Skilled players are effectively conscious of the dangers of downloading video games, mods, skins, and different gaming software program from unofficial sources. Nevertheless, infections also can originate from platforms customers sometimes belief — developer web sites and official shops.
On this publish, we evaluate a number of instances the place attackers distributed malware via official gaming assets. We additionally clarify easy methods to defend your system, loot, and account — so you may hold enjoying in your favourite platforms with none nasty surprises.
Contaminated Endgame Gear mouse-configuration device
In July 2025, Endgame Gear, a producer of superior mice geared toward esports gamers and seasoned players, reported a malware an infection in its OP1w 4k v2 mouse-config utility. The Trojan remained on the corporate’s official website for nearly two weeks, from June 26 to July 9, 2025.
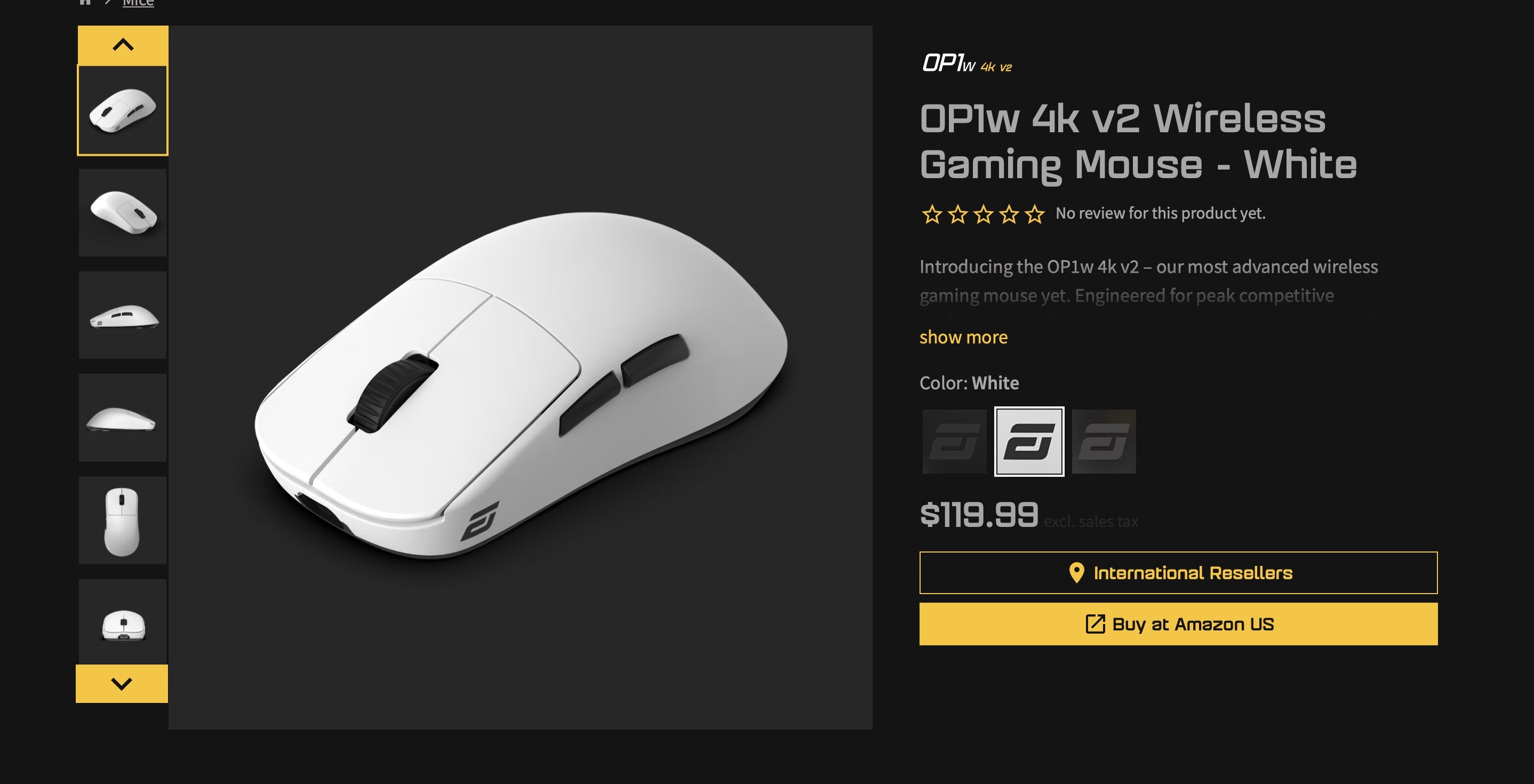
The official web page for the Endgame Gear OP1w 4k v2 mouse hosted a malware-infected setup device. Supply
Because of this, customers who downloaded the utility from the product web page throughout that interval additionally obtained malware with it. Endgame Gear didn’t specify what the malicious payload was, however user-scan knowledge suggests it was an XRed backdoor.
XRed provides a variety of capabilities for distant management of contaminated techniques. These embrace a keylogger and permits attackers to entry the command line, browse disks and folders, obtain and delete information, and take screenshots. XRed also can obtain further modules and exfiltrate system knowledge to distant servers.
It was players themselves who first observed one thing was incorrect with the OP1w 4k v2 configuration device. They started discussing suspicious indicators on Reddit practically two weeks earlier than Endgame Gear launched an official assertion. The important thing particulars that raised consumer suspicions had been the scale of this system — the contaminated model was 2.8MB as an alternative of the standard 2.3MB — and the file signature, listed as “Synaptics Pointing System Driver” as an alternative of “Endgame Gear OP1w 4k v2 Configuration Instrument”.
In its official assertion on the incident, Endgame Gear clarified that customers who downloaded the device from the final downloads web page (endgamegear.com/downloads), GitHub, or the corporate’s Discord channel are secure. The risk solely affected players who downloaded software program instantly from the OP1w 4k v2 product web page between June 26 and July 9, 2025. After that, the malware was faraway from the corporate’s website.
The mouse producer recommends the next steps for any probably affected customers:
- Delete all contents of the folder C:ProgramDataSynaptics.
- Run a full system scan with a dependable antivirus.
- Obtain a clear model of the utility.
As well as, customers ought to change passwords for all necessary accounts, together with monetary providers, electronic mail, and work-related logins.
Malware in three early-access Steam video games
In 2025, a number of instances had been reported of malware being distributed via early-access video games on Steam.
- In February, this concerned PirateFi, a survival sim (we lined this case on the Kaspersky Day by day weblog).
- In March, the same incident occurred with the tactical shooter Sniper: Phantom’s Decision.
- In July, attackers uploaded an contaminated model of Chemia, one other survival sport.
All three instances concerned early-access titles — doubtless as a result of Steam applies looser verification procedures for pre-release video games. Let’s take a more in-depth take a look at these three instances.
A number of days after the beta launch of PirateFi — the primary sport developed by a studio known as Seaworth Interactive — one consumer reported on a Steam discussion board that his antivirus had prevented the sport from launching. The safety software program detected the presence of Trojan.Win32.Lazzzy.gen malware, which the sport tried to put in within the AppData/Temp listing after launch.
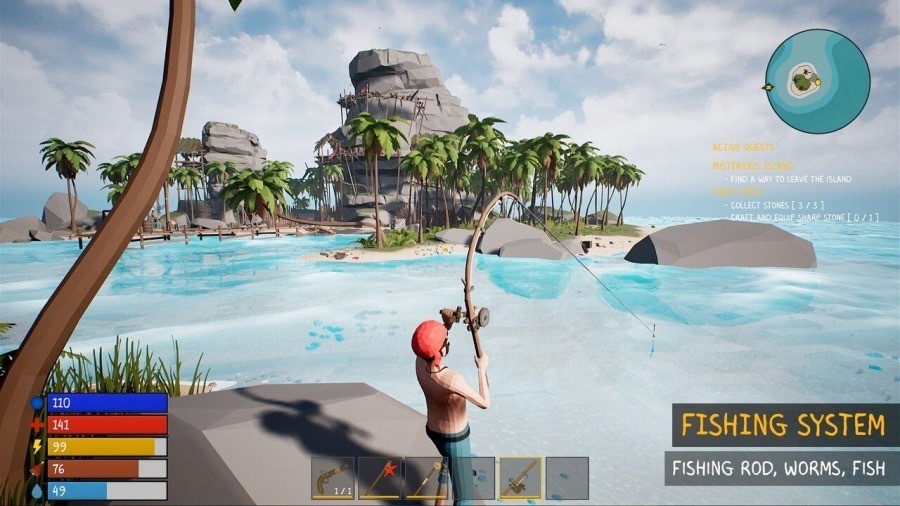
PirateFi promised gamers a pirate-themed survival sim, however in actuality it stole browser cookies to hijack accounts. Supply
The Trojan’s main aim was to steal browser cookies. These cookies allowed the attackers to entry victims’ accounts for monetary providers, social networks, and different on-line platforms. A number of gamers who downloaded and ran the sport reported that the criminals modified the passwords on their accounts and stole funds. PirateFi was pulled from Steam simply 4 days after launch. All customers who had downloaded the sport — fortuitously, solely round 800 folks — obtained an official notification from the platform warning them of the malware on their units.
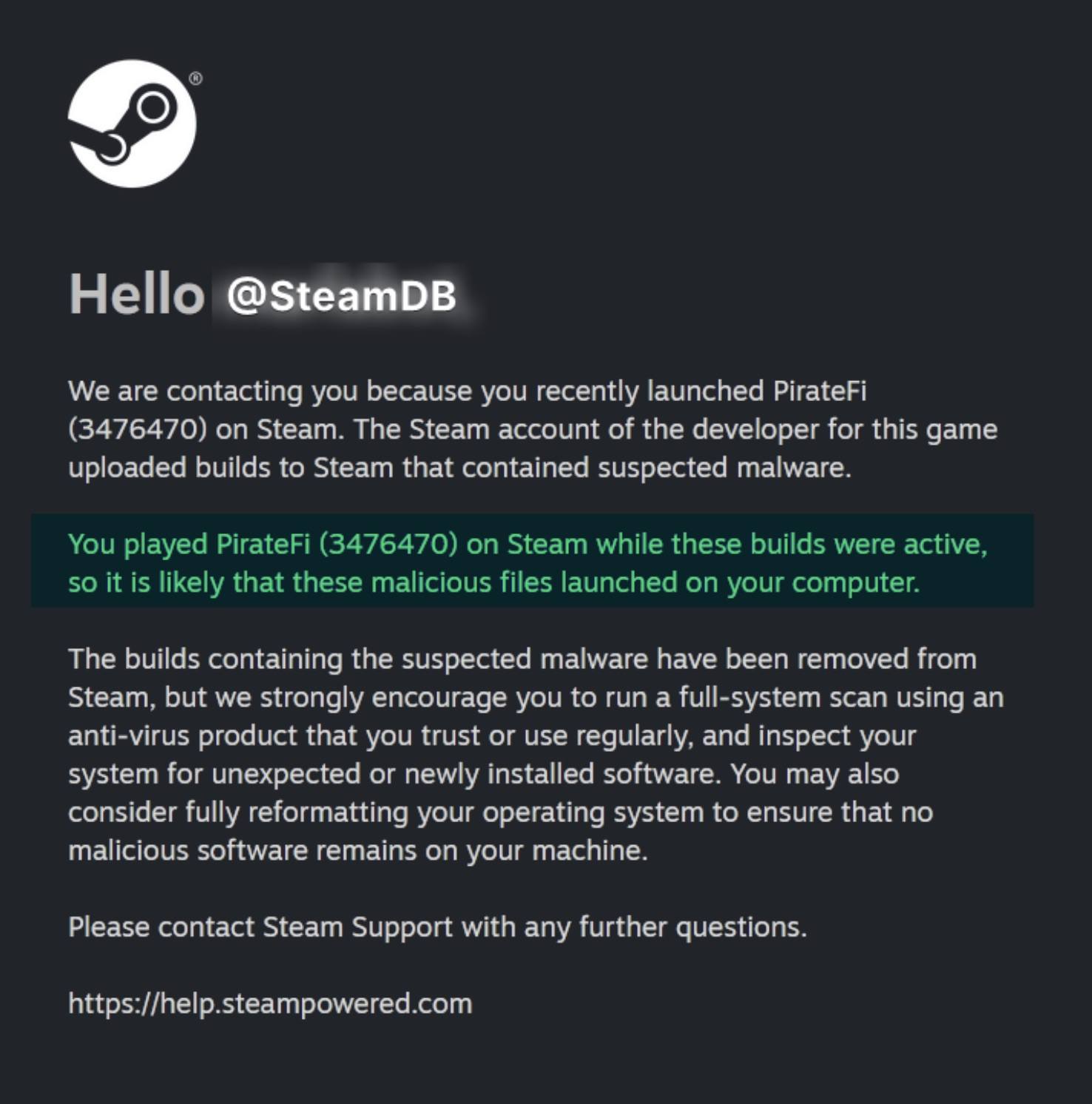
Steam customers who downloaded the contaminated PirateFi sport had been warned of malware on their units. Supply
Only a month later, the same state of affairs occurred with one other sport — Sniper: Phantom’s Decision by Sierra Six Studios. As soon as once more, gamers had been the primary to suspect one thing was incorrect: they observed that the sport’s description and screenshots had been clearly copied from different initiatives. One other pink flag was the developer’s providing a demo installer hosted on an exterior GitHub repository moderately than via Steam.
Additional examination of the installer’s code by Reddit customers revealed suspicious software program hidden inside. Just like the creators of PirateFi, these behind Sniper: Phantom’s Decision gave the impression to be after victims’ on-line accounts. Following consumer studies, each GitHub and Steam rapidly eliminated the malicious sport from their platforms.
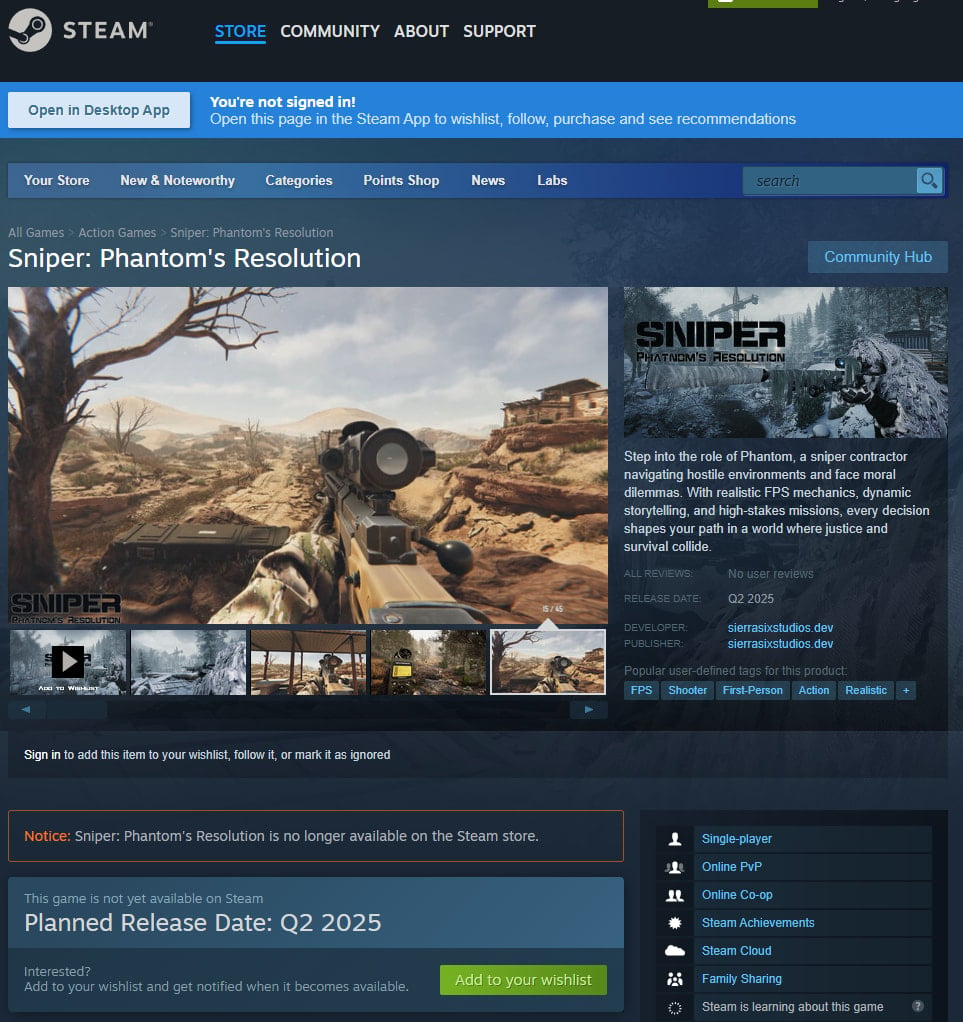
The sport Sniper: Phantom’s Decision was revealed on Steam with an installer containing malware, and was eliminated after consumer complaints. Supply
The third case, involving a sport known as Chemia by Aether Forge Studios, was somewhat completely different: this time, it was a beta model of a reputable sport that was contaminated. Cybersecurity researchers consider the assault was carried out by the hacker group EncryptHub, often known as Larva-208.
It stays unclear how the attackers managed to inject malware into the sport. Nevertheless, gamers who launched the Chemia playtest unknowingly downloaded two infostealers to their units. Each ran silently within the background with out affecting gameplay, leaving players unaware their techniques had been compromised.
The Chemia playtest on Steam was distributed with infostealing malware that ran within the background, extracting knowledge from browsers. Supply
The attackers had been concentrating on knowledge saved in browsers, together with saved passwords, autofill information, cookies, and cryptowallet particulars. On the time of writing, the sport is now not accessible on Steam. Nevertheless, neither the platform nor the sport’s developer has issued an official assertion.
Malicious skins on the official Minecraft web site
Generally risks lurk not simply on Steam, but additionally on builders’ official websites — together with the largest names. In 2018, about fifty thousand Minecraft gamers fell sufferer to attackers who uploaded malicious skins to the official Minecraft web site. That platform has a fan-interaction system the place any participant can share skins they create with others — and that is what the attackers exploited.

The Minecraft skins that might reformat exhausting drives and delete system applications. Supply
The malware was unfold through PNG pores and skin information, and was able to deleting applications, formatting exhausting drives, and destroying backup knowledge. One peculiar element was that some victims obtained weird messages with titles comparable to:
- “You Are Nailed, Purchase A New Laptop This Is A Piece Of Sh*t”,
- “You might have maxed your web utilization for a lifetime”,
- “Your a** received glued.”
The malicious code’s specifics make consultants consider that skilled cybercriminals had been doubtless not behind the assault. Nonetheless, the Minecraft case clearly demonstrated the vulnerability of content-sharing mechanisms on gaming platforms.
Find out how to keep away from turning into a sufferer
Putting in video games, mods, skins, and different gaming software program from official sources is, after all, safer than pirating them from shady ones. Nevertheless, as we have proven on this publish, even reputable websites require vigilance.
- Learn opinions fastidiously earlier than downloading any sport or gaming software program. Do a fast background verify — a easy search would possibly lead you to a Reddit thread discussing suspicious points.
- Be cautious with early-access video games on Steam. Three malicious video games in a single 12 months already indicators a development.
- Set up dependable safety in your system.
Many players could also be skeptical about this final tip, as it is a widespread perception within the gaming group that antivirus software program slows down video games. Which will have been true years in the past, however assessments lately present that the most recent safety options trigger no measurable drops in efficiency.
Furthermore, Kaspersky Premium even features a devoted gaming mode. It activates robotically when a sport launches, suspending database updates, notifications, and routine scans till the session ends — thus minimizing system useful resource utilization.
How else do attackers goal players? Try our number of articles on this matter:



