The development of utilizing spearphishing methods in mass emails continues to realize momentum. We lately got here throughout a pattern electronic mail by which attackers used an entire field of comparatively refined spearphishing methods. Now, one may assume that use of such techniques for a “mere” mass phishing assault could be considerably OTT by way of effort on the attackers’ aspect; not so – it transpired on this case: the attackers nonetheless gave it a shot (although detailed evaluation reveals the assault was doomed from the beginning). In any case, it introduced us with a wonderful alternative to take a dive into the methods employed by phishers.
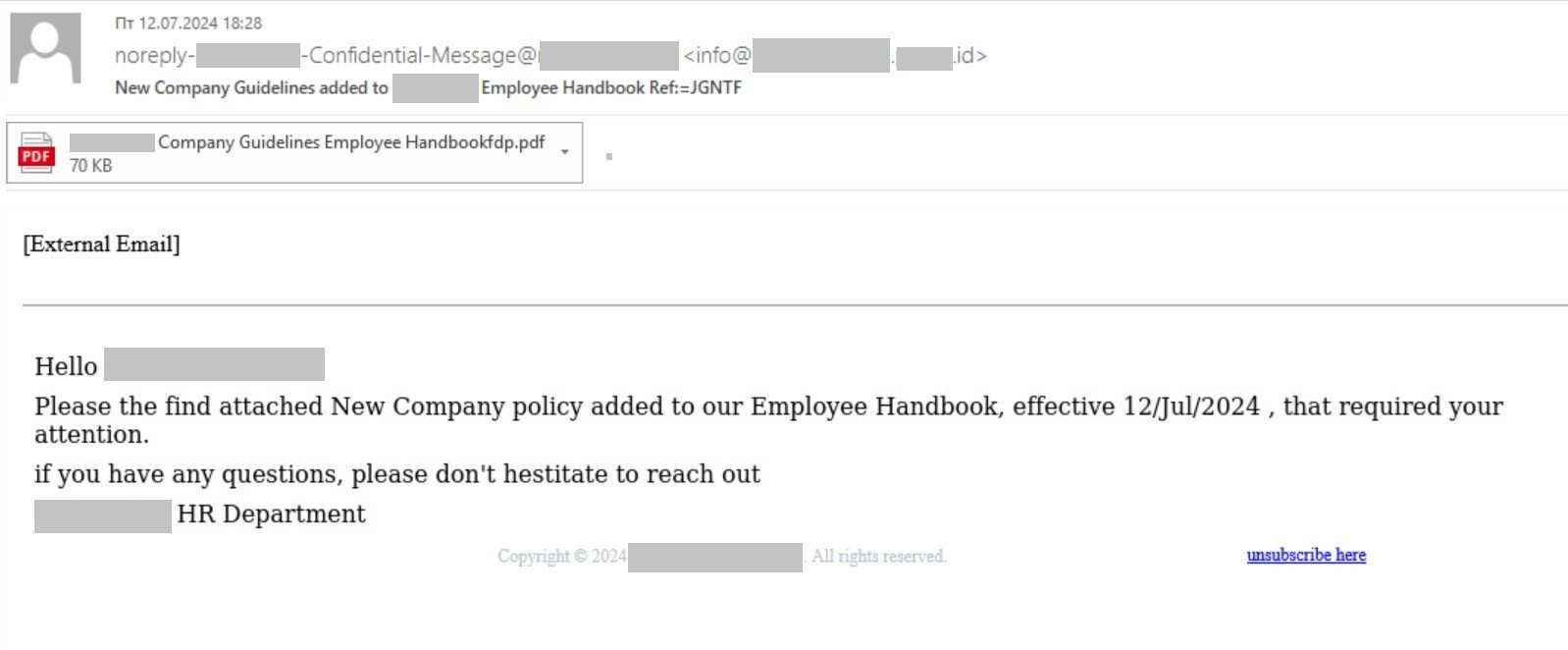
Electronic mail mimicking replace of company tips
Nearly all the things concerning the electronic mail is spot on. It’s addressed to a particular particular person inside a particular group, and makes use of ghost spoofing for the sender’s title — that’s, the “From” area shows a forgery of the reputable handle of the goal firm (which, in fact, has no relation to the handle within the “Reply To” area).
The e-mail is distributed via the infrastructure of a good advertising and marketing firm, elevating no purple flags with electronic mail filters. What’s extra, the title of this firm and the top-level area internet hosting its web site are intentionally chosen to lull the recipient’s vigilance — the web site’s based mostly in Indonesia, and the sufferer might effectively understand the “.id” area as an abbreviation for “identifier” slightly than a rustic code. Alongside the spoofed handle within the “From” area, it appears to be like convincing sufficient:
However that’s not all. Within the electronic mail physique there’s virtually zero textual content — solely a copyright line and an unsubscribe hyperlink (each of which, because it occurs, are inserted by the mail engine of the reputable firm used to ship the message). All the pieces else, together with the recipient’s title, is a picture. That is to stop anti-phishing mechanisms from making use of text-based filtering guidelines.
