A social media menace entails malicious actions concentrating on customers by way of social platforms, reminiscent of phishing scams or id theft. Attackers might impersonate reliable contacts or firms to achieve entry to your private data or unfold dangerous content material.
Social networks present an area for folks to work together, be taught from one another and share bits and items of their life. Whereas there’s little restrict to what’s shared on-line, sharing an excessive amount of data can result in dangerous penalties.
Social media threats are discovered on any social community, so you ought to pay attention to what they’re and what they appear like to keep away from them. One in 4 people who misplaced cash to fraud since 2021 reported that it started on social media. These scams have an effect on the privateness of your account, making it vital to take safety precautions to guard your self and your private knowledge.
Be taught extra about totally different social media assaults and threats and the way to be a safer social media consumer.
What Is a Social Media Risk?
A social media menace encompasses actions that jeopardize a person’s or group’s social media account. As many social media customers submit or share private particulars on-line, attackers can simply use this data to take advantage of or blackmail them.
These threats emerge in several varieties, together with impersonations, on-line harassment and malware. Beneath are a few of the commonest threats on social media that attackers use to achieve entry to your data.

1. Identification Theft
Identification theft is a standard social media menace that may occur to anybody who shares photographs or private data on-line. Impersonation occurs when somebody makes use of public data and photos to create a faux on-line profile and both faux they’re that particular person or create a brand new persona solely.
Identification theft is extraordinarily dangerous if the impersonator positive aspects entry to your financial institution accounts or methods others into sending them cash. It additionally consists of having access to your social media accounts and posting content material to rip-off websites, which places different customers susceptible to being taken benefit of.
2. Cyberbullying
Sixty-seven p.c of web customers have seen hate speech on-line, with 74% below 35 years previous. Cyberbullying consists of dangerous and damaging posts, messages or content material shared both on to a consumer or publicly. It might probably additionally occur anonymously.
To raised shield your self towards on-line harassment and different social media cyberattacks, maintain your account in personal mode and be selective of your on-line followers or mates. Report cases of cyberbullying to the social media platform to get any malicious posts flagged and eliminated.
Many social networks, like Instagram, have neighborhood pointers in place which have a no-tolerance coverage for actions that fall below the cyberbullying umbrella.
3. Pretend Giveaways
Many manufacturers are turning to social networks to advertise their services and products. Giveaways are cost-effective and attain a wider viewers with promoted posts.
To develop consciousness, manufacturers typically promote giveaways of their merchandise to followers. In keeping with Easypromos, almost 93% of manufacturers surveyed run giveaways on their social networks to achieve extra visitors and clicks to their web site.
Whereas these giveaways could seem too good to be true, typically they are surely. Scammers will create faux model profiles that promote giveaways for followers to enter and submit their private data. Since October 2017, Fb has deleted 27.67 billion faux accounts.
4. Likejacking
Likejacking is a artful social media safety threat that hackers use to power customers to click on the “like” button on a submit or web page with out them realizing they did it.
As an illustration, you may see an fascinating picture or video that requires you to click on on it to view extra data. What you don’t know is that the scammers hid a “like” button behind the picture or video so you can’t see it. You’ll then begin seeing extra of those photographs pop up and overload your social feeds.
5. Phishing Scams
Phishing is a technique scammers use to gather private data by way of on-line messages, emails, hyperlinks and spoofed web sites. These messages seem like despatched by an expert firm or trusted supply, like a financial institution or bank card firm.
Hackers ship phishing messages to trick you into sending over contact data like password particulars or bank card account data. These messages might comprise malicious hyperlinks that may give hackers entry to your units or infect them with a virus.
By no means reply to these kinds of messages or click on suspicious hyperlinks except you requested the hyperlink or acknowledge the cellphone quantity or e mail deal with they arrive from. For instance, verify your financial institution’s customer support cellphone quantity or e mail to verify it matches. Contact customer support immediately to verify they despatched the message to you.
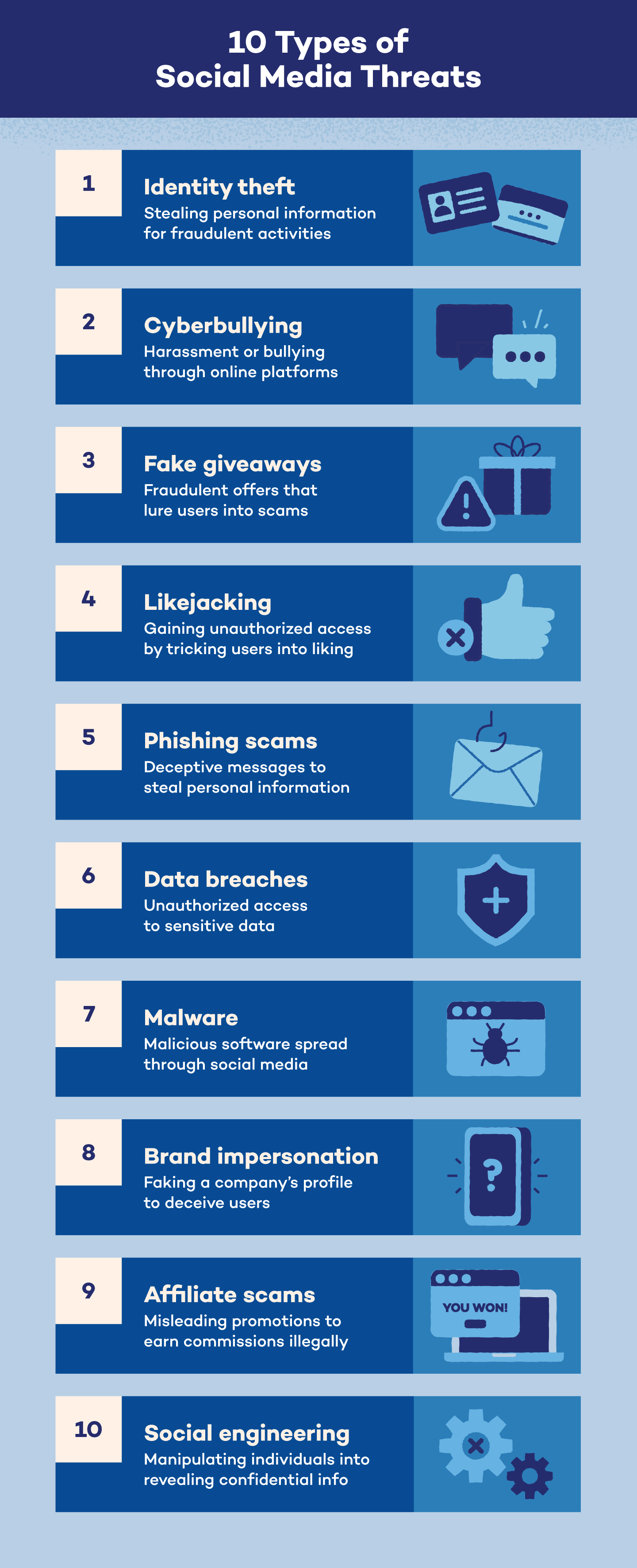
6. Knowledge Breaches
A knowledge breach is a dangerous cyberattack that happens when a hacker positive aspects entry to confidential data. Knowledge breaches can have an effect on any measurement or kind of group or enterprise — the NPD breach in August 2024 compromised 2.9 billion data.
For people, this consists of entry to Social Safety numbers, bank card accounts and well being care data. For bigger organizations, this could embody shopper lists or worker well being data.
If somebody accesses these kinds of knowledge illegally, the goal group might face critical authorized bother. If the info breach causes a violation of any compliance mandates, the affected group may obtain fines and litigation. Relying on the severity of the breach, the corporate may even lose the proper to function.
7. Malware
Malware is designed as a code or file that transfers over to a consumer’s pc to contaminate it or steal private data.
Malware pops up in all varieties, however it’s particularly widespread to make use of with faux information posts or movies. The scammer’s aim is for the consumer to click on on the falsified information story, which is riddled with a malware virus that may compromise the consumer’s system or social media account.
Malware can even present up in faux web sites or domains. It’s possible you’ll be requested to obtain a file to entry the location, however the file is definitely malware, and by downloading it you’ve given the virus (and the one who created it) entry to your system.
For instance, let’s say a web site has a video that “requires” a software program replace to view it. Double-check that the location is reliable earlier than downloading something. When you’re undecided, it’s finest to depart the location to keep away from any chance of malware.
8. Model Impersonation
Not even manufacturers are secure from social media threats. Scammers may create a social media account to impersonate a model and speak to clients below the guise that they’re a reliable firm.
The attacker’s aim is to both obtain private data from recipients, like account login particulars, or share messages that hurt the model’s popularity.
9. Affiliate Scams
Some firms create affiliate applications to contract social media influencers to submit content material in regards to the firm, and in return earn fee on services or products they promote by way of their affiliate hyperlink.
Firms use affiliate internet marketing to drive visitors to their web site and earn income. Nonetheless, you’ll probably come throughout affiliate internet marketing content material that isn’t actual.
