A Smurf assault is a cyberattack the place a hacker methods gadgets into sending undesirable site visitors to a goal, overwhelming it.
Ever skilled your web being overloaded with ineffective site visitors, making every thing sluggish or crashing altogether? That’s what a Smurf assault appears like for a pc community.
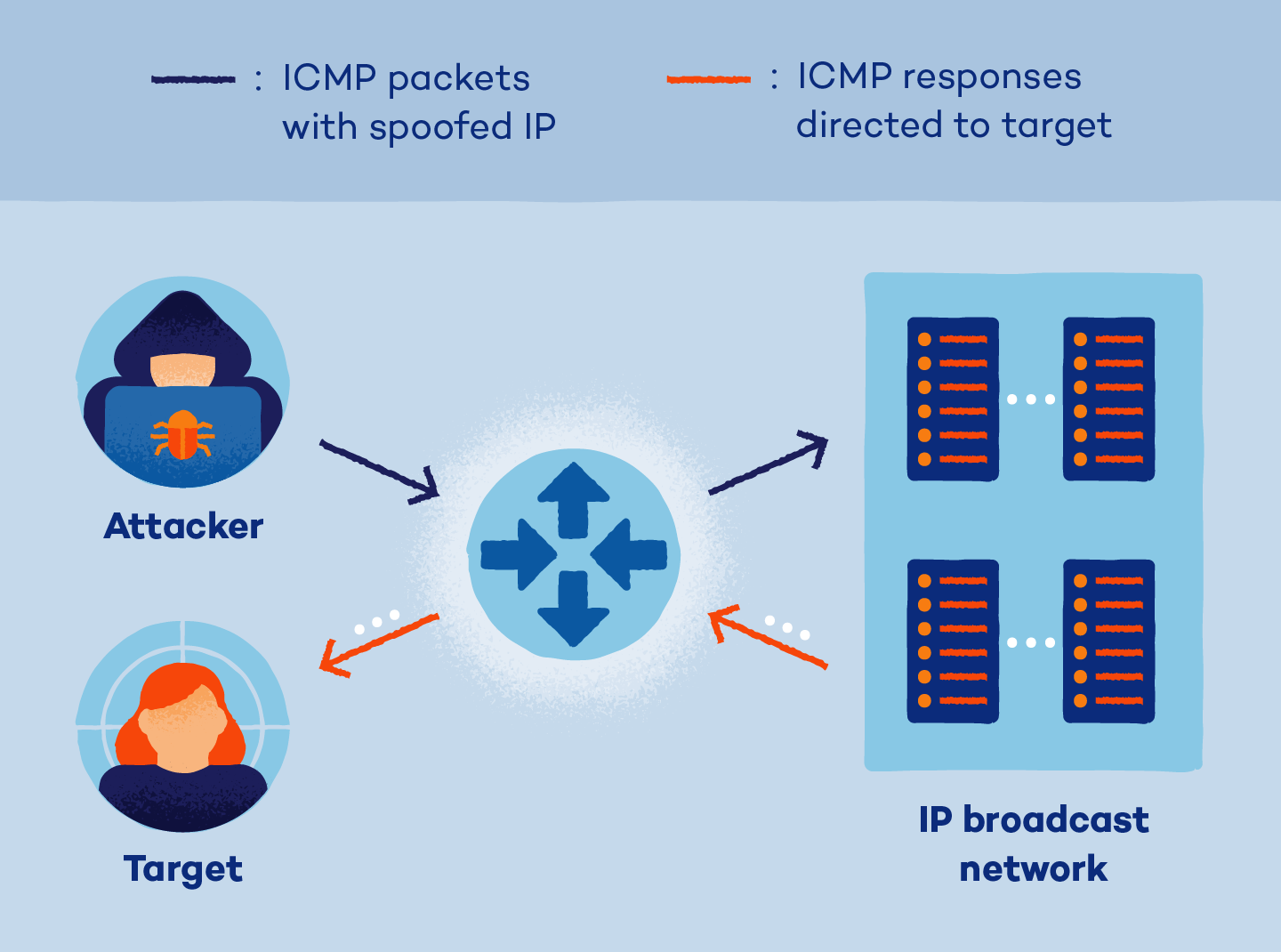
A Smurf assault is a distributed denial-of-service (DDoS) assault wherein an attacker floods a sufferer’s server with spoofed Web Protocol (IP) and Web Management Message Protocol (ICMP) packets. Because of this, the goal’s system is rendered inoperable. This kind of assault will get its title from a DDoS.Smurf malware software that was broadly used within the Nineties. The small ICMP packet generated by the malware software may cause vital injury to a sufferer’s system, therefore the title Smurf.
Whereas Smurf assaults aren’t as frequent right now, understanding how they work can assist defend you from related on-line threats. We’ll break down Smurf assaults, explaining what they’re, their varieties, how they work and keep protected.
Smurf Assault Instance
Consider a trickster (the DDoS.Smurf malware) calling an workplace (the IP broadcast community) whereas masquerading as the corporate’s CEO.
In our instance, the trickster asks a supervisor to inform each worker to return his name (the ICMP echo requests) on his personal quantity to present a mission standing replace — however the personal quantity (the spoofed IP deal with) truly belongs to the trickster’s focused sufferer. Because of this, the sufferer receives an onslaught of undesirable cellphone calls (the ICMP echo replies) from every worker within the workplace.
How Does a Smurf Assault Work?
Smurf assaults are just like a type of denial-of-service (DoS) assaults known as ping floods, since they’re completed by flooding a sufferer’s laptop with ICMP echo requests. Right here’s how a Smurf assault works:
- Attacker locates the goal’s IP deal with: An attacker identifies the goal sufferer’s IP deal with.
- Attacker creates spoofed knowledge packet: Smurf malware is used to create a spoofed knowledge packet, or ICMP echo request, that has its supply deal with set to the true IP deal with of the sufferer.
- Attacker sends ICMP echo requests: The attacker deploys ICMP echo requests to the sufferer’s community, inflicting all linked gadgets throughout the community to reply to the ping through ICMP echo reply packets.
- Sufferer is flooded with ICMP replies: The sufferer then receives a flood of ICMP echo reply packets, leading to a denial-of-service to official site visitors.
- Sufferer’s server turns into overloaded: With sufficient ICMP reply packets forwarded, the sufferer’s server is overloaded and doubtlessly rendered inoperable.
Kinds of Smurf Assaults
Smurf assaults are usually categorized as primary or superior. The one distinction in the kind of assault is the diploma of the assault that takes place.
Primary
Think about a prankster sending hundreds of postcards together with your return deal with to a single random deal with. A primary Smurf assault works equally. The attacker finds the sufferer’s IP deal with and exploits community vulnerabilities to ship a large wave of ICMP “ping” requests (like digital echoes) to the sufferer’s community’s broadcast deal with.
These requests seem to come back from the sufferer, tricking each system on the community to reply with a reply. This flood of replies overwhelms the sufferer’s system, doubtlessly crashing it.
Superior
A sophisticated Smurf assault takes this idea additional. Now, the prankster is sending postcards together with your deal with and in addition together with extra addresses on the postcards as targets. It begins like a primary assault, however the attacker manipulates the “ping” requests to incorporate a number of sufferer IP addresses.
When gadgets on the preliminary goal community reply, the replies are additionally directed at these extra victims. This creates a domino impact, overwhelming not simply the unique goal but additionally the unsuspecting extra victims bombarded with sudden site visitors.

Penalties of a Smurf Assault
Whereas the purpose of a Smurf assault is to render a sufferer’s system ineffective for hours and even days, it can be step one towards extra dangerous assaults like knowledge theft or identification theft. Both approach, the results of a Smurf assault stay:
- Income loss: An organization server that’s inoperable for hours or days on finish typically means a halt in enterprise operations, leading to misplaced income and pissed off clients.
- Knowledge theft: Attackers can acquire unauthorized entry to the info on the sufferer’s host server throughout an assault.
- Reputational injury: In case your purchasers’ confidential knowledge is leaked after an assault, it will probably result in a everlasting breach of their belief and loyalty to your group.
Smurf Assault Prevention: Find out how to Shield Your self
Mitigating a Smurf assault comes all the way down to securing your community, which begins together with your router. To guard your self, you’ll have to configure how your routers and gadgets work together with ICMP packets. This entails 5 necessary prevention steps:
- Disable IP broadcast deal with responses: This setting prevents your community gadgets from replying to messages despatched to a normal broadcast deal with. It’s like stopping your mailbox from accepting mail addressed to “Everybody on This Road.”
- Fee restrict ICMP site visitors: This helps you set a restrict on the variety of ICMP requests (pings) your community can obtain inside a selected timeframe. Consider it like having a safety guard at your mailbox who solely permits a specific amount of mail per hour.
- Make use of community firewalls: Firewalls act as safety guards to your community site visitors. You possibly can configure them to establish and block suspicious ICMP site visitors patterns which may point out a Smurf assault.
- Configure anti-spoofing guidelines: These guidelines stop gadgets in your community from disguising their IP addresses as another person’s. It’s like requiring everybody sending mail to make use of their actual deal with, making it tougher for attackers to spoof the sufferer’s IP.
- Maintain community gadgets up to date: Outdated software program can have vulnerabilities that attackers exploit. Recurrently updating your router and different community gadgets ensures they’ve the most recent safety patches to defend towards recognized assault strategies.
In case your present router is an older mannequin, we advocate investing in a brand new one since newer fashions often include the above configurations already in place by default. As well as, think about using antivirus and anti-malware options to safe your firewalls and add an additional layer of safety to your community.
As with most cyberattacks, prevention is commonly the most effective technique for defense. Whereas Smurf assaults are nothing new, they continue to be a frequent tactic amongst cybercriminals trying to exploit susceptible networks. To additional defend your self from every kind of cyberattacks, take into account putting in a trusted antivirus software program program to maintain all of your gadgets safe.
Smurf Assault FAQ
Now that questions like how a Smurf assault operates and why we name it a Smurf assault are clear, let’s reply some extra often requested questions in regards to the assault that can assist you defend your self from them.
What’s the Distinction Between a Smurf Assault and a DDoS Assault?
A DDoS assault goals to stop victims from accessing their community by flooding it with pretend data requests. A Smurf assault is a type of a DDoS assault that renders a sufferer’s community inoperable in an analogous approach, however the distinction is that it does so by exploiting IP and ICMP vulnerabilities. Exploiting these vulnerabilities is what units a Smurf assault aside, in flip growing the potential for injury.
What’s the Distinction Between a Smurf Assault and a Fraggle Assault?
Each a Fraggle assault and a Smurf assault are types of a DDoS assault that purpose to flood a sufferer’s system with pretend data requests. The distinction is that whereas a Smurf assault makes use of spoofed ICMP packets, a Fraggle assault makes use of spoofed Person Datagram Protocol (UDP) site visitors to realize the identical purpose. All the pieces else about these assaults is identical.
What Is a Smurf Assault Amplifier?
A Smurf assault amplifier is a part of Smurf assaults that will increase their injury potential. The amplification issue correlates to the variety of hosts on the sufferer’s IP broadcast community.
For instance, an IP broadcast community with 300 hosts will yield 300 responses for each pretend ICMP echo request. This permits an attacker with low bandwidth to efficiently disable a sufferer’s system, even when that system has a a lot greater bandwidth. Smurf amplifiers may be deployed so long as the attacker maintains a connection and the amplifiers are broadcasting the ICMP site visitors.



