For those who’re an energetic cryptocurrency consumer however you’re nonetheless downloading torrent recordsdata and aren’t positive how you can safely retailer your seed phrases, we’ve some unhealthy information for you. We’ve found a brand new Trojan, Efimer, that replaces crypto pockets addresses proper in your clipboard. One click on is all it takes to your cash to finish up in a hacker’s pockets.
Right here’s what you might want to do to maintain your crypto secure.
How Efimer spreads
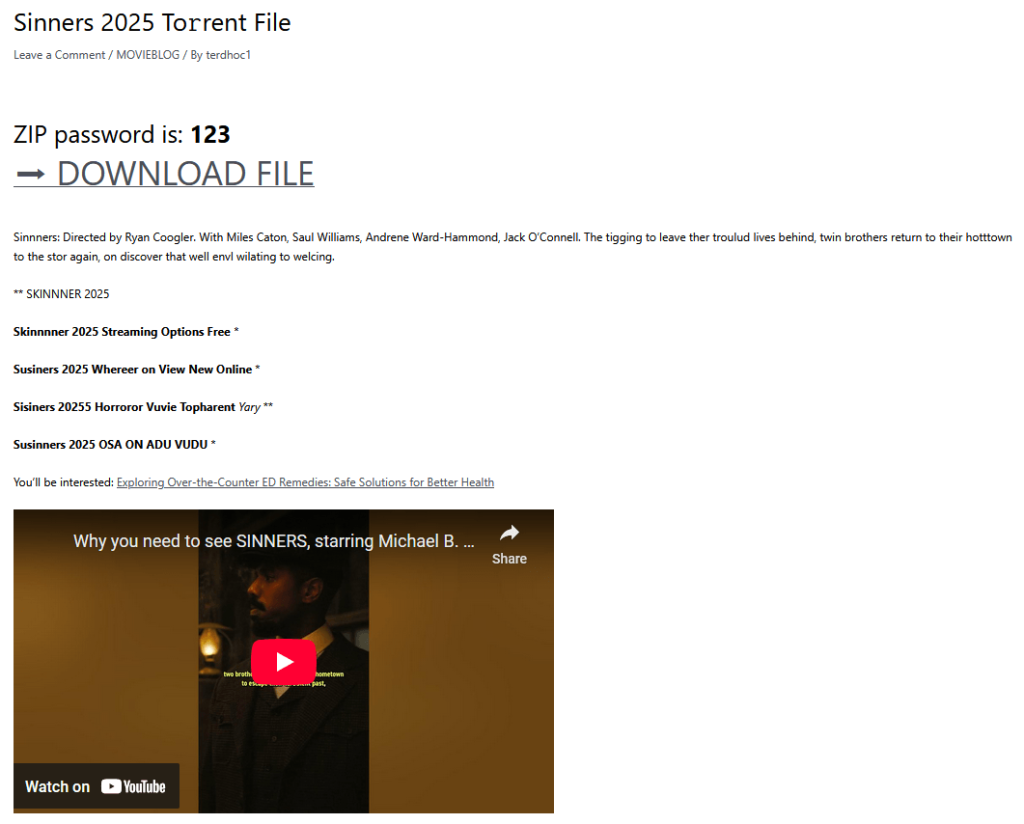
Certainly one of Efimer’s predominant distribution channels is WordPress web sites. It doesn’t assist that WordPress is a free content-management system for web sites — or that it’s the world’s hottest. Everybody from small-time bloggers and companies to main media shops and companies makes use of it. Scammers exploit poorly secured websites and publish posts with contaminated torrent recordsdata.
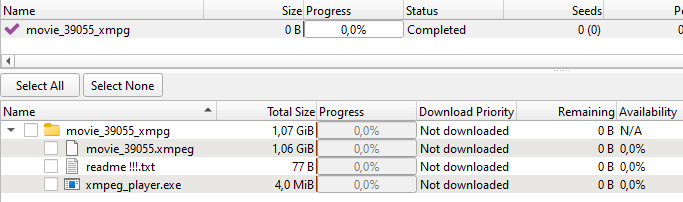
When a consumer downloads a torrent file from an contaminated web site, they get a small folder that comprises what appears to be like like a film file with the .xmpeg extension. You’ll be able to’t open a file in that format and not using a “particular media participant”, which is conveniently included within the folder. In actuality, the “participant” is a Trojan installer.
Not too long ago, Efimer has additionally began spreading by phishing emails. Web site and area homeowners obtain emails, purportedly from attorneys, falsely claiming copyright infringement and demanding content material elimination. The emails say all the small print are within the attachment… which is definitely the place the Trojan is lurking. Even in case you don’t personal a web site your self, you’ll be able to nonetheless obtain spam e mail messages with Efimer connected. Menace actors gather consumer e mail addresses from WordPress websites they’ve beforehand compromised. So, in case you get an e mail like this, no matter you — don’t open the attachment.
How Efimer steals your crypto
As soon as Efimer infects a tool, one in every of its scripts provides itself to the Home windows Defender exclusion record — supplied the consumer has administrator privileges. The malware then installs a Tor shopper to speak with its command-and-control server.
Efimer accesses the clipboard and searches for a seed phrase, which is a singular sequence of phrases that enables entry to a crypto pockets. The Trojan saves this phrase and sends it to the attackers’ server. If it additionally finds a crypto pockets deal with within the clipboard, Efimer discreetly swaps it out for a faux one. To keep away from elevating suspicion, the faux deal with is usually similar to the unique. The tip result’s that cryptocurrency is silently transferred to the cybercrooks.
Wallets containing Bitcoin, Ethereum, Monero, Tron, or Solana are primarily in danger, however homeowners of different cryptocurrencies shouldn’t let their guard down. The builders of Efimer commonly replace the malware by including new scripts and increasing help for extra crypto wallets. You could find out extra about Efimer’s capabilities in our evaluation on Securelist.
Who’s in danger?
The Trojan is attacking Home windows customers all around the world. At the moment the malware is most energetic in Brazil, Russia, India, Spain, Germany, and Italy, however the scope of those assaults may simply broaden to your nation, if it’s not already on the record. Customers of crypto wallets, homeowners of WordPress websites, and those that continuously obtain motion pictures, video games, and torrent recordsdata from the web ought to be particularly vigilant.
The way to shield your self from Efimer
The Efimer Trojan is an actual jack-of-all-trades. It’s able to stealing cryptocurrencies, swapping crypto wallets, and it poses a severe menace to each people and organizations. It could possibly use scripts to hack WordPress websites, and is ready to unfold by itself. Nonetheless, in each case, a tool can solely be contaminated if the potential sufferer downloads and opens a malicious file themselves. Which means that just a little vigilance and a wholesome dose of warning — ignoring recordsdata from suspicious sources on the very least — is your finest protection in opposition to Efimer.
Listed below are our suggestions for dwelling customers:
- Use a sturdy safety answer that may scan recordsdata for malware and warn you in opposition to opening phishing hyperlinks.
- Create distinctive and sturdy passwords. And no, storing them in your notes app isn’t a good suggestion. Be sure to use a password supervisor.
- Use two-factor authentication to sign up to crypto wallets and web sites.
- Keep away from downloading motion pictures or video games from unverified websites. Pirated content material is usually crawling with every kind of Trojans. Even in case you select to take that threat, pay shut consideration to the file extensions. A daily video file positively gained’t have an .exe or .xmpeg extension.
- Don’t retailer your seed phrases in plain textual content recordsdata. Belief a password supervisor. Learn this text to study extra about how you can shield your cryptocurrency property.
What different threats lurk within the crypto world: