Digitalization of enterprise – particularly within the small and medium-sized section – permits for fast upscaling, higher customer support, and entry into new markets. On the draw back, digitalization amplifies the injury brought on by a cyberattack, and complicates the restoration course of. Provided that firm assets are all the time restricted, which assaults ought to be deflected first?
To reply this query, we studied the INTERPOL Africa Cyberthreat Evaluation Report 2025. The doc is helpful as a result of it collates police cybercrime statistics and information from data safety corporations – together with Kaspersky – permitting us to match the quantity and varieties of assaults with the precise injury they triggered. This information can be utilized to construct an organization’s data safety technique.
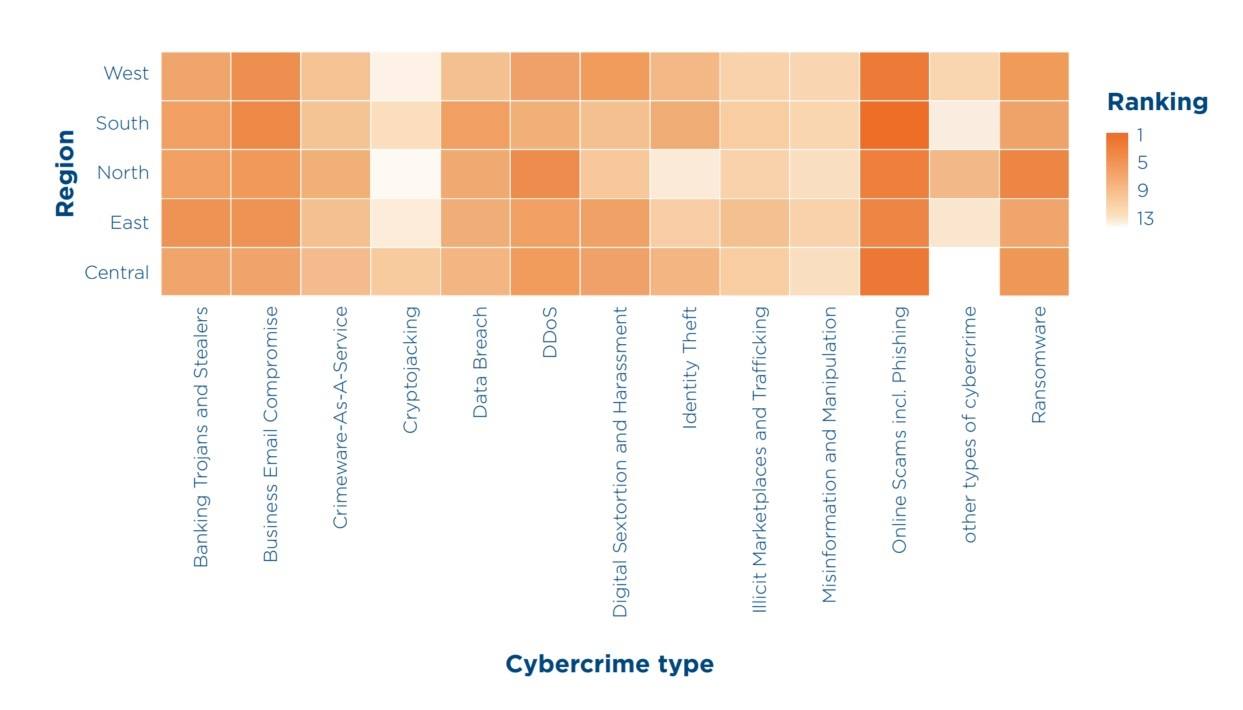
Common rating of cybercrime sorts by reported monetary affect throughout African subregions, based mostly on INTERPOL member nation information. Supply
Focused on-line fraud
Fraudulent operations have been the clear chief when it comes to injury triggered throughout the continent. They’re gaining momentum according to the rising reputation of cell banking, digital commerce, and social media. Along with mass phishing geared toward private and cost information theft, focused assaults are rising at a speedy fee. Scammers are grooming potential victims in messenger apps for months, constructing belief and guiding them right into a cash extortion scheme – for instance, a pretend cryptocurrency funding. Such schemes typically exploit romantic relationships and are subsequently referred to as romance scams, however there are different variations. In Nigeria and Ivory Coast, for instance, scammers have been arrested for attacking small media platforms and promoting companies. Posing as advertisers, they stole virtually 1.5 million U.S. {dollars} from victims.
The truth that 93% of Africans use plain outdated WhatsApp moderately than company communication instruments for work considerably boosts the success fee of assaults on workers and firm homeowners.
Ransomware incidents
Press headlines could give the impression that ransomware operators primarily goal giant organizations, however the statistics within the report debunk this concept – displaying that each the variety of assaults and the precise monetary injury triggered are vital throughout all enterprise segments. What’s extra, there’s a direct hyperlink between the extent of digitalization and the variety of assaults. So, if an organization observes an general improve in “digitized” enterprise exercise in its market section, the menace stage is certain to rise accordingly. In Africa, “associates” of the biggest and most harmful ransomware-as-a-service platforms – comparable to LockBit and Hunters Worldwide – are accountable for main incidents on a nationwide scale.
Among the many foremost ransomware incidents in Africa – hardly recognized about outdoors the continent – we spotlight the next: the theft of $7 million from Nigerian fintech firm Flutterwave; assaults on Cameroonian electrical energy provider ENEO; a large-scale ransomware assault to exfiltrate information from Telecom Namibia; and the focusing on of South Africa’s Nationwide Well being Laboratory Service (NHLS), which led to canceled operations and the lack of hundreds of thousands of lab take a look at outcomes.
Banking Trojans and infostealers
Though the direct losses from banking Trojans and infostealers fell outdoors the top-three when it comes to injury, it’s the “successes” of this prison trade which have a direct affect on the quantity and severity of different assaults – primarily ransomware and enterprise e mail compromise (BEC). After stealing what credentials they’ll from hundreds of customers with infostealers, attackers filter and group them by numerous standards, then promote curated units of accounts on the illicit market. This permits different criminals to purchase passwords to infiltrate organizations of curiosity to them.
Enterprise e mail compromise
For small and medium companies primarily utilizing public providers like Gmail or Workplace 365, an infection with an infostealer offers attackers full entry to company correspondence and enterprise operations. The attackers can then exploit this to trick clients and counterparties into paying for items and providers to a fraudulent account. BEC assaults have a agency maintain on the prime of the injury charts, and small companies can fall sufferer to them in two methods. First, cybercriminals can extract cash from bigger shoppers or companions by impersonating the compromised small enterprise. Second, it’s simpler with a small enterprise to steer the proprietor or accountant to switch cash than it’s with a big group.
There are a number of giant prison syndicates based mostly in Africa which can be accountable for worldwide BEC operations inflicting multi-billion-dollar injury. Their targets additionally embody African organizations — primarily these within the monetary and worldwide commerce sectors.
How one can shield enterprise from cyberthreats
To successfully counter digital threats, legislation enforcement companies must share information with business data safety corporations that harness telemetry to establish menace distribution hotspots. Latest successes of such partnerships embody operations Serengeti (1000 arrests, 134 000 malicious on-line assets disabled), Purple Card (300 arrests), and Safe (32 arrests, 20 000 malicious assets disabled). These operations, performed below the auspices of INTERPOL, used cyberthreat intelligence obtained from companions – together with Kaspersky.
However companies can’t depart cybersecurity solely to the police; they should implement easy however efficient safety measures of their very own:
- Allow phishing-resistant multi-factor authentication (MFA) for all on-line accounts: Google, Microsoft, WhatsApp, and so on.
- Set up dependable anti-malware safety on all company and private gadgets. For company gadgets, centralized safety administration is really useful – as applied, for instance, in Kaspersky Endpoint Detection and Response.
- Maintain common cybersecurity coaching – for instance, utilizing our Kaspersky Automated Safety Consciousness platform. This can scale back the danger of your organization falling sufferer to BEC and phishing. All workers, together with administration, ought to take part in coaching repeatedly.
- Again up all firm information regularly and in such a method that the backups can’t be destroyed throughout an assault. This implies backing up information both to media which can be bodily disconnected from the community, or to cloud storage the place a coverage prohibits information deletion.



