Our weblog has coated vulnerabilities in some uncommon devices — from good mattress covers and robotic vacuums to visitors sign audio buttons, youngsters’s toys, pet feeders, and even bicycles. However the case we’re discussing immediately would possibly simply be essentially the most… unique but. Just lately, cybersecurity researchers uncovered two extraordinarily severe vulnerabilities within the distant management apps for… Lovense intercourse toys.
All the pieces about this story is wild: the character of the weak devices, the corporate’s intention to take 14 months (!) to repair the issues, and the scandalous particulars that emerged after researchers printed their findings. So let’s… get caught straight in to proper into this story, which is as absurd as it’s improbable.
The Lovense on-line ecosystem
The very first thing that makes this story so uncommon is that Lovense, a maker of intimate toys, caters to each long-distance {couples} and cam fashions (human fashions that use webcams) engaged on streaming platforms.
To manage gadgets and allow consumer interplay, the corporate has developed a whole suite of software program merchandise tailor-made for a wide range of situations:
- Lovense Distant: the primary cell app for controlling intimate gadgets.
- Lovense Join: a companion app that acts as a bridge between Lovense gadgets and different apps or on-line companies. It’s put in on a smartphone or pc and permits a toy to attach by way of Bluetooth, after which relays management instructions from exterior sources.
- Lovense Cam Extension: a browser extension for Chrome and Edge that hyperlinks Lovense gadgets with streaming platforms. It’s used with the Lovense Join app and the OBS Toolset streaming software program for interactive management throughout stay broadcasts.
- Lovense Stream Grasp: an all-in-one app for streamers and cam fashions combining machine management options with stay streaming performance.
- Cam101: Lovense’s on-line academic platform for fashions engaged on streaming websites.
After all, this entire setup additionally consists of APIs, SDKs, an inside platform for mini-apps, and extra. In brief, Lovense isn’t nearly internet-connected intimate toys — it’s a full-fledged ecosystem.
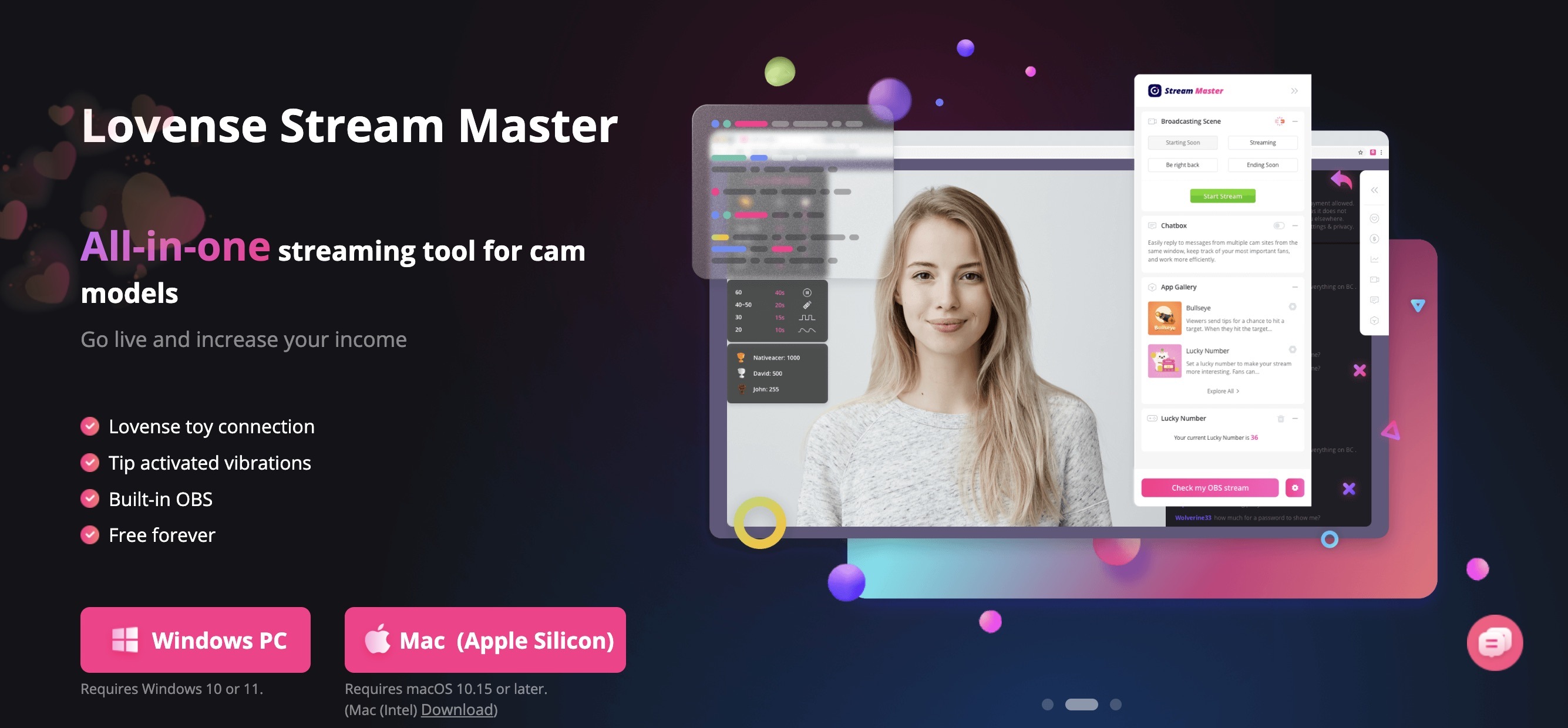
UI of the Stream Grasp app, which mixes machine administration and video streaming. Supply
If you happen to create an account within the Lovense infrastructure, you’re required to supply an e-mail deal with. Whereas some companies supply the choice to check in with Google or Apple, an e-mail deal with is the first sign-up methodology for a Lovense account. This element might sound insignificant, but it surely’s on the core of the vulnerabilities that have been found.
Two vulnerabilities in Lovense on-line merchandise
So, how did this all unfold? In late July 2025, a researcher often known as BobDaHacker printed on his weblog an in depth submit about two vulnerabilities in Lovense’s on-line merchandise. Lots of the merchandise (together with Lovense Distant) have social-interaction options. These options permit customers to speak, add associates, ship requests and subscribe to different customers, together with folks they don’t know.
Whereas utilizing the social-interaction options of one of many Lovense apps, BobDaHacker noticed the primary vulnerability: when he disabled notifications from one other consumer, the app despatched an API request to the Lovense server. After inspecting the physique of this request, BobDaHacker was shocked to search out that, as an alternative of the consumer’s ID, the request contained their precise e-mail deal with.
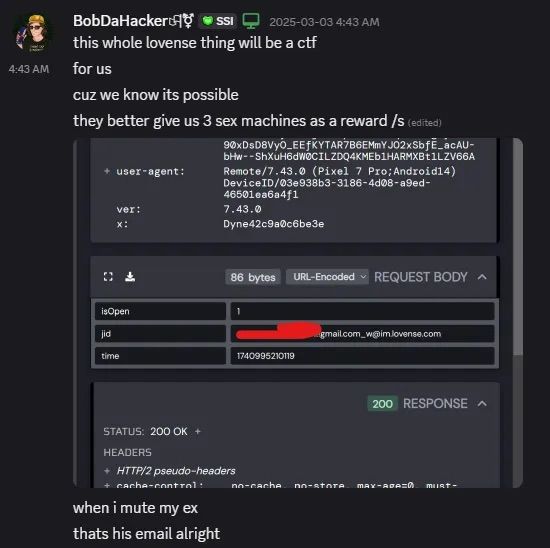
When a easy motion (like disabling notifications) was carried out, the app would ship a request to the server that included one other consumer’s actual e-mail deal with. Supply
Upon additional investigation, the researcher discovered that Lovense’s API structure was designed in order that for any motion that involved one other consumer (like disabling their notifications), the app sends a request to the server. And on this request the consumer’s account is at all times recognized by the true e-mail deal with they signed up with.
