In September 2024, a workforce of researchers from each the College of Florida and Texas Tech College introduced a paper detailing a moderately subtle methodology for intercepting textual content entered by customers of the Apple Imaginative and prescient Professional combined actuality (MR) headset.
The researchers dubbed this methodology GAZEploit. On this put up, we’ll discover how the assault works, the extent of the menace to homeowners of Apple VR/AR gadgets, and the way greatest to shield your passwords and different delicate data.
How textual content enter works in Apple visionOS
First, a bit about how textual content is enter in visionOS — the working system powering Apple Imaginative and prescient Professional. One of the crucial spectacular improvements of Apple’s MR headset is its extremely efficient use of eye monitoring.
Gaze course serves as the first methodology of person interplay with the visionOS interface. The monitoring is so exact that it really works even for the smallest interface parts — together with the digital keyboard.
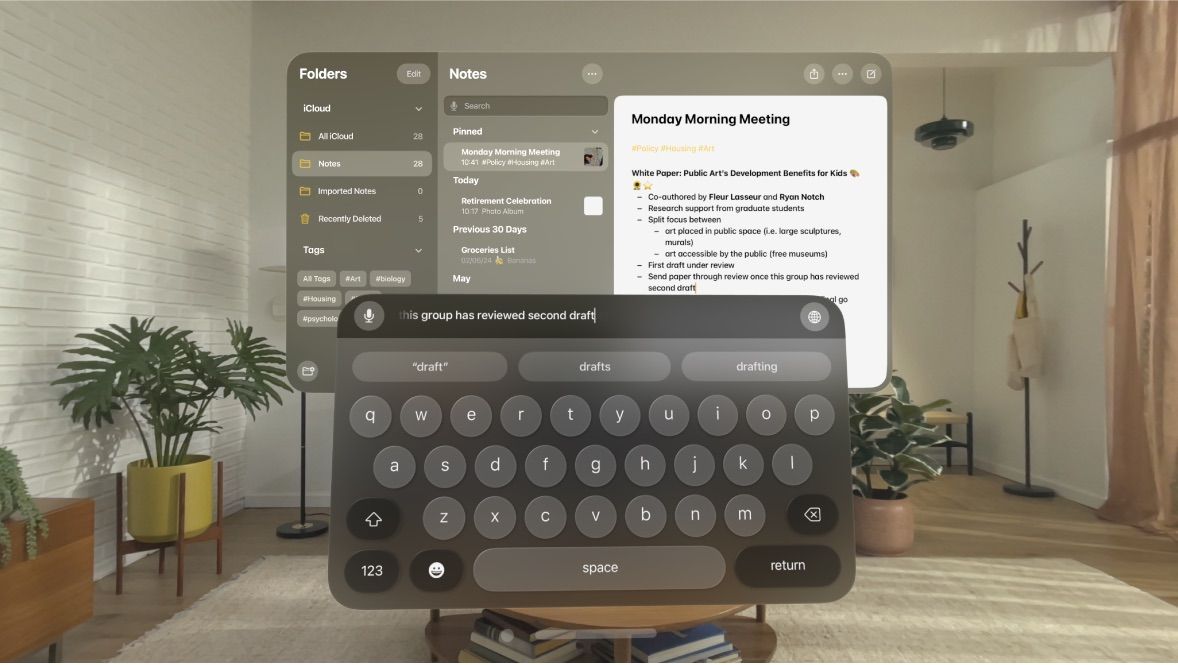
visionOS makes use of a digital keyboard and eye monitoring to enter textual content. Supply
Though visionOS gives voice management, the digital keyboard stays the first textual content enter methodology. For delicate data comparable to passwords, visionOS offers safety towards prying eyes: in screen-sharing mode, each the keyboard and the entered password are routinely hidden.
Throughout display sharing, visionOS routinely hides passwords entered by Imaginative and prescient Professional customers. Supply
One other key function of Apple’s MR headset lies in its method to video calls. Because the system sits immediately on the person’s face, the usual front-camera choice isn’t any good for transmitting the person’s video picture. Alternatively, utilizing a separate exterior digicam for video calls can be very un-Apple-like; plus, video-conference contributors carrying headsets would look moderately odd.
So Apple got here up with a extremely unique know-how that encompasses a so-called digital digicam. Primarily based on a 3D face scan, Imaginative and prescient Professional creates a digital avatar of the person (Apple calls it a Persona), which is what really takes half within the video name. You should utilize your Persona in FaceTime and different video-conferencing apps.
By utilizing a lot of biometric knowledge, the Persona digital avatar in visionOS seems to be actually lifelike. Supply
The headset’s sensors observe the person’s face in real-time, permitting the avatar to imitate head actions, lip actions, facial expressions, and so forth.
GAZEploit: listen in on Apple Imaginative and prescient Professional person enter
For the GAZEploit researchers, the seminal function of the Persona digital avatar is the usage of knowledge fed from the Imaginative and prescient Professional’s extremely exact sensors to duplicate the person’s eye actions with absolute pinpoint accuracy. And it was right here that the workforce found a vulnerability enabling interception of enter textual content.
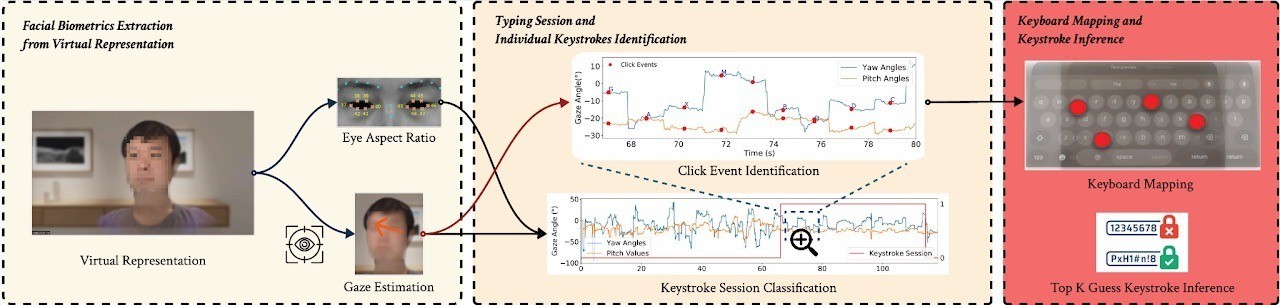
Right here’s how GAZEploit works in precept — permitting an attacker to intercept textual content entered by an Apple Imaginative and prescient Professional person. Supply
The assault’s core idea is kind of easy: though the system rigorously hides passwords entered throughout video calls, by monitoring the person’s eye actions, mirrored by their digital avatar, a menace actor can reconstruct the characters entered on the digital keyboard, or, moderately, keyboards, as visionOS has three: passcode (PIN) keyboard, default QWERTY keyboard, and quantity and particular character keyboard. This complicates the popularity course of, since an outdoor observer doesn’t know which keyboard is in use.
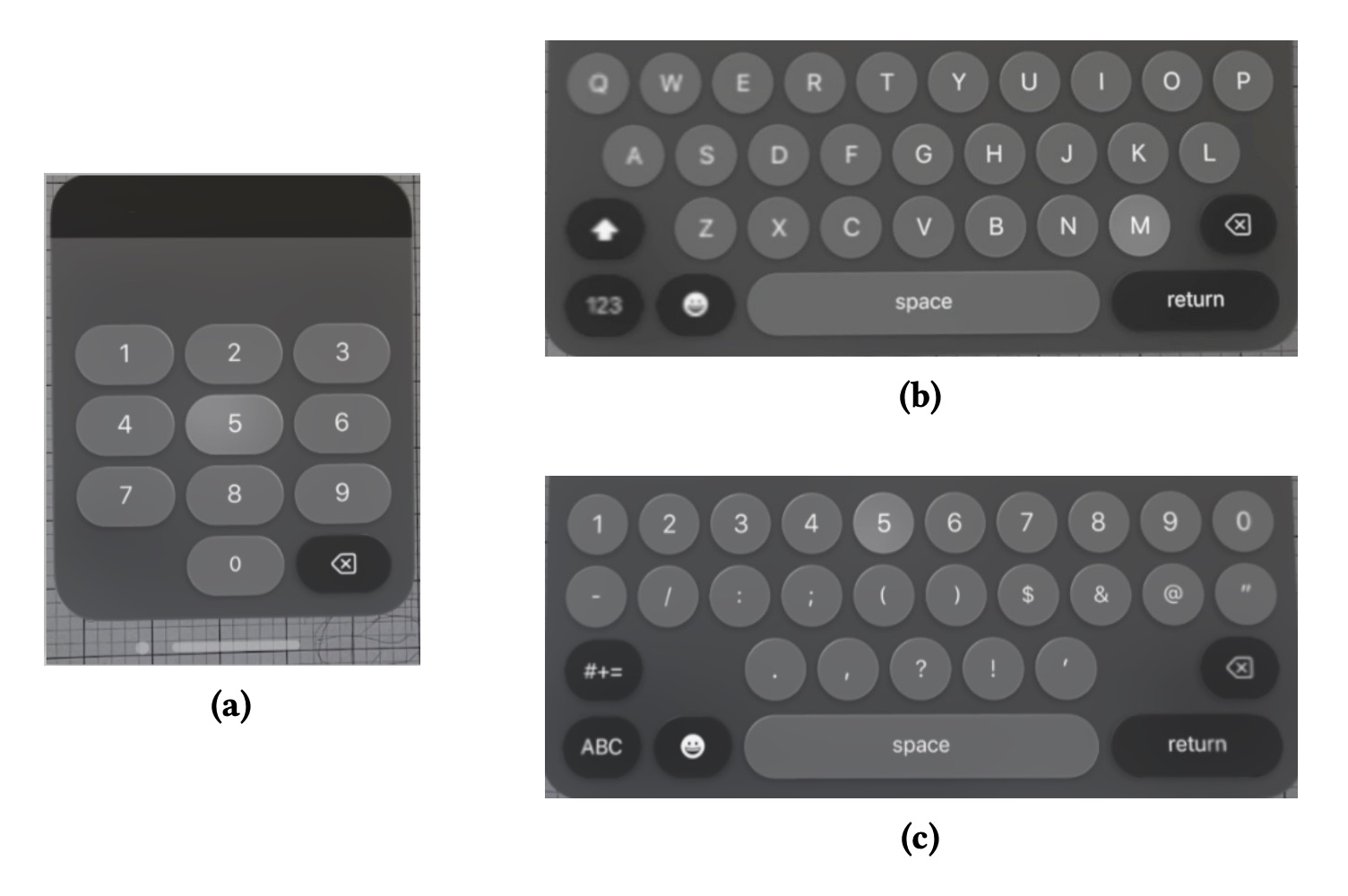
visionOS really has three completely different digital keyboards: (а) for passcodes, (b) for letters, and (c) for numbers and particular characters. Supply
Nevertheless, neural networks successfully automate the GAZEploit assault. The primary stage of the assault makes use of a neural community to determine text-input classes. Eye motion patterns throughout use of the digital keyboard differ considerably from regular patterns: blink charges lower, and gaze course turns into extra structured.
