Cerber is a pressure of ransomware that was first recognized in early 2016. It’s a sort of malware that encrypts a sufferer’s information and calls for a ransom for the decryption key wanted to unlock the information. Cerber, like many different ransomware variants, usually targets people and organizations by encrypting their information and demanding a ransom cost, (normally in cryptocurrencies like Bitcoin), for the decryption key.
Technical Evaluation:
The Cerber ransomware’s primary payload is a custom-packed pattern, so the code is initially unreadable at first. After unpacking the pattern, we are able to discover the precise payload 376165CCD556CD74658AFEA9F6F428F9. As proven in Fig 1.
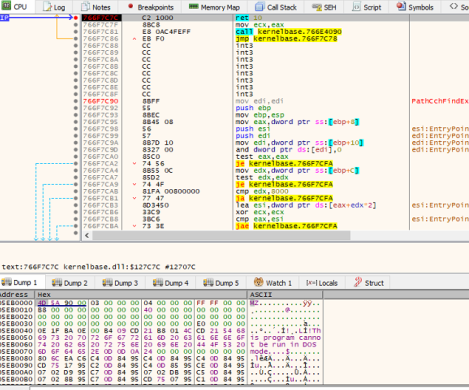
Fig.1: Unpacking of Cerber
When the payload is executed, it checks for a particular mutex. If any of these mutexes are discovered to be current, the malware will cease its execution. This validation mechanism, involving mutex strings, is constructed into the ransomware code to forestall it from re-infecting the identical machine.
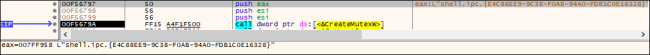
Fig.2: Creating Mutex
Additional, it decrypts the info utilizing CryptoAPI, which comprises the following info:,
- Blocklisted files, extensions and folders
- Excluded nation primarily based on Language ID
- Focused Extensions
- Base64 encrypted Public RSA key and Ransom Observe in HTML format
- Ransom Observe in TXT format
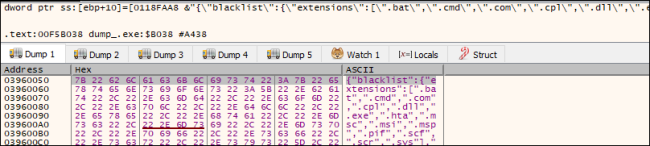
Fig.3: Decrypted Information
The Ransomware has determined to exclude a number of international locations from the assault (specifically, Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, and Uzbekistan).
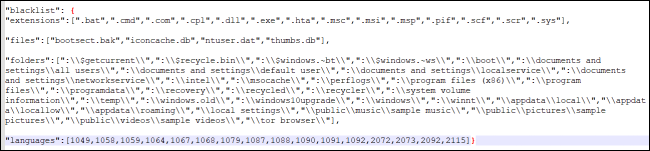
Fig.4: Excluded Extensions, folders and nation codes
Then it traverses the decrypted information and makes use of its worth for additional encryption course ofes.
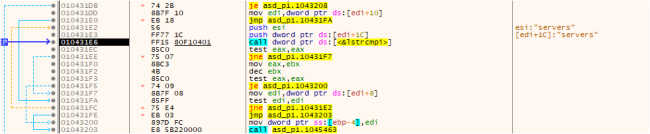
Fig.5: Traversing the Information
Evasion Method:
Cerber displays superior capabilities by figuring out and configuring Home windows firewall guidelines to hinder outbound site visitors from the executable binaries of put in firewalls, antivirus, and anti–spyware and adware merchandise. This tactic goals to impede the communication and performance of those safety instruments, probably enhancing the ransomware’s means to persist on the compromised system and evade detection. This subtle maneuver underscores the evolving nature of Cerber, posing a major problem for cybersecurity measures in search of to counteract its affect.
