
What Is a Man-in-the-Center (MITM) Assault?
A person-in-the-middle (MITM) assault intercepts communication or knowledge switch, both by eavesdropping or impersonating a participant, permitting attackers to quietly hijack info with out the sufferer’s data.
On this seemingly innocent setting, hackers can intercept your knowledge because it travels between your machine and the web, probably accessing your delicate info like login credentials with out your data.
Understanding MITM assaults is essential for safeguarding your self on-line, because it empowers you to acknowledge and mitigate these threats, guaranteeing your privateness and safety in an more and more related world.
What Is a Man-in-the-Center (MITM) Assault?
A MITM assault is a sort of cyberattack the place attackers intercept an current dialog or knowledge switch, both by eavesdropping or by pretending to be a legit participant. To the sufferer, it would seem as if a normal trade of knowledge is underway — however by inserting themselves into the “center” of the dialog or knowledge switch, the attacker can quietly hijack info.

The aim of a MITM spoofing assault is to retrieve confidential knowledge corresponding to checking account particulars, bank card numbers or login credentials, which can be used to hold out additional crimes like identification theft or unlawful fund transfers. As a result of MITM assaults are carried out in actual time, they typically go undetected till it’s too late.
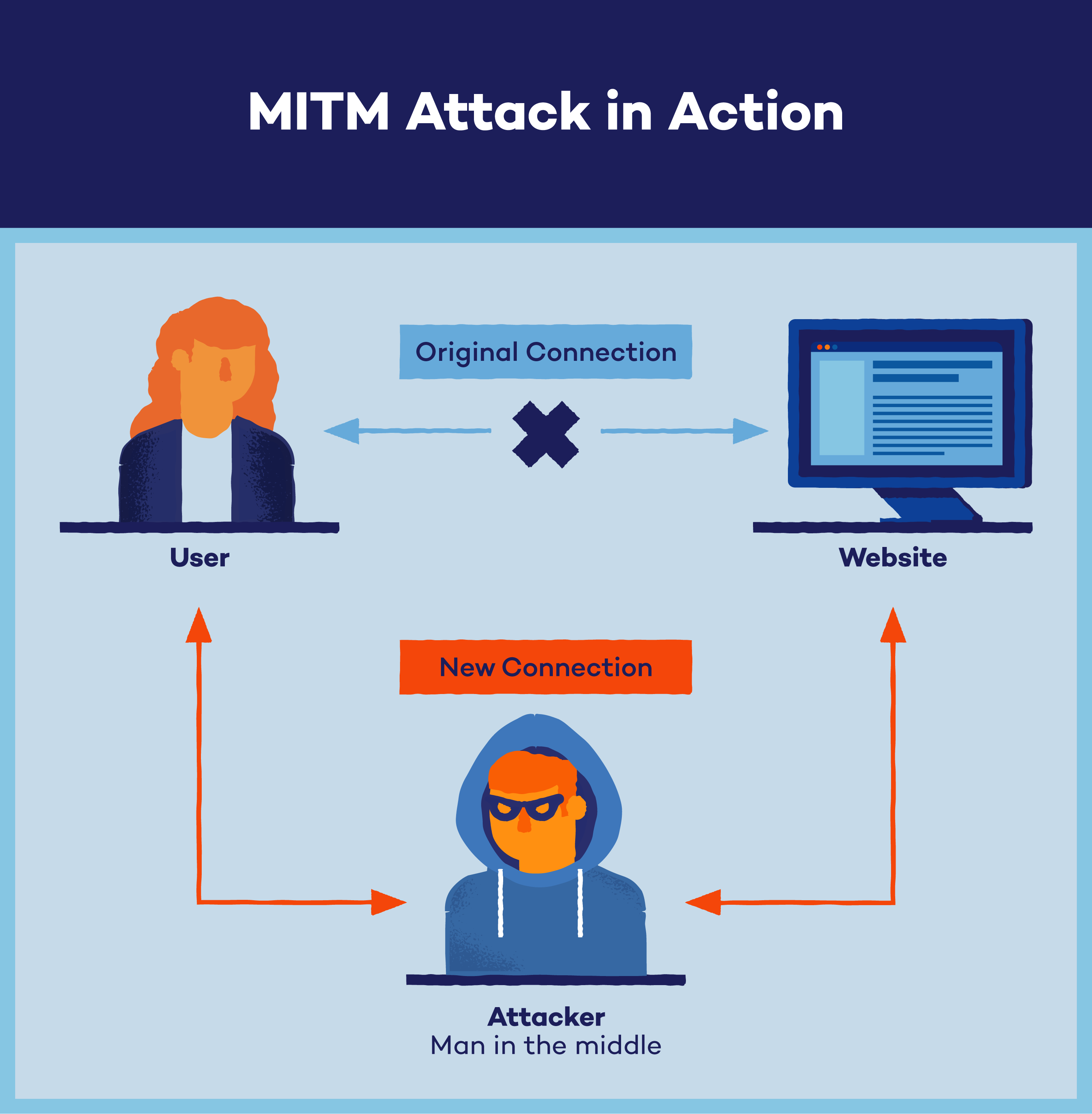
How Does a MITM Assault Work?
Right here’s a simplified breakdown of how a MITM assault works in three steps:
- Interception: The attacker units up a faux Wi-Fi hotspot in a public house, typically with out requiring a password. When a sufferer connects to this hotspot, the attacker can intercept any on-line knowledge exchanges, corresponding to emails and web site logins.
- Positioning between sufferer and vacation spot: The attacker makes use of methods like IP spoofing, the place they alter IP packets to impersonate the sufferer’s pc system and redirect the sufferer to the attacker’s web site.
- Decryption: By methods like HTTPS spoofing, SSL hijacking and SSL stripping, the hacker decrypts the intercepted knowledge, making the sufferer’s exercise seen to the attacker.
Actual-World Instance
The Lapsus$ focusing on Workplace 365 incident in 2022 highlights how attackers can mix MITM methods with social engineering. By spoofing the Workplace 365 login web page, Lapsus$ group stole person credentials and bypassed multi-factor authentication (MFA) to entry e mail accounts.
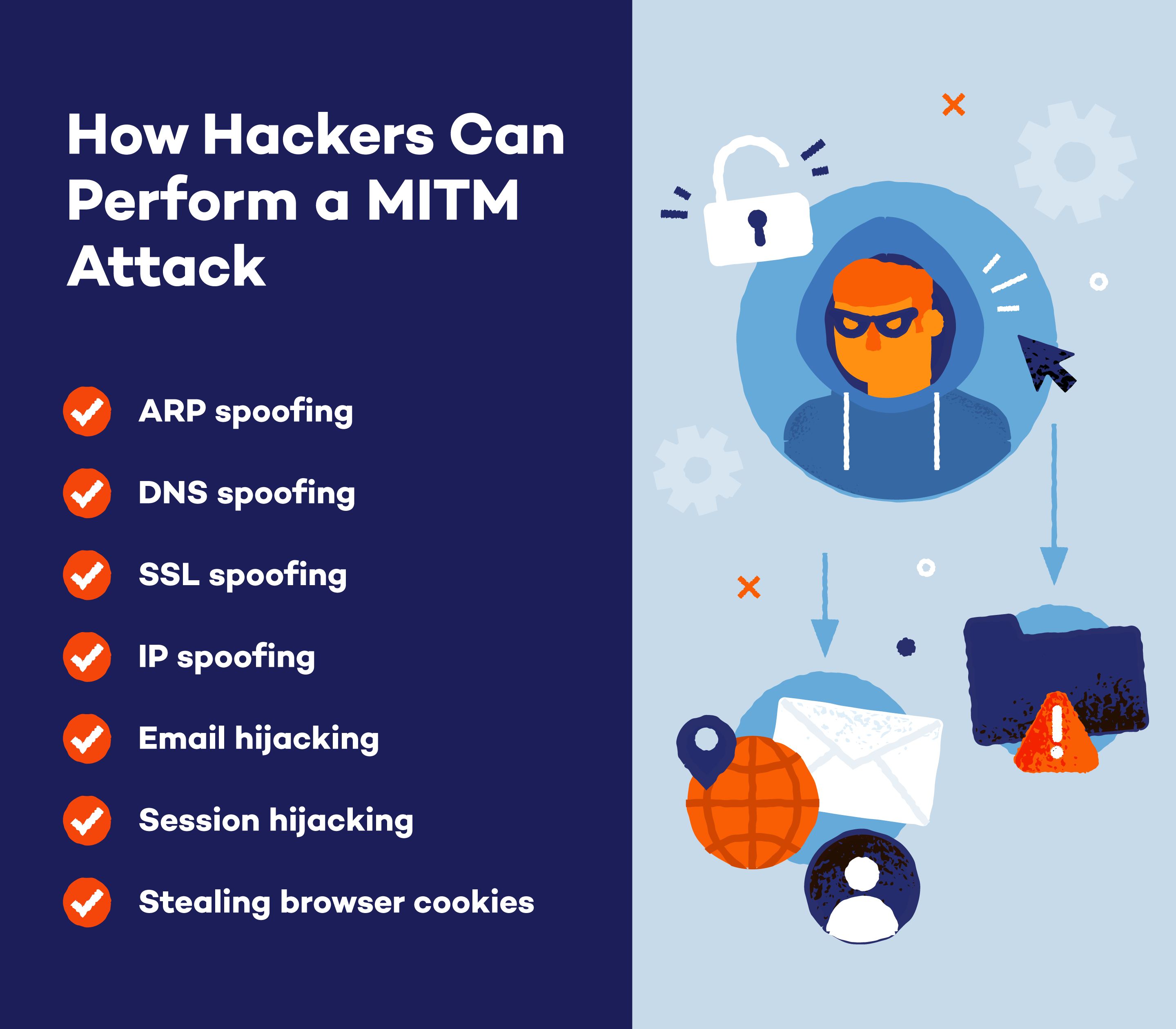
Forms of MITM Assaults
Hackers use numerous methods to hold out man-in-the-middle assaults, aiming to intercept and manipulate communication between two events. Listed here are some widespread forms of MITM assaults:
ARP Spoofing
ARP spoofing is a way utilized by attackers to intercept and manipulate knowledge packets in a community. By sending falsified Handle Decision Protocol (ARP) messages, the attacker hyperlinks their very own MAC tackle to the IP tackle of the sufferer’s machine, tricking the community into sending knowledge packets to the attacker as an alternative of the meant recipient. This permits the attacker to snoop on communication, modify knowledge or launch additional assaults on the community.
DNS Spoofing
DNS spoofing, or DNS cache poisoning, is a kind of man-in-the-middle assault the place an attacker alters the knowledge in a Area Identify System (DNS) server to redirect customers to malicious web sites. By tampering with the DNS information, the attacker can deceive customers into visiting faux web sites that intently resemble legit ones.
SSL Stripping
SSL stripping is a way attackers use in MITM assaults to downgrade a sufferer’s safe HTTPS connection to an unsecure HTTP connection.
By intercepting the communication between the sufferer and the web site, the attacker removes the encryption layer (SSL/TLS) from the connection. This makes the sufferer’s exercise seen to the attacker in plain, unencrypted textual content, permitting them to seize delicate info corresponding to login credentials, monetary particulars and private knowledge exchanged between the sufferer and the web site.
IP Spoofing
IP spoofing is a way wherein attackers manipulate IP packets to impersonate the sufferer’s pc system, redirecting them to malicious web sites.
By altering the supply IP tackle within the packets, attackers make it seem as if the info is coming from a trusted supply, fooling programs into accepting and processing it. This permits attackers to intercept and manipulate communication between the sufferer and the meant vacation spot, resulting in potential knowledge theft or unauthorized entry.
