Think about receiving an electronic mail that claims Google has obtained a subpoena to launch the contents of your account. The e-mail appears completely “Googley”, and the sender’s tackle seems official too: no-reply@accounts.google.com. Just a little unnerving (or possibly panic-inducing?) to say the least, proper?
And what luck — the e-mail accommodates a hyperlink to a Google assist web page that has all the main points about what’s taking place. The area identify within the hyperlink appears legit, too, and appears to belong to Google…
Common readers of our weblog have in all probability already guessed that we’re speaking right here a few new phishing scheme. And so they’d be proper. This time, the scammers are exploiting a number of real Google companies to idiot their victims and make the emails look as convincing as doable. Right here’s the way it works…
How phishing electronic mail mimics an official Google notification
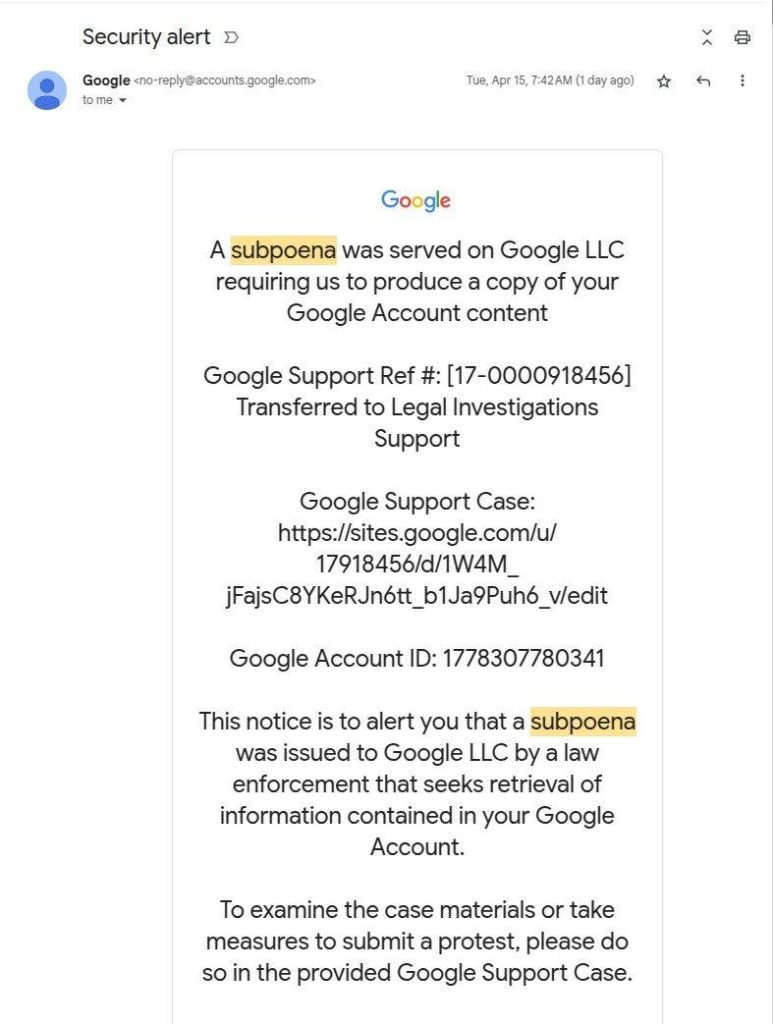
The screenshot under reveals the e-mail that kicks off the assault; and it does a very credible job of pretending to be an alert from Google’s safety system. The message informs the consumer that the corporate has obtained a subpoena requesting entry to the information of their Google account.
The “from” area accommodates a real Google tackle: no-reply@accounts.google.com. That is the very same tackle Google’s safety notifications come from. The e-mail additionally accommodates just a few particulars that reinforce the phantasm of authenticity: a Google Account ID, a assist ticket quantity, and a hyperlink to the case. And, most significantly, the e-mail tells the recipient that in the event that they wish to study extra concerning the case supplies or contest the subpoena, they will accomplish that by clicking a hyperlink.
The hyperlink itself appears fairly believable, too. The tackle consists of the official Google area and the assist ticket quantity talked about above. And it takes a savvy consumer to identify the catch: Google assist pages are positioned at assist.google.com, however this hyperlink results in websites.google.com as an alternative. The scammers are, after all, relying on customers who both don’t perceive such technicalities or don’t discover the phrase substitution.
If the consumer isn’t logged in, clicking the hyperlink takes them to a real Google account login web page. After authorizing, they land on a web page at websites.google.com, which fairly convincingly mimics the official Google assist web site.
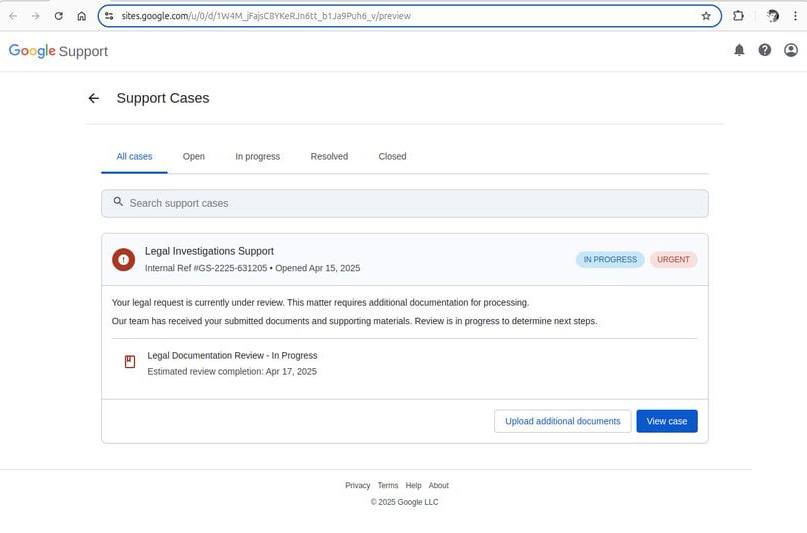
That is what a faux Google Assist web page linked within the electronic mail appears like. Supply
Now, it simply so occurs that the websites.google.com area belongs to the official Google Websites service. Launched again in 2008, it’s a reasonably unsophisticated web site builder — nothing out of the unusual. The vital nuance about Google Websites is that each one web sites created inside the platform are mechanically hosted on a google.com subdomain: websites.google.com.
Attackers can use such an tackle to each lull victims’ vigilance and circumvent numerous safety programs, as each customers and safety options are inclined to belief the Google area. It’s little surprise that scammers have more and more been utilizing Google Websites to create phishing pages.
Recognizing fakes: the satan’s within the (electronic mail) particulars
We’ve already described the primary signal of a dodgy electronic mail: the tackle of the faux assist web page positioned at websites.google.com. Look to the e-mail header for extra pink flags:
Spot the faux: have a look at the “to” and “mailed-by” fields within the header. Supply
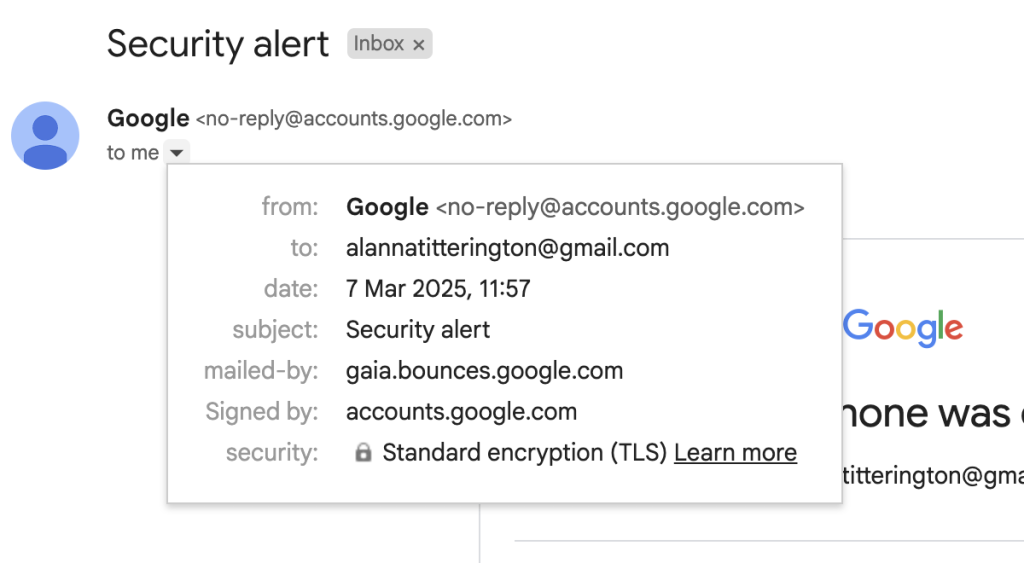
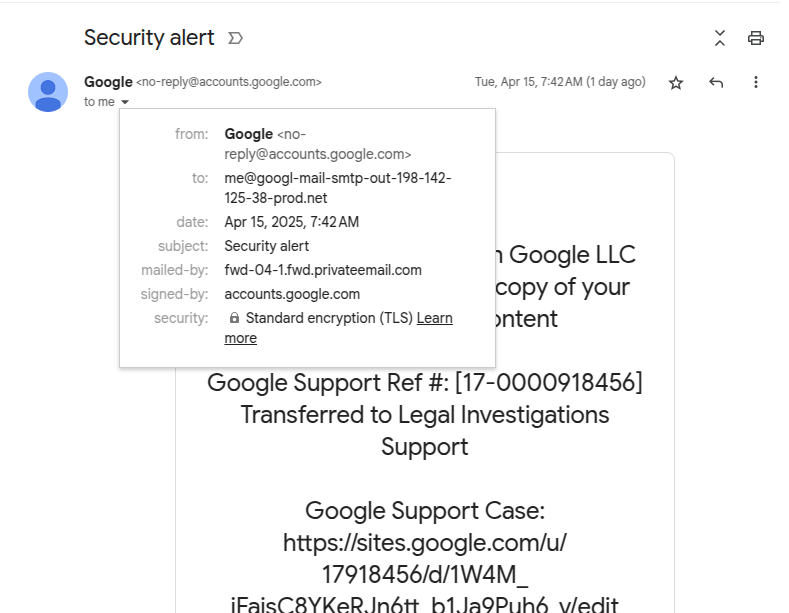
The fields to concentrate to are “from“, “to“, and “mailed-by“. The “from” one appears tremendous: the sender is the official Google electronic mail, no-reply@accounts.google.com.
However lo and behold, the “to” area slightly below it reveals the precise recipient tackle, and this one positive appears phishy: me[@]googl-mail-smtp-out-198-142-125-38-prod[.]internet. The tackle is attempting onerous to mimic some technical Google tackle, however the typo within the firm area identify is a useless giveaway. Furthermore, it has completely no enterprise being there — this area is meant to include the recipient’s electronic mail.
As we hold inspecting the header, one other suspicious tackle pops up within the “mailed-by” area. Now, this one is clearly nowhere close to Google territory: fwd-04-1.fwd.privateemail[.]com. But once more, nonsense like this has no place in an genuine electronic mail. For reference, right here’s what these fields appear like in an actual Google safety alert:
Unsurprisingly, these delicate indicators would probably be misplaced on the typical consumer — particularly once they’re already freaked out by the looming authorized bother. Including to the confusion is the truth that the faux electronic mail is definitely signed by Google: the “signed-by” area reveals accounts.google.com. Within the subsequent a part of this put up, we clarify how the criminals managed to realize this, after which we’ll speak about how you can keep away from changing into a sufferer.
Reconstructing the assault step-by-step
To determine precisely how the scammers managed to ship such an electronic mail and what they have been after, cybersecurity researchers reenacted the assault. Their investigation revealed that the attackers used Namecheap to register the (now-revoked) googl-mail-smtp-out-198-142-125-38-prod[.]internet area.
Subsequent, they used the identical service once more to arrange a free electronic mail account on this area: me[@]googl-mail-smtp-out-198-142-125-38-prod[.]internet. As well as, the criminals registered a free trial model of Google Workspace on the identical area. After that the scammers registered their very own net software within the Google OAuth system, and granted it entry to their Google Workspace account.
Google OAuth is a expertise that permits third-party net purposes to make use of Google account knowledge to authenticate customers with their permission. You’ve probably encountered Google OAuth as a method to authenticate for third-party companies: it’s the system you utilize each time you click on a “Sign up with Google” button. Apart from that, purposes can use Google OAuth to acquire permission to, for instance, save information to your Google Drive.
However let’s get again to our scammers. After a Google OAuth software is registered, the service permits sending a notification to the e-mail tackle related to the verified area. Apparently sufficient, the administrator of the online software is free to manually enter any textual content because the “App identify” — which appears to be what the criminals exploited.
Within the screenshot under, researchers show this by registering an app with the identify “Any Phishing E mail Textual content Inject Right here with phishing URLs…”.
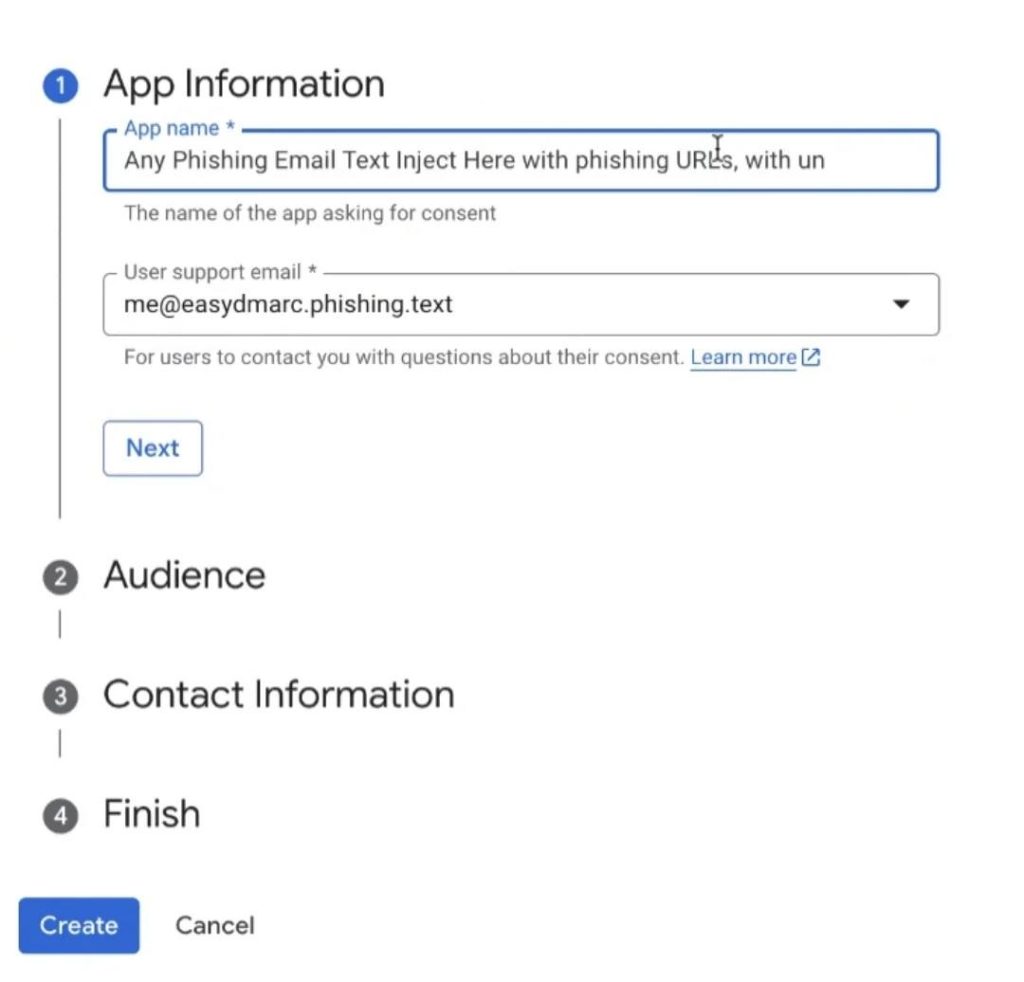
Registering an online app with an arbitrary identify in Google OAuth: the textual content of a rip-off electronic mail with a phishing hyperlink may be entered as a reputation. Supply
Google then sends a safety alert containing this phishing textual content from its official tackle. This electronic mail goes to the scammers’ electronic mail tackle on the area registered by means of Namecheap. This service permits forwarding the obtained notification from Google to any addresses. All they want do is about a particular forwarding rule and specify the e-mail addresses of potential victims.
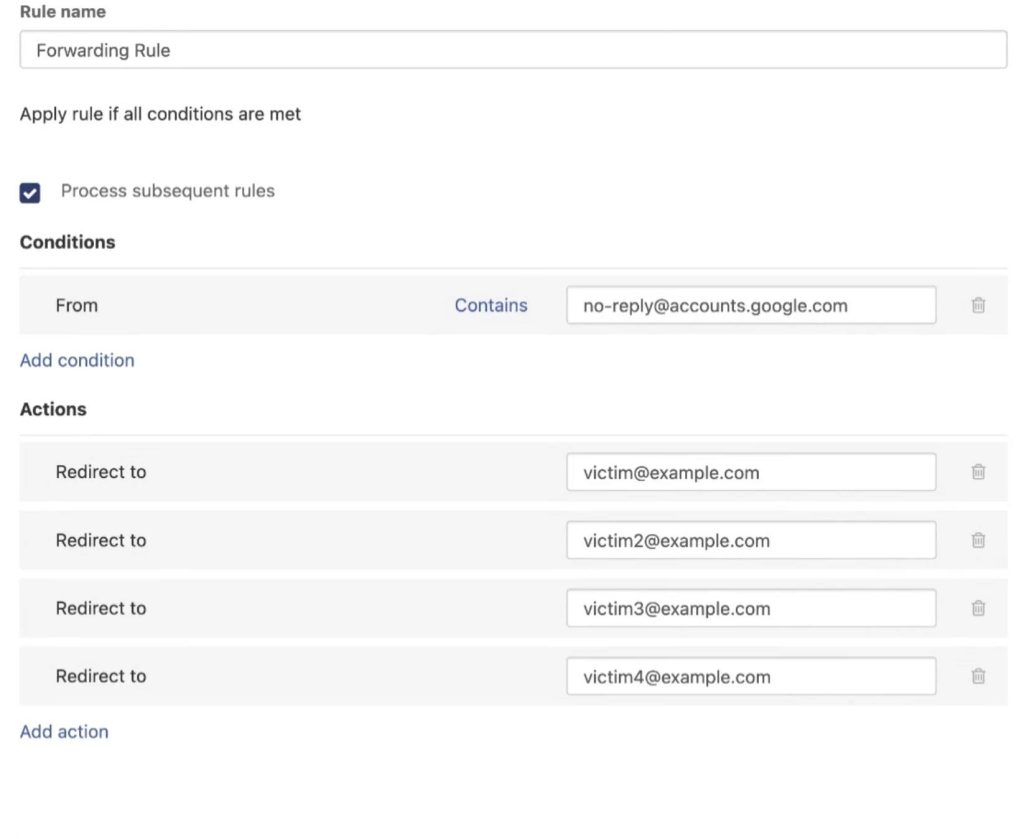
Establishing a forwarding rule that permits sending the faux electronic mail to a number of recipients. Supply
The right way to defend your self from phishing assaults like this one
It’s not fully clear what the attackers have been hoping to realize with this phishing marketing campaign. Utilizing Google OAuth to authenticate doesn’t imply the sufferer’s Google account credentials are shared with the scammers. The method generates a token that solely offers restricted entry to the consumer’s account knowledge — relying on the permissions the consumer licensed and the settings configured by the scammers.
The faux Google Assist web page the deceived consumer lands on prompt that the aim was to persuade them to obtain some “authorized paperwork” supposedly associated to their case. The character of those paperwork is unknown, however likelihood is they contained malicious code.
The researchers reported this phishing marketing campaign to Google. The corporate acknowledged this as a possible danger for customers and is presently engaged on a repair for the OAuth vulnerability. Nevertheless, how lengthy it can take to resolve the problem stays unknown.
Within the meantime, right here’s some recommendation that will help you keep away from changing into a sufferer of this and different intricate phishing schemes.
- Keep calm should you get an electronic mail like this. Start by rigorously inspecting all the e-mail header fields and evaluating them to official emails from Google — you probably have some in your inbox. In the event you see any discrepancies, don’t hesitate to hit “Delete”.
- Be cautious of internet sites on the google.com area which might be created with Google Websites. These days, scammers have been more and more exploiting it for a variety of phishing schemes.
- As a common rule, keep away from clicking hyperlinks in emails.
- Use a sturdy safety answer that may present well timed warnings about hazard and block phishing hyperlinks.
Comply with the hyperlinks under to examine 5 extra examples of out-of-the-ordinary phishing.