A distributed denial-of-service (DDoS) assault is sort of a digital site visitors jam aimed toward a web site. Attackers flood the location with junk web site visitors, overwhelming it and making it sluggish or inaccessible to actual customers.
In at the moment’s interconnected digital world, distributed denial-of-service (DDoS) assaults pose a critical menace to on-line companies and companies, disrupting operations and inflicting important monetary losses.
By understanding DDoS assaults and studying about efficient mitigation methods, you may higher defend your on-line belongings and make sure the uninterrupted availability of your companies.
On this put up, we’ll discover the insidious nature of DDoS assaults, how they work and study some prevention tricks to keep protected.
What Is a DDoS Assault?
A DDoS assault is a malicious try and shut down a web site or on-line service. The attacker does this by flooding the goal with an enormous quantity of web requests, like faux web site visits or knowledge downloads.
These requests come from a community of hacked units managed by the attacker, making them seem like official site visitors and tough to differentiate from actual customers. This overwhelming flood of requests jams the goal’s system, stopping actual customers from accessing the web site or service.
Consider it like a mall on a busy buying day. Usually, the mall can deal with the group of buyers coming out and in of the shops. But when a bunch of individuals determine to focus on one particular retailer on the similar time and overwhelm the doorway with buying carts, deliveries and faux buy orders, that retailer can be unable to perform correctly and serve its actual prospects.
How Does a DDoS Assault Work?
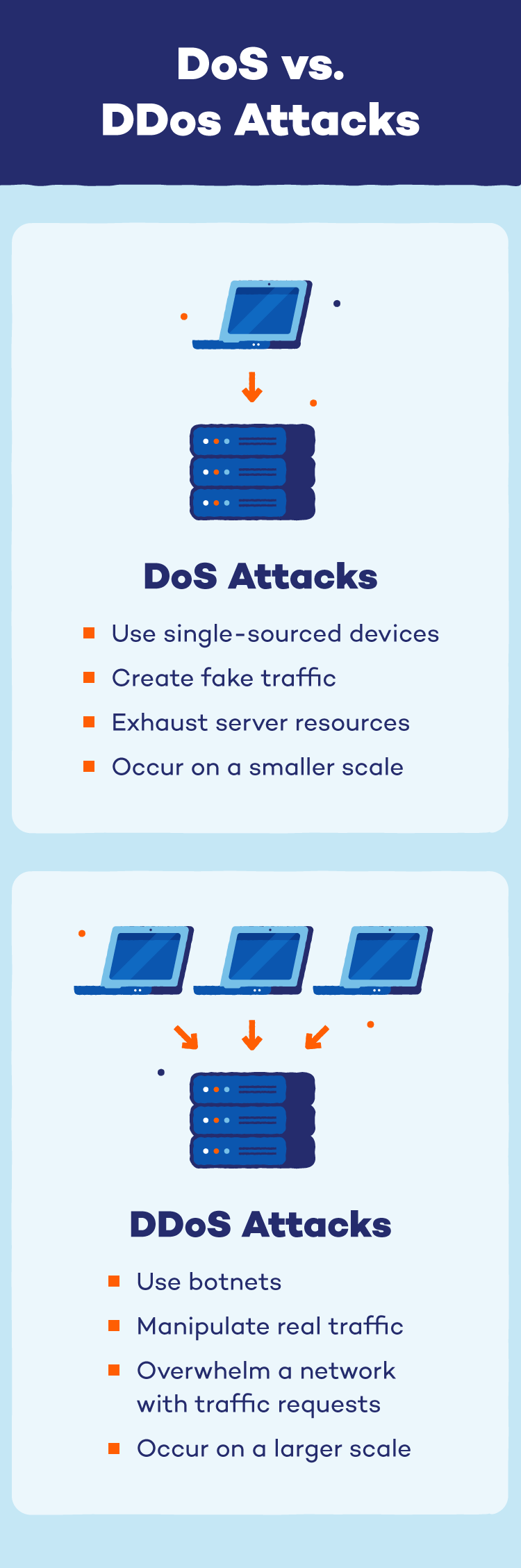
DDoS assaults cripple web sites and companies by leveraging an enormous military of compromised units. Not like a denial-of-service (DoS) assault that floods a goal with site visitors from a single supply, a DDoS assault makes use of a botnet — a community of hacked units secretly managed by the attacker.
These units, starting from computer systems to smartphones, grow to be the attacker’s “troopers” and bombard the goal with requests concurrently. This distributed assault overwhelms the goal system’s capability, stopping actual customers from accessing the web site or service.
The best way to Determine a DDoS Assault
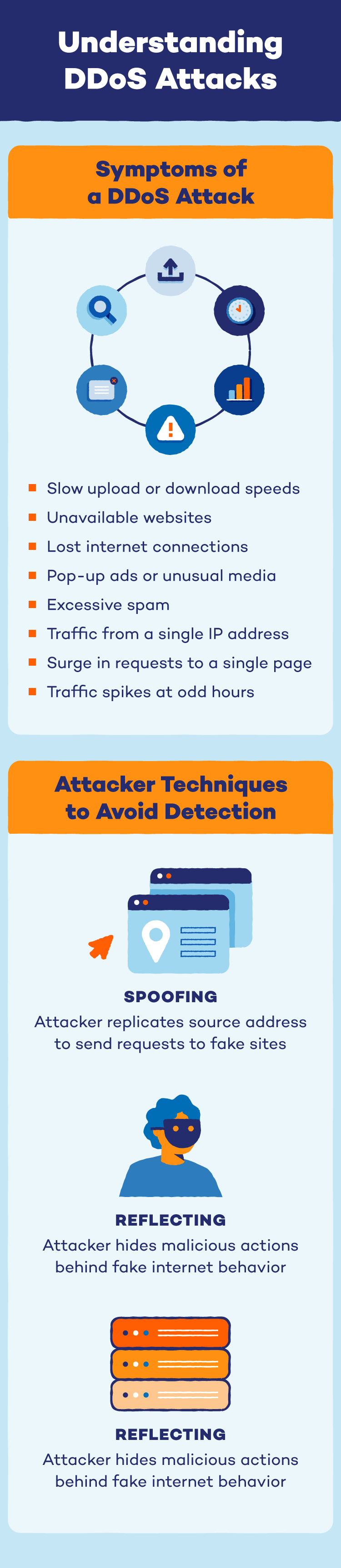
In case your web site is sluggish, unresponsive and even crashes solely, it may be underneath a DDoS assault! Listed here are some crimson flags to be careful for:
- Sluggish add or obtain speeds
- Unavailable web sites
- Misplaced web connections
- Pop-up adverts or uncommon media
- Extreme spam
- Visitors originating from a single IP tackle
- A surge in requests to a single web page
- Spikes of site visitors at odd hours of the day
Every sort of assault has extra particular indicators, however these frequent DDoS assault signs may warn you to an assault earlier than it’s in full drive.
Many of those distributed denial-of-service assaults are additionally tough to forestall, establish and mitigate. DDoS attackers keep away from detection in a lot of methods, notably by:
- Spoofing: Spoofing — together with DNS spoofing — is when an attacker replicates supply addresses and sends official site visitors to illegitimate websites or locations.
- Reflecting: Reflecting refers to when an attacker adjustments the traditional conduct of web companies to cover their malicious actions.
- Amplifying: Amplifying is when an attacker makes use of a supply modifier to create massive quantities of site visitors that may then overwhelm a community or server.
Kinds of DDoS Assaults
Based on the open methods interconnection (OSI) mannequin, a community has seven completely different connection layers that assist networks talk with one another. As a result of these layers individually decide the behaviors, instruments and methods wanted to invade it, every sort of DDoS assault is classed primarily based on the layers it targets and the behaviors it wants to duplicate.