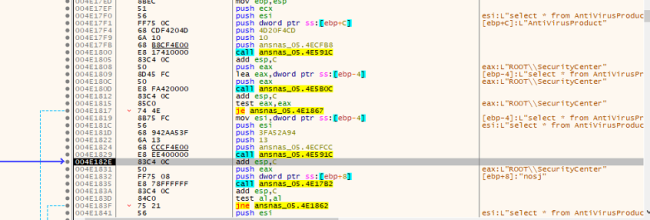
Fig.6: Disabling AV Companies
C2 connection:
Cerber ransomware establishes connections to port 6893 on IPs specified by CIDR within the configuration. The communication packet initiation entails a hash prefixed with the Machine GUID (MD5_KEY). The packet concludes with parameters similar to PARTNER_ID, OS particulars, IS_X64 (indicating whether or not the system is 64-bit), IS_ADMIN (reflecting administrative privileges), COUNT_FILES (the rely of information on the system), STOP_REASON (cause for stopping), and STATUS (standing info). This communication protocol serves as a technique for exchanging information with the required IPs, illustrating the ransomware’s subtle strategy to interplay and management inside the compromised system.
The communication packet begins with a hash consisting of the Machine GUID: {MD5_KEY} and ending with {PARTNER_ID}{OS}{IS_X64}{IS_ADMIN}{COUNT_FILES}{STOP_REASON}{STATUS}.
With Ip various type ip”:[“93.107.12.0/27″,”95.1.200.0/27″,”87.98.176.0/22”]
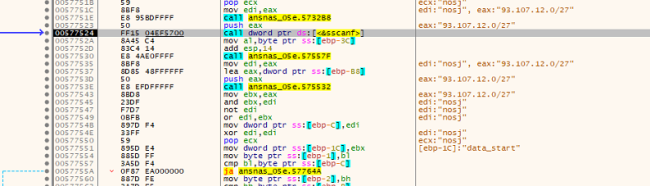
Fig.7: C2 Connection
Encryption:
It drops two information containing the RSA key, which is additional used for the Encryption course of.
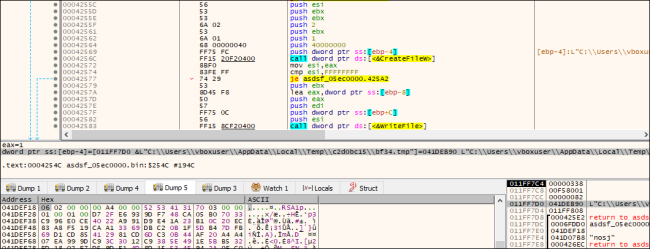
Fig.8: Including a part of the Key within the Temp File
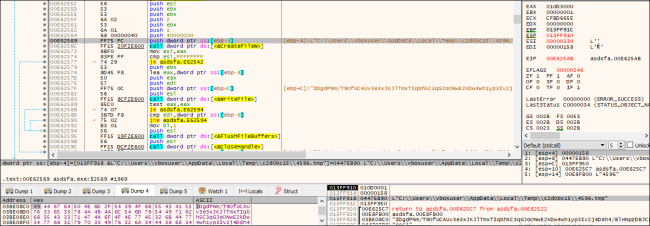
Fig.9: Including a part of the Key in Temp File
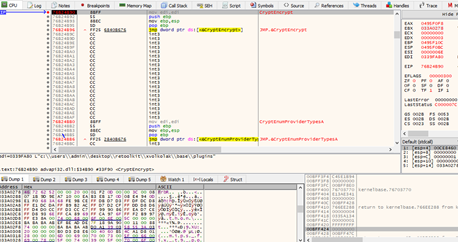
Fig.10: Use of Crypto API
It implements RSA and RC4 algorithms in its encryption routine and using CryptoAPI – a separate perform that reads and skips the primary 1800 bytes, encrypts the remainder of the content material, and writes again to the file, as mentioned in Fig. 12.
Following the encryption course of, the ransomware appends a “.a769” extension and renames the file with a randomly generated string with sample [0-9a-zA-Z_-]{10}. The determine beneath illustrates the information which have undergone this encryption and adjustments in file names and extensions.
