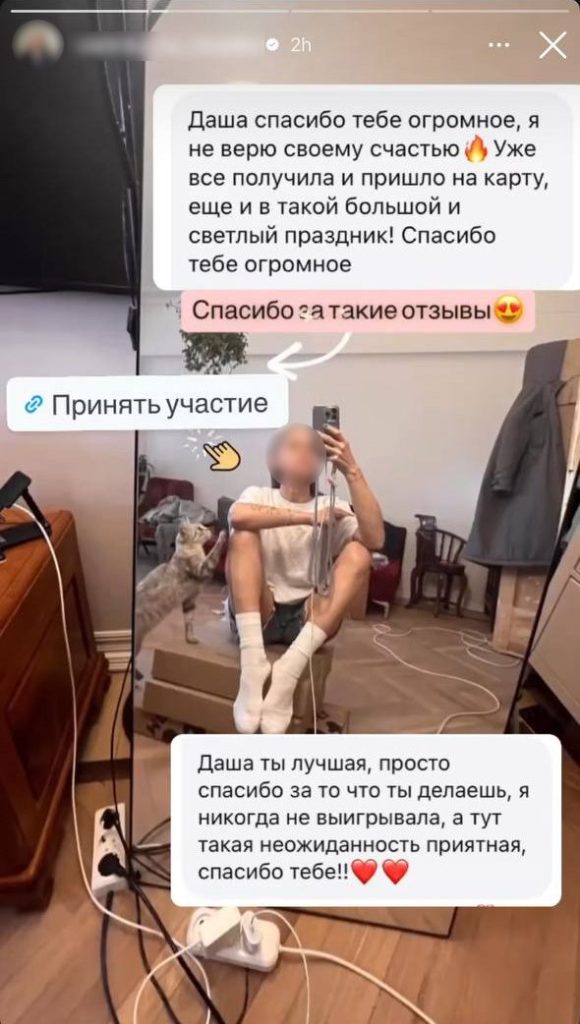
“I’m making a gift of $125 000! Be a part of the mission through the hyperlink in my profile!”
— instantly, a well-liked Russian blogger launches an enormous money giveaway on Instagram. A well-recognized face, talking in upbeat voice and assured tone, seems in Tales. All of it seems to be too good to be true…
That’s as a result of it’s. There’s no actual mission. The blogger didn’t launch something. Her account was merely hijacked. And the scammers went past the standard methods: not solely did they steal entry and put up a pretend giveaway hyperlink, however additionally they stitched collectively a brand new video from outdated footage and dubbed it with a voice generated by neural networks. Learn the entire story to find out how Instagram accounts are stolen by swapping SIM playing cards — and what you are able to do to guard your self.
An virtually flawless rip-off marketing campaign
With the rise of AI instruments, scammers have instantly gotten “smarter”. Earlier than, having hacked a blogger, they’d have simply posted phishing hyperlinks and hoped the viewers would chew. Now they will run full-fledged PR campaigns from the stolen account. Right here’s what the scammers did this time:
- One brief video. They wrote a script, voiced it with a deepfake of the blogger’s voice, and edited collectively visuals from her beforehand posted Reels.
- A textual content put up. They revealed a photograph with a tear-jerking caption about how onerous it was to launch the mission, making an attempt to imitate the blogger’s traditional tone.
- 4 Tales. They reused outdated Tales the place the blogger talked about an actual mission, added a hyperlink to a phishing web site, and reposted them.
All this lends the pretend mission an air of legitimacy — since bloggers typically use content material like this throughout completely different codecs to advertise actual initiatives. The scammers spared no effort — even throwing in some testimonials from grateful followers; pretend ones, in fact.
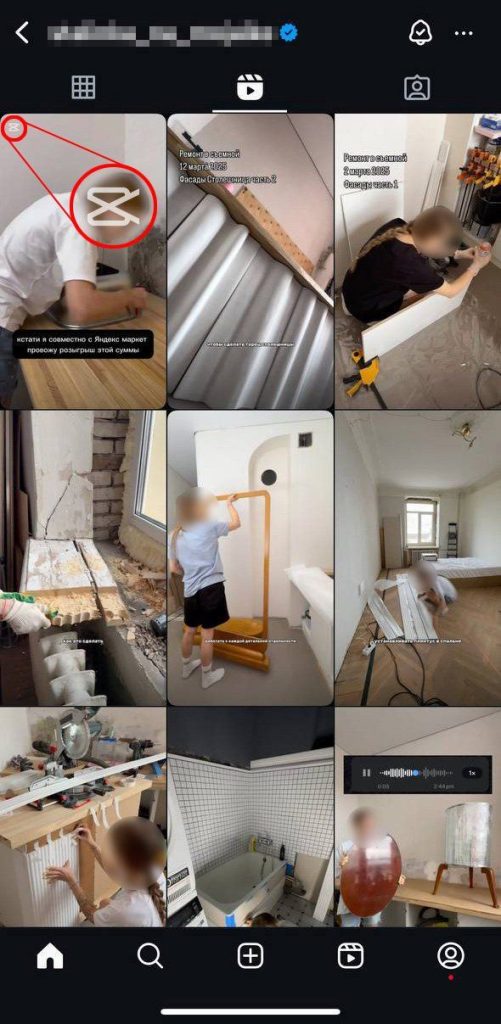
Let’s take a more in-depth have a look at the video. At first look, it’s surprisingly high-quality. It follows all of the weblog’s guidelines: the weblog’s subject (dwelling renovation), voiceover narration, fast enhancing. However upon nearer examination, the phantasm is shattered. Take a look at the screenshot under: just one video has a watermark within the top-left nook — from the free model of the enhancing app CapCut. That’s the pretend. The opposite movies don’t have this watermark — as a result of the actual blogger both makes use of the premium model or edits with one other app.
There’s one other element: the subtitles. In all her actual movies, the blogger makes use of plain white textual content with no background. Within the pretend video, the textual content is white on a black background. Certain, bloggers typically change their type, however normally settings like font and shade are saved of their enhancing software program and keep constant.
What occurs in the event you click on the hyperlink within the profile?
Right here’s the place it will get attention-grabbing. What sort of “mission” precisely had been the scammers selling, and what occurs in the event you click on the hyperlink?
For those who’re utilizing a tool with out dependable safety (which might warn you in the event you attempt to go to a phishing web site), you’ll land on a really fundamental web page: a flashy picture, some eye-catching textual content, and a Declare your prize button. Clicking such buttons sometimes results in one in every of two outcomes: you’ll be requested to pay a fee, or prompted to enter your information — purportedly to obtain your winnings. In any case, you’ll be requested to share your financial institution particulars. In fact, no prize is coming — it’s pure phishing.
A lady with {dollars} and a smartphone symbolizes the riches that await… the scammers after they steal your banking account
How did attackers hack the blogger’s Instagram account?
Essential: there’s no official model of how the account was compromised but. It’s a high-profile case, and the blogger has reported it to the police. She at present suspects she fell sufferer to a SIM-swap assault. Briefly, which means the scammers satisfied her cell supplier to switch her cellphone quantity to a brand new SIM card. There are two predominant methods this may be completed:
- Outdated technique. Scammers forge an influence of lawyer and bodily go to the cell supplier’s workplace to request a SIM substitute.
- New technique. The criminals entry the sufferer’s on-line account supplied by the cell provider and remotely challenge an eSIM.
SIM swapping allowed scammers to bypass two-factor authentication and persuade Instagram help that they had been the actual account house owners. Comparable methods can be utilized with any service that sends verification codes through textual content — together with on-line banks.
As for the blogger’s authentic SIM card, it immediately changed into a ineffective piece of plastic: no web, no calls, no texts.
Easy methods to shield your account from being hacked
Listed below are the fundamental guidelines to forestall most sorts of account hacks — whether or not on messaging apps, social networks, boards, or different websites:
- Use superior two-factor authentication with app-generated codes as an alternative of texts (SMS). For Instagram, we suggest additionally including a backup technique: Settings and exercise → Accounts Middle → Password and safety → Two-factor authentication → Add a backup technique. Then, obtain a devoted app to generate your login codes.
- Set up dependable safety on all of your gadgets. Pre-installed antivirus safety will block phishing hyperlinks and shield you from varied malware.
- Create robust, distinctive passwords. For those who’re brief on creativeness, let Kaspersky Password Supervisor do it for you and maintain them protected.
- Comply with the golden rule: every service has its personal distinctive password. That manner, hackers received’t get entry to every part without delay.
- Ask your cell operator if it’s attainable to both utterly prohibit servicing you remotely, or arrange a particular code you could state in each interplay — distant or in particular person. This may help shield you from SIM-swapping assaults.
Extra to learn on defending your accounts from hacking: