A few yr in the past, UnitedHealth Group, the U.S. health-insurance big, was focused in one of many largest ransomware assaults ever. It had such far-reaching, extreme penalties that new particulars concerning the assault and its aftermath have continued to emerge because the incident. To mark its anniversary, we’ve compiled a abstract of all the information out there in the present day.
The ransomware assault on UnitedHealth Group
Earlier than we proceed, let’s briefly introduce this group to these unfamiliar with it. With a capitalization of roughly $500 billion, UnitedHealth Group is the most important firm within the U.S. marketplace for medical insurance and healthcare providers. It ranks ninth globally by way of income — proper after Apple.
UnitedHealth Group includes two corporations. Certainly one of them, UnitedHealthcare, focuses on medical insurance. The opposite, Optum, makes a speciality of delivering a broad spectrum of healthcare providers starting from prescription drugs and direct medical care to the IT methods underlying healthcare operations.
Optum Perception, certainly one of Optum’s three divisions (and essentially the most worthwhile), handles the latter. Within the fall of 2022, UnitedHealth Group acquired the Change Healthcare platform, and Optum Perception built-in it. This digital platform processes insurance coverage claims — appearing as a monetary middleman between sufferers, healthcare suppliers, and insurers.
Change Healthcare was the goal of the assault. On February 21, 2024, its methods have been contaminated with ransomware — rendering the platform inaccessible. The incident wreaked havoc on the U.S. healthcare system, leaving many sufferers to shoulder the monetary burden of medical bills as insurance coverage claims couldn’t be processed rapidly. Healthcare suppliers have been compelled to course of payments manually.
Recovering the compromised methods took a number of months. For example, the Change Healthcare clearing service didn’t resume full operations till November. UnitedHealth Group even arrange a devoted web site to trace the restoration efforts. Even now, a yr after the assault, the corporate continues to be recurrently publishing updates on the web site, and a few methods are nonetheless listed as solely “partially out there”.
Timeline of the assault on UnitedHealth Group
Just a few months after the incident, on Might 1, the CEO of UnitedHealth Group, Andrew Witty, was summoned to testify earlier than Congress. From that testimony, most people was lastly capable of find out about how the assault on the corporate unfolded.
In line with Witty, the assault started on February 12. The attackers used compromised credentials to realize entry to the Change Healthcare Citrix portal, which was used for distant desktop connections. Two-factor authentication ought to have stopped them however… it wasn’t enabled. Thus, attackers have been capable of acquire entry just by utilizing the compromised credentials.
After gaining preliminary entry, they started to maneuver laterally and harvest information. The attackers clearly managed to gather a considerable quantity of precious information throughout the following 9 days. In any case, on February 21, they deployed ransomware — initiating the encryption of Change Healthcare’s methods.
Confronted with this case, UnitedHealth determined to disconnect Change Healthcare information facilities from the community to include the ransomware assault.
Witty argued that the choice successfully prevented the an infection from spreading to Optum, UnitedHealthcare, UnitedHealth Group, and any exterior organizations. Nonetheless, the entire shutdown of a crucial digital platform had a devastating impression on each UnitedHealth Group’s enterprise operations and the broader U.S. healthcare system as a complete.
Thus, essentially the most intensive ransomware assault of 2024 was attributable to the absence of two-factor authentication on a distant desktop entry portal — exactly the place the place it completely ought to have been enabled. As Oregon Senator, Ron Wyden, summarized, “This hack may have been stopped with cybersecurity 101”.
UnitedHealth Group pays up
A number of days after the breach, the BlackCat/ALPHV cybercrime gang claimed accountability for it. The attackers claimed to have exfiltrated 6TB of confidential information — together with medical data, monetary paperwork, and private info belonging to U.S. civilians and navy personnel, amongst different delicate info.
In March 2024, UnitedHealth Group paid a ransom of $22 million to the gang. However the story didn’t finish there: after receiving the ransom, ALPHV feigned having their infrastructure seized by the FBI once more. This was doubtless a ploy to double-cross certainly one of their associates — pocketing the funds and disappearing into the ether.
Stated affiliate claimed ALPHV had failed to offer them their lower, and later teamed up with one other ransomware gang — RansomHub. That gang made among the stolen information public in April 2024, after which tried to extort extra money from UnitedHealth.
