-Fi networks are a hacker’s playground. Keep away from accessing delicate data, resembling banking apps, over public Wi-Fi. When you should use it, think about using a Digital Personal Community (VPN) to encrypt your web connection.
5. Flip Off Computerized Wi-Fi Connections
Disable the automated Wi-Fi connection function in your telephone. This prevents your machine from connecting to unknown networks with out your permission.
See additionally – Repair iPhone Emails Not Being Pushed
6. Use a VPN
A VPN encrypts your web visitors, making it tougher for hackers to intercept your information. Select a good VPN service and use it everytime you hook up with the web, particularly on public networks – (NordVPN 71% off)
7. Watch out for Phishing Makes an attempt

Whereas touring, you may obtain emails or messages from unfamiliar sources. Be cautious of clicking on hyperlinks or downloading attachments from unknown senders, as these might be phishing makes an attempt to steal your data .
See additionally – What to Do When You Obtain a Phishing Electronic mail (and How one can Defend Your self)
8. Set up Safety Apps
Contemplate putting in safety apps that provide options like anti-virus safety, malware scanning, and theft prevention. Apps like Lookout, Bitdefender, and Norton can present an additional layer of safety .
9. Flip Off Bluetooth When Not in Use
Bluetooth might be one other gateway for hackers. Flip off Bluetooth if you’re not utilizing it to forestall unauthorized entry to your telephone .
See additionally – Repair Android Bluetooth Issues
10. Hold Your Telephone Bodily Safe
Bodily safety is simply as essential as digital safety. Hold your telephone near you, particularly in crowded locations, to keep away from theft. Use a safe bag or pocket, and be conscious of your environment.
11. Backup Your Knowledge
Commonly again up your telephone’s information to a safe cloud service or exterior storage. This ensures you possibly can recuperate your data in case your telephone is misplaced, stolen, or compromised.
12. Disable Pointless Companies
Flip off any providers you don’t want whereas touring, resembling location providers, cellular information, and NFC. This reduces the variety of methods hackers can exploit your telephone.
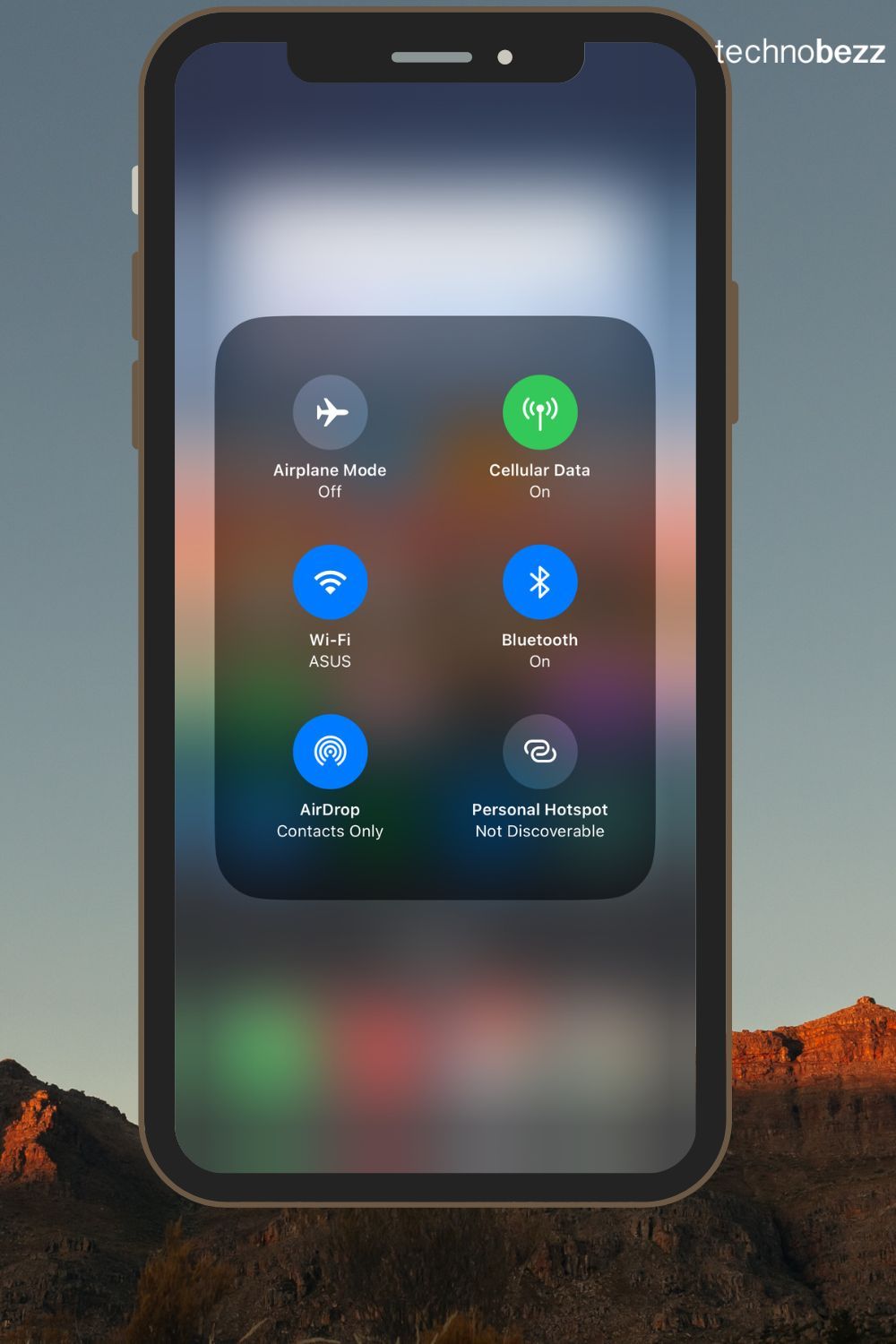
See additionally – Android Name Forwarding Issues
13. Use Encrypted Communication Apps
Use apps that provide end-to-end encryption for communication, like WhatsApp, Sign, or Telegram. These apps be sure that solely you and the particular person you are speaking with can learn the messages.

14. Monitor Your Accounts
Commonly examine your financial institution and electronic mail accounts for any suspicious exercise. When you discover something uncommon, take motion instantly, resembling altering passwords or contacting your financial institution .
15. Set Up Distant Wipe
Allow the distant wipe function in your telephone. In case your machine is misplaced or stolen, you possibly can remotely erase all information to forestall it from falling into the incorrect arms. (You are able to do this with Apple or Android).
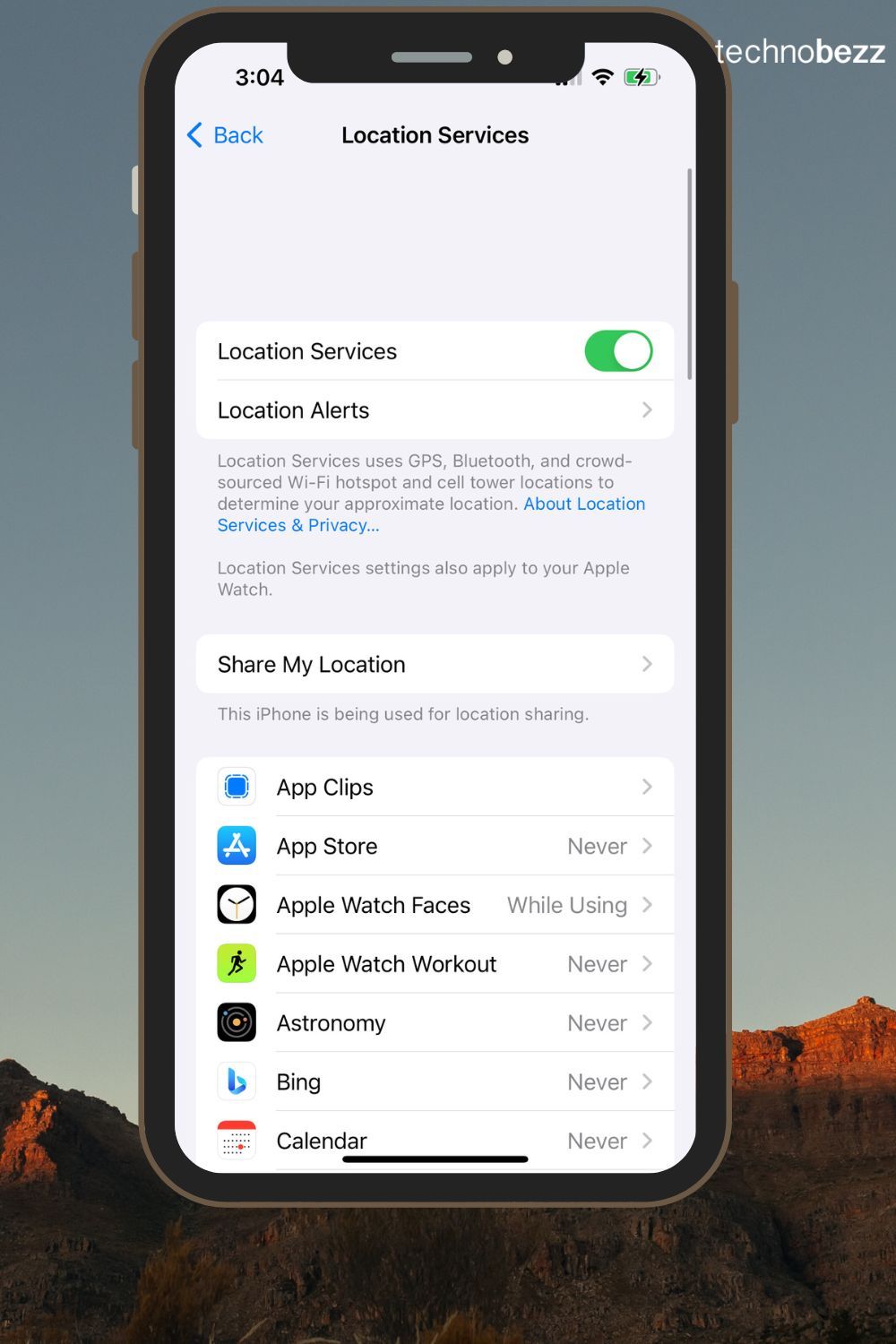
16. Restrict Digital Entry
Obtain any crucial software program earlier than touring. Disable Bluetooth and Wi-Fi when not in use, and keep away from sharing your location with apps except crucial. (Apple : Navigate to Settings > Privateness & Safety > Location Companies)
17. Use Retailers, Not USB Ports
Keep away from utilizing public USB charging stations, which might be tampered with to steal your information. Use an everyday electrical outlet or a private energy financial institution as an alternative. (That is referred to as Juice Jacking – learn extra on FCC.gov)
Why Keep away from Public USB Ports?
-
Juice Jacking: It is a sort of cyber assault the place hackers can set up malware or steal information by means of public USB charging ports. While you plug right into a compromised USB port, it will probably silently switch malicious software program to your machine or entry your private information.
-
Pretend USB Ports: Some hackers arrange faux charging stations that look authentic however are designed to steal data. These might be present in locations like airports, motels, and different public areas.

See additionally – Dash Not Registered On Community
18. Energy Down Your Units Typically
When touring, it’s a great apply to energy down your units often. That is particularly helpful at safety checkpoints the place officers could demand to go looking your units. Powering down reduces the danger of unauthorized entry as a result of:
- Units are safer when off: When your telephone or laptop computer is powered off, it’s much less prone to hacking makes an attempt. Many types of malware and distant entry instruments can not function when the machine is totally shut down.
- Prevents information interception: Some safety measures and surveillance instruments used at border controls and different checkpoints can doubtlessly entry your information. Powering down your machine can decrease this threat.
- Reduces monitoring: Turning off your machine can forestall it from connecting to rogue Wi-Fi networks or Bluetooth units that might be used to trace or entry your information.