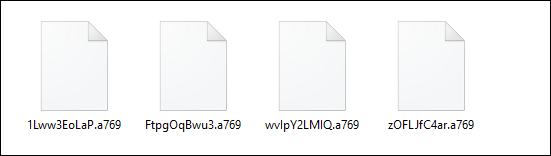
Fig.11: Encrypted Recordsdata
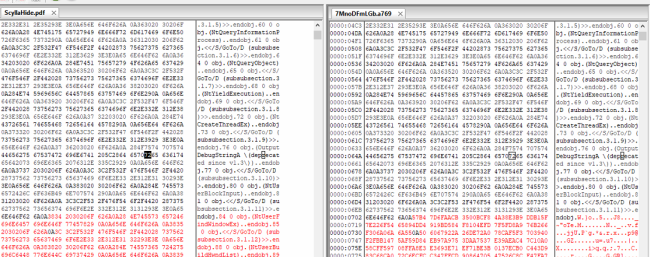
Fig.12: Skipping 1800 bytes from the Header
Ransom notes:
It drops the ransom notes within the folders with the encrypted information, with the identify “__R_E_A_D__T_H_I_S__.html” and TXT type. On this ransom be aware, the menace actors (TAs) instructs the victims to contact them through their TOR web site. Moreover, the TAs subject a warning that if the victims fail to contact inside 30 days following the ransomware assault, they will disclose the sufferer‘s confidential information on public information retailers and web sites.
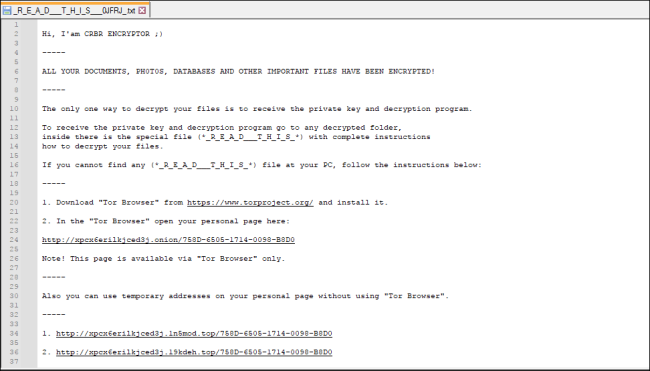
Fig.13: Dropped Ransom Observe in TXT Format
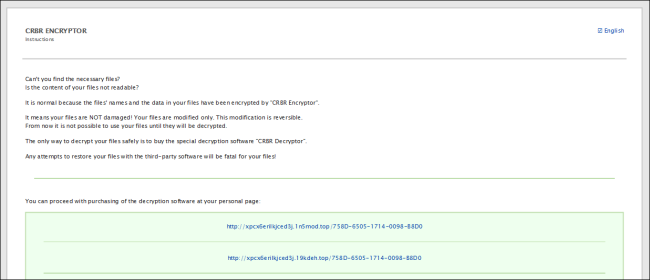
Fig.14_Dropped Ransom Observe in HTML File
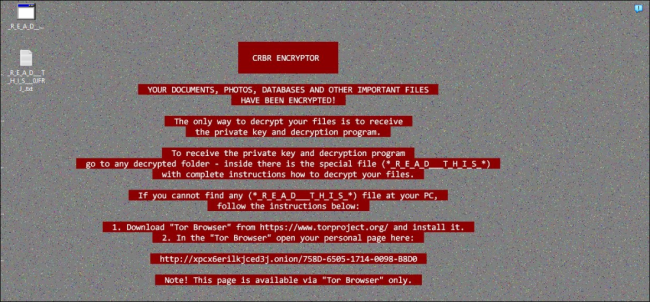
Fig.15: Modified Desktop Wallpaper
Submit Encryption:
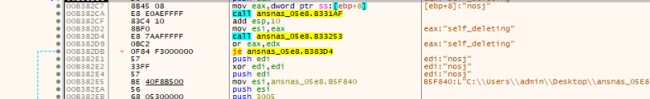
Following an infection, the ransomware employs the ShellExecuteA() API perform with particular arguments to eradicate its personal file from the compromised system. By this motion, the malware orchestrates the removing of its executable, abandoning solely the encrypted information and the accompanying ransom be aware. This deliberate self-deletion mechanism signifies an try by the ransomware to hide its presence, complicating post-infection evaluation and removing efforts whereas making certain the persistence of the encrypted information and the related ransom demand.
