Worrying in regards to the safety of your wi-fi community just isn’t as paranoid as some might imagine it’s. Many routers have a setting enabled by default that makes your WPA/WPA2-protected Wi-Fi community relatively susceptible. On this submit, we’ll talk about one of the efficient strategies of hacking wi-fi networks that exploits this setting, and the way to defend in opposition to it.
The only and simplest assault on WPA/WPA2-PSK: PMKID interception
PMKID interception is the simplest, easy-to-execute, and utterly undetectable technique of attacking wi-fi networks protected by the WPA/WPA2 requirements. In essence, this assault includes intercepting the encrypted Wi-Fi passwords that wi-fi routers broadcast always — even when no gadgets are related to them. Having obtained the encrypted password, the attacker can use the brute-force technique to decrypt it — and thereby connect with the Wi-Fi community.
This assault will also be carried out on a big scale utilizing a way referred to as wardriving. Right here, the attacker drives round a metropolis scanning all out there wi-fi networks and intercepting encrypted passwords which might be broadcast by routers. Not a lot tools is required for this — only a laptop computer, a long-range Wi-Fi adapter, and a strong antenna.
The intercepted encrypted passwords will be cracked on the go. However an attacker might favor to attend till they’re residence and enter all of the garnered passwords right into a password-cracking instrument on a high-performance laptop (or lease computing energy within the cloud). The effectiveness of this assault was not too long ago demonstrated in Hanoi: a Vietnamese hacker scanned round 10,000 wi-fi networks and managed to decrypt the passwords for half of them.

That is all it’s essential hack 5000 wi-fi networks utilizing PMKID interception. Supply
How is it even doable to hack Wi-Fi utilizing PMKID interception?
So why do wi-fi routers broadcast their Wi-Fi password on a regular basis, albeit in encrypted kind? Effectively, it is a fundamental operate of the 802.11r customary, which is carried out on most routers and often enabled by default. This customary permits quick roaming in Wi-Fi networks utilizing a number of entry factors. To hurry up the reconnection of the consumer gadget to new entry factors, they always broadcast their identifier — the exact same PMKID.
This identifier is a spinoff of the Pairwise Grasp Key (PMK). Extra exactly, it accommodates the results of an SHA-1 hash operate calculation, whose supply knowledge consists of the PMK key and a few further knowledge. The PMK key itself, in flip, is the results of an SHA-1 hash operate calculation of the Wi-Fi password.
In different phrases, the PMKID accommodates the wi-fi community password, hashed twice. In idea, the hashing course of is irreversible, that means it’s inconceivable to recuperate the unique knowledge from the ensuing hashed worth. Presumably, the creators of the 802.11r customary relied on this when devising the PMKID-based quick roaming mechanism.
Nonetheless, hashed knowledge will be brute-forced. That is made particularly simple by the truth that folks hardly ever use notably robust passwords for wi-fi networks, usually counting on pretty predictable combos of characters as a substitute. The creators of 802.11r clearly didn’t take this under consideration.
This downside was found just a few years in the past by the workforce behind one of the well-liked password restoration utilities — in different phrases, a password-cracking instrument — Hashcat. Since then, specialised instruments have been developed particularly for cracking intercepted PMKIDs.