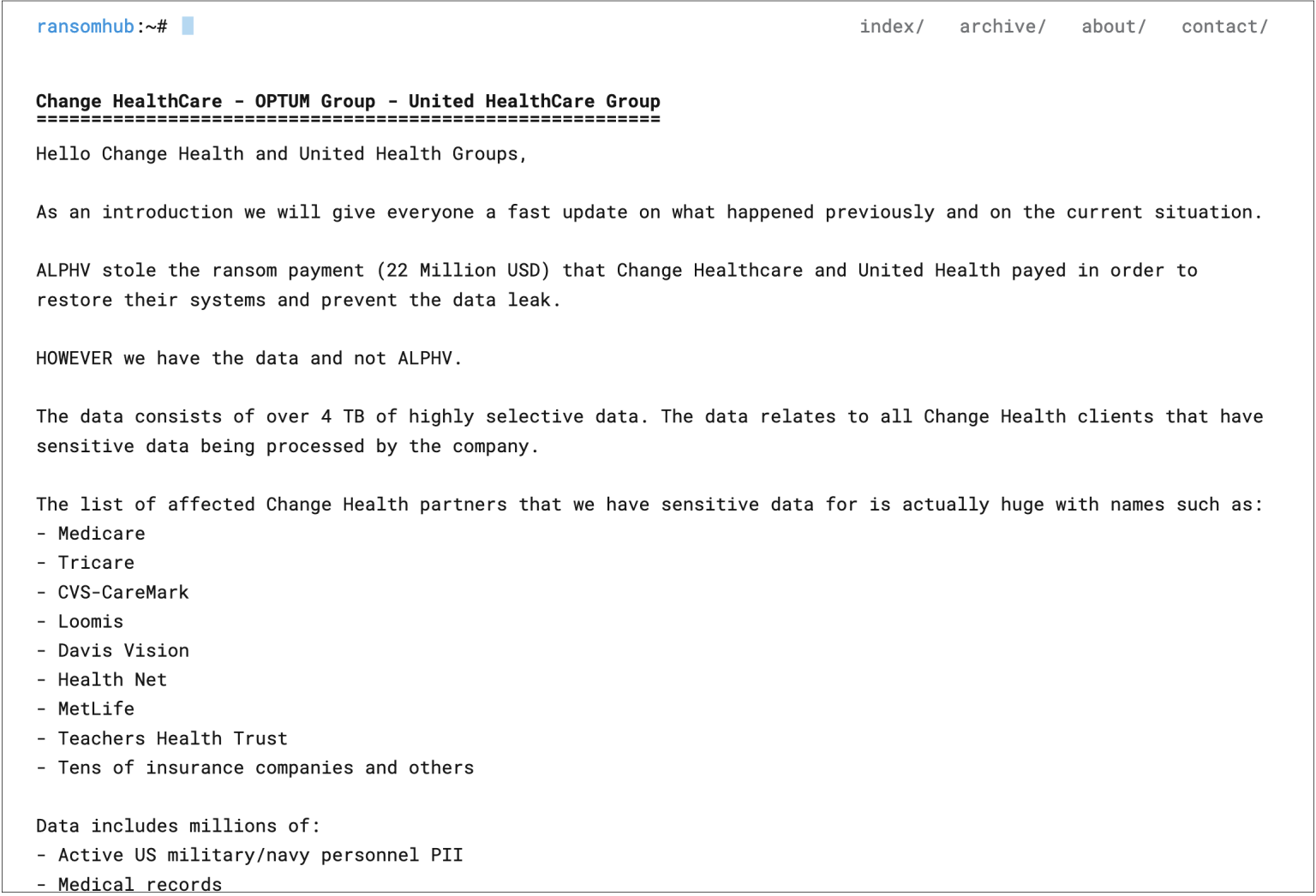
Submit by RansomHub demanding a second ransom from UnitedHealth Group. Supply
It stays unclear whether or not UnitedHealth ever paid the second ransom, as there was no official affirmation. Nonetheless, the demand was later faraway from RansomHub’s web site, and no additional leaks of the stolen firm information have been noticed. Due to this fact, it may be assumed that the corporate did, in reality, pay twice. That is much more doubtless if one considers that the ransom quantities are dwarfed by the huge monetary impression the assault had on UnitedHealth Group.
The aftermath of the ransomware assault on UnitedHealth Group
UnitedHealth Group posted $872 million in losses related to the cyberattack in Q1 2024 alone. The corporate additionally estimated in its Q1 report that the annual value of the breach may attain $1.35 to $1.6 billion.
These preliminary estimates proved to be far too optimistic: predicted injury saved rising quarter after quarter, first rising to $2.3 to $2.45 billion, after which to $2.87 billion.
By the tip of the fiscal yr, as reported by UnitedHealth Group in January 2025, the incident resulted in a whole annual lack of $3.09 billion. Though the injury estimate for 2024 is now finalized, the entire injury may nonetheless enhance considerably as the corporate continues to cope with the results of the assault.
An official estimate of the variety of people whose information may have been stolen by the cybercriminals took a very long time to materialize. It was solely eight months after the incident, on October 24, 2024, that UnitedHealth Group lastly got here up with a tally. It was a mind-boggling determine: 100 million, or practically a 3rd of your entire inhabitants of the USA.
Nonetheless, it will change into evident that these estimations have been as overly hopeful as the unique predictions concerning the monetary losses. Three months later, on the finish of January 2025, UnitedHealth Group launched an up to date report that put the variety of these impacted by the breach at 190 million.
Defending your organization towards ransomware
Clearly, the obvious lesson to be discovered from the UnitedHealth Group breach is that two-factor authentication is a should for any public-facing service. In any other case, a single compromised password may trigger huge issues and billions of {dollars} in losses.
Important as it’s, two-factor authentication is under no circumstances adequate safety towards ransomware. Defending company infrastructure from ransomware assaults should be multilayered. Listed here are some further suggestions:



