Our International Analysis and Evaluation Crew (GReAT) specialists have found two malicious packages within the Python Package deal Index (PyPI) – a well-liked third-party software program repository for Python. In accordance with the packages’ descriptions, they have been libraries that allowed to work with in style LLMs (giant language fashions). Nonetheless, in reality, they imitated the declared performance utilizing the demo model of ChatGPT, and their predominant function was to put in JarkaStealer malware.
The packages have been accessible for obtain for greater than a 12 months. Judging by the repository’s statistics, throughout this time they have been downloaded greater than 1700 occasions by customers from greater than 30 nations.
Malicious packages and what have been they used for
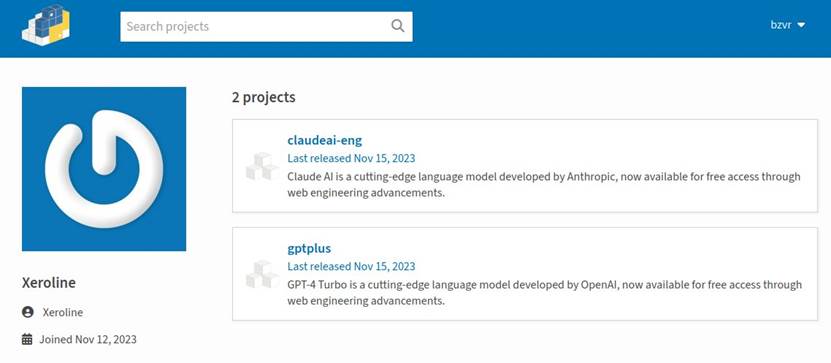
The malicious packages have been uploaded to the repository by one writer and, in reality, differed from one another solely in identify and outline. The primary was known as “gptplus” and allegedly allowed entry to the GPT-4 Turbo API from OpenAI; the second was known as “claudeai-eng” and, based on the outline, additionally promised entry to the Claude AI API from Anthropic PBC.
The descriptions of each packages included utilization examples that defined find out how to create chats and ship messages to language fashions. However in actuality, the code of those packages contained a mechanism for interplay with the ChatGPT demo proxy so as to persuade the sufferer that the package deal was working. In the meantime, the __init__.py file contained within the packages decoded the information contained inside and downloaded the JavaUpdater.jar file from the GitHub repository. If Java was not discovered on the sufferer’s machine, it additionally downloaded and put in the Java Runtime Surroundings (JRE) from Dropbox. The jar file itself contained the JarkaStealer malware, which was used to compromise the event surroundings and for undetected exfiltration of stolen knowledge.
What’s JarkaStealer malware, and why is it harmful?
JarkaStealer is malware, presumably written by Russian-speaking authors, which is used primarily to gather confidential knowledge and ship it to the attackers. Right here’s what it will possibly do:
- Steal knowledge from numerous browsers;
- Take screenshots;
- Gather system data;
- Steal session tokens from numerous functions (together with Telegram, Discord, Steam, and even a Minecraft cheat consumer);
- Interrupt browser processes to retrieve saved knowledge.
The collected data is then archived, despatched to the attacker’s server, after which deleted from the sufferer’s machine.
The malware authors distribute it via Telegram utilizing the malware-as-a-service (MaaS) mannequin. Nonetheless, we additionally discovered the supply code of JarkaStealer on GitHub, so it’s attainable that this marketing campaign didn’t contain the unique authors of the malware.
Methods to keep protected
We promptly knowledgeable PyPI directors in regards to the malicious implants within the gptplus and claudeai-eng packages, and as of now they’ve already been faraway from the repository. Nonetheless, there’s no assure that this (or an analogous) trick received’t be pulled on another platform. We proceed to observe exercise associated to the JarkaStealer malware and search for different threats in open supply software program repositories.
For individuals who downloaded and used one of many malicious packages, the primary advice is to right away delete it. The malware doesn’t have persistence performance, so it’s launched solely when the package deal is used. Nonetheless, all passwords and session tokens that have been used on a sufferer’s machine might have been stolen by JarkaStealer, and so needs to be instantly modified or reissued.
We additionally suggest that builders be particularly vigilant when working with open supply software program packages, and examine them totally earlier than integrating them into their initiatives. This features a detailed evaluation of the dependencies and the respective provide chain of software program merchandise – particularly in relation to such a hyped matter as the combination of AI applied sciences.
On this case, the writer’s profile’s creation date on PyPI might have been a purple flag. Should you look intently on the screenshot above, you’ll be able to see that each packages have been revealed on the identical day, whereas the account that revealed them was registered simply a few days earlier.
With the intention to decrease the dangers of working with third-party open supply software program packages and keep away from an assault on the provision chain, we suggest together with in DevSecOps processes the Kaspersky Open Supply Software program Threats Knowledge Feed, which is designed particularly for monitoring used open supply elements so as to detect threats that may be hidden inside.