In observe, this meant that any consumer who intercepted their very own community visitors might get entry to the true e-mail addresses of different folks on the app. It’s essential to do not forget that the Lovense apps have social-interaction options and permit communication with cam fashions. In lots of circumstances, customers don’t know one another exterior of the platform, and exposing the e-mail addresses linked to their profiles might result in deanonymization.
BobDaHacker mentioned his findings with one other cybersecurity researcher named Eva, and collectively they examined the Lovense Join app. This led them to find an much more severe vulnerability: producing an authentication token within the app solely required the consumer’s e-mail deal with — no password was wanted.
This meant that any technically expert individual might achieve entry to any Lovense consumer’s account — so long as they knew the consumer’s e-mail deal with. And as we simply discovered, that deal with might simply be obtained by exploiting the primary vulnerability.
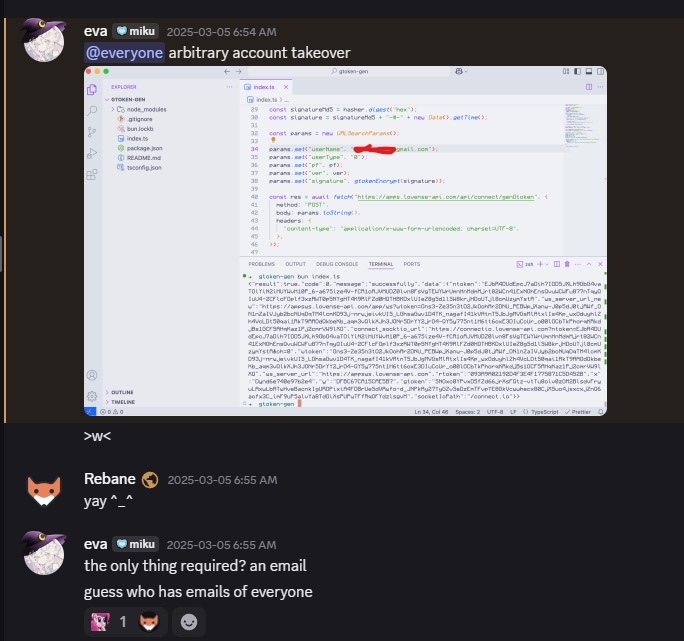
To generate an authentication token within the Lovense app, solely the consumer’s e-mail was required — with out the password. Supply
These tokens have been used for authentication throughout varied merchandise within the Lovense ecosystem, together with:
- Lovense Cam Extension
- Lovense Join
- Stream Grasp
- Cam101
Moreover, the researchers efficiently used this methodology to achieve entry to not solely common consumer profiles but additionally accounts with administrator privileges.
Lovense’s response to vulnerability studies
In late March 2025, BobDaHacker and Eva reported the vulnerabilities they’d found in Lovense merchandise via The Web Of Dongs Mission — a gaggle devoted to researching and enhancing the safety of internet-connected intimate gadgets. The next month, in April 2025, in addition they posted each vulnerabilities on HackerOne, a extra conventional platform for partaking with safety researchers and paying bug bounties.
Lovense, the adult-toy producer, acknowledged the report and even paid BobDaHacker and Eva a complete of $4000 in bounties. Nonetheless, in Could after which once more in June, the researchers seen the vulnerabilities nonetheless hadn’t been mounted. They continued speaking to Lovense, which is when essentially the most weird a part of the story started to unfold.
First, Lovense instructed the researchers that the account takeover vulnerability had been mounted on April. However BobDaHacker and Eva checked and confirmed this was false: it was nonetheless attainable to get an authentication token for an additional consumer’s account with out a password.
The scenario with the e-mail disclosure vulnerability was much more absurd. The corporate said it’d take 14 months to completely resolve the difficulty. Lovense admitted they’d a repair that could possibly be carried out in only one month, however they determined in opposition to it to keep away from compatibility issues and preserve assist for older app variations.
The back-and-forth between the researchers and the producer continued for a number of extra months. The corporate would repeatedly declare the vulnerabilities have been mounted, and the researchers would simply as constantly show they might nonetheless entry each emails and accounts.
