Right here at Kaspersky Each day we’re without end urging readers of our weblog to be actual cautious when downloading content material to their gadgets. In spite of everything, even Google Play isn’t resistant to malware — not to mention unofficial sources with mods and hacked variations. For so long as the digital world retains turning, Trojans will proceed to worm their approach onto gadgets that don’t have dependable safety.
In the present day we inform the story of how 11 million Android customers worldwide fell sufferer to the Necro Trojan. Learn on to study which apps we discovered it in — and how one can defend your self.
What’s Necro
Our common readers could recall studying about Necro once we first wrote about it again in 2019. Again then, our consultants found a Trojan in CamScanner, a textual content recognition app, which had clocked up over 100 million downloads on Google Play. Now the “necromancers” have injected new blood into the previous Trojan: we discovered a model richer in options each in well-liked apps on Google Play and in numerous app mods on unofficial websites. Almost definitely, the builders of those apps used an unverified advert integration instrument by which Necro infiltrated the code.
In the present day’s Necro is a loader obfuscated to keep away from detection (however that didn’t cease us from discovering it). It downloads the malicious payload in no much less a artful approach utilizing steganography to cover its code in a seemingly innocent picture.
And downloaded malicious modules are capable of load and run any DEX recordsdata (compiled code written for Android), set up downloaded apps, tunnel by the sufferer’s machine, and even — probably — take out paid subscriptions. As well as, they will show and work together with advertisements in invisible home windows, in addition to open arbitrary hyperlinks and run any JavaScript code.
Learn extra about how Necro is designed and the way it operates on our Securelist weblog.
The place Necro hides
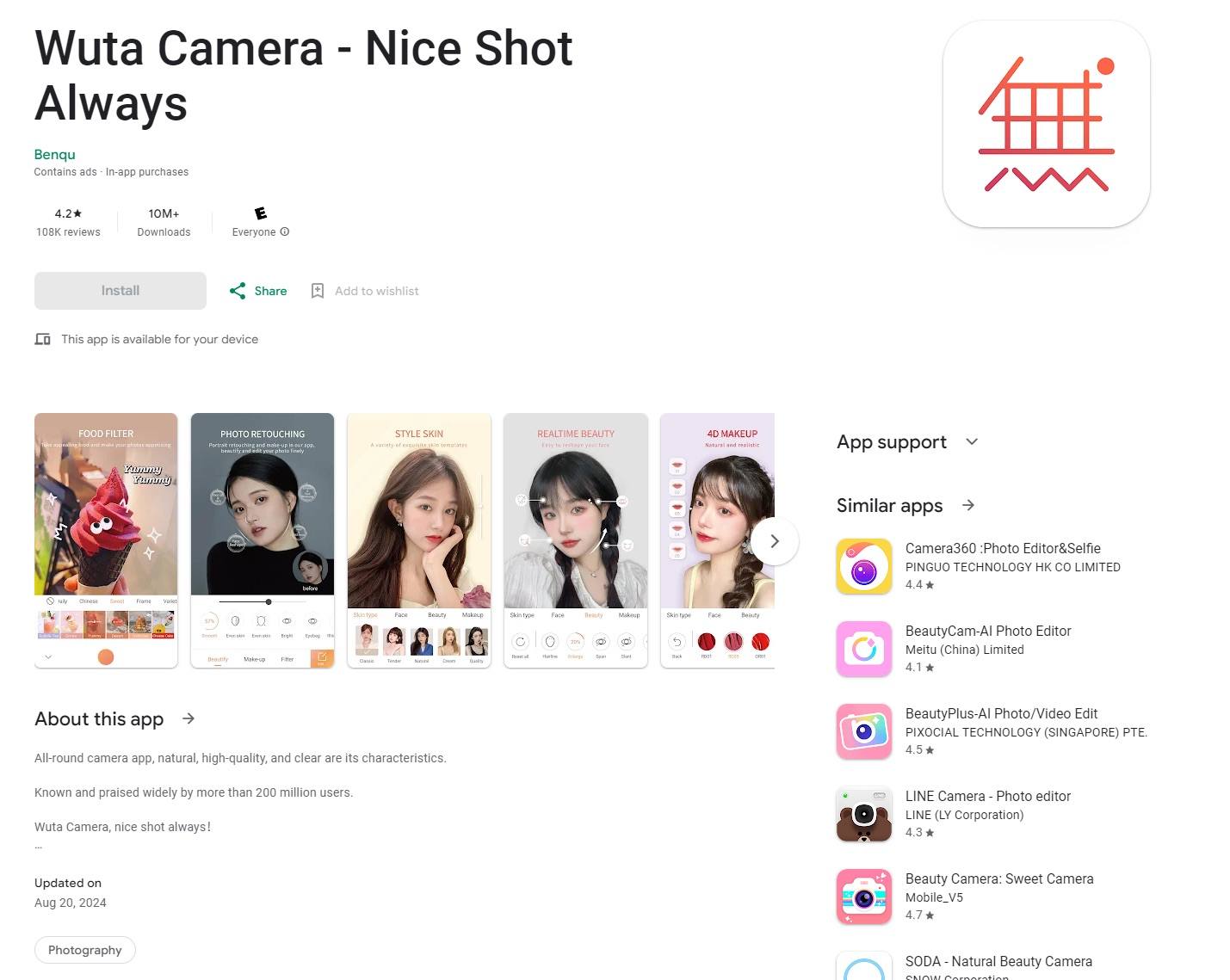
We discovered traces of the malware in a user-modded model of Spotify, within the photograph modifying app Wuta Digital camera, in Max Browser, and in mods for each WhatsApp and well-liked video games (together with Minecraft).
In modded Spotify
On the very begin of our investigation, our eye was caught by an uncommon modification of the Spotify Plus app. Customers had been invited to obtain a brand new model of their favourite app from an unofficial supply — without spending a dime and with an unlocked subscription providing limitless listening, each on-line and off. The great inexperienced Obtain Spotify MOD APK button seems so tempting, proper? Cease! It’s malware. By no means thoughts the Safety Verified and Official Certification ensures; this app will wreak havoc.
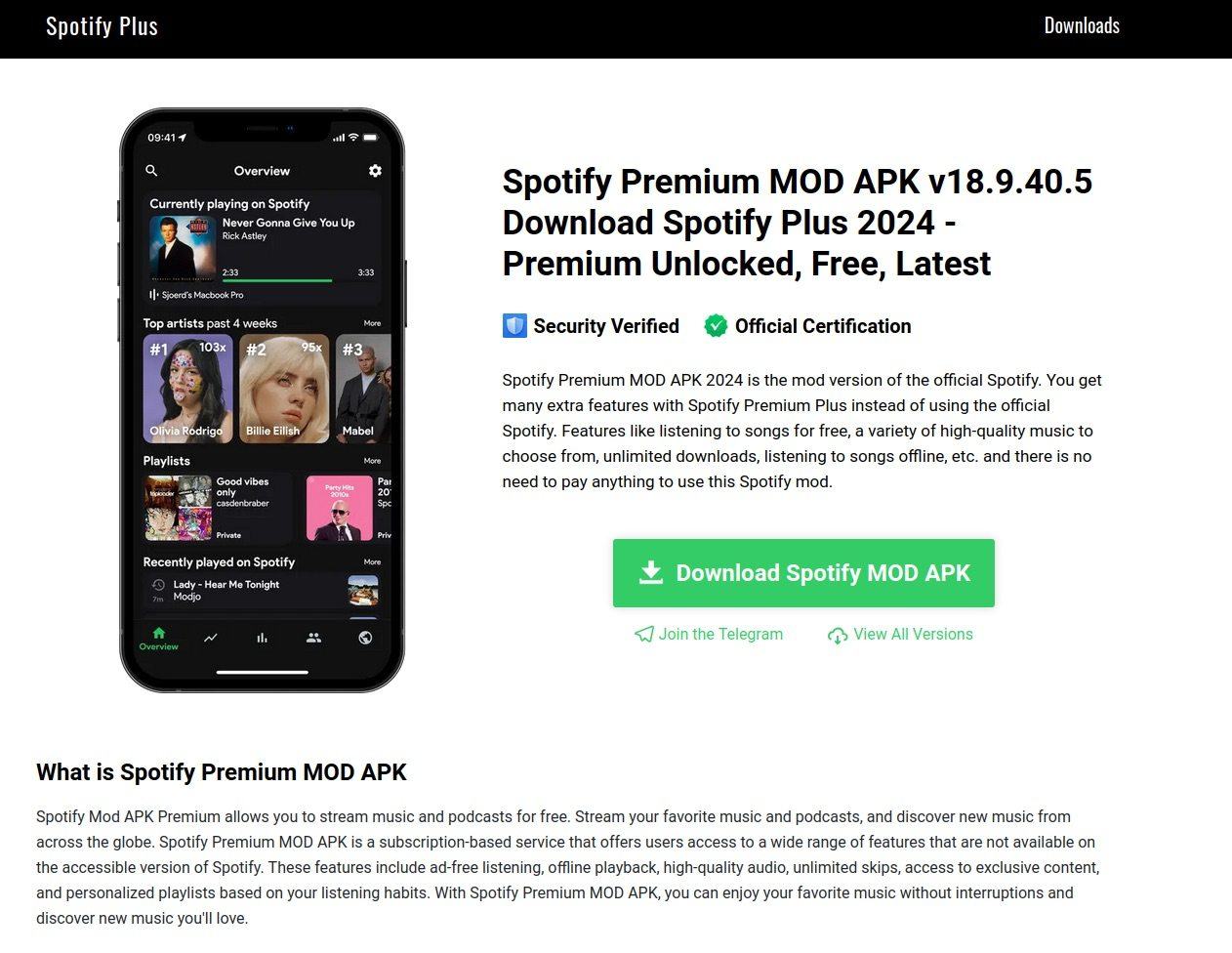
Nicely I by no means, all variations are viewable. May Necro or different Trojans be lurking there too?
When this app was launched, the Trojan despatched details about the contaminated machine to the attackers’ C2 server, and in response obtained a hyperlink to obtain a PNG picture. The malicious payload was hidden on this picture by way of steganography.
In apps on Google Play
Whereas the Spotify mod was distributed by unofficial channels, the Necro-infected Wuta Digital camera discovered its approach onto Google Play, from the place the app was downloaded greater than 10 million occasions. In line with our knowledge, the Necro loader penetrated model 6.3.2.148 of Wuta Digital camera, with clear variations ranging from 6.3.7.138. So, in case your model is decrease than that, you have to replace instantly.
Max Browser’s viewers is way smaller — only one million customers. Necro infiltrated its app code in model 1.2.0. The app was faraway from Google Play following our notification, however it’s nonetheless obtainable on third-party assets. These, in fact, must be trusted even much less, since trojanized variations of the browser should still reside there.
In mods for WhatsApp, Minecraft, and different well-liked apps
Various messenger shoppers normally boast extra options than their official cousins. However you need to deal with all mods, be they on Google Play or a third-party web site, as suspicious, for they typically come bundled with Trojans.
As an example, we discovered mods for WhatsApp with the Necro loader being distributed from unofficial sources, in addition to mods for Minecraft, Stumble Guys, Automotive Parking Multiplayer, and Melon Sandbox. And this choice certain isn’t random — attackers all the time goal the hottest video games and apps.
The best way to guard in opposition to Necro
Initially, we strongly advise in opposition to downloading apps from unofficial sources as a result of the danger of machine an infection is extraordinarily excessive. Secondly, apps on Google Play and different official platforms must also be handled with a wholesome dose of skepticism. Even a preferred app like Wuta Digital camera, with 10 million downloads, proved powerless within the face of Necro.
- Ensure that to defend your gadgets in order to not be caught off guard by a Trojan. Kaspersky for Android detects Necro and different comparable malware.
- Examine the app web page within the retailer earlier than downloading. We notably suggest evaluations with low scores, as these usually give heads-up about potential pitfalls. Rave evaluations might be faux, whereas a excessive total rating is straightforward to inflate.
- Don’t search for mods or hacked variations. Such apps are virtually all the time filled with every kind of Trojans: from probably the most innocent to cellular spyware and adware like CanesSpy.