In an try and bypass safety options, attackers are more and more hiding phishing and different malicious hyperlinks inside QR codes. It’s because of this that we’ve added a expertise to Kaspersky Safe Mail Gateway that reads QR codes (together with ones hidden inside PDF information), extracts hyperlinks and checks them earlier than they land in an worker’s inbox. We clarify the way it works.
Why do attackers use QR codes?
Ever since even fundamental safety instruments realized to verify phishing hyperlinks successfully sufficient, attackers have been inventing methods to cover them from scanners. Probably the most generally employed trick is to put up hyperlinks on third-party companies; that means, victims don’t obtain an e-mail instantly from the attackers, however a notification from some reliable web site the place a doc with a malicious hyperlink is already positioned. Whereas such ploys work properly on dwelling customers, with firm staff the success price is much decrease. That’s as a result of any self-respecting group lately has geared up all its work computer systems with safety software program that catches redirects to phishing websites.
Subsequently, attackers have turned their consideration to QR codes. First, this expertise obligingly transforms common URLs into one thing incomprehensible to plain methods that verify hyperlinks for malicious intent. Second, QR codes are widespread sufficient for individuals to scan them and not using a second thought. And third and most essential, individuals overwhelmingly scan QR codes with a telephone or pill that won’t have a safety resolution with anti-phishing expertise – particularly if it’s a private, not work, system.
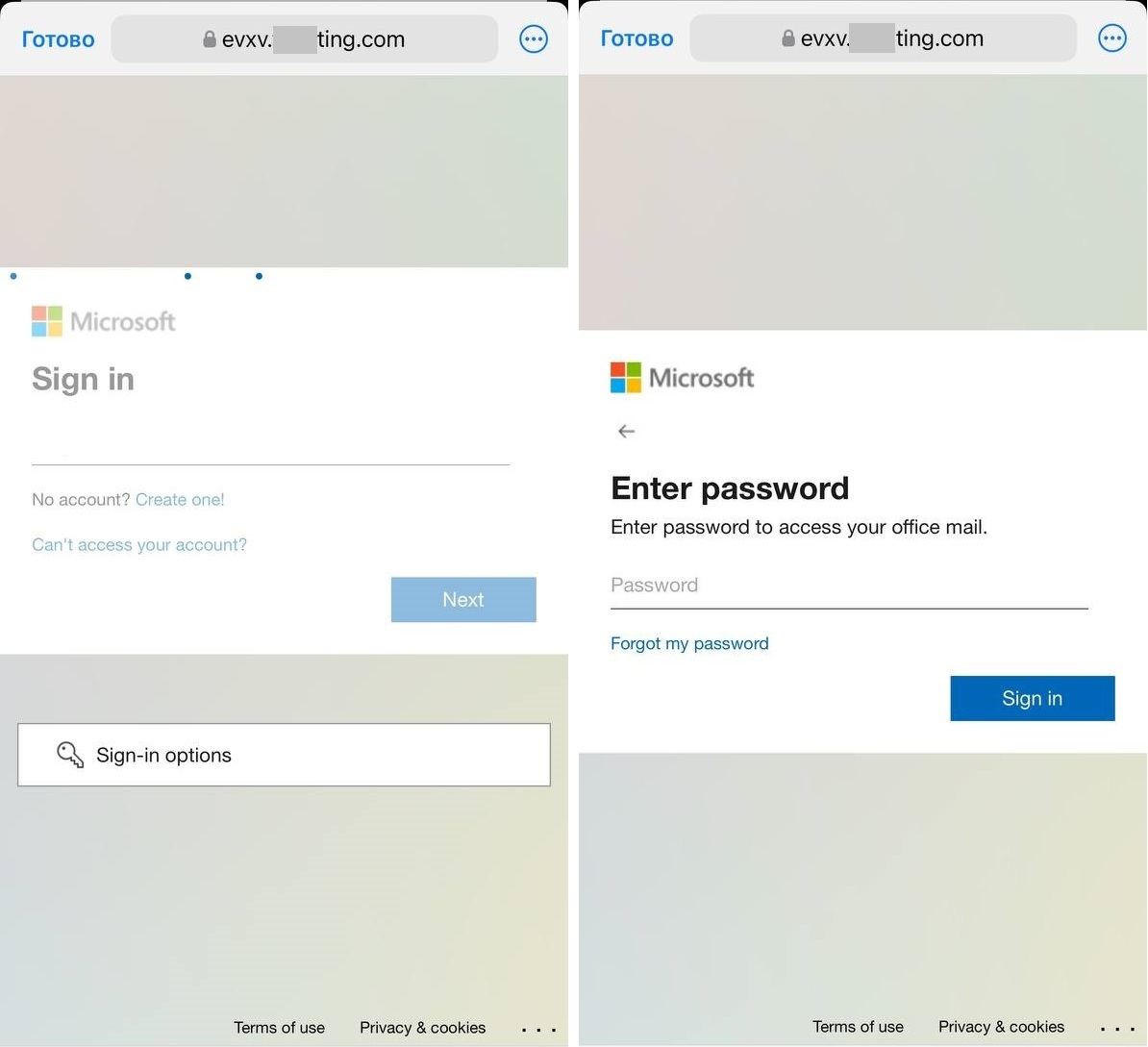
Plus, on this case, much less suspicion is raised by the immediate to enter work credentials, that are what the attackers mainly need. On a pc, the consumer is prone to be signed in already, however accessing work methods from a private system requires extra authentication, proper?