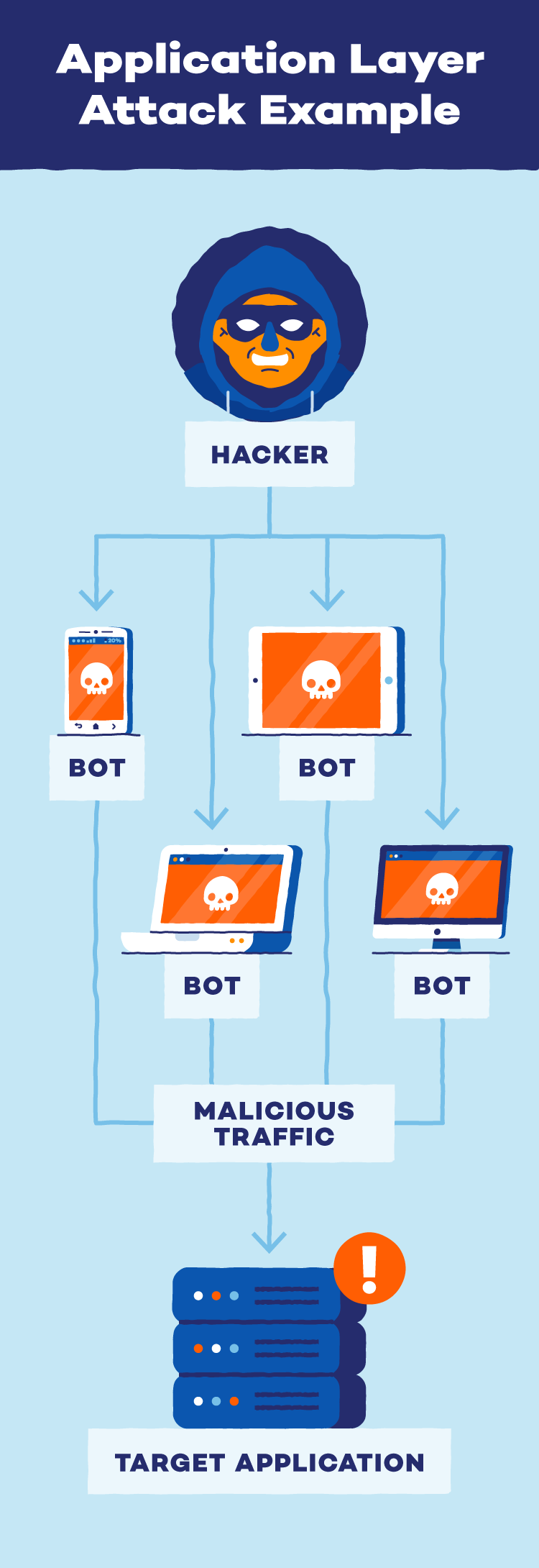
Software Layer Assaults
Software layer assaults goal vulnerabilities throughout the software program purposes operating on a system, bypassing community safety measures. Not like community assaults that disrupt general site visitors move, these assaults exploit weaknesses within the code itself. This will contain manipulating databases (SQL injection) or injecting malicious scripts (XSS) to steal knowledge, disrupt performance or compromise consumer units.
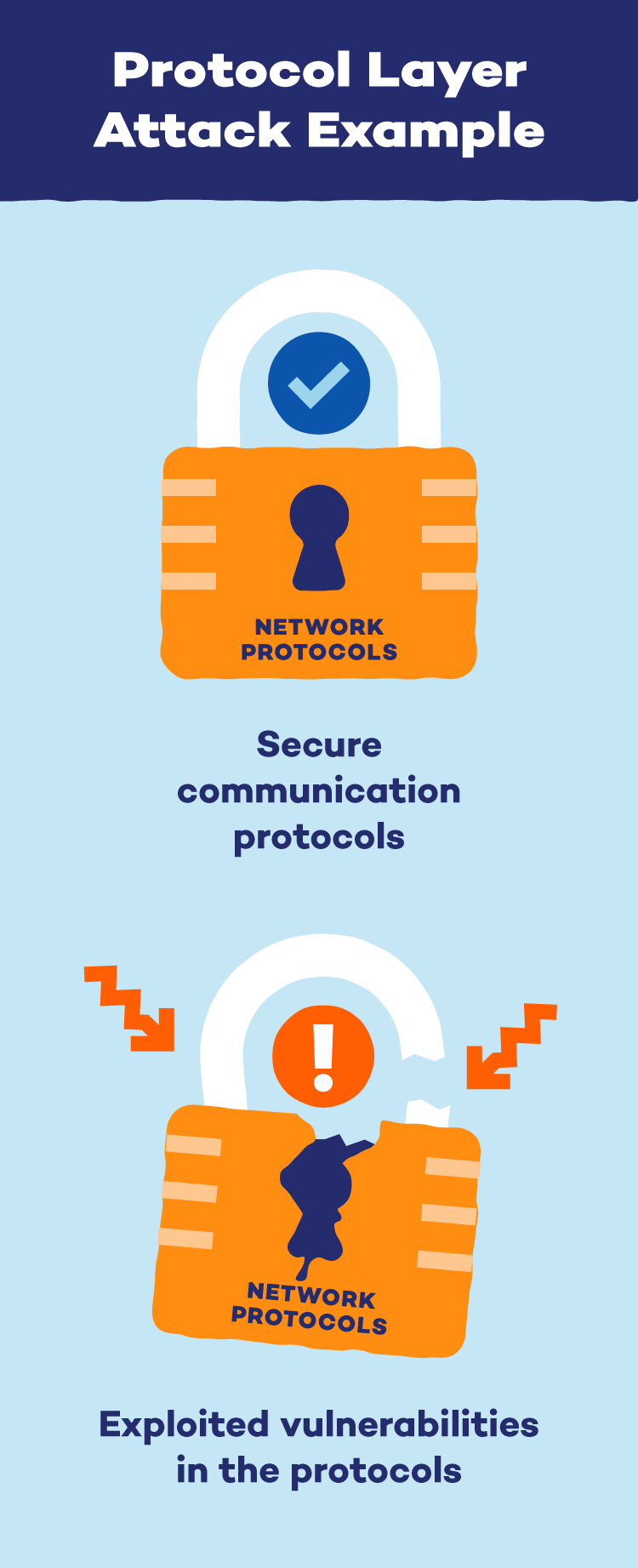
Protocol or Community Layer Assaults
Protocol assaults, additionally known as community layer assaults, often goal ranges three and 4 of a community’s communication system. Networks have communication protocols, like a freeway with lanes and site visitors lights. Hackers exploit weaknesses in these protocols to disrupt communication.
These assaults overwhelm the capability of the assets in these layers, like firewalls, which causes a state of exhaustion to overhaul the system. SYN floods and smurf assaults are examples of protocol assaults that focus on the third or fourth OSI layers.
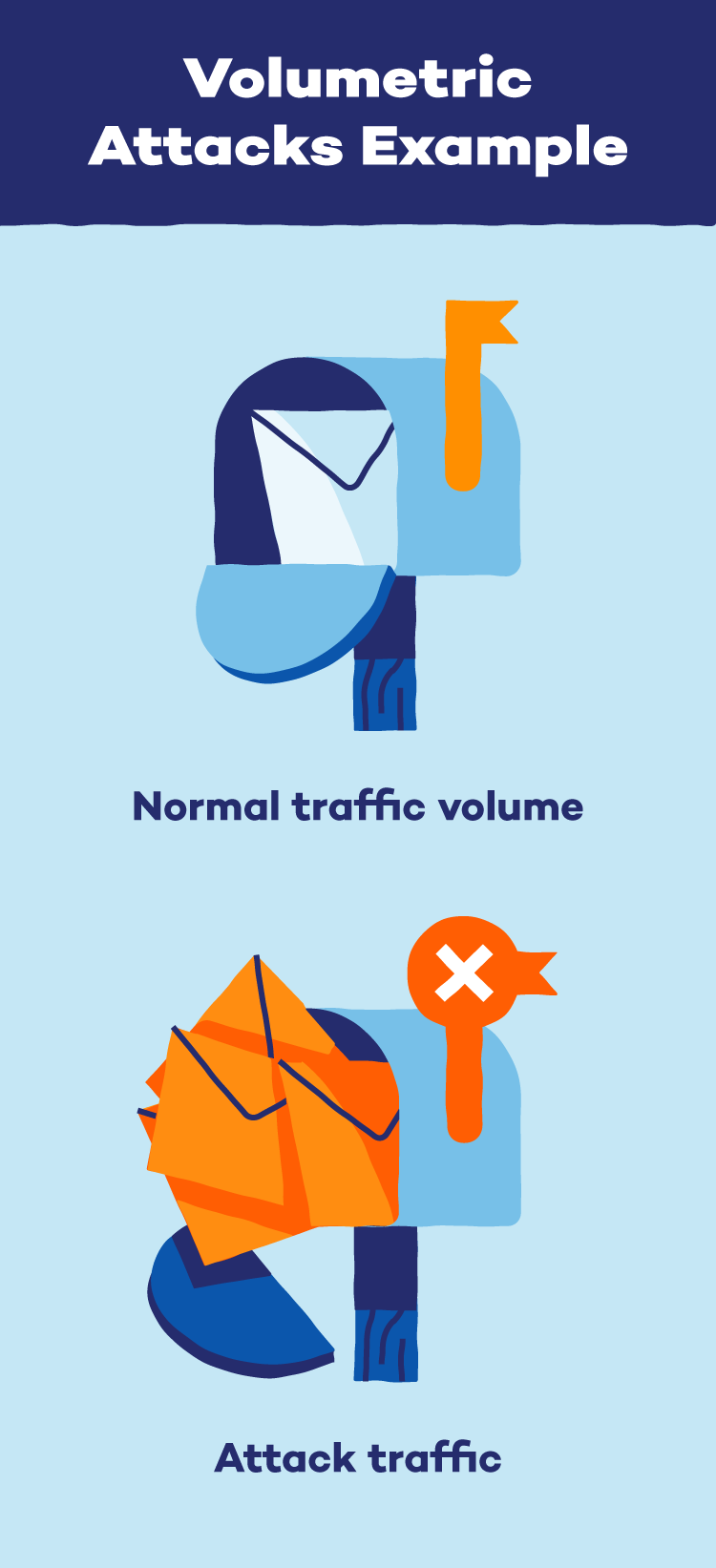
Volumetric Assaults
Volumetric assaults try and overwhelm a community and its connection to the web. Attackers will amplify knowledge and different communication requests to the extent {that a} system is unable to function efficiently. DNS assaults, together with DNS amplification assaults, are generally used to extend the amount of site visitors for volumetric assaults.
Every of a lot of these DDoS assaults will be damaged down additional primarily based on the period of the assault:
- Lengthy-term assaults: An extended-term DDoS assault is any assault that lasts hours, days, weeks, months or longer.
- Burst assaults: A burst DDoS assault will often solely final a couple of seconds to a couple minutes.
Irrespective of how lengthy an assault lasts, the harm will be crippling to every focused connection layer.
Stopping a DDoS Assault
Whereas there isn’t a one-stop store for DDoS safety, there are a couple of methods you may put together your methods for a possible assault. Being conscious of the potential for a DDoS assault is step one, and these 5 suggestions are the following finest methods to forestall a attainable system assault.
1. Vulnerability Assessments
Should you run a corporation with an info and safety infrastructure system, it’s essential to carry out common vulnerability assessments. Along with merely discovering system vulnerabilities, a vulnerability evaluation may also doc these findings and supply steerage for menace options. Penetration checks are additionally advisable, and white hat hackers will be employed to assist run these checks and discover and warn you to attainable weaknesses or entry factors.
2. Black Gap Routing
Black gap routing is a extra excessive prevention and safety tactic. When you have purpose to imagine that you could be fall sufferer to a DDoS assault, a black gap route can ship your whole site visitors on a impartial route away out of your methods. This may take away all official site visitors — each good and dangerous — which may result in enterprise loss.
3. Fee Limiting
Fee limiting is one approach to stop or mitigate a DDoS assault. This lowers the variety of requests a server can settle for primarily based on a selected timeframe, which may cease a DDoS assault from damaging or overtaking your methods. Whereas this prevention tactic might not work for all assaults, it could scale back the harm one might trigger.
4. Community Diffusion
As a substitute of permitting a DDoS assault to overwhelm and take over a community, community diffusion disperses site visitors between a wide range of distributed servers so it’s absorbed by the community itself. This spreads the distributed denial-of-service assault’s influence so it turns into manageable as an alternative of harmful.
5. Firewalls
Within the occasion of a seven-layer DDoS assault, it’s essential to have an internet utility firewall in impact. This can be a software that separates the server from the web and provides a further layer of safety safety from harmful and overwhelming site visitors. Moreover, firewalls can implement customized guidelines throughout an assault to higher disperse or settle for site visitors.
Whereas these finishing up a DDoS assault will be sneaky, there are methods to guard your enterprise, your house and your self. By investing in safety protocols, together with VPNs and safety plans, you will be ready for a DDoS assault at any time.