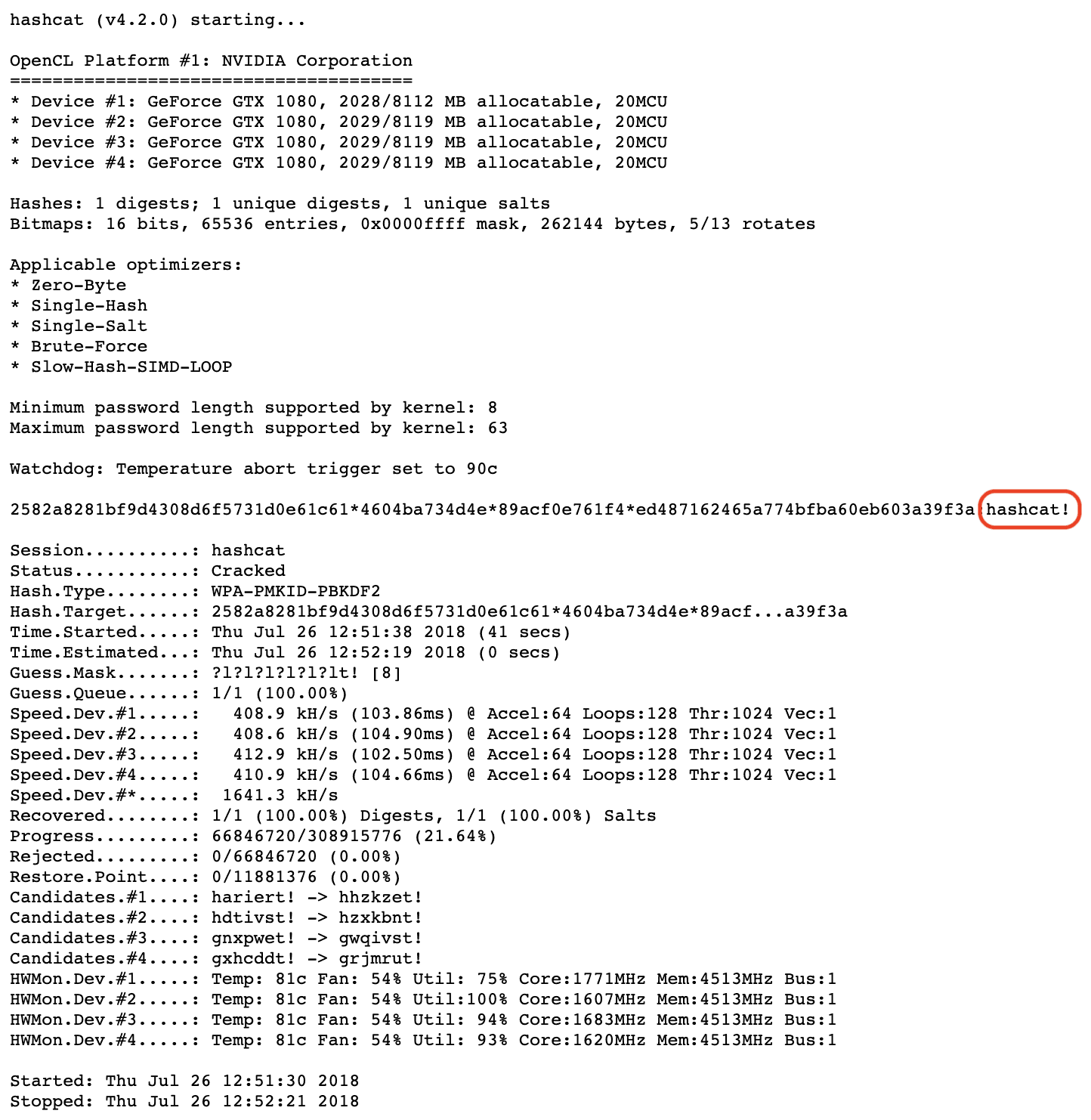
Profitable extraction of the password “hashcat!” from the intercepted PMKID of a wi-fi community. Supply
Thus, in follow, the attacker often intercepts the PMKID containing the encrypted password, after which makes use of a dictionary assault — that’s, they brute-force the commonest passwords, that are collected in a database.
Tips on how to defend your wi-fi community from a PMKID assault
What are you able to do to stop a PMKID interception assault in your wi-fi community? Fortuitously, there are a number of protecting measures that aren’t too tough to implement:
- Create a password in your wi-fi community that’s as lengthy and sophisticated as doable. If a PMKID attacker intercepts the hashed password out of your Wi-Fi, they nonetheless have to decrypt it afterward, however the extra advanced the password — the much less possible the attackers are to succeed. Subsequently, to guard in opposition to this assault, create the longest and most unguessable password doable in your wi-fi community.
- Disable PMKID transmission within the router settings. Sadly, not all routers permit this, but it surely’s price checking if yours has this setting. You will discover it by trying to find PMKID or 802.11r.
- Change to WPA3. If all of your gadgets help this newer Wi-Fi safety customary, it’s price contemplating switching to it: WPA3 is usually way more safe than WPA2 and, importantly, isn’t vulnerable to PMKID interception.
- Arrange a visitor community. It may be tedious to must often enter a robust password for the primary community on new gadgets, so arrange a visitor community with an easier password. By the best way, it’s additionally a good concept to switch doubtlessly insecure issues like IoT gadgets to the visitor community.
- Use the “Gadgets on My Community“ function, which is out there in our Kaspersky Plus and Kaspersky Premium This function exhibits a listing of gadgets in your community and alerts you if a brand new gadget connects to it.
For extra safety of transmitted knowledge in case somebody nonetheless manages to hack your Wi-Fi, use a VPN on all of your gadgets to safe the web connection — for instance, our Kaspersky Safe Connection, which can also be included within the Kaspersky Plus and Kaspersky Premium subscriptions.


