Android always tightens app restrictions to forestall scammers from utilizing malicious software program to steal cash, passwords, and customers’ personal secrets and techniques. Nevertheless, a brand new vulnerability dubbed Pixnapping bypasses each protecting layer and permits an attacker to imperceptibly learn picture pixels from the display — basically taking a screenshot. A malicious app with zero permissions can see passwords, checking account balances, one-time codes, and anything the proprietor views on the display. Fortuitously, Pixnapping is at present a purely research-based mission and isn’t but being actively exploited by menace actors. The hope is that Google will totally patch the vulnerability earlier than the assault code is built-in into real-world malware. As of now, the Pixnapping vulnerability (CVE-2025-48561) probably impacts all trendy Android smartphones, together with these operating the newest Android variations.
Why screenshots, media projection and display studying are harmful
As demonstrated by the SparkCat OCR stealer we found, menace actors have already mastered picture processing. If a picture on a smartphone comprises a precious piece of data, the malware can detect it, carry out optical character recognition instantly on the telephone, after which exfiltrate the extracted information to the attacker’s server. SparkCat is especially noteworthy as a result of it managed to infiltrate official app marketplaces together with the App Retailer. It could not be troublesome for a malicious Pixnapping-enabled app to duplicate this trick, particularly provided that the assault requires zero particular permissions. An app that seems to supply a reputable, helpful function may concurrently and silently ship one-time multi-factor authentication codes, cryptowallet passwords, and another info to scammers.
One other common tactic utilized by malicious actors is to view the required information because it’s proven, in real-time. For this social engineering method, the sufferer is contacted by way of a messaging app and, underneath numerous pretexts, satisfied to allow display sharing.
Anatomy of the Pixnapping assault
The researchers have been capable of screenshot content material from different apps by combining beforehand recognized strategies of stealing pixels from browsers and from ARM telephone graphics processing items (GPUs). The attacking app silently overlays translucent home windows atop the goal info after which measures how the video system combines the pixels of those layered home windows right into a remaining picture.
Way back to 2013, researchers described an assault that allowed one web site to load one other inside a part of its personal window (by way of an iframe) and, by performing reputable operations of picture layering and transformation, infer precisely what was drawn or written on the opposite web site. Whereas trendy browsers have mitigated that particular assault, a bunch of U.S. researchers have now found out find out how to apply the identical core precept to Android.
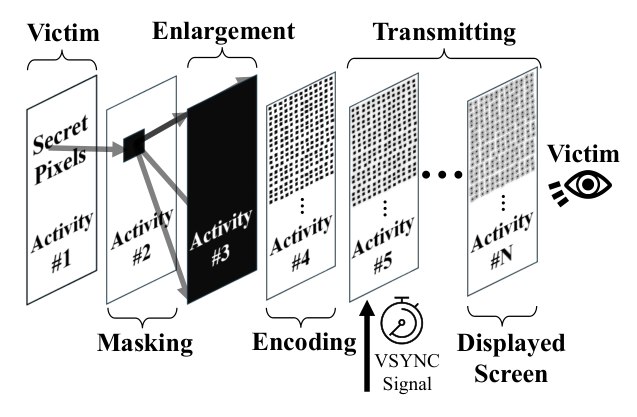
The malicious app first sends a system name to the goal app. In Android, this is called an intent. Intents sometimes allow not solely easy app launching but additionally issues like instantly opening a browser to a particular URL or a messaging app to a particular contact’s chat. The attacking app sends an intent designed to pressure the goal app to attract the delicate info onto the display. Particular hidden launch flags are used. The attacking app then sends a launch intent to itself. This particular mixture of actions permits the sufferer app to not seem on the display in any respect, but it nonetheless renders the data sought by the attacker in its window, within the background.
Within the second stage of the assault, the malicious app overlays the hidden window of the sufferer app with a collection of translucent home windows, every of which covers and blurs the content material beneath it. This advanced association stays invisible to the consumer, however Android dutifully calculates how this mix of home windows ought to look if the consumer have been to carry it to the foreground.
