A safety researcher often called mr.d0x has revealed a publish detailing a brand new method that can be utilized for phishing and probably different malicious actions. The method exploits so-called progressive internet apps (PWAs). On this publish, we talk about what these functions are, why they are often harmful, how attackers can use them for their very own functions, and tips on how to [placeholder Kaspersky Premium]defend your self[/placeholder] towards this risk.
What are progressive internet apps?
PWAs are functions developed utilizing internet applied sciences. Basically, they’re web sites that look and performance similar to native functions put in in your working system.
The overall concept is much like functions constructed on the Electron framework, with one key distinction. Electron apps are like a “sandwich” of a web site (the filling) and a browser (the bread) devoted to operating that website; that’s, every Electron utility has a built-in browser. In distinction, PWAs make the most of the engine of the browser already put in on the consumer’s system to show the identical web site – like a sandwich with out the bread.
All fashionable browsers help PWAs, with Google Chrome and Chromium-based browsers (together with the Microsoft Edge browser that comes with Home windows) providing probably the most complete implementation.
Putting in a PWA (if the respective web site helps it) could be very easy. Simply click on an not easily seen button within the browser’s deal with bar and make sure the set up. Right here’s the way it’s performed, utilizing the Google Drive PWA for instance:
After that, the PWA seems in your system virtually immediately, trying similar to an actual utility — with an icon, its personal window, and all the opposite attributes of a fully-fledged program. It’s not simple to inform from the PWA window that it’s really a browser displaying a web site.
PWA-based phishing
One essential distinction between a PWA and the identical web site opened in a browser is clear within the screenshot above: the PWA window lacks an deal with bar. This very characteristic kinds the muse of the phishing technique mentioned on this publish.
With no deal with bar within the window, attackers can merely draw their very own — displaying an URL that serves their phishing targets. For instance, this one:
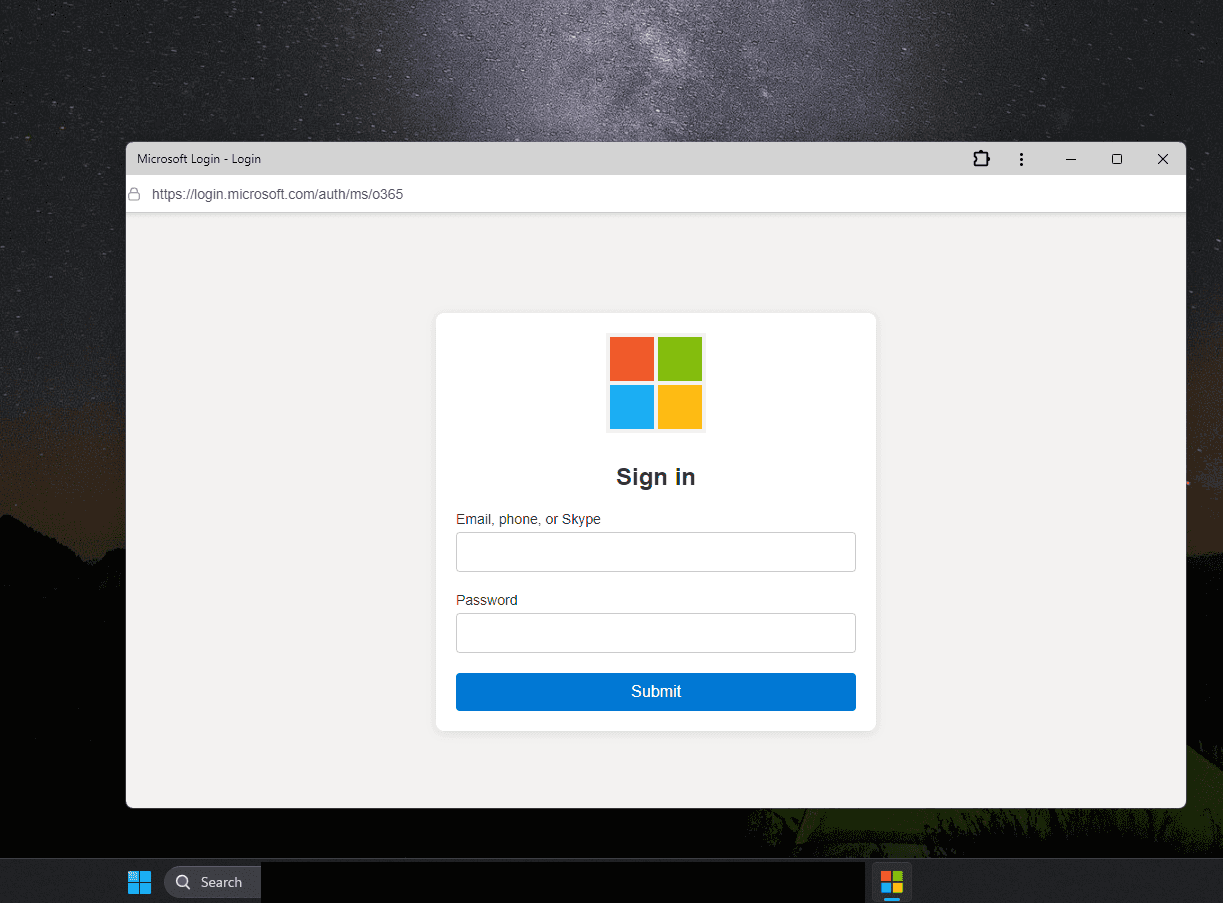
With a PWA, you possibly can convincingly mimic any website — for instance, the Microsoft account login web page. Supply
Attackers can additional improve the deception by giving the PWA a well-known icon.
The one remaining hurdle is convincing the sufferer to put in the PWA. Nonetheless, this may be simply achieved with persuasive language and cleverly designed interface parts.
It’s necessary to notice that throughout the PWA set up dialog, the displayed app title may be something the attacker wishes. The true origin is barely revealed by the web site deal with within the second line, which is much less noticeable:
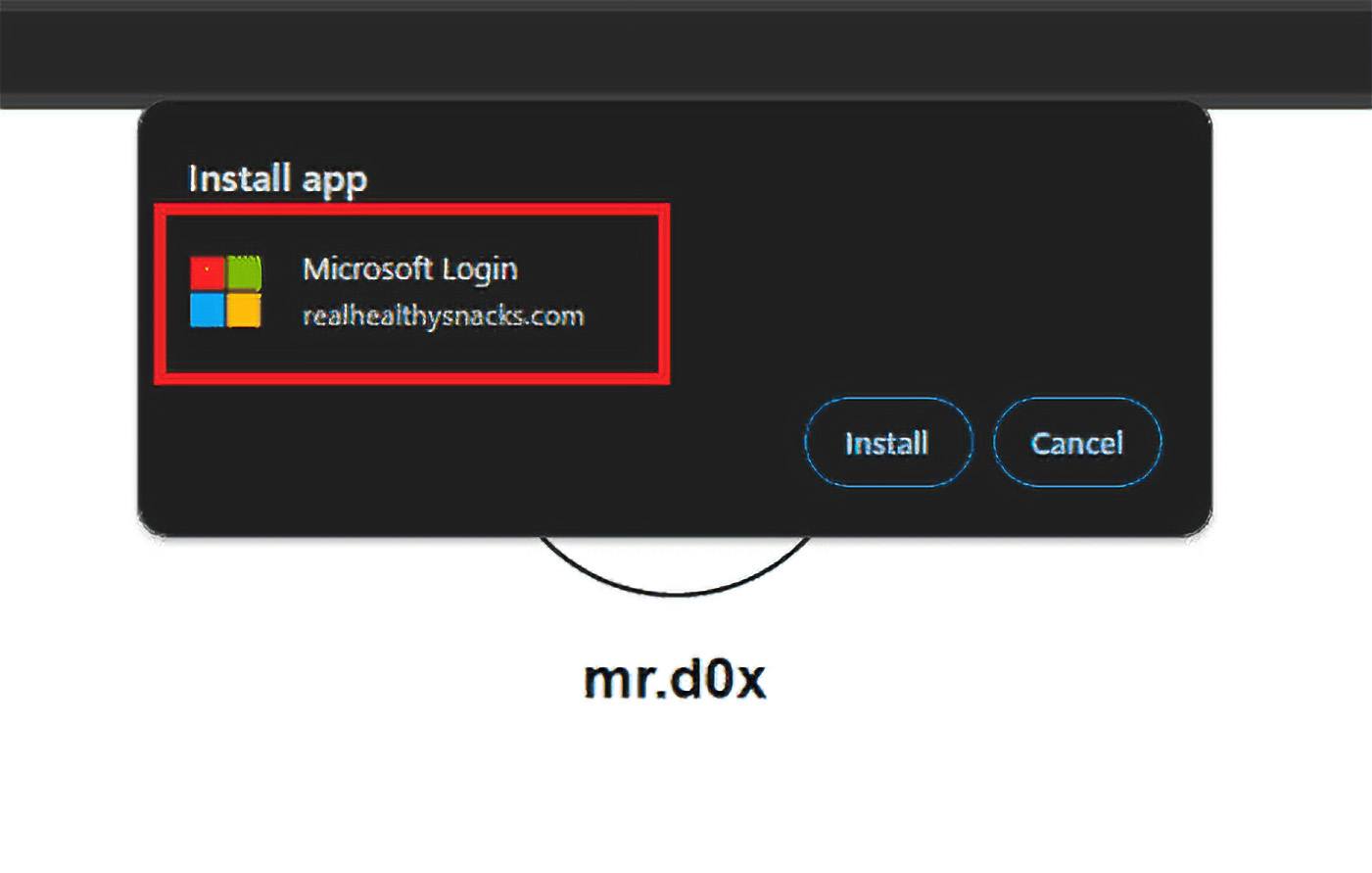
The malicious PWA set up dialog shows a reputation that aids the attacker’s targets. Supply
The method of stealing a password utilizing a PWA usually unfolds as follows:
- The sufferer opens a malicious web site.
- The web site convinces the sufferer to put in the PWA.
- Set up happens virtually immediately, and the PWA window opens.
- A phishing web page with a pretend deal with bar displaying a legitimate-looking URL opens within the PWA window.
- The sufferer enters their login credentials into the shape — handing them on to the attackers.

What phishing utilizing a malicious PWA appears like. Supply
After all, convincing the sufferer to put in a local utility is simply as simple, however there are a few nuances. PWAs set up considerably sooner and require a lot much less consumer interplay in comparison with conventional app installations.
Moreover, growing PWAs is easier, as they’re basically phishing web sites with minor enhancements. These elements make malicious PWAs a robust instrument for cybercriminals.
defend your self from PWA phishing
By the way, the identical mr.d0x beforehand gained recognition for devising the browser-in-the-browser phishing method, which we wrote about a few years in the past. Since then there have been a number of reported situations of attackers using this system not just for stealing account passwords but in addition for spreading ransomware.
Given this precedent, it’s extremely possible that cybercriminals will undertake malicious PWAs and devise novel methods to use this system past phishing.
What are you able to do to guard towards this risk?
- Train warning when encountering PWAs, and chorus from putting in them from suspicious web sites.
- Periodically assessment the record of PWAs put in in your system. As an example, in Google Chrome, sort
chrome://appsinto the deal with bar to view and handle put in PWAs.
- Use a dependable safety answer with safety towards phishing and fraudulent websites, which is able to promptly warn you of potential risks.






