Worms and viruses are each varieties of malware. Worms are extra self-sufficient and unfold independently by means of networks, whereas viruses want human assist and a bunch file or program to unfold.
Worms, viruses, bots, oh my! Such names sound much less like monikers for malicious software program than characters in a sci-fi novel. Regardless of their fictional-sounding names, the financial injury these varieties of malware may cause to computer systems and information could be very actual. Research put the worldwide value of information breaches for 2024 at $4.88 million.
Worms and viruses are malware designed to hurt computer systems or networks. Worms unfold mechanically throughout networks, whereas viruses want a bunch file or program to latch onto. In case your pc isn’t protected, each may cause injury — whether or not by stealing information, disrupting operations, or making your machine unusable.
Study the variations between them and the way they work to restrict the injury of a malware assault and keep away from an infection altogether.
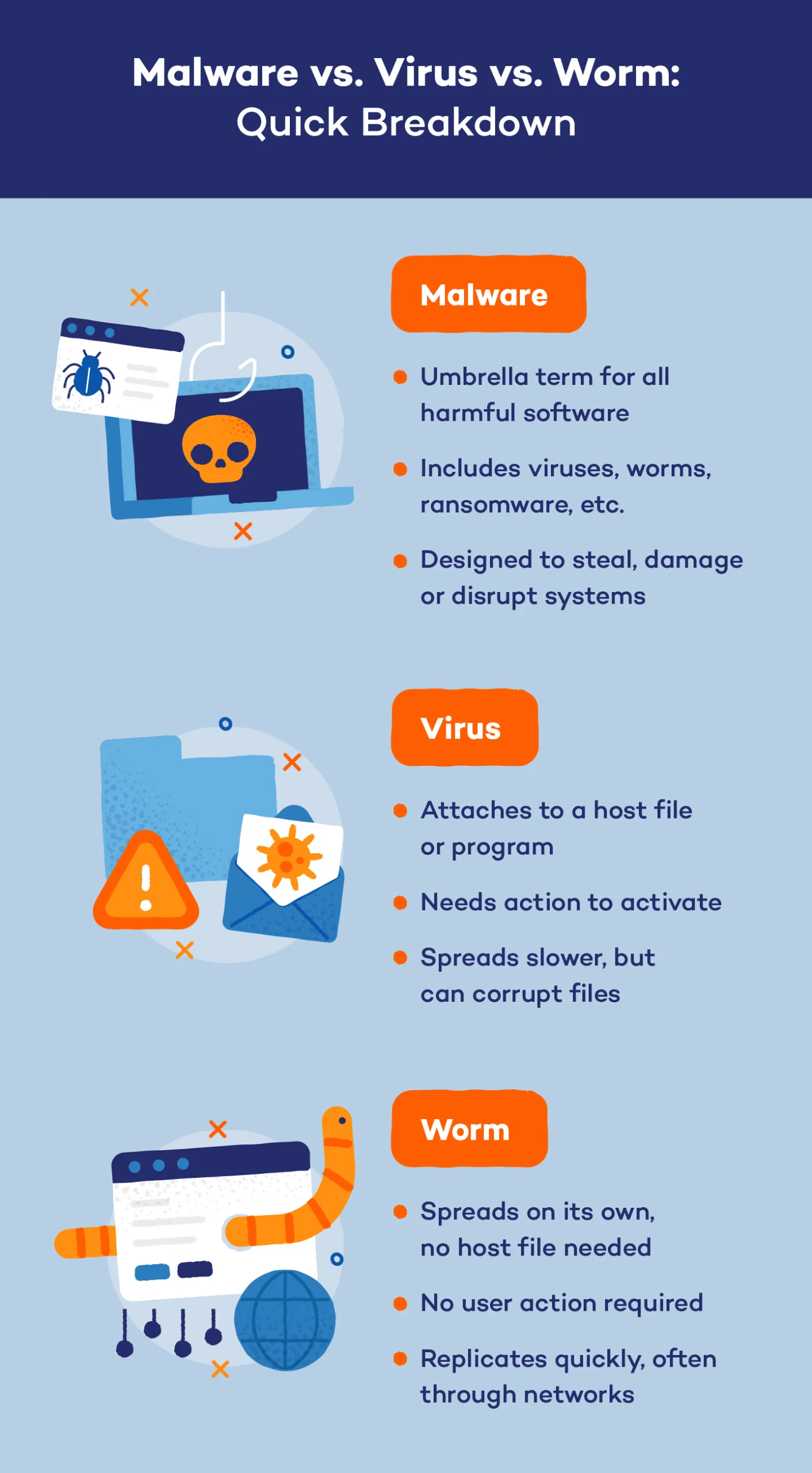
Malware vs. Virus vs. Worm
Malware is available in many varieties, however two of the most typical sorts are viruses and worms. These threats can infect your pc, steal information and disrupt operations. Let’s check out the primary variations between malware, pc worms and viruses.
Malware
Consider malware as a sneaky intruder attempting to interrupt into your house. Some use totally different strategies, however the aim is all the time the identical: to trigger injury or steal one thing invaluable. Malware encompasses all dangerous software program — whether or not it sneaks in by means of a suspicious hyperlink, an contaminated file or a community vulnerability. Its function can vary from stealing your information to locking you out of your system for ransom.
Virus
A virus is a sort of malware, performing like a thief hiding inside a harmless-looking bundle. It’s a must to open the bundle (or file) for it to do injury. As soon as activated, the virus can unfold to different recordsdata and even units, corrupting information and inflicting chaos — bear in mind Friday the thirteenth? A virus is sort of a booby-trapped present that appears harmless however can launch a dangerous shock when opened.
Worm
A worm is like an intruder who doesn’t must be invited in. It slips in by means of unlocked home windows and doorways (community vulnerabilities) and spreads itself throughout the home (community) with none assist from you. Laptop worms can rapidly multiply, infecting many units without delay, inflicting widespread injury, making worm malware a very harmful menace.
Which Is Extra Harmful: Malware, Viruses or Worms?
In the case of threats, each viruses and worms may cause critical injury, however worms usually current a much bigger threat resulting from their capacity to unfold independently. A virus requires human motion — akin to opening an contaminated file — to activate and unfold. Whereas nonetheless dangerous, virus unfold is extra managed and may generally be simpler to include.
Worms, alternatively, don’t want any assist. They’ll rapidly transfer by means of networks, replicating themselves and infecting a number of units in a brief period of time. This makes worm malware notably harmful, particularly for companies with interconnected programs.
With out antivirus safety, the chance of a malware assault skyrockets. Antivirus software program acts as a protection, detecting and blocking these threats earlier than they’ll enter your system. With out it, your units are left susceptible to assaults — whether or not it’s from a virus you by accident set off or a worm that slips into your community unnoticed. Set up an antivirus to cut back the chance of an assault.
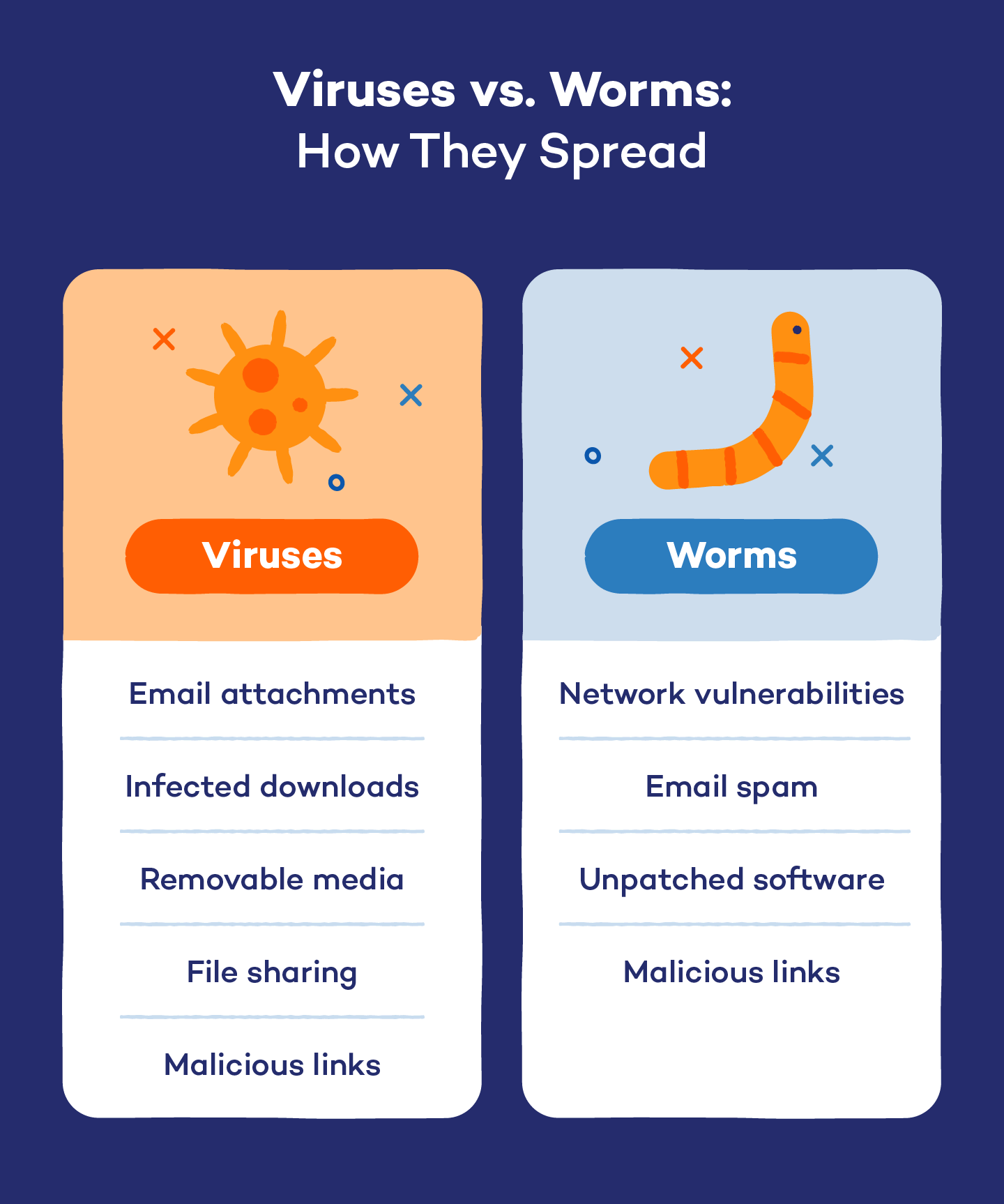
How Viruses and Worms Unfold
It takes human motion to copy a virus. Even iPhones can get contaminated, which revolve round safety and information privateness. Listed below are the primary methods viruses can infiltrate your system:
- Electronic mail attachments: Many viruses are despatched as contaminated attachments. Opening these recordsdata can activate the virus.
