Many macOS customers consider their working system is proof against malware, in order that they don’t must take additional safety precautions. In actuality, it’s removed from the reality, and new threats maintain popping up.
Are there viruses for macOS?
Sure — and loads of ’em. Listed below are some examples of Mac malware we’ve beforehand coated on Kaspersky Day by day and Securelist:
- A crypto-wallet-stealing Trojan disguised as pirated variations of in style macOS apps.
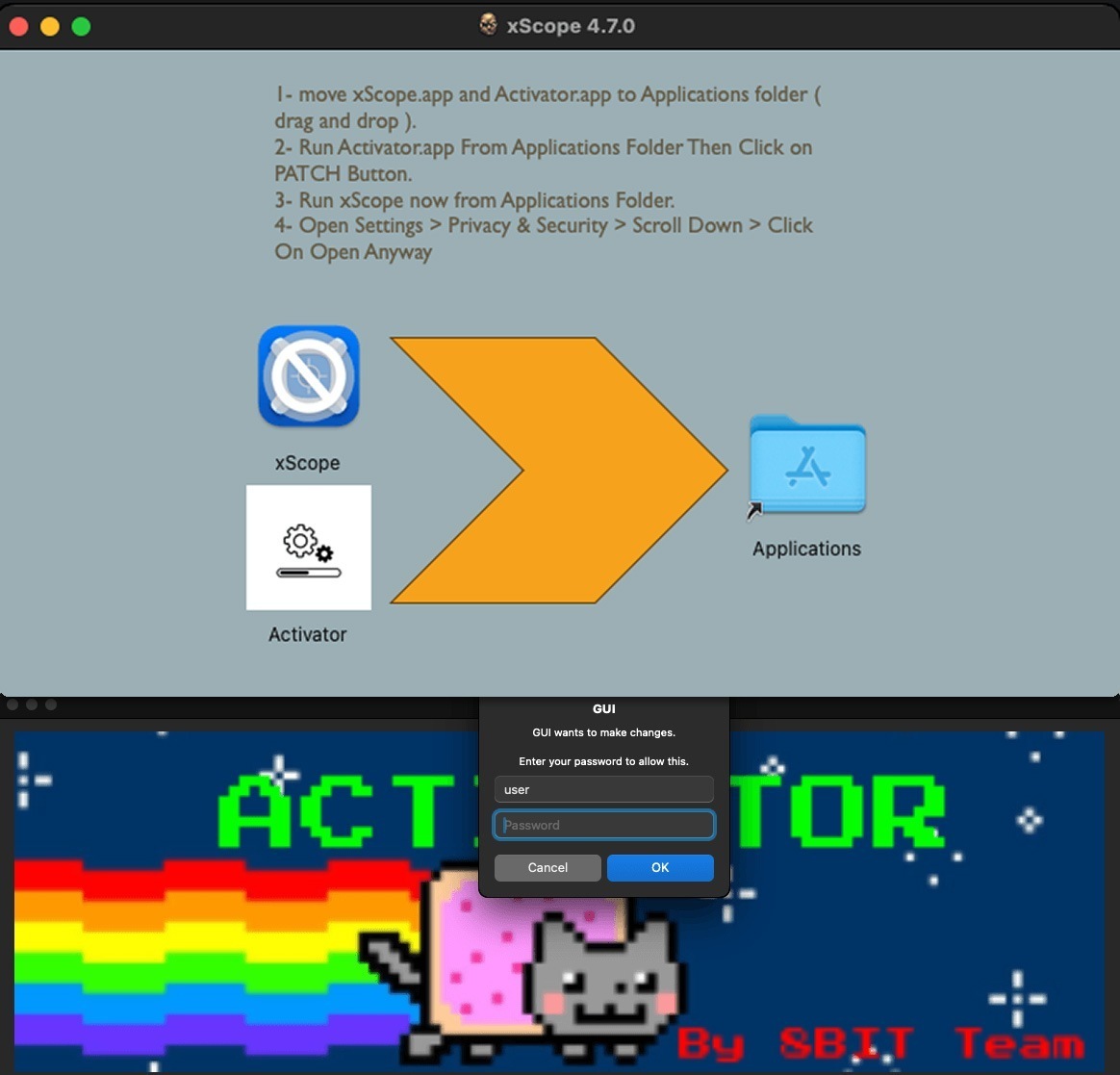
This Trojan’s malicious payload is saved within the “activator”. The cracked app gained’t work till it’s launched.Supply
We might go on with this listing of previous threats, however let’s as a substitute now concentrate on one of many newest assaults concentrating on macOS customers, particularly – the Banshee stealer…
What the Banshee stealer does
Banshee is a fully-fledged infostealer. It is a sort of malware that searches the contaminated system (in our case, a Mac) for worthwhile information and sends it to the criminals behind it. Banshee is primarily targeted on stealing information associated to cryptocurrency and blockchain.
Right here’s what this malware does as soon as it’s contained in the system:
- Steals logins and passwords saved in numerous browsers: Google Chrome, Courageous, Microsoft Edge, Vivaldi, Yandex Browser, and Opera.
- Steals info saved by browser extensions. The stealer targets over 50 extensions – most of that are associated to crypto wallets, together with Coinbase Pockets, MetaMask, Belief Pockets, Guarda, Exodus, and Nami.
- Steals 2FA tokens saved within the Authenticator.cc browser extension.
- Searches for and extracts information from cryptocurrency pockets functions, together with Exodus, Electrum, Coinomi, Guarda, Wasabi, Atomic, and Ledger.
- Harvests system info and steals the macOS password by displaying a pretend password entry window.
Banshee compiles all this information neatly right into a ZIP archive, encrypts it with a easy XOR cipher, and sends it to the attackers’ command-and-control server.
In its newest variations, Banshee’s builders have added the power to bypass the built-in macOS antivirus, XProtect. Curiously, to evade detection, the malware makes use of the identical algorithm that XProtect makes use of to guard itself, encrypting key segments of its code and decrypting them on the fly throughout execution.
How the Banshee stealer spreads
The operators of Banshee primarily used GitHub to contaminate their victims. As bait, they uploaded cracked variations of costly software program comparable to Autodesk AutoCAD, Adobe Acrobat Professional, Adobe Premiere Professional, Seize One Professional, and Blackmagic Design DaVinci Resolve.
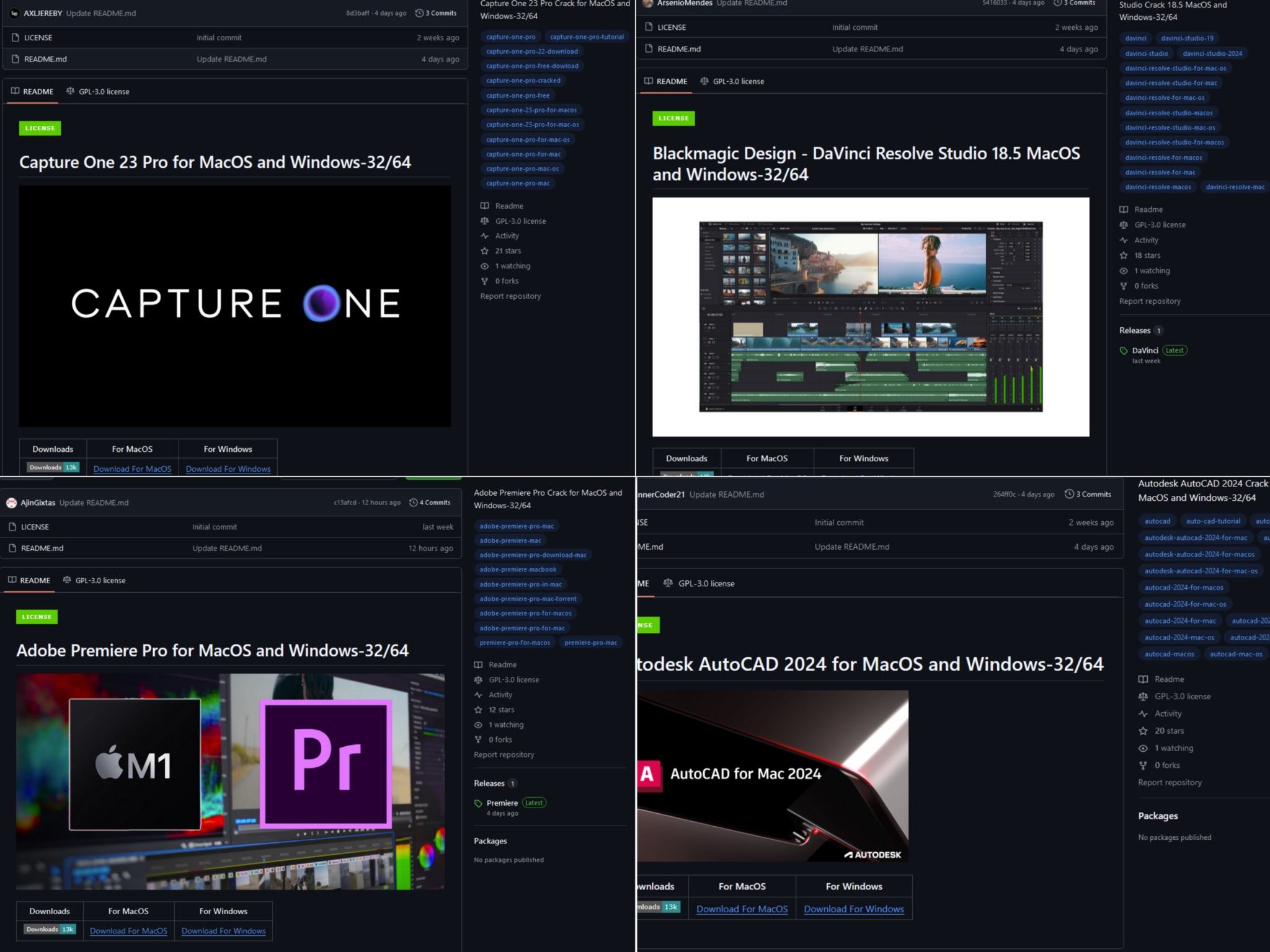
The creators of Banshee used GitHub to unfold the malware below the guise of pirated software program. Supply
The attackers typically focused each macOS and Home windows customers on the similar time: Banshee was typically paired with a Home windows stealer referred to as Lumma.
One other Banshee marketing campaign, found after the stealer’s supply code was leaked (extra on that under), concerned a phishing website providing macOS customers to obtain “Telegram Native” – supposedly designed to guard towards phishing and malware. After all, the downloaded file was contaminated. Curiously, customers of different working methods wouldn’t even see the malicious hyperlink.
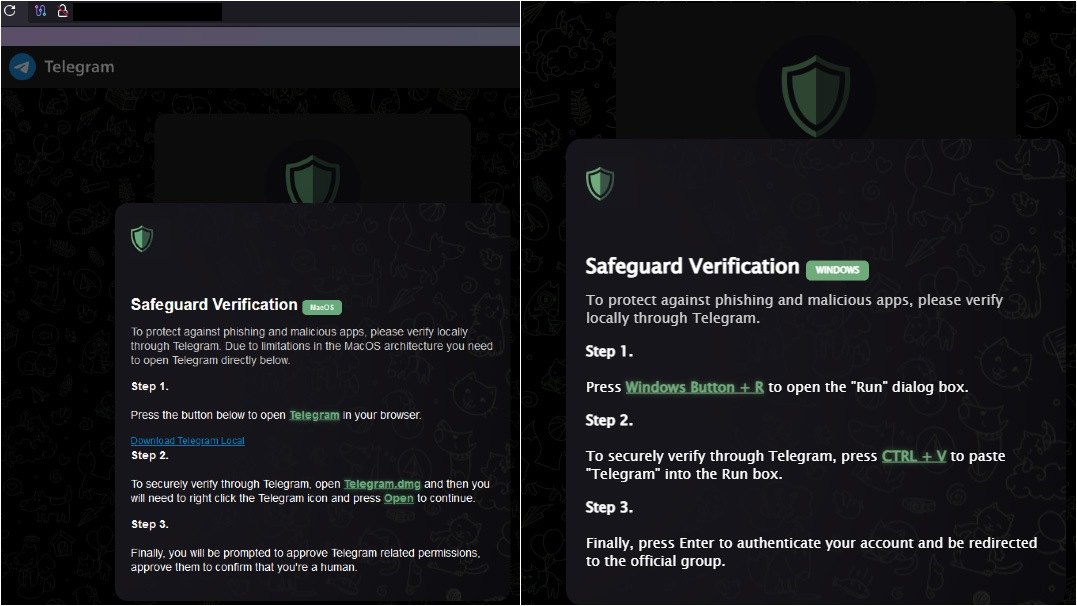
A phishing website presents to obtain Banshee disguised as “Telegram Native”, however solely to macOS customers (left). Supply
The previous and way forward for Banshee
Let’s now flip to Banshee’s historical past, which is absolutely fairly fascinating. This malware first appeared in July 2024. Its builders marketed it as a malware-as-a-service (MaaS) subscription, charging $3000 per 30 days.
Enterprise should not have been nice, as by mid-August they’d slashed the worth by 50% – bringing the month-to-month subscription right down to $1500.
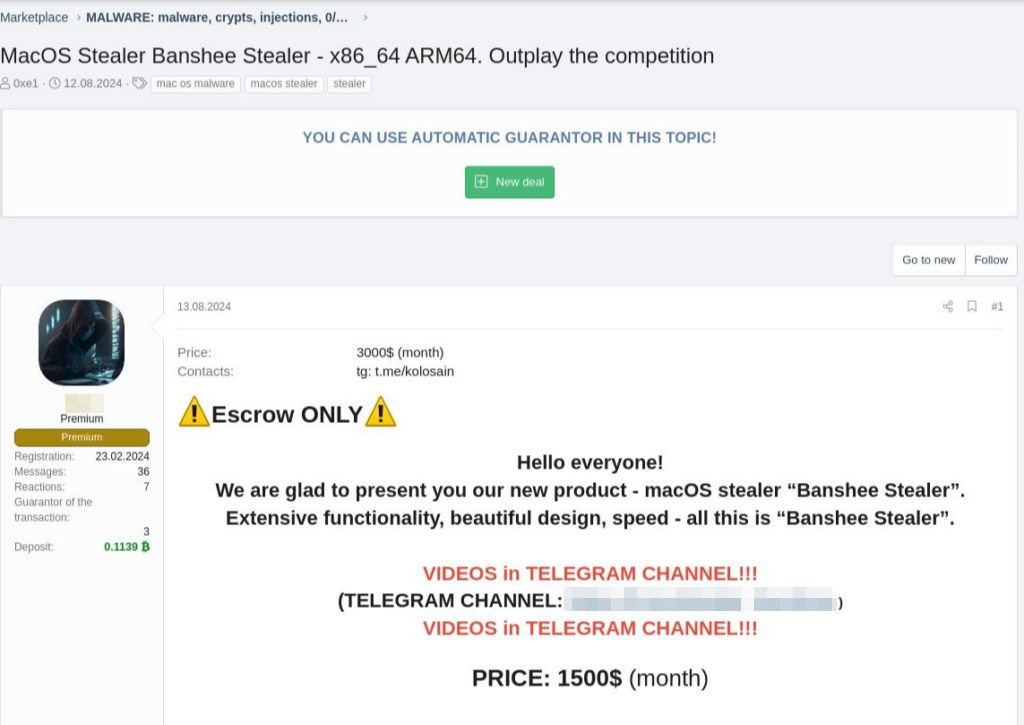
A hacker website advert saying a reduction on Banshee: $1500 as a substitute of $3000 per 30 days. Supply
Sooner or later, the creators both modified their technique, or determined so as to add an associates program to their portfolio. They started recruiting companions for joint campaigns. In these campaigns, Banshee’s creators supplied the malware, and the companions executed the precise assault. The builders’ thought was to separate the earnings 50/50.
Nonetheless, one thing will need to have gone very improper. In late November, Banshee’s supply code was leaked and revealed on a hacker discussion board – thus ending the malware’s industrial life. The builders introduced they had been quitting the enterprise – however not earlier than trying to promote your complete venture for 1BTC, after which for $30,000 (most certainly having realized of the leak).
Thus, for a number of months now, this critical stealer for macOS has been obtainable to basically anybody utterly freed from cost. Even worse, with the supply code additionally obtainable, cybercriminals can now create their very own modified variations of Banshee.
And judging from the proof, that is already taking place. For instance, the unique variations of Banshee stopped working if the working system was operating within the Russian language. Nonetheless, one of many newest variations has eliminated the language examine, which means Russian-speaking customers are actually additionally in danger.
Learn how to shield your self from Banshee and different macOS threats
Listed below are some ideas for macOS customers to remain protected:
- Don’t set up pirated software program in your Mac. The danger of operating right into a Trojan by doing so may be very excessive, and the results will be extreme.
- That is very true for those who use the identical Mac for cryptocurrency transactions. On this case, the potential monetary injury might considerably exceed any financial savings you make on buying real software program.
- Typically, keep away from putting in pointless functions, and keep in mind to uninstall applications you now not use.
- Be cautious with browser extensions. They might appear innocent at first look, however many extensions have full entry to the contents of all internet pages, making them simply as harmful as full-fledged apps.
- And naturally, be sure you set up a dependable antivirus in your Mac. As we’ve seen, malware for macOS is a really actual risk.
Lastly, a phrase on Kaspersky safety merchandise. They will detect and block many Banshee variants with the decision Trojan-PSW.OSX.Banshee. Some new variations resemble the AMOS stealer, to allow them to even be detected as Trojan-PSW.OSX.Amos.gen.



