A current publication by researchers on the College of California, Irvine, demonstrates an interesting truth: optical sensors in pc mice have change into so delicate that, along with monitoring floor actions, they’ll decide up even minute vibrations — for example, these generated by a close-by dialog. The theoretical assault, dubbed “Mic-E-Mouse”, might probably permit adversaries to pay attention to discussions in “safe” rooms, supplied the attacker can one way or the other intercept the information transmitted by the mouse. As is commonly the case with tutorial papers of this sort, the proposed methodology comes with fairly a number of limitations.
Specifics of the Mic-E-Mouse assault
Let’s be clear from the beginning — not simply any previous mouse will work for this assault. It particularly requires fashions with probably the most delicate optical sensors. Such a sensor is actually an especially simplified video digital camera that movies the floor of the desk at a decision of 16×16 or 32×32 pixels. The mouse’s inside circuitry compares consecutive frames to find out how far and through which path the mouse has moved. How typically these snapshots are taken determines the mouse’s ultimate decision, expressed in dots per inch (DPI). The upper the DPI, the much less the consumer has to maneuver the mouse to place the cursor on the display screen. There’s additionally a second metric: the polling fee — the frequency at which the mouse information is transmitted to the pc. A delicate sensor in a mouse that transmits information sometimes is of no use. For the Mic-E-Mouse assault to even be possible, the mouse wants each a excessive decision (10 000DPI or extra) and a excessive polling fee (4000Hz or extra).
Why do these specific specs matter? Human speech, which the researchers meant to snoop on, is audible in a frequency vary of roughly 100 to 6000Hz. Speech causes sound waves, which create vibrations on the surfaces of close by objects. Capturing these vibrations requires an especially exact sensor, and the information coming from it have to be transmitted to the PC in probably the most full kind doable — with the information replace frequency being most important. In keeping with the Nyquist–Shannon sampling theorem, an analog sign inside a selected frequency vary might be digitized if the sampling fee is not less than twice the very best frequency of the sign. Consequently, a mouse transmitting information at 4000Hz can theoretically seize an audio frequency vary as much as a most of 2000Hz. However what sort of recording can a mouse seize anyway? Let’s have a look.
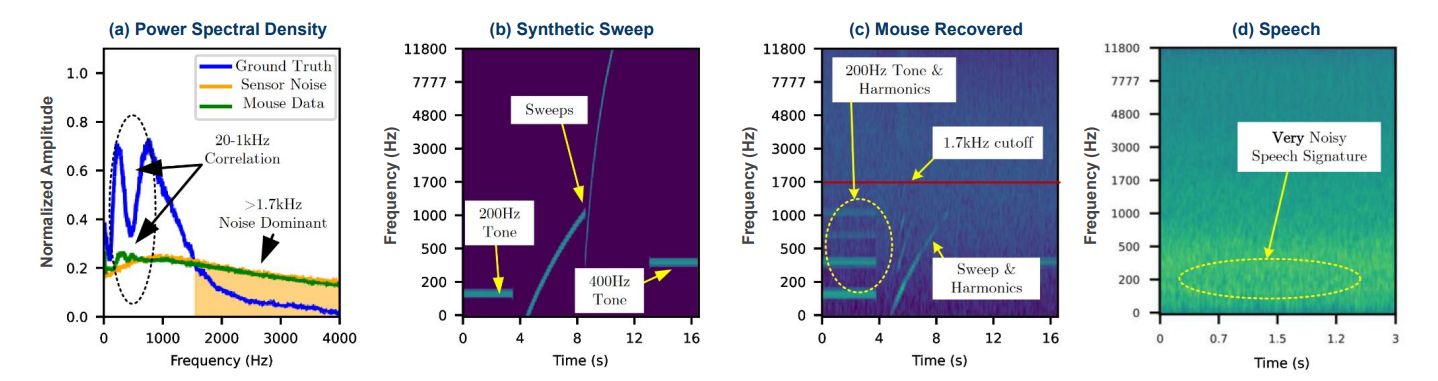
Outcomes of the examine on the sensitivity of a pc mouse’s optical sensor for capturing audio info. Supply
In graph (a), the blue coloration reveals the frequency response typical of human speech — that is the supply information. Inexperienced represents what was captured utilizing the pc mouse. The yellow represents the noise degree. The inexperienced corresponds very poorly to the unique audio info and is sort of fully drowned in noise. The identical is proven in a spectral view in graph (d). It seems to be as if it’s not possible to get well something in any respect from this info. Nevertheless, let’s take a look at graphs (b) and (c). The previous reveals the unique check alerts: tones at 200 and 400Hz, in addition to a variable frequency sign from 20 to 16 000Hz. The latter reveals the identical alerts, however captured by the pc mouse’s sensor. It’s clear that some info is preserved, though frequencies above 1700Hz can’t be intercepted.