Why are QR codes most frequently hidden in PDF information?
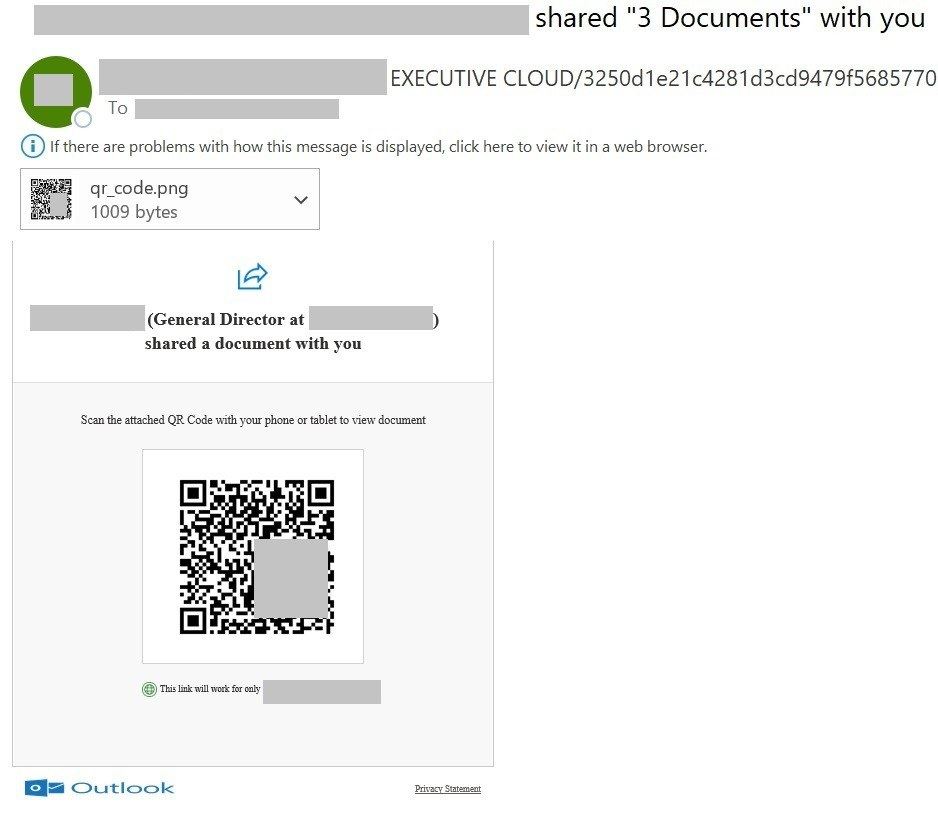
Positive, a QR code may also be despatched within the physique of an e-mail. However hardly anybody will comply with a QR code and not using a few phrases explaining why they need to, and this textual content might be analyzed and flagged as phishing. Apart from, a picture has sure traits – at the least its dimensions – by which it may be recognized.
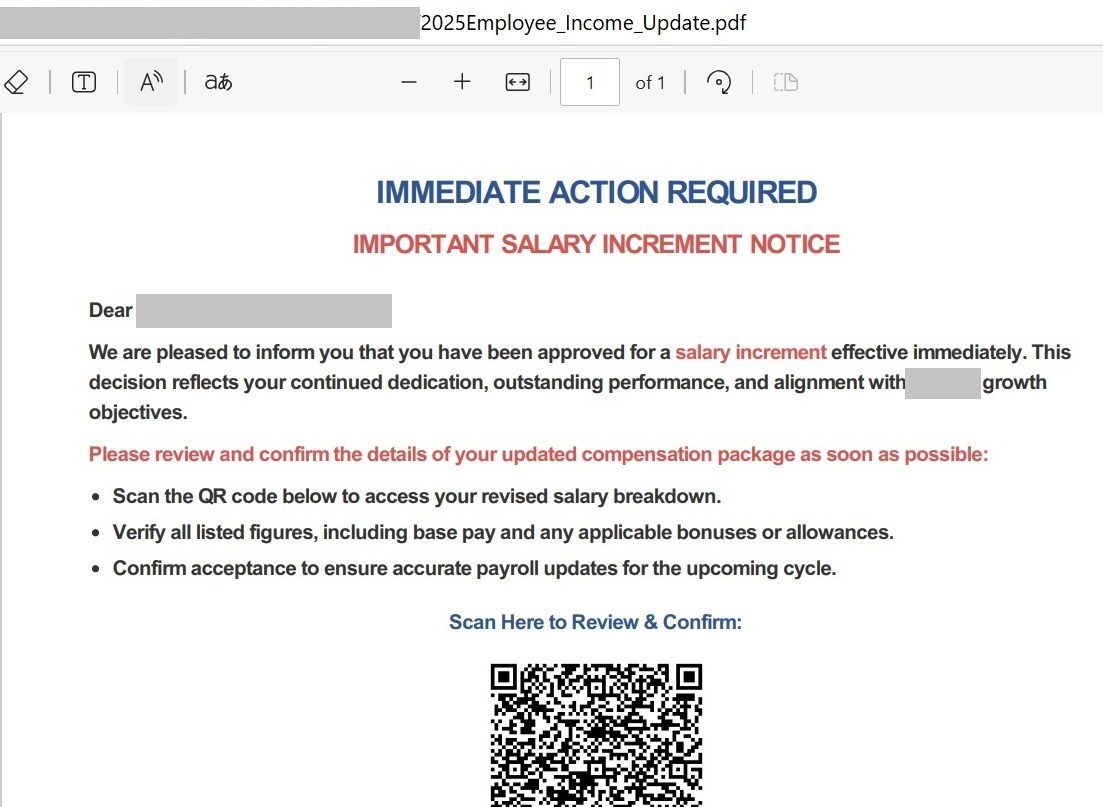
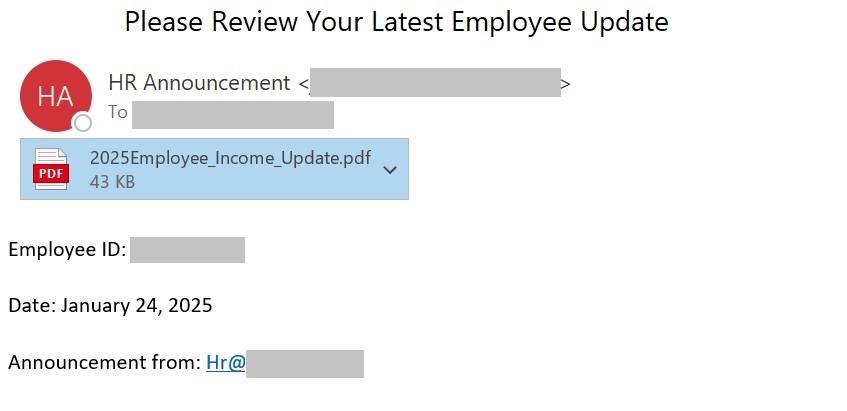
A PDF file, alternatively, is a form of black field. The format is proprietary – you’ll be able to’t peek inside with out particular instruments. As well as, the quilt e-mail can include minimal textual content, one thing like: “Vital! All data within the PDF”
How does our expertise work?
In fact, a QR code in an e-mail isn’t all the time an indication of phishing. For instance, cell software builders typically furnish their PDF paperwork and mailings with direct hyperlinks to app shops. Generally, it’s a fast and straightforward option to ship a hyperlink to a telephone. That’s why we are able to’t mark every e-mail with a QR-code as a suspicious. So our builders created a software to extract URLs from QR codes for extra checking by anti-phishing modules and anti-spam heuristics.
Not solely can the expertise extract URLs from QR codes in pictures, but additionally verify PDF information – extracting all hyperlinks from all QR codes discovered inside them. If a hyperlink is acknowledged as phishing, the e-mail can also be flagged as phishing and processed in accordance with the Kaspersky Safe Mail Gateway settings. So the top consumer by no means even sees the harmful QR code. One of the best consequence!