As of late, it’s not simply authorities companies or personal detectives who can spy on you. Monitoring has change into really easy and low-cost that jealous spouses, automobile thieves, and even overly suspicious employers are doing it. They don’t need to peek round corners, conceal in shops, and even get near their goal in any respect. A smartphone and a Bluetooth monitoring beacon — like an Apple AirTag, Samsung Sensible Tag or Chipolo — will do the job completely. In keeping with one of many lawsuits filed towards Apple, this methodology of spying is utilized in a wide range of crimes — from stalking ex-partners to planning murders.
Fortunately for all of us, there’s safety! As a part of Kaspersky’s anti-stalking marketing campaign, we’ll clarify how you possibly can be tracked and what you are able to do about it.
On-line and offline monitoring
Surveillance of a sufferer is often carried out in one in every of two methods.
Technique one: purely software-based. A business monitoring app is put in on the sufferer’s smartphone — we name this class of apps stalkerware or spouseware. Such apps are sometimes marketed as “parental management apps”, however they differ from respectable parental controls as a result of the app’s exercise is saved hidden after set up. Most frequently, the app is solely invisible on the gadget, although generally it disguises itself as one thing innocuous, like a messenger, recreation or photo-gallery app. Stalker apps can repeatedly transmit the sufferer’s geolocation to a server, ship messages and different confidential knowledge from the gadget to an attacker, and even activate the microphone to report audio.
The principle disadvantage of stalkerware for the attacker is the issue of set up — it requires having access to the sufferer’s unlocked smartphone for a while. That’s why, in lots of instances, particularly when it’s an ex-partner or automobile thief doing the stalking, they use the opposite methodology.
Technique two: a wi-fi beacon. A monitoring gadget is planted on the sufferer. In a automobile, it is perhaps hidden in an not noticeable spot, akin to behind the license plate; for an individual, the tracker may very well be slipped right into a bag or amongst different private objects.
Initially, Bluetooth trackers — small gadgets in regards to the measurement of a coin — had been invented to assist find misplaced belongings akin to keys, wallets or baggage. Nonetheless, if planted on a goal, their actions might be tracked in close to real-time utilizing a particular app. By the way, lots of right now’s Bluetooth headphones even have built-in monitoring performance to make them simpler to search out — and these too can be utilized for stalking. So, if you happen to occur to discover a pair of fancy headphones mendacity round, don’t begin considering it’s your fortunate day — they might have been intentionally planted in an effort to observe your actions, even after you pair them with your personal smartphone.
Monitoring expertise works even when the beacon is properly past the Bluetooth vary of the stalker’s smartphone: different smartphones assist find the “misplaced” merchandise. Lots of the newest Android and iOS gadgets report the situation of close by seen beacons to the central servers of Google or Apple. Because of this, these tech giants are in a position to find any beacon if there’s any fashionable Bluetooth-enabled smartphone with web entry close by.
The most well-liked beacon remains to be the Apple AirTag, and Apple has gone to plenty of bother for the reason that first product launch to guard customers from malicious use of the tracker. The newest AirTags begin beeping to draw consideration if they continue to be away from their proprietor’s smartphone for too lengthy. Nonetheless, attackers can simply bypass this safety by damaging the speaker on the tracker. Such hacked tags with disabled audio system may even by purchased — simply.
defend your self from surveillance
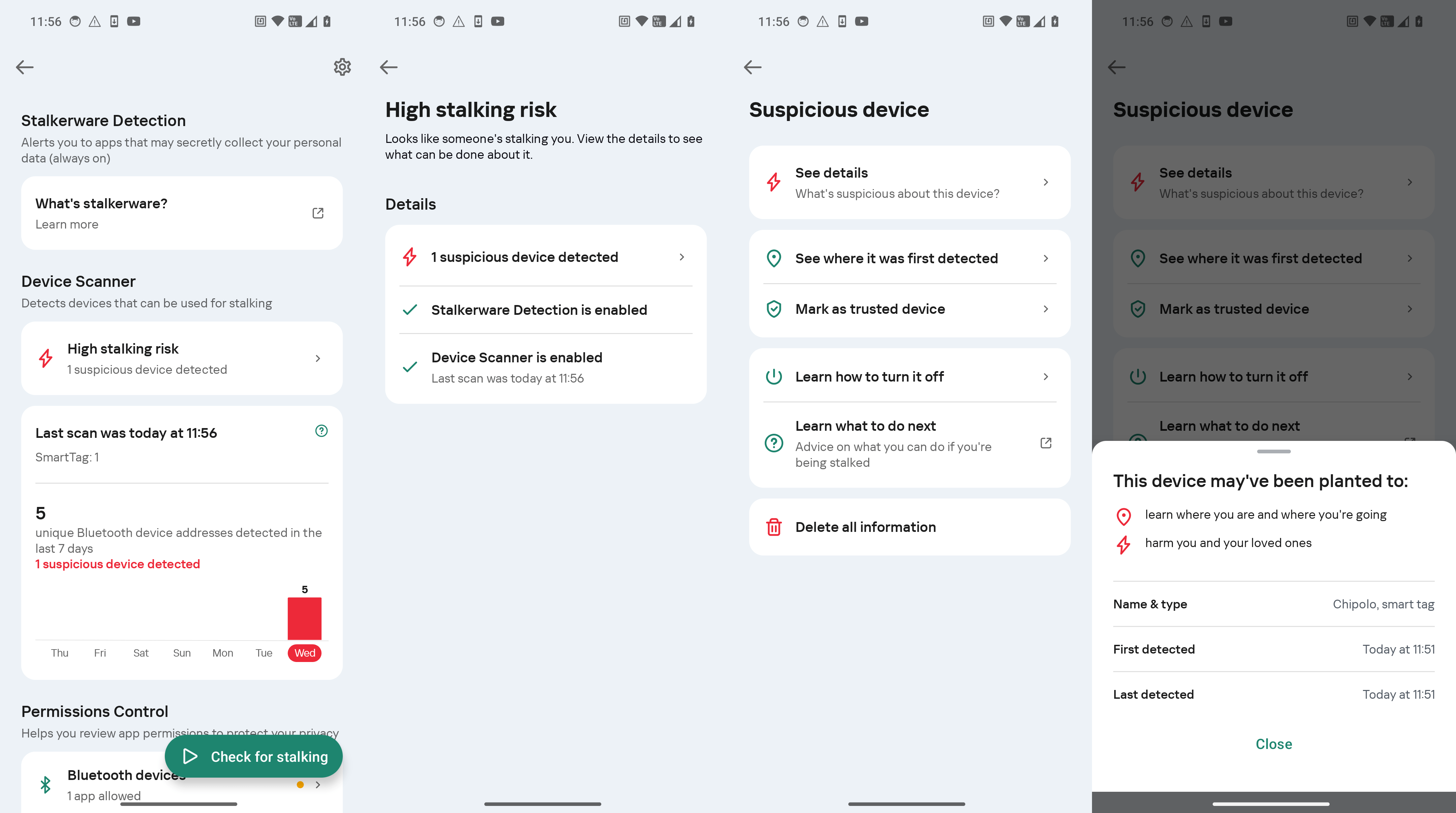
To safeguard your self from each on-line and offline monitoring, we suggest utilizing Kaspersky for Android. This device now consists of the “Who’s spying on me” characteristic, which lets you rapidly detect surveillance.
Safety towards monitoring beacons. Happily, by their very nature, trackers can by no means be fully invisible, as they’re continually signaling their presence by way of Bluetooth. A smartphone geared up with dependable safety can alert the consumer if an unregistered Bluetooth gadget is continuously detected close by or in varied totally different areas. If such a tool strikes round with you or stays shut for too lengthy, Kaspersky for Android will notify you.
Upon discovering a tracker, it’s important to look at it carefully. Generally, the scenario could also be harmless, akin to if a member of the family you spend plenty of time with has a tracker hooked up to their keys. Often, there could also be trackers on rental automobiles or laptops (though rental firms are required to inform customers and embrace this within the contract).
Safety towards stalkerware. Kaspersky Premium detects recognized stalkerware apps. Oh, and by the way in which — do you know that Kaspersky merchandise received a stalkerware detection take a look at? If such apps — and even their set up recordsdata, whether or not downloaded by you or another person — are discovered in your gadget, Kaspersky for Android will warn you instantly.
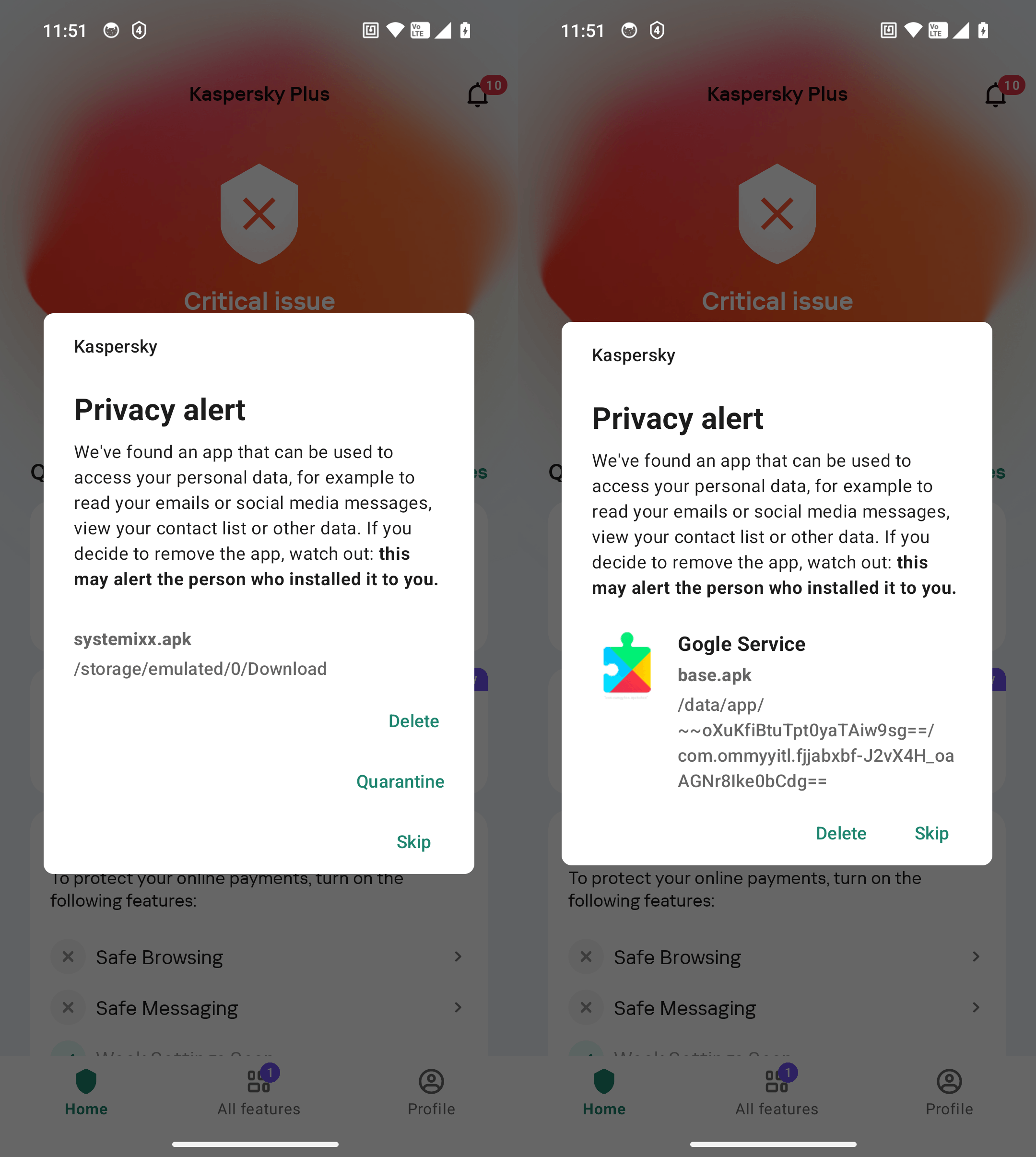
Kaspersky for Android detects each put in stalkerware apps (on the proper) and their set up recordsdata (on the left)
Even customers of the free model of Kaspersky for Android can scan for stalkerware. The one distinction on this case between Kaspersky Premium and the free model is that in Kaspersky Premium, scanning is completed routinely and repeatedly. Within the free model of Kaspersky for Android, customers must manually provoke every scan.
Suspicious beacons that seem continuously in your neighborhood shall be listed and labeled within the Machine Scanner part.
In the meantime, the permission-control characteristic frequently checks the entry of apps to your digital camera, microphone, location and Bluetooth, so you’ll be able to rapidly determine suspicious new apps.
Extra precautions A number of basic safety and cyber-hygiene measures could make it tougher for anybody to trace you, and are really helpful for all customers:
- By no means go away private objects unattended. This is applicable particularly to digital gadgets which can be powered on.
- Arrange biometric authentication in your smartphone.
- Set the auto-lock display screen time to 30 seconds or much less.
- Arrange biometrics or a robust password for logging into your laptop computer, and all the time lock the display screen if you happen to go away your desk.
- Make a password mandatory to put in apps from the app retailer (you are able to do this on each iOS and Android).
- Disable the set up of apps from unknown sources on Android.
- Replace all of your apps at the very least as soon as a month and delete any that you simply now not use.
- By no means share your passwords with anybody. When you’ve ever shared them with anybody, otherwise you suspect they might have been intercepted, seen or guessed — change them instantly.
- Keep away from logging into private accounts on shared gadgets at house or at work, and positively don’t do that in libraries, lodges or cafes. When you completely need to log in, make certain to log off afterwards.
- Use a password supervisor, create a singular password for every account, and allow two-factor authentication.
- Watch out with what you share on social media and in messengers — keep away from disclosing particulars that reveal your location, each day routine, or social circle.
For people at increased threat of stalking (say, from an undesirable admirer, disaffected partner or enterprise associate), here’s a extra complete listing of precautions, together with bodily security and authorized safety measures.
What to do if you happen to detect surveillance
When you’ve found a beacon or monitoring app and dominated out any harmless explanations, take into account the doable causes for why you is perhaps underneath surveillance.
For these concerned in home violence or severe conflicts, bodily security is the precedence. Subsequently, in such instances, it’s vital to not reveal that you simply’ve detected the surveillance, however as a substitute contact the police or devoted help organizations. Likewise, it’s important that the smartphone or beacon doesn’t find yourself in a location that may point out the invention (for instance, a police station). You possibly can both go away the smartphone at house when you go to the police, or prepare to satisfy a help group in a secure place. For extra detailed recommendation on such tough instances, seek the advice of our anti-stalking consciousness information.
If the danger of violence is low, you must nonetheless contact the police. Hand over the spy tracker, and let regulation enforcement create a digital copy of your smartphone to assemble proof of an infection (if current). After that, you’ll be able to take away the stalkerware out of your smartphone.