The attacking app can solely instantly learn the pixels from its personal translucent home windows; the ultimate mixed picture, which includes the sufferer app’s display content material, shouldn’t be instantly accessible to the attacker. To bypass this restriction, the researchers make use of two ingenious tips. The precise pixel to be stolen is remoted from its environment by overlaying the sufferer app with a principally opaque window that has a single clear level exactly over the goal pixel. A magnifying layer is then positioned on high of this mix, consisting of a window with heavy blurring enabled.
To decipher the ensuing mush and decide the worth of the pixel on the very backside, the researchers leveraged one other recognized vulnerability, GPU.zip (this may increasingly seem like a file hyperlink, nevertheless it truly results in a analysis paper web site). This vulnerability is predicated on the truth that all trendy smartphones compress the info of any photos being despatched from the CPU to the GPU. This compression is lossless (like a ZIP file), however the velocity of packing and unpacking modifications relying on the data being transmitted. GPU.zip permits an attacker to measure the time it takes to compress the data. By timing these operations, the attacker can infer what information is being transferred. With the assistance of GPU.zip, the remoted, blurred, and magnified single pixel from the sufferer app’s window will be efficiently learn by the attacking app.
Stealing one thing significant requires repeating your complete pixel-stealing course of a whole lot of instances, because it must be utilized to every level individually. Nevertheless, that is solely possible inside a short while body. In a video demonstration of the assault, a six-digit code from Google Authenticator was efficiently extracted in simply 22 seconds, whereas it was nonetheless legitimate.
How Android protects display confidentiality
Google engineers have practically twenty years of expertise combating numerous privateness assaults, which has resulted in a layered protection constructed towards unlawful seize of screenshots and movies. An entire listing of those measures would span a number of pages, so we solely listing some key protections:
- The FLAG_SECURE window flag prevents the working system from taking screenshots of content material.
- Entry to media projection instruments (capturing display content material as a media stream) requires express consumer affirmation and may solely be carried out by an app that’s seen and lively.
- Tight restrictions are positioned on entry to administrative providers like AccessibilityService and the flexibility to attract app parts over different apps.
- One-time passwords and different secret information are hidden routinely if media projection is detected.
- Android restricts apps from accessing different apps’ information. Moreover, apps can not request a full listing of all put in apps on the smartphone.
Sadly, Pixnapping bypasses all these present restrictions and requires completely no particular permissions. The attacking app solely wants two elementary capabilities: to attract inside its personal home windows and to ship system calls (intents) to different apps. These are fundamental constructing blocks of Android performance, so they’re very troublesome to limit.
Which units are affected by Pixnapping, and find out how to defend oneself
The assault’s viability was confirmed on Android variations 13–16 throughout Google Pixel units from generations 6–9, in addition to Samsung Galaxy S25. The researchers consider the assault can be useful on different Android units as nicely, as all of the mechanisms used are commonplace. Nevertheless, there could also be nuances associated to the implementation of the second section of the assault (the pixel magnification method).
Google launched a patch in September after being notified of the assault in February. Sadly, the chosen methodology for fixing the vulnerability proved to be insufficiently dependable, and the researchers shortly devised a strategy to bypass the patch. A brand new try and remove the vulnerability is deliberate for Google’s December replace launch. As for GPU.zip, there are not any plans to challenge a patch for this particular information leakage channel. No less than, no smartphone GPU producer has introduced plans to that impact for the reason that flaw turned public data in 2024.
Person capabilities to defend towards Pixnapping are restricted. We advocate the next measures:
- Promptly replace to the newest model of Android with all present safety patches.
- Keep away from putting in apps from unofficial sources, and train warning with apps from official shops if they’re too new, have low obtain counts, or are poorly rated.
- Guarantee a full-fledged safety system is used in your telephone, corresponding to Kaspersky for Android.
What different non-standard Android assault strategies exist: