In September 2025, researchers at ETH Zurich (the Swiss Federal Institute of Expertise) revealed a paper introducing Phoenix, a modification of the Rowhammer assault that works on DDR5 reminiscence modules. The authors not solely demonstrated the brand new assault’s effectiveness towards 15 examined modules, but additionally proposed three sensible use instances: studying and writing information from reminiscence, stealing a non-public encryption key saved in reminiscence, and bypassing Linux’s sudo utility protections to escalate privileges.
The Rowhammer assault: a short historical past
To know this relatively complicated research, we have to first briefly revisit the historical past of Rowhammer. The Rowhammer assault was first described in a 2014 analysis paper. Again then, researchers from each Carnegie Mellon College and Intel confirmed how repeatedly accessing rows of reminiscence cells might trigger adjoining reminiscence cells to vary worth. These neighboring cells might comprise vital information — the alteration of which might have severe penalties (resembling privilege escalation).
This occurs as a result of every cell in a reminiscence chip is basically a capacitor: a easy part that may maintain {an electrical} cost for less than a short while. That’s why such reminiscence is unstable: flip off the pc or server, and the information disappears. For a similar cause the cost in cells have to be incessantly refreshed — even when nobody is accessing that reminiscence area.
Reminiscence cells aren’t remoted; they’re organized in rows and columns, interconnected in methods that may trigger interference. Accessing one row can have an effect on a neighboring row; for instance, refreshing one row can corrupt information in one other. For years, this impact was solely recognized to reminiscence producers — who tried their finest to mitigate it as a way to enhance reliability. However as cells grew to become smaller and subsequently packed extra tightly collectively, the “row hammering” impact grew to become exploitable in real-world assaults.
After the Rowhammer assault was demonstrated, reminiscence builders started to introduce defenses, leading to Goal Row Refresh (TRR) {hardware} know-how. In idea, TRR is easy: it screens aggressive entry to rows and, if detected, forcibly refreshes adjoining rows. In apply, it wasn’t so efficient. In 2021, researchers described the Blacksmith assault, which bypassed TRR by utilizing extra refined memory-cell entry patterns.
Builders tailored once more — including much more superior defenses towards Rowhammer-like assaults in DDR5 modules and rising the enforced refresh charge. To additional impede new assaults, producers averted disclosing which countermeasures have been in place. This led many to imagine that DDR5 had successfully solved the Rowhammer drawback. Nonetheless, simply final 12 months, researchers from the identical ETH Zurich managed to efficiently assault DDR5 modules — albeit below sure circumstances: the reminiscence needed to be paired with AMD Zen 2 or Zen 3 CPUs, and, even then, some modules remained unaffected.
Options of the brand new assault
To develop Phoenix, the researchers reverse-engineered the TRR mechanism. They analyzed its habits below numerous reminiscence row entry patterns and checked whether or not the safety triggered for adjoining rows. It turned out that TRR has change into considerably extra complicated, and beforehand recognized entry patterns now not work — the safety now accurately flags these patterns as doubtlessly harmful and forcibly refreshes adjoining rows. Consequently, the researchers found that after 128 TRR-tracked reminiscence accesses, a “window of alternative” of 64 accesses seems, throughout which defenses are weaker. It’s not that the safety system utterly fails, however its responses are inadequate to stop a price change in a focused reminiscence cell. The second window presents itself after accessing reminiscence cells over the course of 2608 refresh intervals.
The researchers then studied these weak factors intimately to ship a extremely focused strike on reminiscence cells whereas knocking out the defenses. Put merely, the assault works like this: malicious code performs a collection of dummy accesses that successfully lull the TRR mechanism right into a false sense of safety. Then the lively section of the assault happens, which finally modifies the goal cell worth. Consequently, the workforce confirmed that the assault reliably labored towards all 15 examined DDR5 modules manufactured by SK Hynix, one of many market leaders.
Three real-world assault situations
A practical assault should change a price in a exactly outlined reminiscence area — a troublesome process. Firstly, an attacker wants detailed information of the goal software program. They need to bypass a number of typical safety controls, and lacking the goal by only one or two bits may end up in a system crash as a substitute of a profitable hack.
The Swiss researchers got down to show that Phoenix could possibly be used to trigger real-world harm. They evaluated three assault situations. The primary (PTE) concerned accessing the web page desk to create circumstances for arbitrary studying/writing of RAM information. The second (RSA) aimed to steal an RSA-2048 non-public encryption key from reminiscence. The third (sudo) concerned bypassing the protections of the usual Linux sudo utility with the purpose of privilege escalation. The research’s closing outcomes are proven on this desk:
[phoenix-rowhammer-attack-results.jpg]
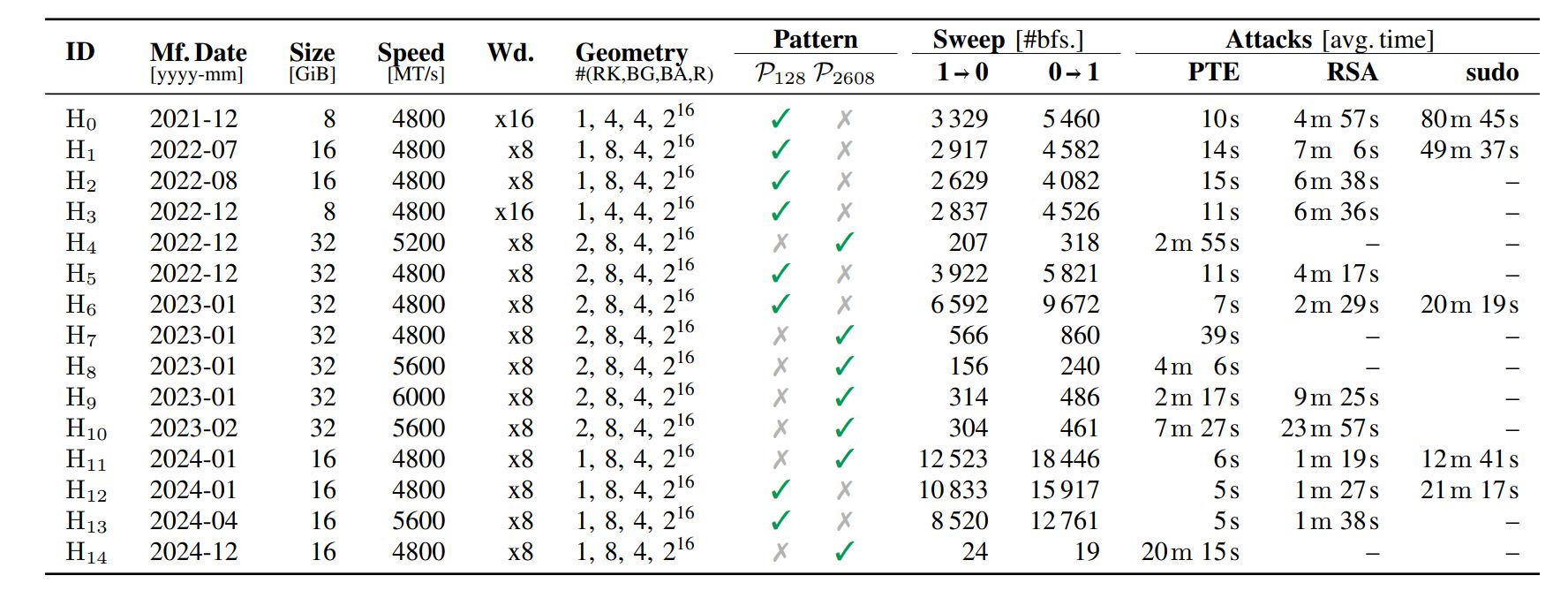
Phoenix assault effectiveness. Supply
For some modules, the primary assault variant (128 refresh intervals) was efficient, whereas for others solely the second (2608 intervals) technique labored. In some experiments the RSA key theft and sudo exploits didn’t succeed. Nonetheless, a technique for arbitrary reminiscence learn/write was discovered for all modules, and the exploitation time was comparatively brief for this class of assaults — from about 5 seconds as much as seven minutes. That’s sufficient to display that Rowhammer assaults pose an actual threat, albeit in a extremely constrained set of situations.
Relevance and countermeasures
The Phoenix assault exhibits that Rowhammer-style assaults may be carried out towards DDR5 modules simply as successfully as on DDR4 and DDR3. Although modules from a simply single vendor have been examined and the researchers uncovered a reasonably easy weak spot in that vendor’s TRR algorithm that may almost definitely be straightforward to repair, this can be a important step ahead within the safety analysis of reminiscence modules.
The authors proposed a number of countermeasures towards Rowhammer-type assaults. First, lowering the enforced refresh interval throughout all cells can considerably impede the assault. This may increasingly enhance energy consumption and chip temperature, nevertheless it’s an easy resolution. Second, reminiscence with an error correction code (ECC) can be utilized. This complicates Rowhammer assaults, though — considerably paradoxically — it doesn’t make them utterly not possible.
Past these apparent measures, the authors point out two extra. The primary is the Effective Granularity Refresh safety technique, which is already being carried out. Constructed into the processor’s reminiscence controller, it modifies memory-cell refresh habits so as to withstand Rowhammer assaults. As for the second, the researchers urge memory-module and chip builders to cease counting on proprietary safety measures (“safety by way of obscurity”). As a substitute, they advocate adopting an strategy frequent in cryptography — the place safety algorithms are publicly accessible and topic to unbiased testing.