- Contaminated downloads: Downloading software program or recordsdata from untrustworthy sources can introduce viruses that disguise inside seemingly reliable downloads.
- Detachable media: USB drives and exterior onerous drives can carry viruses. Plugging in an contaminated machine can switch the virus to your pc.
- File sharing: Sharing recordsdata over peer-to-peer networks can result in virus infections, particularly if the recordsdata come from unverified sources.
- Malicious hyperlinks: Clicking on hyperlinks in emails or on web sites can result in virus downloads or redirection to malicious websites that set up malware.
Identical to viruses, clicking on malicious hyperlinks can result in worm infections, particularly in the event that they exploit community flaws. Listed below are another methods worms can unfold:
- Community vulnerabilities: Worms exploit safety gaps in networks. As soon as a worm enters, it replicates and spreads to different linked units with out consumer interplay.
- Electronic mail spam: Some worms can unfold by means of spam emails, utilizing contaminated attachments or hyperlinks to copy themselves when opened.
- Unpatched software program: Worms usually goal unpatched software program vulnerabilities. Conserving software program up to date is important to stop this sort of unfold.
How Social Engineering Spreads Malware
Social engineering is a approach of tricking individuals into spreading malware to others, and each viruses and worms usually depend on tricking customers into taking motion, akin to opening a file or clicking a hyperlink. Hackers use your personal assumptions and affirmation bias to idiot you.
For instance, if you go to your financial institution’s web site, you normally first search for essentially the most recognizable options: firm title, emblem and the acquainted format of the web page. All of those options tip you off that you just’re in the proper place. As an alternative of making use of a extra vital eye, you rapidly evaluate what you see to what you count on. When these primary expectations are confirmed, you click on forward.
Every single day, hackers create malicious copies of reliable web sites and emails to steal our personal credentials. These digital fakes don’t must be excellent copies both, simply shut sufficient to match our expectations. That’s why it’s greatest to keep away from clicking e mail hyperlinks to widespread web sites and as a substitute use a browser bookmark so that you all the time know you’re in the proper place.
Worms Unfold Otherwise From Different Viruses
Worms are handed by means of recordsdata like attachments or web site hyperlinks, however have the power to self-replicate. They can clone and transmit themselves to hundreds of different computer systems with none assist from people. Consequently, worms are inclined to unfold exponentially sooner than viruses.
Worms have this viral superpower partially as a result of they don’t depend on a bunch file like a virus. Whereas viruses use these recordsdata and applications to run, worms solely want them as disguises to sneakily wiggle into your pc. After that, the worm runs the present. No extra host recordsdata or social engineering required.
Easy methods to Shield Your self From Worms and Viruses
Despite the fact that worms and viruses are totally different, you are taking related precautions to keep away from them, akin to avoiding unfamiliar attachments, holding your OS up to date and defending your units with antivirus or anti-malware.

Keep away from Opening Unfamiliar Messages and Attachments
Like we stated earlier, social engineering preys on our assumptions and familiarity, however you’ll be able to combat it by paying extra consideration to your on-line interactions. Examine emails carefully. Phishing emails normally have telltale indicators they’re scams. Most significantly, by no means open an e mail attachment from an unknown supply. In the event you can’t verify the supply, delete the attachment. One second of satisfying your curiosity isn’t definitely worth the threat.
Keep away from Nonsecure Webpages
Nonsecure web sites don’t encrypt how they discuss to your browser like safe ones do. It’s simple to establish web sites which might be nonsecure. They begin with HTTP of their URL tackle. Attempt to go to solely safe websites that begin with HTTPS. The “s” stands for “safe.” Browser plugins like HTTPS All over the place could make looking out solely HTTPS websites simpler.
Replace Your Working Methods
Hackers love to search out safety holes in working programs like Home windows. It’s a sport of cat and mouse performed with software program engineers who continuously take a look at, establish and patch methods of infiltrating their very own software program. The results of their efforts is the safety replace. Updating your OS applies these patches as quickly as they’re launched, growing your safety stage. Setting your system to auto-update can also be a wise method to keep away from viruses.
Be Choosy About Your Packages
Like working programs, particular person apps in your units additionally want updating — and for a similar purpose. Except for updating them, you also needs to resolve whether or not you even want them in any respect. Keep in mind, viruses want host recordsdata and applications for execution and disguise. Resolve whether or not you really want the app, or if you have already got it, how usually you utilize it. The extra apps you have got, the extra updates you’ll must do. The extra updates, the extra alternatives for a safety breach or an infection.
A few applications it would be best to give particular consideration to are Adobe Flash and Acrobat Reader. Each are fashionable targets for cybercriminals. In the event you don’t use them, uninstall them.
Get Antivirus Safety
The simplest and handiest motion you’ll be able to take to guard your self from worms and viruses is to get a complete antivirus safety plan. Antivirus software program can’t be manipulated by social engineering tips. It by no means assumes something. It scans each file you open and each program you run for viruses and worms. Good ones do that in actual time.
Each worm and virus found will get assigned a “signature,” a novel indicator that claims “This can be a virus!” Antivirus software program retains a listing of these signatures and compares them to the entire information coming by means of your system.
You now perceive the variations between worms and viruses, how they unfold and the place they disguise. Be extra vital the subsequent time you open an unfamiliar e mail or go to a well-recognized web site. Following the following tips and getting antivirus, together with for MacBook, is the easiest way to keep away from malware.
Worm vs. Virus FAQ
Let’s dive into some widespread questions on worms and viruses to clear up any confusion. Understanding these threats is tremendous vital for holding your digital life safe.
What Is the Distinction Between Worms and Viruses?
Worms and viruses are each varieties of malware, however they differ in how they unfold. A virus attaches itself to a bunch file and requires consumer motion to activate, whereas a worm can replicate and unfold independently throughout networks with none human intervention. This makes worms typically extra aggressive of their capacity to contaminate a number of units rapidly.
How Do You Know if You Have a Worm Virus?
The time period “worm virus” is usually mistakenly used, however technically, it’s a misnomer. Worms and viruses are distinct varieties of malware, and there’s no particular malware referred to as a worm virus. Figuring out each may be tough, however widespread indicators embody sluggish system efficiency, sudden crashes and strange community exercise.
What Are 5 Examples of Worms?
Notable pc worms embody ILOVEYOU, Conficker, Sasser, Mydoom and Nimda, every inflicting vital injury by means of strategies like e mail attachments and exploiting system vulnerabilities.
How Is a Worm Totally different From a Trojan?
A worm is a sort of malware that may replicate and unfold independently throughout networks with none consumer motion, whereas a Trojan disguises itself as reliable software program to trick customers into downloading it. In contrast to worms, Trojans don’t self-replicate; as a substitute, they depend on customers to execute the dangerous program, which might result in information theft or system compromise.