Two totally different filtering strategies have been utilized to this extraordinarily noisy information. First, the well-known Wiener filtering methodology, and second, filtering utilizing a machine-learning system educated on clear voice information. Right here’s the consequence.
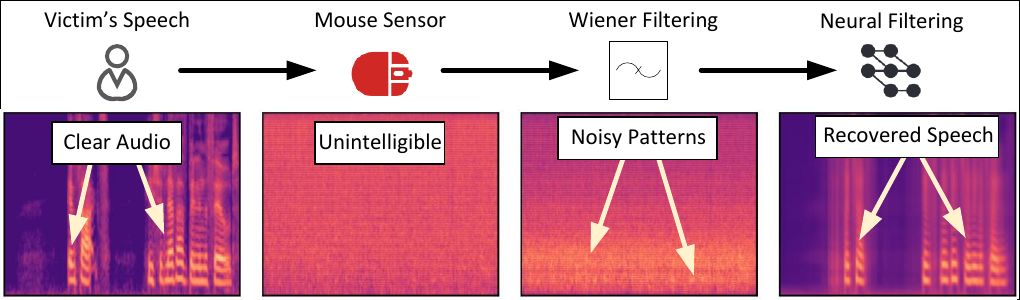
Spectral evaluation of the audio sign at totally different phases of filtering. Supply
Proven right here from left to proper are: the supply sign, the uncooked information from the mouse sensor (with most noise), and the 2 filtering phases. The result’s one thing very carefully resembling the supply materials.
So what sort of assault may very well be constructed based mostly on such a recording? The researchers suggest the next state of affairs: two persons are holding a dialog in a safe room with a PC in it. The sound of their speech causes air vibrations, that are transmitted to the tabletop, and from the tabletop to the mouse related to the PC. Malware put in on the PC intercepts the information from the mouse, and sends it to the attackers’ server. There, the sign is processed and filtered to totally reconstruct the speech. Sounds fairly horrifying, doesn’t it? Luckily, this state of affairs has many points.
Extreme limitations
The important thing benefit of this methodology is the bizarre assault vector. Acquiring information from the mouse requires no particular privileges, which means safety options might not even detect the eavesdropping. Nevertheless, not many functions entry detailed information from a mouse, which suggests the assault would require both writing customized software program, or hacking/modifying specialised software program that’s able to utilizing such information.
Moreover, there are at the moment not many mice fashions with the required specs (decision of 10 000DPI or greater, and polling fee of 4000Hz or extra). The researchers discovered a couple of dozen potential candidates and examined the assault on two fashions. These weren’t the costliest units — for example, the Razer Viper 8KHz prices round $50 — however they’re gaming mice, that are unlikely to be discovered related to a typical workstation. Thus, the Mic-E-Mouse assault is future-proof fairly than present-proof: the researchers assume that, over time, high-resolution sensors will change into commonplace even in the most typical workplace fashions.
The accuracy of the strategy is low as effectively. At greatest, the researchers managed to acknowledge solely 50 to 60 % of the supply materials. Lastly, we have to think about that for the sake of the experiment, the researchers tried to simplify their activity as a lot as doable. As an alternative of capturing an actual dialog, they have been taking part in again human speech by means of pc audio system. A cardboard field with a gap was positioned on high of the audio system. This opening was lined with a membrane with the mouse on high of it. This implies the sound supply was not solely synthetic, but additionally situated mere inches from the optical sensor! The authors of the paper tried overlaying the opening with a skinny sheet of paper or cardboard, and the popularity accuracy instantly plummeted to unacceptable ranges of 10–30%. Dependable transmission of vibrations by means of a thick tabletop isn’t even a consideration.
Cautious optimism and safety mannequin
Credit score the place it’s due: the researchers discovered one more assault vector that exploits sudden {hardware} properties — one thing nobody had beforehand considered. For a primary try, the result’s exceptional, and the potential for additional analysis is undoubtedly there. In any case, the U.S. researchers solely used machine studying for sign filtering. The reconstructed audio information was then listened to by human observers. What if neural networks have been additionally used for speech recognition?
In fact, such research have an especially slim sensible utility. For organizations whose safety mannequin should account for even such paranoid situations, the authors of the examine suggest a collection of protecting measures. For one, you possibly can merely ban connecting mice with high-resolution sensors — each by means of organizational insurance policies and, technically, by blocklisting particular fashions. You may also present workers with mousepads that dampen vibrations. The extra related conclusion, nonetheless, considerations safety towards malware: attackers can typically make the most of fully atypical software program options to trigger hurt — on this case, for espionage. So it’s value figuring out and analyzing even such complicated circumstances; in any other case, it could later be not possible to even decide how an information leak occurred.



