Info safety has a number of layers of complexity. Efficient but technically easy assaults by way of phishing emails and social engineering are well-known about. We additionally typically submit about subtle focused assaults that exploit vulnerabilities in enterprise software program and providers. And among the many most subtle are assaults that exploit basic {hardware} options. Though such assaults aren’t low-cost, the associated fee doesn’t deter all menace actors. Or a minimum of researchers.
Researchers at two US universities lately printed a paper with a captivating instance of an assault on {hardware}. Utilizing the usual working system characteristic for switching between duties, the researchers developed an assault they named Sleepwalk, which might crack a cutting-edge information encryption algorithm.
Aspect-channeling — sleep-walking
Sleepwalk is a sort of side-channel assault. On this context, “aspect channel” sometimes refers to any technique of stealing secret data by oblique statement. For instance, think about somebody is typing a password on a keyboard. You’ll be able to’t see the letters/symbols, however you possibly can hear the keys being pressed. It is a possible assault during which the sound of the keystrokes — the aspect channel — reveals what textual content is being typed. A basic instance of a aspect channel is monitoring adjustments within the energy consumption of a pc system.
Why does energy consumption range? Easy: completely different computing duties require completely different sources. Critical quantity crunching will max out the load on the CPU and RAM, whereas typing in a textual content editor will see the pc largely idle. In some instances, adjustments in energy consumption give away delicate data, comparable to personal keys for information encryption. That is just like how a couple of barely audible clicks can reveal the proper rotor positions to choose the mix lock on a secure.
Why are these assaults subtle? As a result of a pc performs a number of duties concurrently. And all of them have an effect on energy consumption in a method or one other. Extracting helpful data from this noise is a extremely complicated job. Even when analyzing the best units comparable to sensible card readers, researchers take lots of of hundreds of measurements in a brief interval, repeating them tens or lots of of occasions, then apply subtle signal-processing strategies to substantiate or refute the potential of a side-channel assault. Sleepwalk in a way simplifies this work: the researchers had been capable of extract helpful data by measuring the sample of energy consumption simply as soon as, throughout a so-called context change.
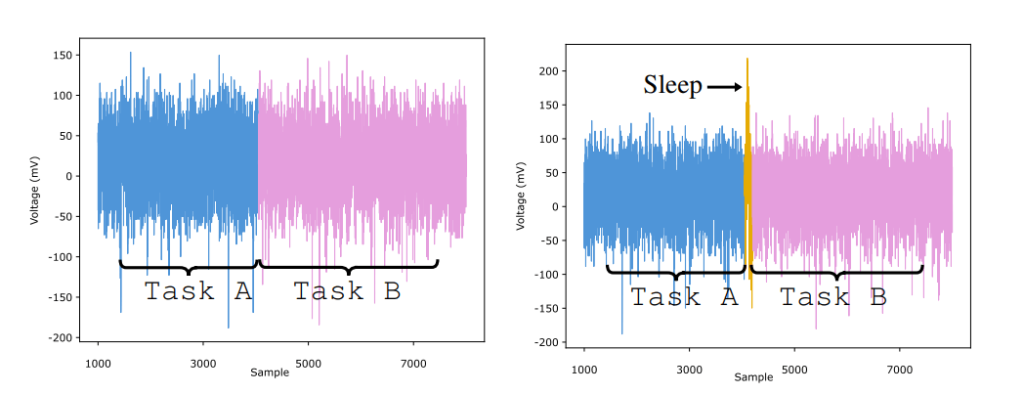
Voltage fluctuations throughout CPU context switching. Supply
Context switching
We’re all used to switching between packages on a pc or smartphone. At a deeper degree, such multitasking is enabled by varied mechanisms behind the scenes, one in all which is context switching. The state of 1 program is saved, whereas information from one other is loaded into the CPU. The choice on which program to present precedence to, and when, is made by the working system. That mentioned, there’s a easy approach for a programmer to power a context change by including a sleep instruction to this system code. The working system then sees that this system doesn’t require CPU energy in the interim, and switches to a different process. Context switching, particularly when the sleep perform known as, is an energy-consuming exercise that requires saving the state of 1 program and loading information from one other into the CPU. The screenshot above exhibits a spike within the measured voltage throughout such a change.
Because it seems, the character of this energy spike is decided each by the duty that was working earlier than and by the info being processed. Primarily, the researchers massively simplified implementing a side-channel assault during which the system’s power consumption is measured. As an alternative of measuring over a protracted interval, a single spike is analyzed at a predetermined time. This serves up oblique information of two sorts: what program was working earlier than the change, and what information was being processed. All that is still is to hold out the assault in response to the scheme under:
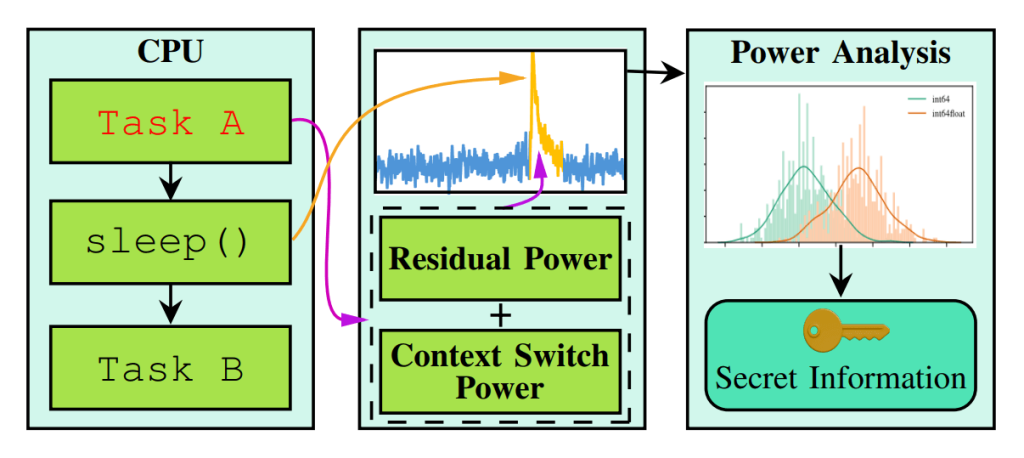
Define of the Sleepwalk assault Supply
Sleepwalk assault in the true world
The researchers did their experiments on a single-board Raspberry Pi 4, demonstrating to start with that the ability spike produced by completely different computing duties throughout context switching has a novel fingerprint. Let’s suppose that this laptop is performing information encryption. We are able to feed any textual content to the encryption algorithm as enter, however we don’t know the important thing for encrypting the info.
What if we set off a context change at a selected level within the encryption algorithm’s operation? The working system will save the state of this system, inflicting a spike in energy consumption. Utilizing an oscilloscope to repeatedly measure the character of this spike, the researchers had been capable of extract the key key!
That was simply one in all many vital issues realized within the experiment. In addition they succeeded in absolutely reconstructing a SIKE personal key. The pretty new encryption algorithm SIKE is proposed as a substitute for conventional algorithms to guard information even within the quantum age. But regardless of its obvious innovativeness, questions are already being requested in regards to the algorithm’s power. Furthermore, to extract the key key, the researchers didn’t simply perform a Sleepwalk assault, but additionally exploited a weak point within the algorithm itself.
The Sleepwalk assault was unable to completely crack the normal and dependable (however not post-quantum) AES-128 algorithm. However the staff was capable of reconstruct 10 of the 16 bytes of the personal key — and this in itself is an achievement since Sleepwalk is considerably less complicated than different side-channel assault strategies.
Certain, there’s no speak but of deploying Sleepwalk in observe. The researchers merely needed to reveal that energy spikes throughout context switching can reveal secret data. Which they did. However unhealthy guys in the future would possibly be capable to develop the assault in order to steal actual secrets and techniques — be they from a pc, safe flash drive, or crypto pockets.
As results of this analysis, current and in-development encryption algorithms ought to develop into a bit extra dependable. Not solely that, the Sleepwalk assault not directly factors up a key facet within the implementation of cryptographic programs. Future algorithms will must be proof against evaluation utilizing quantum computing (so-called “post-quantum cryptography”); however no much less vitally, this may must be executed appropriately. In any other case, a brand new, theoretically safer algorithm might turn into extra susceptible to conventional assaults than a pre-quantum one.