Scammers might submit content material that seems to be an commercial providing a free reward card, requiring you to enter your private e mail deal with to obtain it. However as an alternative of receiving the reward card, you get an endless quantity of spam emails, a few of which can even comprise malware.
10. Social Engineering
Social engineering is a tactic cybercriminals use to govern people into divulging confidential data. Within the context of social media, attackers may pose as reliable workers or inner contacts inside the firm. They typically craft convincing tales or use faux identities to achieve the belief of precise workers.
As soon as they’ve established credibility, they’ll request delicate private details about you, reminiscent of login credentials or contact particulars. This sort of deception can result in unauthorized entry to consumer accounts, private knowledge breaches and additional exploitation of each the corporate and its customers.
How Do Social Media Threats Happen?
Social media cybersecurity threats happen when a consumer’s private data and particulars are accessed on-line by hackers and scammers. Fraudsters are inclined to assault accounts which have little safety and customers who aren’t conscious of the hazards of cyberattacks.
Hackers typically use ways like social engineering, manipulating you into clicking dangerous hyperlinks or revealing private knowledge. Moreover, weak passwords or lack of two-factor authentication make accounts simple targets. As soon as inside, attackers can steal knowledge, unfold false data or use the account for malicious actions.
How Do You Stop Social Media Threats?
The easiest way to forestall social media dangers from knocking in your digital door is by realizing the way to spot them and being proactive about your on-line security. Beneath are just a few methods to push back social media threats:
- Advert blockers: Most organizations suggest or request that workers use advert blockers on-line, and it’s a good suggestion exterior of labor, too. Advert blockers remove random pop-ups that would comprise malware.
- Filter buddy requests: By no means settle for a buddy request from somebody you don’t know, even when you’ve got mutual mates. It’s probably the greatest methods to keep away from social media threats of violence like cyberbullying.
- Replace passwords often: Updating your login credentials repeatedly and selecting robust passwords will lower the probabilities of a hacker determining your password. With that, by no means share your passwords with anybody.
It’s additionally finest observe to maintain educating your self and others about on-line threats and scams, as attackers continually replace their ways to maintain tricking unsuspecting customers.
Be cautious about clicking on suspicious hyperlinks, even when they arrive from mates. Cybercriminals typically hack accounts and ship messages that seem like from trusted contacts. These messages might or might not appear uncommon or out of character, so it’s vital to confirm with the buddy immediately earlier than clicking on any hyperlinks or downloading attachments. This straightforward step may also help shield towards falling sufferer to scams or malware.

6 Ideas for Utilizing Social Networks Safely
Whether or not you contact base on social media periodically or use it each day, it’s vital to observe secure on-line habits and shield your self from hackers and spammers. Beneath are a number of tricks to higher shield your self, your children and your units.
1. Set up a Safety Resolution
Set up a safety answer, like antivirus software program, with proactive applied sciences on the pc. You’ll be protected towards malicious codes that unfold by way of these networks, even when no earlier assault has been launched.
2. Preserve Your Laptop Up-to-Date
Customers should pay attention to and resolve all of the vulnerabilities that have an effect on the applications put in on the pc.
Sustain with software program updates on your web browser and different applications in your pc. These updates embody safety fixes to maintain hackers from accessing your data. Some applications even provide the choice of computerized updates when you are inclined to neglect.
3. Don’t Share Confidential Info
When you entry boards and chats to trade data, discuss, and so forth., keep in mind to not present confidential data like e mail addresses or login credentials.
When you do by accident share login data, instantly replace it with a robust password to keep away from somebody signing in to your account. Replace your passwords repeatedly for one of the best safety.
4. Educate Youngsters About Social Media
Youngsters should know what data they shouldn’t share. Meaning mother and father should know the social networks their kids entry and educate them the way to safely have interaction.
Selling open communication about utilizing social media may also help your little one really feel extra comfy. Be open to their questions and considerations, and talk about the way to have a wholesome relationship with social networks.
5. Solely Present Vital Info in Your Profile
When creating consumer profiles, solely present the data vital. If it requests personal knowledge like an e mail deal with or age, select the personal profile mode to forestall different customers from seeing the data, to make sure no customers apart from your self and the administrator entry your knowledge.
6. Report Crimes
When you observe inappropriate or felony habits (like makes an attempt to contact kids, inappropriate photographs, modified profiles, and so forth.), you could inform the social community directors.
Enhance Your Social Media Safety With Panda Safety
On-line safety is vital to us, and that’s why Panda Safety offers cybersecurity companies and instruments which might be used to forestall cyberattacks and threats to your units. Panda Safety’s antivirus software program not solely protects towards viruses but in addition protects your knowledge, passwords and searching historical past.