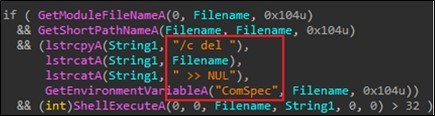
Fig.16: Self-delete utilizing Shell ExecuteA perform
Precaution of Cerber Ransomware
Cerber Ransomware is a kind of malware that encrypts a sufferer’s information and calls for a ransom for the decryption key. To guard your self and your pc methods from Cerber Ransomware, or ransomware typically, it’s vital to take numerous precautions. Listed here are just a few some steps measures you’ll be able to take to attenuate your threat:
Often Backup Your Information:
Again up your vital information commonly to an exterior system or a cloud service. This manner, in case your information are encrypted, you received’t need to pay a ransom to get better them.
Maintain Your Software program Up to date:
Make sure that your working system and all software program, together with your antivirus program, are updated. Ransomware usually takes benefit of identified vulnerabilities in outdated software program.
Use Sturdy, Distinctive Passwords:
Use sturdy and sophisticated passwords for all of your accounts and gadgets. Think about using a good password supervisor to generate and retailer sturdy passwords.
Allow Two-Issue Authentication (2FA):
Allow 2FA each time attainable in your on-line accounts. This supplies an additional layer of safety, making it tougher for attackers to entry your accounts.
Train Warning with E-mail:
Be cautious of e-mail attachments and hyperlinks, particularly if they arrive from unknown or sudden sources. Ransomware might be delivered by means of phishing emails.
Set up a Dependable Antivirus Program:
Set up and commonly replace a good antivirus or anti-malware software program. Be sure it consists of real-time scanning and ransomware safety options.
Use a Firewall:
An excellent firewall may help block incoming threats and scale back the probability of a malware an infection.
Often Replace and Patch:
Maintain your system and software program up to date. Many ransomware assaults exploit vulnerabilities in outdated software program, so patching these vulnerabilities is important.
Community Safety:
Implement community safety measures, similar to intrusion detection methods, and commonly audit community site visitors for uncommon exercise.
Monitor for Suspicious Exercise:
Maintain an eye fixed out for any uncommon or suspicious exercise in your pc or community, as early detection may help cease an an infection from spreading.
Often Check Backups:
Periodically take a look at your backups to make sure that they are often efficiently restored.
Fast Heal Safety:
Ransom.Cerber.S443347
Ransom.Cerber.S126609
Ransom.Cerber.S22591
Ransom.Cerber.S1538045
Conclusion:
Cerber ransomware, first recognized in 2016, represents a extremely subtle menace with superior evasion strategies. It can configure Home windows firewall guidelines, exclude particular international locations from assaults, and make use of persistence on compromised methods. It combines RSA, and RC4 algorithms within the encryption course of, and makes use of the self-deletion mechanism post-infection.
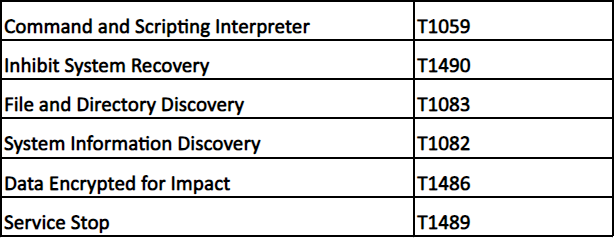
MITRE ATTACK TTPs:
IOCs:
FE1BC60A95B2C2D77CD5D232296A7FA4
376165CCD556CD74658AFEA9F6F428F9
Authors:
Soumen Burma
Vaibhav Krushna Billade