An connected PDF file is used as a substitute of a direct phishing hyperlink for a similar cause. Web sites can simply be blacklisted and blocked on the mail-server stage. A PDF file, alternatively, seems as a totally reputable attachment.
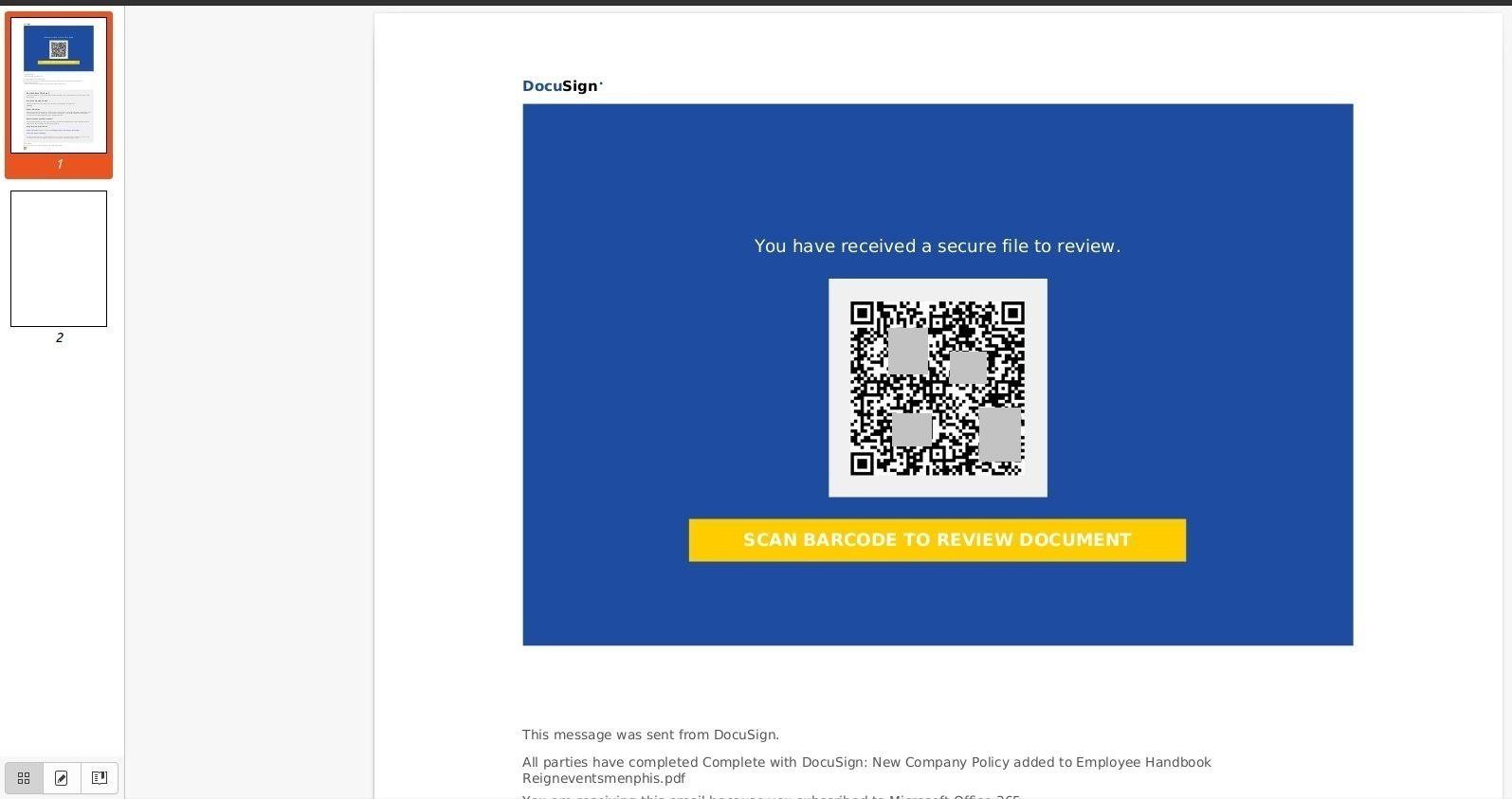
PDF attachment
In precise truth, attackers have lengthy been concealing hyperlinks in PDF information. Thus, in idea, safety software program ought to be capable of analyze a PDF — together with any textual content and hyperlinks inside. However the creators of this phishing marketing campaign have been smart to that as effectively. Their PDF technically has no textual content or hyperlinks in it in any respect. As an alternative, it presents one other picture that includes a QR code and embedded accompanying textual content.
As well as, the PDF mimics the interface of DocuSign, a widely known service used for digital doc administration. DocuSign does certainly help you ship paperwork for signing, and to trace their standing. However, in fact, it has nothing to do with PDF information housing a QR code.
At this level, it turns into painfully apparent that the attackers overcooked the assault. The sufferer receives what appears to be confidential company tips by electronic mail, however to learn them they should scan a QR code with a cell phone… — not precisely reasonable. Most workers received’t hassle — particularly in the event that they use their very own (non-corporate) telephone.
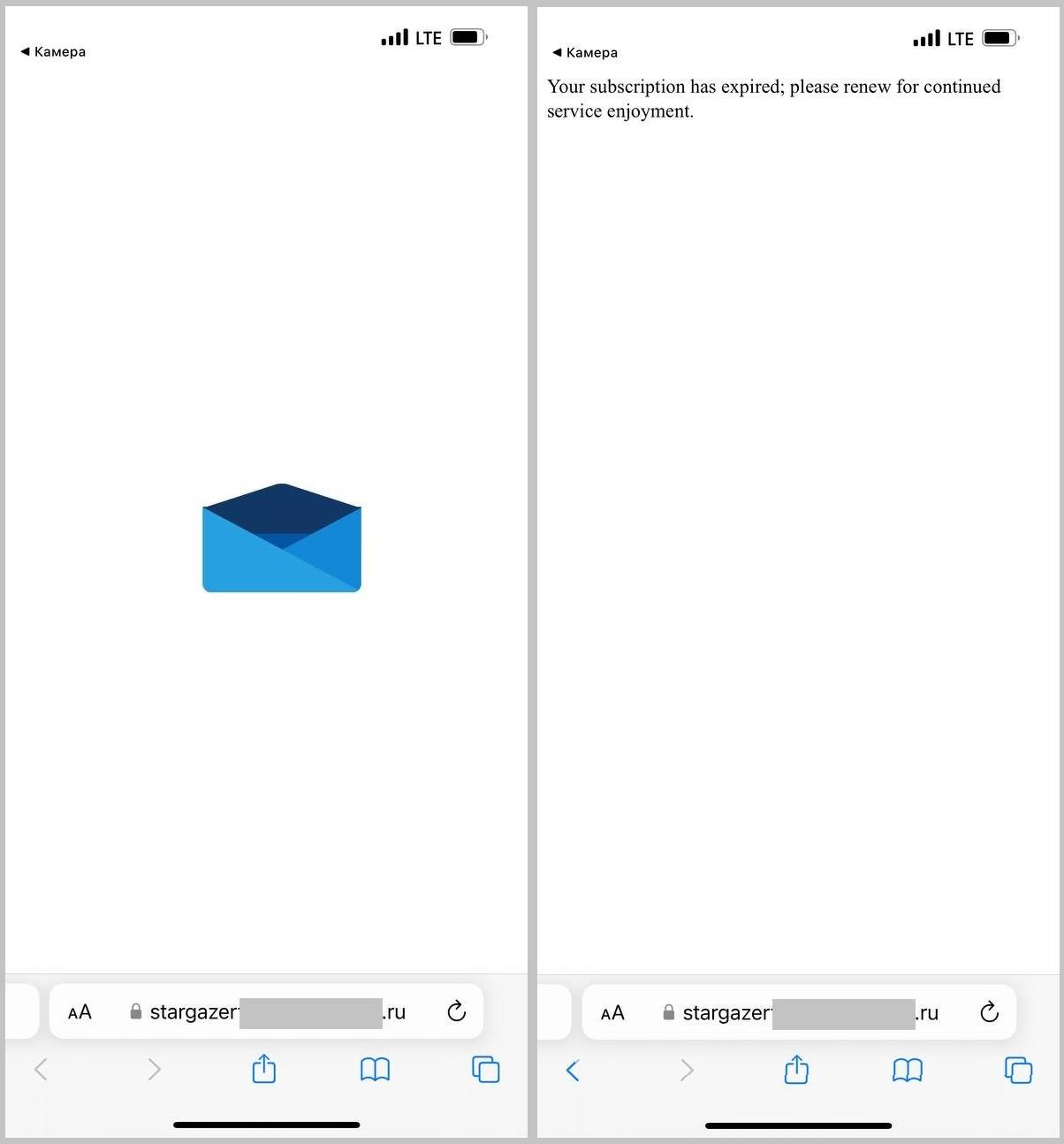
Epic fail: the phishing web site
So what occurs if the sufferer does pull out their telephone and scan the code? Nicely, for starters, they’ll be greeted by Cloudflare’s verification system and requested to show they’re human. Cloudflare is a reputable service to protect towards DDoS assaults, and cybercriminals wish to put their phishing pages behind it so as to add plausibility.
However after that it’s a catastrophe. The web site performs an animation of an envelope opening, then crashes with an error message.
It seems the attackers forgot to resume their subscription to the internet hosting companies. Perhaps the positioning had some extra kooky methods in retailer for the sufferer, however by the point the phishing emails have been being pumped out, it was already defunct.
Find out how to keep protected
To guard firm workers from phishing: