The ransomware group Interlock has began utilizing the ClickFix method to realize entry to its victims’ infrastructure. In a current publish, we mentioned the normal idea of ClickFix. At the moment we’ll take a look at a particular case the place a ransomware group has put this tactic into motion. Cybersecurity researchers have found that Interlock is utilizing a faux CAPTCHA imitating a Cloudflare-protected website on a web page posing as the web site of Superior IP Scanner — a well-liked free community scanning software. This means the assault is geared toward IT professionals working in organizations of potential curiosity to the group.
How Interlock is utilizing ClickFix to unfold malware
The Interlock attackers lure victims to a webpage with an URL mimicking that of the official Superior IP Scanner website. The researchers discovered a number of cases of this similar web page hosted at completely different addresses throughout the online.
When the consumer clicks the hyperlink, they see a message asking them to finish a CAPTCHA, seemingly offered by Cloudflare. The message states that Cloudflare helps firms “regain management of their know-how”. This legitimate-looking advertising textual content is in actual fact copied from Cloudflare’s personal What’s Cloudflare? webpage. It’s adopted by directions to press Win + R, then Ctrl + V, and eventually Enter. Subsequent come two buttons: Repair it and Retry.
Lastly, a message claims that the useful resource the sufferer is attempting to entry must confirm the connection’s safety.
In actuality, when the sufferer clicks Repair it, a malicious PowerShell command is copied to the clipboard. The consumer then unknowingly opens the command console with Win + R and pastes the command with Ctrl + V. Urgent Enter then executes the malicious command.
Executing the command downloads and launches a 36-megabyte faux PyInstaller installer file. And to distract the sufferer, a browser window with the actual Superior IP Scanner web site opens.
From knowledge assortment to extortion: the phases of an Interlock assault
As soon as the faux installer is launched, a PowerShell script is activated that collects system info and sends it to a C2 server. In response, the server can both ship the ooff command to terminate the script, or ship further malware. On this case the attackers used Interlock RAT (distant entry Trojan) because the payload. The malware is saved within the %AppData% folder and runs mechanically, permitting the attackers to entry confidential knowledge and set up persistence within the system.
After preliminary entry, the Interlock operators attempt to use beforehand stolen or leaked credentials and the Distant Desktop Protocol (RDP) for lateral motion. Their main goal is the area controller (DC) — getting access to it permits the attackers to unfold malware throughout the infrastructure.
The ultimate step earlier than launching the ransomware is to steal the sufferer group’s beneficial knowledge. These information are uploaded to Azure Blob Storage managed by the attackers. After exfiltrating the delicate knowledge, the Interlock group publishes it on a brand new Tor area. A hyperlink to this area is then offered in a brand new publish on the group’s .onion website.
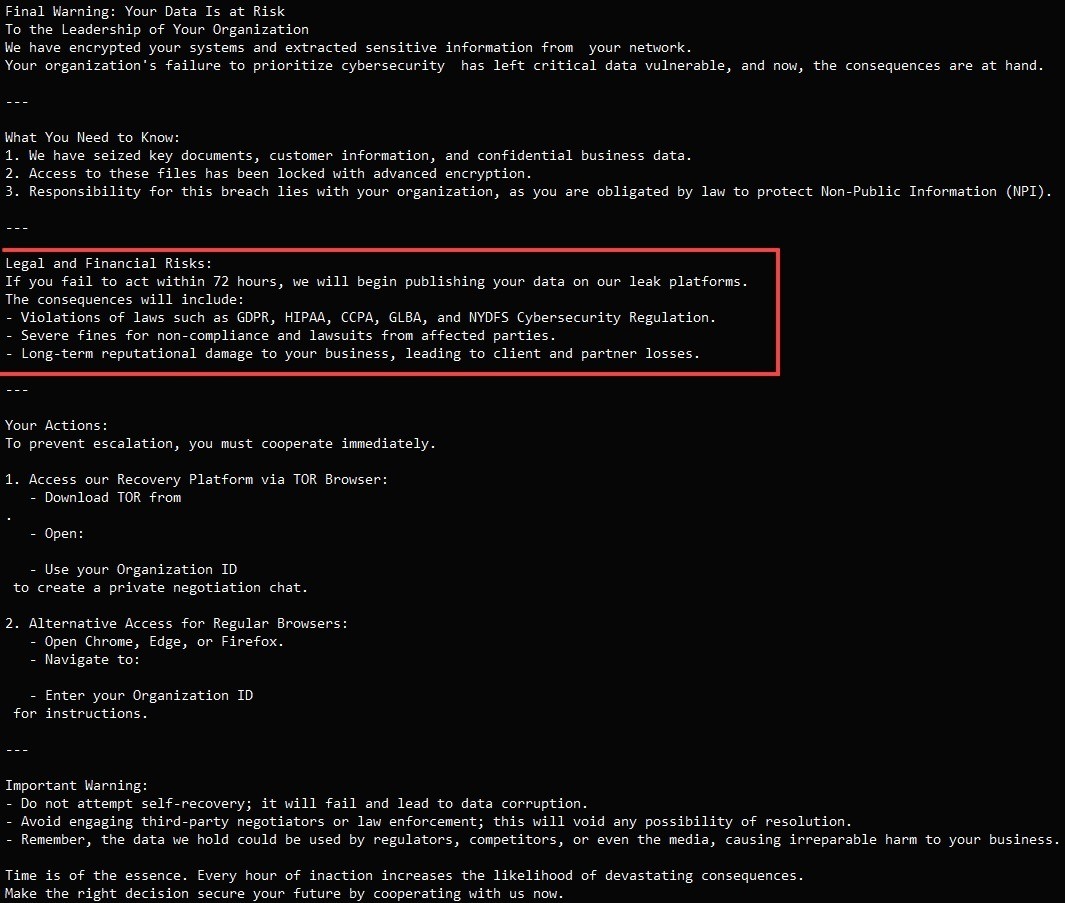
Instance of a ransom notice despatched by the Interlock ransomware group. Supply
Easy methods to defend towards ClickFix assaults
ClickFix and different comparable strategies rely closely on social engineering, so the perfect safety is a scientific strategy centered totally on elevating worker consciousness. To assist with this, we advocate our Kaspersky Automated Safety Consciousness Platform, which automates coaching packages for employees.
As well as, to guard towards ransomware assaults, we advocate the next:



