What’s whale phishing?
Whale phishing is a cyberattack that particularly targets high-level executives (CEOs and CTOs) inside a company, aiming to steal delicate info or authorize fraudulent monetary transactions by impersonating trusted people.
Have you ever ever acquired an electronic mail from a trusted sender who actually turned out to be an internet phisher? In that case, you’re not alone. Even massive organizations like Snapchat and Seagate have fallen sufferer to whale phishing assaults.
On the subject of whaling, company electronic mail addresses and high-level staff are sometimes the targets of those refined phishing schemes. Whereas premium safety companies work properly in opposition to smaller, at-home assaults, whaling assaults can slip by means of an even bigger group’s defenses if staff and potential targets are unaware of their risk.
However what precisely is whaling in cybersecurity? Is there extra to it than simply being a cyberattack? We are going to reply all such questions and share some methods to detect whaling assaults so you’ll be able to fortify your cyber defenses.
What Is Whale Phishing?
A whaling assault, or CEO fraud, targets high-level executives like CEOs and CFOs. Not like common phishing scams, whaling assaults are extremely customized and leverage refined ways to trick victims.
As an alternative of mass emails, attackers meticulously analysis their targets, gathering particulars like names, titles and even ongoing firm tasks. This intel fuels the creation of plausible emails that impersonate trusted sources, typically senior colleagues or enterprise companions.
These cyberattacks attempt to manipulate executives into surrendering delicate info, authorizing fraudulent funds or granting entry to inside methods — all with the potential for important monetary acquire for the attackers.

How Whaling Assaults Work
We’ve seen how whaling assaults goal high-level executives and use refined ways to bypass safety consciousness coaching. Let’s break down the three primary steps hackers use to drag off government phishing:
Think about a fisherman rigorously selecting bait for a particular kind of fish. In whaling assaults, the attackers are like these fishermen.
They spend time researching their targets, typically by scouring the web (firm web sites, social media) and even compromising low-level worker accounts to collect intel. Right here’s what they is likely to be in search of:
- Names and titles of CEOs, CFOs or different high-ranking officers
- Particulars about ongoing firm tasks or current information
- Details about the goal’s private pursuits or skilled community
With this intel, they’ll choose the proper “whales” to focus on and craft a convincing assault.
-
Crafting plausible emails
As soon as the attackers have their goal, they create a spoofed electronic mail that appears to return from a reputable supply. They may impersonate:
- A senior colleague, just like the CEO or one other government
- A trusted enterprise accomplice the goal has labored with earlier than
- Even somebody exterior the corporate, like a pretend lawyer or marketing consultant
Hackers use whaling social engineering strategies to rigorously craft emails which can be related to your scenario. For instance, the attacker may:
- Point out a particular challenge the goal is engaged on and request pressing info.
- Reference a current information article or occasion associated to the goal’s trade.
- Use private particulars they’ve discovered on-line to construct belief (e.g., “I hope your current trip to New York was gratifying.”).
-
Tricking the goal
These emails typically create a way of urgency or strain to get the goal to behave shortly. They may embody:
- Requests to click on on a hyperlink to entry a doc or obtain an attachment (typically containing malware that steals credentials or infects the pc)
- Directions to wire cash urgently (typically to a fraudulent account)
- Strain to reply shortly with out double-checking particulars
Utilizing a mix of stolen info, impersonation and urgency, whaling assaults try and trick even probably the most security-conscious executives into freely giving delicate info or granting entry to firm methods.
Whaling Assault Examples
Listed below are some frequent situations dangerous actors use in whaling cyberattacks:
- Faux mergers and acquisitions: The attacker impersonates somebody excessive up within the firm (CEO, CFO) and initiates contact with one other government or a trusted enterprise accomplice. They may declare to be negotiating a confidential merger or acquisition and request delicate monetary paperwork or wire transfers to expedite the deal.
- Pressing requests from acquainted faces: The attacker spoofs the e-mail tackle of a colleague, advisor or shopper the goal is aware of and trusts. The e-mail may include a fabricated story about needing fast assist with fee, doc switch or login credentials resulting from a technical difficulty or misplaced cellphone.
- Knowledge exfiltration by means of pretend inside communication: Attackers might acquire entry to a low-level worker’s electronic mail account and use it to focus on different staff throughout the firm. They may pose as a supervisor or HR consultant and request worker info (like payroll knowledge) underneath the guise of a reputable inside course of.
These ways, typically mixed with refined social engineering strategies, make whaling assaults extremely efficient in compromising delicate info and inflicting important monetary loss. Organizations should implement sturdy safety measures and educate staff in regards to the dangers of those assaults.
Easy methods to Detect a Whaling Assault
Since whaling assaults have the next return risk, they’re extra strategically deliberate and might be tough to detect. You may detect most whale phishing assaults by means of these indicators:
- Spoofed and pressing emails: Many whaling assaults will use spoofed emails with pressing messages to start an assault. These emails will look virtually equivalent to trusted organizational emails, giving them an air of credibility that may spur motion.
- Contaminated hyperlinks, attachments and touchdown pages: Suspicious hyperlinks, attachments and touchdown pages are used to deposit malware onto weak gadgets. They are often embedded within the physique of a spoofed electronic mail or textual content message.
- Excessive-value targets: Whaling assaults will typically goal high-value people in a company. These targets might have direct entry to credentials or firm funds.
- Impersonation: If a whaling assault doesn’t goal a CEO or COO, hackers might select to impersonate them as a substitute. Impersonators then goal lower-level staff who might have entry to servers or different delicate info.
If a number of of those indicators are current in a cyberattack, you might have the makings of an ideal storm for a whaling assault.

6 Methods to Defend In opposition to Whaling Assaults
Whereas whaling could also be a extra refined phishing assault, there are nonetheless methods to organize for and defend in opposition to it. Listed below are six protection ways and whaling cyber consciousness measures you should use:
- Conduct common safety coaching on phishing ways, social media security and pink flags for everybody — from CEOs to interns.
- Make multi-factor authentication (MFA) necessary, particularly for wire transfers, entry to delicate knowledge and electronic mail/knowledge verification processes.
- Implement knowledge loss prevention (DLP) options that monitor emails for suspicious exercise and block spoofed addresses or malicious content material.
- Tighten social media privateness and upskill staff (particularly high-value targets) in sturdy social media privateness settings.
- Limit entry to private info, and be conscious that each private {and professional} accounts might be focused by attackers.
- Put money into anti-phishing assets and subscribe to companies supplied by organizations just like the Anti-Phishing Working Group (APWG).
In brief, vigilance, training and know-how working collectively are important for safeguarding delicate info and defending the underside line.
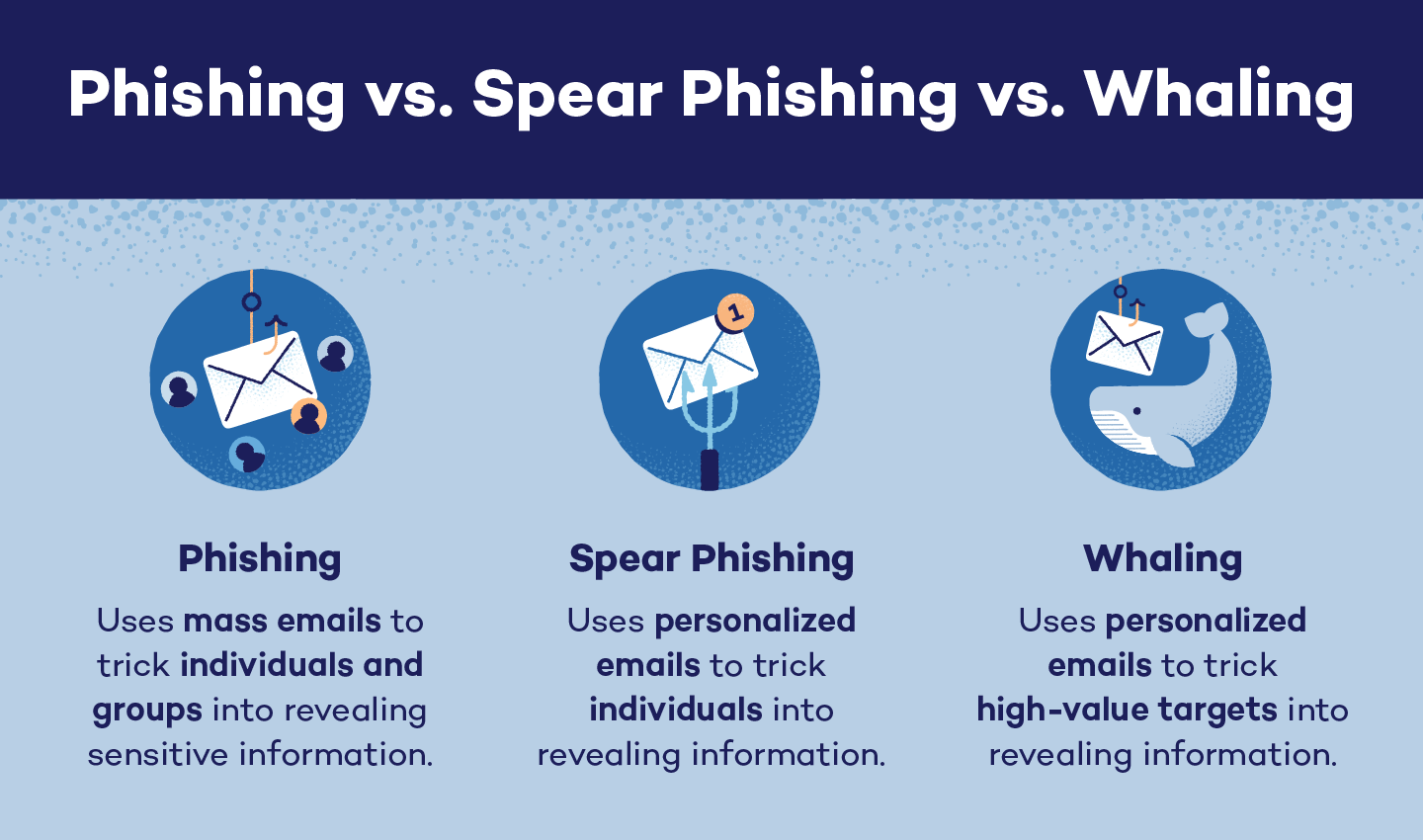
Phishing vs. Spear Phishing vs. Whaling
Phishing, spear phishing and whaling cyberattacks can simply be confused as a result of they’re from the identical household of cyberattacks. Nevertheless, they’re completely different, and every kind of assault makes use of particular ways.
Phishing assaults confer with the broad class of phishing schemes. These might be beginner or refined assaults, they usually goal a wide range of completely different entities — together with people, teams and organizations. Phishing assaults attempt to idiot or persuade somebody to take motion, which might be so simple as clicking on a hyperlink or as intricate as wiring funds to a checking account.
Spear phishing lies underneath the umbrella class of phishing, nevertheless, spear phishing assaults normally goal particular people somewhat than teams. These assaults will use particular info — like notices of present occasions, monetary data or organizational happenings — to achieve belief.
Whaling is a particular kind of spear phishing assault. Whereas spear phishing can goal any particular person, whaling targets high-value people who usually tend to have entry to knowledge or funds. Just like spear phishing assaults, whaling assaults use tactical emails which can be customized to persuade people to behave. Whaling attackers won’t ship mass emails and should even use follow-up calls to seem extra reputable.
Phishing scams might be scary, and whaling assaults are a very sneaky type. To maintain your info safe, select distinctive passwords and use a VPN to soundly and securely browse the web.