E-mail Hijacking
E-mail hijacking happens when an attacker good points unauthorized entry to somebody’s e mail account, typically via phishing or malware, and takes management of it with out the proprietor’s data. As soon as hijacked, the attacker can learn, ship, and delete emails, in addition to entry any linked accounts or delicate info contained inside emails. E-mail hijacking can result in privateness breaches, monetary fraud and even identification theft.
Stealing Browser Cookies
Stealing browser cookies entails attackers intercepting and acquiring the cookies saved on a sufferer’s internet browser with out their data.
These cookies include info corresponding to login credentials, session tokens and shopping historical past, which the attacker can exploit to achieve unauthorized entry to the sufferer’s accounts, monitor their on-line actions or impersonate them on web sites.
Session Hijacking
Session hijacking is a kind of cyberattack the place an attacker intercepts and takes over an ongoing session between a person and a web site or service.
This usually happens by stealing the session ID or token used to authenticate the person’s session, permitting the attacker to impersonate the person and achieve unauthorized entry to their account or knowledge. As soon as hijacked, the attacker can carry out actions on behalf of the person, corresponding to making transactions, sending messages or accessing delicate info.
The right way to Detect a MITM Assault: 5 Indicators
Detecting a MITM assault may be difficult, however there are a number of indicators to look at for:
- Sudden HTTPS warnings: In case your browser reveals warnings about invalid or suspicious HTTPS certificates, it could possibly be an indication that somebody is making an attempt to intercept your connection.
- Uncommon community exercise: An sudden spike in community exercise, sluggish web pace or frequent disconnections can point out a doable MITM assault.
- Unusual URLs or web site conduct: For those who discover odd URLs within the tackle bar, uncommon redirects or web sites that look barely totally different than common, it could possibly be an indication that site visitors is being manipulated.
- Repeated login prompts: Being repeatedly requested to log in to web sites, particularly people who usually hold you logged in, can point out that somebody is making an attempt to seize your login credentials.
- Unrecognized units in your community: Discovering unknown units related to your community generally is a signal that an unauthorized person has accessed your community, probably facilitating a MITM assault.
For those who’re not actively looking for indicators that your on-line communications have been intercepted or compromised, detecting a man-in-the-middle assault may be tough. Whereas it’s straightforward for them to go unnoticed, there are specific issues it is best to take note of if you’re shopping the net — primarily the URL in your tackle bar.
Right here is how one can test if the web site is safe:
- The signal of a safe web site is denoted by “HTTPS” in a web site’s URL.
- If a URL is lacking the “S” and reads as “HTTP,” it’s an instantaneous pink flag that your connection will not be safe.
- You also needs to search for an SSL lock icon to the left of the URL, which denotes a safe web site.

Man-in-the-Center Assault Prevention
Whereas being conscious of easy methods to detect a possible MITM assault is essential, one of the simplest ways to guard in opposition to them is by stopping them within the first place. Remember to observe these greatest practices:
- Keep away from Wi-Fi networks that aren’t password-protected, and by no means use a public Wi-Fi community for delicate transactions that require your private info.
- Use a digital personal community (VPN) — particularly when connecting to the web in a public place. VPNs encrypt your on-line exercise and stop an attacker from having the ability to learn your personal knowledge, like passwords or checking account info.
- Sign off of delicate web sites (like a web-based banking web site) as quickly as you’re completed to keep away from session hijacking.
- Preserve correct password habits, corresponding to by no means reusing passwords for various accounts, and use a password supervisor to make sure your passwords are as sturdy as doable.
- Use multi-factor authentication for your whole passwords.
- Use a firewall to make sure protected web connections.
- Use antivirus software program to guard your units from malware.
As our digitally related world continues to evolve, so does the complexity of cybercrime and the exploitation of safety vulnerabilities. Taking care to coach your self on cybersecurity greatest practices is vital to the protection of man-in-the-middle assaults and different forms of cybercrime. On the very least, being outfitted with a sturdy antivirus software program goes a great distance in holding your knowledge protected and safe.


