Our researchers have uncovered a number of malicious pretend extensions focusing on Solidity builders within the Open VSX market. A minimum of one firm has fallen sufferer to the attackers distributing these extensions — dropping roughly US$500 000 in crypto property.
Threats related to malware distribution in open-source repositories have been identified about for a very long time. Regardless of this, customers of AI-powered code editors like Cursor AI and Windsurf are compelled to make use of the open-source extension market Open VSX, as they don’t have any different supply for the extensions these platforms want.
Nevertheless, extensions on Open VSX don’t endure the identical rigorous checks as these on the Visible Studio Market. This loophole permits attackers to distribute malicious software program disguised as reputable options. On this publish, we dive into the small print of the malicious Open VSX extensions investigated by our specialists, and clarify how you can stop related incidents inside your group.
Dangers for customers of Open VSX extensions
In June 2025, a blockchain developer who had simply misplaced roughly US$500 000 in crypto property to attackers reached out to our specialists and requested an incident investigation. Whereas inspecting a disk picture from the compromised system, our researchers observed a suspicious part of an extension named Solidity Language for the Cursor AI improvement atmosphere. The part was executing a PowerShell script — a positive signal of malicious exercise.
The extension was put in from the Open VSX market, the place it had tens of hundreds of downloads (presumably inflated by bot exercise). The outline claimed to optimize improvement of sensible contract code written within the Solidity language. Nevertheless, evaluation of the extension revealed it had no helpful performance by any means. The builders who put in it mistook the shortage of marketed options for a bug, didn’t instantly examine, and simply continued their work.
The browser extension wasn’t really defective; it was pretend. As soon as put in, it contacted a command-and-control server to obtain and run a malicious script. This script then put in ScreenConnect — a distant entry software — on the sufferer’s pc.
The attackers used ScreenConnect to add further malicious payloads. Within the incident our specialists investigated, these instruments particularly allowed the attackers to steal passphrases for the developer’s crypto wallets after which syphon off cryptocurrency. An in depth technical description of the assault, together with indicators of compromise, is accessible in a Securelist weblog publish.
Manipulating search: how attackers promote malicious extensions
A glance into the Open VSX market revealed a regarding pattern: a pretend extension, deceptively named “Solidity Language”, ranked fourth in search outcomes, whereas the reputable extension, merely known as solidity, appeared all the best way down at eighth. It’s no shock then that the developer downloaded the counterfeit as an alternative of the real article.
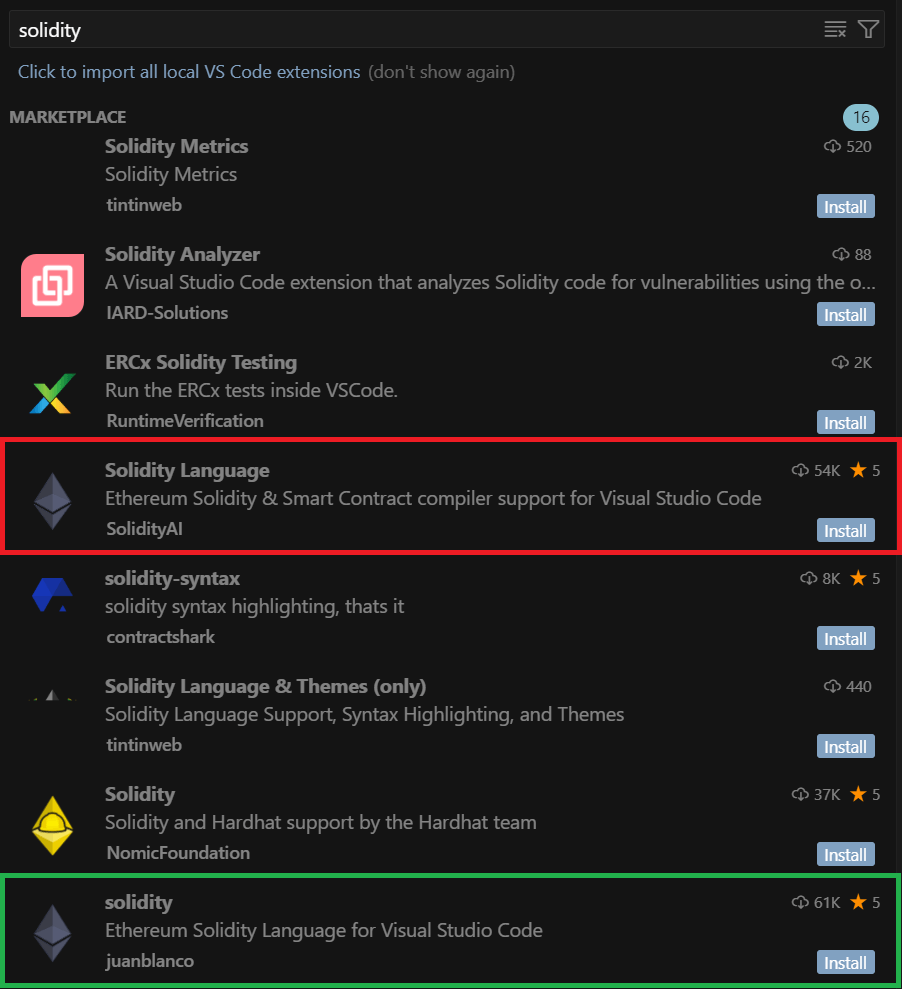
Search outcomes for “solidity”: the malicious extension (crimson) vs. the reputable one (inexperienced)
This rating is sort of stunning, particularly contemplating that on the time of the search, the reputable extension had extra downloads: 61 000 in comparison with the pretend’s 54 000.
The important thing lies in Open VSX’s rating algorithm. It doesn’t solely depend on obtain counts to find out relevance; it additionally considers different components like verification standing, scores, and recency. That is precisely how the attackers managed to outrank the real extension in search outcomes: the pretend one had a more moderen replace date.
The pretend plugin was faraway from the Open VSX market on July 2, 2025, proper after the cryptocurrency heist. Nevertheless, the very subsequent day, we discovered one other malicious bundle with the identical title as the unique extension, “solidity”, and the identical dangerous performance as Solidity Language.
Moreover, our researchers used an open-source component-monitoring device to find one more malicious bundle in Open VSX. A number of particulars hyperlink this bundle to the identical cybercriminals.
Why do builders should depend on the Open VSX market?
The Visible Studio Market, Microsoft’s official retailer, has lengthy been the first business supply for extensions. It consists of automated scanning for malicious code, sandboxed execution of extensions for behavioral evaluation, monitoring for anomalies in extension utilization, and a variety of different options to assist establish dangerous extensions. Nevertheless, its licensing settlement dictates that solely options to be used with Visible Studio merchandise may be revealed within the Visible Studio Market.
Consequently, customers of more and more in style AI-powered code editors like Cursor AI and Windsurf should set up extensions from another retailer: Open VSX. The issue is that this platform has much less stringent extension vetting, which makes it simpler to distribute malicious packages in comparison with Microsoft’s official market.
To be honest, attackers typically handle to publish malicious extensions even within the safer Visible Studio Market. For example, this spring, specialists discovered three malicious extensions there with an an infection scheme similar to the one described on this publish, additionally focusing on Solidity builders.
How one can keep secure?
Irrespective of the place you’re putting in extensions from, we advocate the next:
- Watch out when looking out marketplaces.
- At all times be aware of who the developer of an extension is.
- Test the code and habits of extensions you put in.
- Use an XDR resolution to observe any suspicious exercise inside the company community.