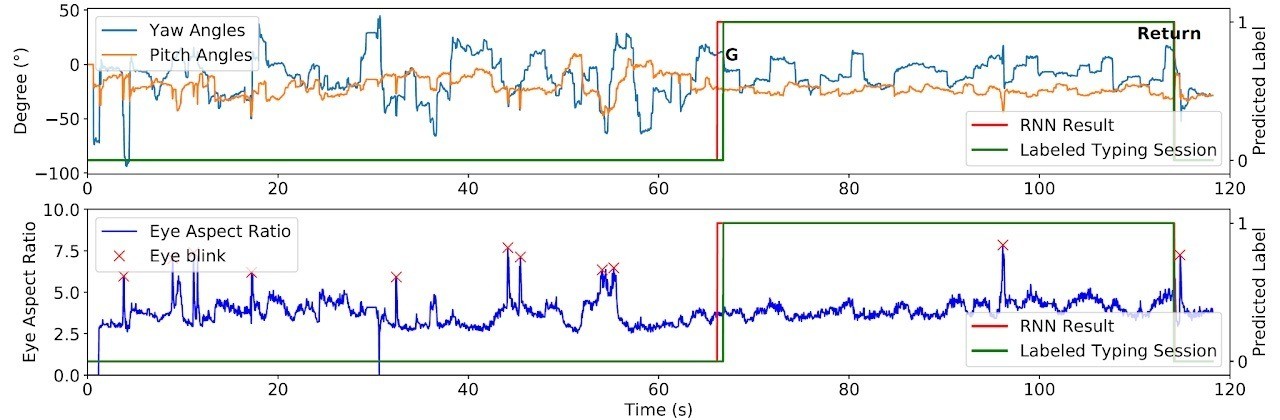
First, the neural community identifies when textual content is being entered on the digital keyboard. Supply
On the second stage, the neural community analyzes gaze stability modifications to determine eye-based number of characters, and makes use of attribute patterns to pinpoint digital key presses. Then, based mostly on gaze course, the system calculates which key the person was .
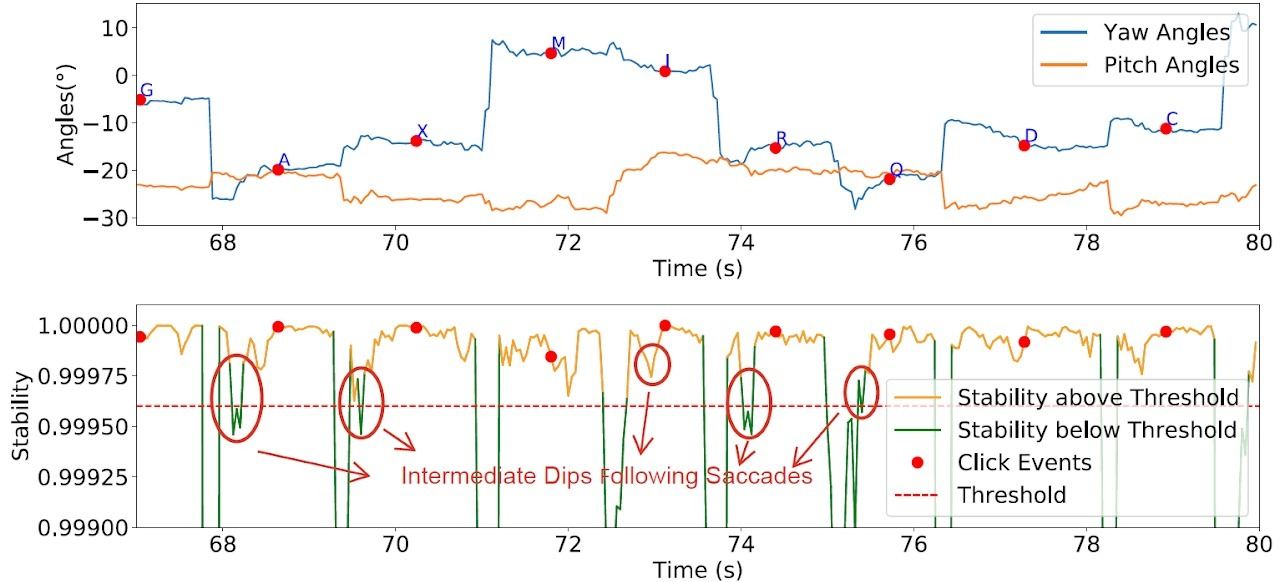
Subsequent, the neural community acknowledges particular person digital keystrokes and the characters being entered. Supply
How precisely GAZEploit acknowledges enter knowledge
In precise truth, it’s all a bit extra difficult than the graph above suggests. Calculations based mostly on the avatar’s eye place generate a heatmap of possible factors on the digital keyboard the place the person’s gaze may need landed throughout textual content entry.
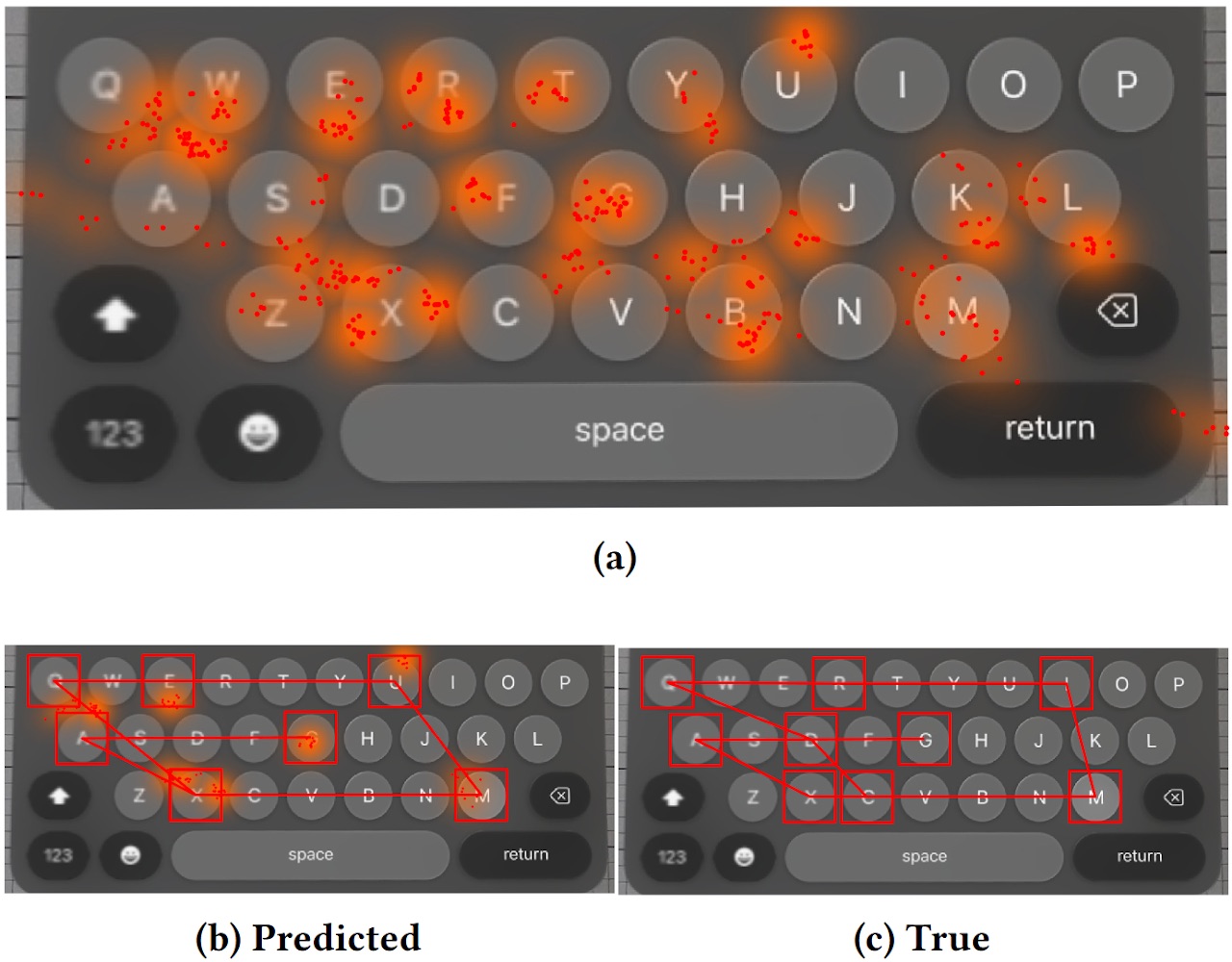
Mapped gaze instructions for keystroke inference of the demo assault: (a) adaptive digital keyboard mapping, (b) predicted first guess keystrokes, (c) precise keystrokes. The accuracy isn’t excellent, but it surely’s no unhealthy. Supply
Then, the researchers’ mannequin converts the collected data into a listing of Okay digital keys that have been more than likely “pressed” by the person. The mannequin additionally offers for numerous data-entry situations (password, e-mail handle/hyperlink, PIN, arbitrary message), considering the specifics of every.
What’s extra, the neural community makes use of a dictionary and extra strategies to enhance interpretation. For instance, attributable to its measurement, the spacebar is usually a top-five candidate — producing many false positives that want filtering. The backspace key requires particular consideration: if the keystroke guess is appropriate, it means the earlier character was deleted, but when it’s fallacious, then two characters might get mistakenly discarded.
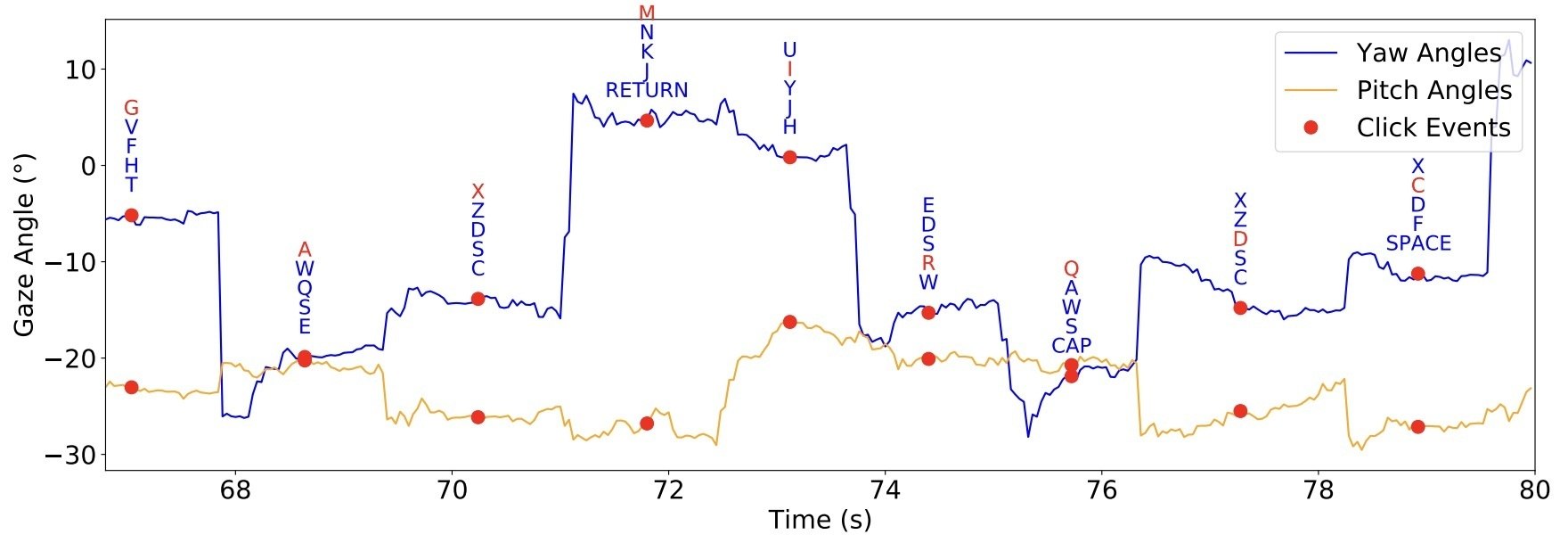
GAZEploit suggests the top-five more than likely characters. Supply
The researchers’ detailed error evaluation exhibits that GAZEploit usually confuses adjoining keys. At most precision (Okay=1), roughly one-third of entered characters are recognized accurately. Nevertheless, for teams of 5 more than likely characters (Okay=5), relying on the precise state of affairs, the accuracy is already 73–92%.
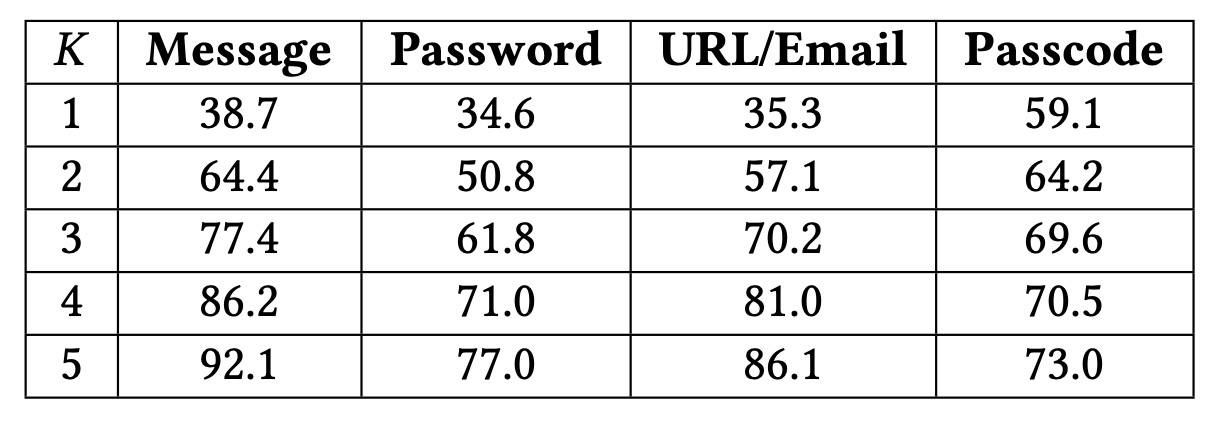
The accuracy of GAZEploit recognition in numerous situations. Supply
How harmful the GAZEploit assault is in sensible phrases
In observe, such accuracy implies that potential attackers are unlikely to acquire the goal password in ready-to-go type; however they’ll dramatically — by many orders of magnitude, in truth — scale back the variety of makes an attempt wanted to brute-force it.
The researchers declare that for a six-digit PIN, it’ll solely take 32 makes an attempt to cowl 1 / 4 of all of the more than likely combos. For a random eight-character alphanumeric password, the variety of makes an attempt is slashed from a whole bunch of trillions to a whole bunch of 1000’s (from 2.2×1014 to three.9×105, to be exact), which makes password cracking possible even with a prehistoric Pentium CPU.
In mild of this, GAZEploit might pose a severe sufficient menace and discover sensible software in high-profile focused assaults. Happily, the vulnerability has already been patched: within the newest variations of visionOS, Persona is suspended when the digital keyboard is in use.
Apple might conceivably shield customers from such assaults in a extra elegant manner — by sprinkling some random distortions within the exact biometric knowledge driving the digital avatar’s eye actions.
Regardless, Apple Imaginative and prescient Professional homeowners ought to replace their gadgets to the newest model of visionOS — and breathe simply. One very last thing, we advise them — and everybody else — to train warning when coming into passwords throughout video calls: keep away from it when you can, at all times use the strongest (lengthy and random) character combos doable, and use a password supervisor to create and retailer them.