Motives for DDoSing
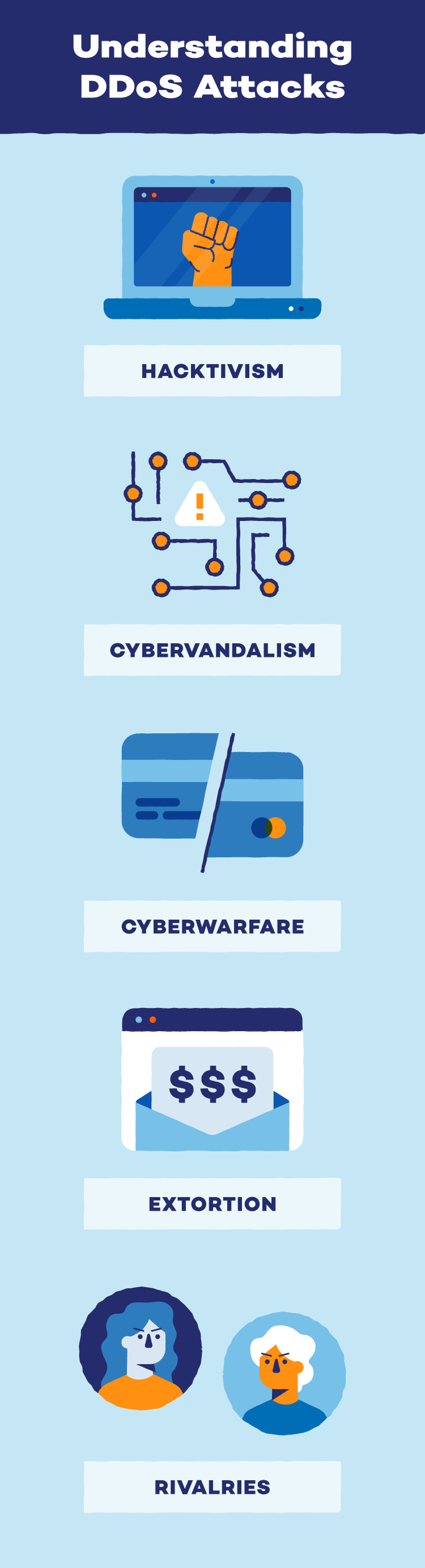
DDoSing — the time period used when somebody executes a DDoS assault — may result from a wide range of motives. Whereas these motives are completely different for each hacker, they will vary wherever from political acquire to social justice.
- Hacktivism: Hacktivism is a type of digital activism. Hacktivists often interact in hacktivism to achieve social, political or non secular justice, and so they typically battle for the larger good. Some hackers will use DDoS assaults throughout a hacktivism marketing campaign.
- Cybervandalism: Cybervandalism is a cyberattack that always has no social, political, non secular or prison intentions. Most on-line vandalism acts are meant to indicate a hacker’s experience, and vandals typically pay a DDoS-for-hire payment to provoke DDoS booters and IP stressors.
- Cyberwarfare: Not like cybervandalism, cyberwarfare has political or navy intent and is commonly used to overhaul or dismember organizational infrastructures. A lot of a lot of these DDoS assaults are state-sanctioned and might disrupt funds, well being care and authorities safety.
- Extortion: A cybercriminal might demand cash or different assets whereas threatening a DDoS assault. If the sufferer complies, the attacker might not problem the assault. However, if the sufferer doesn’t comply, organizations could also be compelled to go offline till the menace has handed or been mitigated.
- Rivalries: DDoS assaults are typically used as competitors instruments for each private {and professional} rivalries. These assaults can dissuade folks from going to occasions, shut down on-line storefronts, trigger reputational harm and extra.
DDoS and utility layer assaults can pose important threats to web sites and on-line companies. By understanding these completely different assault strategies and implementing the advisable safety measures, organizations can considerably bolster their defenses. Nevertheless, cyberthreats are consistently evolving.
Panda Free Antivirus provides complete real-time safety in opposition to numerous on-line threats, together with malware, phishing makes an attempt and even botnet infections. And for an additional layer of safety when utilizing public Wi-Fi, think about using Panda Safety VPN. It encrypts your web site visitors, making it unreadable to hackers and eavesdroppers, so you may browse safely on any community.
DDoS Assault FAQ
Let’s focus on some frequent queries associated to DDoS assaults.
What Does DDoS Assault Stand For?
DDoS stands for distributed denial-of-service assault. It’s a malicious try and overwhelm a web site or on-line service with a flood of web site visitors, making it unavailable to official customers.
What Does a DDoS Assault Look Like?
You would possibly expertise a DDoS assault as:
- Sluggish or unresponsive web sites: The web site would possibly take a really very long time to load or not load in any respect.
- Error messages: You would possibly see error messages concerning the server being overloaded.
- Bother utilizing on-line companies: On-line video games, streaming platforms, and many others. may be tough to connect with or use.