Lastly, in late July, BobDaHacker printed an in depth blogpost describing the vulnerabilities and Lovense’s inaction, however solely after giving the corporate advance discover. Journalists from TechCrunch and different retailers contacted BobDaHacker and have been capable of affirm that in early August — 4 months after the corporate was first notified — the researcher might nonetheless confirm any consumer’s e-mail deal with.
And that was removed from the top of it. Probably the most scandalous particulars have been revealed to BobDaHacker and Eva solely after their analysis was printed.
A historical past of negligence: who warned Lovense and when
BobDaHacker’s work made waves throughout media, blogs, and social networks. Because of this, simply two days after the report was printed, Lovense lastly patched each vulnerabilities — and this time, it appears, for actual.
Nonetheless, it quickly got here to gentle that this story began lengthy earlier than BobDaHacker’s report. Different researchers had already warned Lovense about the exact same vulnerabilities for years, however their messages have been both ignored or hushed up. These researchers shared their tales with BobDaHacker and the publications that coated his investigation.
To actually grasp the extent of Lovense’s indifference to consumer safety and privateness, you simply want to have a look at the timeline of those studies:
- 2023: a researcher often known as @postypoo reported each bugs to Lovense, and was supplied… two free grownup toys in response, however the vulnerabilities have been by no means mounted.
- Also2023: researchers @Krissy and @SkeletalDemise found the vulnerability associated to account takeovers. Lovense claimed the difficulty had been mounted, and paid a bounty in the identical month. Nonetheless, @Krissy’s follow-up message stating that the vulnerability was nonetheless current went unanswered.
- 2022: a researcher named @radiantnmyheart found the bug that uncovered emails, and reported it. The message was ignored.
- 2017: the corporate Pen Check Companions reported the e-mail publicity vulnerability and the dearth of chat encryption within the Lovense Physique Chat app, and printed its research on this. The report was ignored.
- 2016: The Web Of Dongs Mission recognized three comparable e-mail publicity vulnerabilities. This all implies that Lovense requested BobDaHacker to provide it 14 months to patch vulnerabilities they’d identified about for at the very least eight years!
What’s extra, after BobDaHacker’s report was printed, they heard not solely from the moral hackers who’d beforehand reported these bugs, but additionally from the creator of an OSINT web site and their associates, who have been something however completely satisfied. These people had apparently been exploiting the vulnerabilities for their very own functions — particularly, harvesting consumer emails and subsequent deanonymization. This isn’t stunning although provided that the Pen Check Companions report had been publicly obtainable since 2017.
Defending your privateness
Lovense’s strategy to consumer privateness and safety clearly leaves rather a lot to be desired — to place it mildly. Whether or not to proceed utilizing the model’s gadgets after this — particularly connecting them to the corporate’s on-line companies — is a call every consumer must make for themselves.
For our half, we provide some tips about tips on how to defend your self and preserve your privateness must you work together with grownup on-line companies.
- All the time create a separate e-mail deal with whenever you register for these kind of companies. It shouldn’t include any info that can be utilized to establish you.
- Don’t use this e-mail deal with for another actions.
- When registering, don’t use your actual first identify, surname, age, date of delivery, metropolis of residence, or another knowledge that would establish you.
- Don’t add actual images of your self that would simply be used to acknowledge you.
- Defend your account with a powerful password. It ought to include at the very least 16 characters and ideally embody a mixture of uppercase and lowercase letters, numbers, and particular characters.
- This password should be distinctive. By no means use it for different companies so that you don’t put them in danger within the occasion of an information leak.
- To keep away from forgetting the password and e-mail deal with you created particularly for this service, use a dependable password supervisor. KPM can even enable you to generate a random, sturdy, and distinctive password.
And if you wish to be extra… boned up with regards to selecting grownup toys and related companies, we suggest taking a look at specialised assets like The Web Of Dongs Mission, the place you could find details about manufacturers that curiosity you.
Try our different posts on tips on how to defend your non-public life from prying eyes:



