Your snapshots are, fairly actually, the keys to your non-public life. Your gallery holds your future plans, monetary secrets and techniques, cat photos, and typically even belongings you’d by no means share with anybody. However how usually do you really take into consideration defending these photographs? We hope that ever because you heard in regards to the SparkCat cross-platform stealer, you’ve been pondering it extra usually than normal.
Now we’ve found that Trojan’s little sibling, which we’ve affectionately named SparkKitty. However don’t let the lovable title idiot you — behind it lies a spy that, like its older brother, goals to steal photographs from its victims’ smartphones. What makes this risk distinctive, and why ought to each Android and iPhone customers prick up their ears?
How SparkKitty makes its approach onto gadgets
The stealer spreads in two methods: (i) within the wild — that’s, throughout the untamed elements of the web; and (ii) by official app shops just like the App Retailer and Google Play. Let’s break this down.
Official app shops
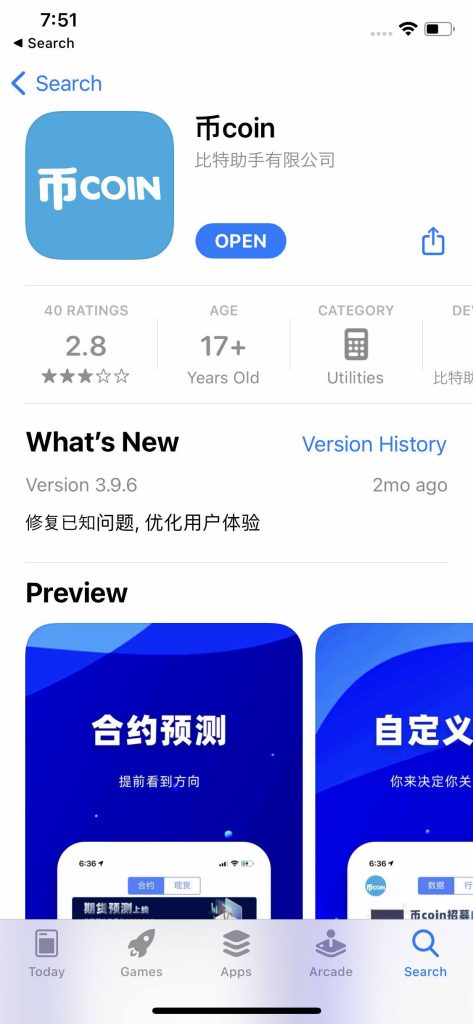
In Apple’s App Retailer, the malware was lurking contained in the 币coin app — designed for monitoring cryptocurrency charges and buying and selling indicators. We’re undecided precisely how this suspicious spy exercise ended up within the app. It’s attainable there was a supply-chain compromise, and the builders themselves weren’t conscious of SparkKitty till we notified them. However there’s additionally a second risk: the builders intentionally embedded the stealer into the app. Regardless, that is the second time we’ve seen a Trojan sneak into the App Retailer, and we’ve alerted Apple about it. SparkCat was the primary occasion.
It’s a special story with Google Play: malicious apps pop up regularly, and we often cowl these threats on Kaspersky Every day. This time, we detected malicious exercise in a messaging app that features crypto-exchange options. This can be a well-liked app that’s been put in greater than 10 000 instances, and was nonetheless accessible within the retailer on the time of the research. We’ve contacted Google to warn them in regards to the risk.
Suspicious hyperlinks within the wild
That mentioned, the attackers have been way more inventive this time in spreading the malware out within the wild. As soon as, throughout a routine evaluate of suspicious hyperlinks (we click on them so that you don’t must!) our specialists uncovered a number of related pages distributing a TikTok mod for Android. One of many primary issues this mod did was name extra code. “That appears suspicious”, we thought. And we had been proper. The code contained hyperlinks displayed as buttons inside the app, all directing customers to a web-based retailer referred to as TikToki Mall, which bought a wide range of objects. Sadly, we couldn’t decide if the shop was reliable or only a large entice — however one attention-grabbing reality stood out: TikToki Mall accepts cryptocurrency funds, and also you want an invite code to enroll and pay for any merchandise. We didn’t discover any additional suspicious exercise at this stage, and no traces of SparkKitty or different malware.
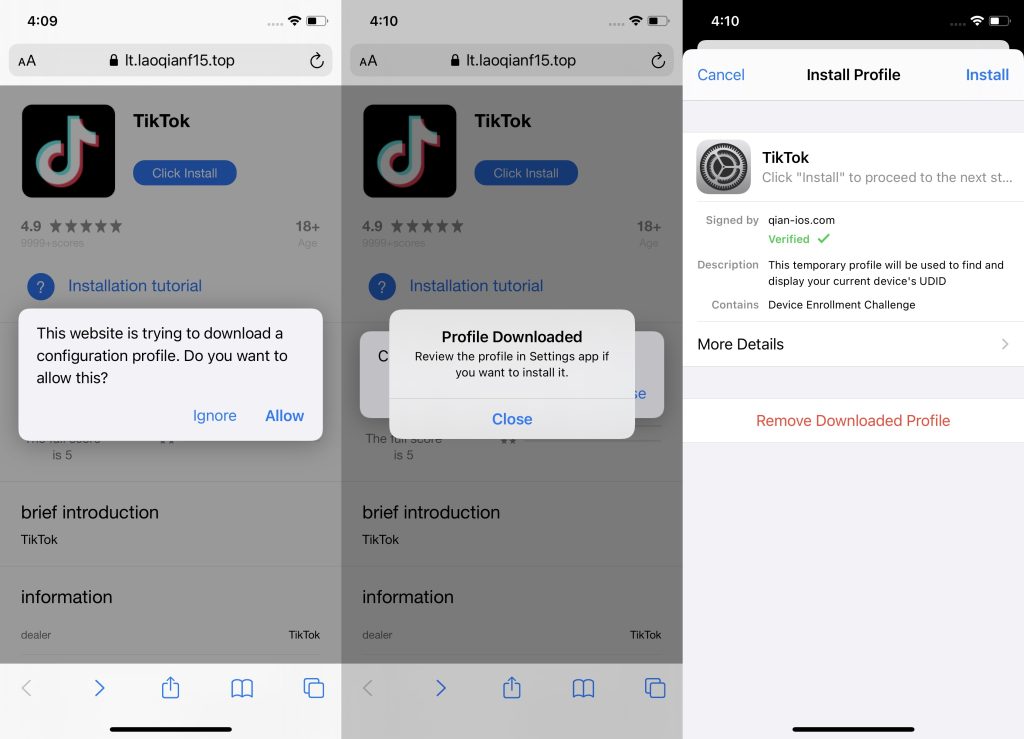
So we determined to take a special method and see what occurred after we tapped these identical suspicious hyperlinks from an iPhone. This led us to a web page that vaguely resembled the App Retailer, which instantly prompted us to obtain the “TikTok app”.
iOS doesn’t enable customers to obtain and run purposes from third-party sources. Nonetheless, Apple supplies so-called provisioning profiles to each member of the Apple Developer Program. These enable putting in customized purposes not accessible within the App Retailer on consumer gadgets, similar to beta variations or apps developed for inside company use. Attackers exploit these profiles to distribute apps that comprise malware.
The set up course of differed barely from the same old process. Sometimes, within the App Retailer, you solely have to faucet Set up as soon as, however on this case, putting in the pretend TikTok required extra steps: downloading and putting in a developer provisioning profile.
Naturally, this model of TikTok didn’t have any humorous movies; it was simply one other retailer, much like the Android model. Whereas seemingly innocent, the iOS model requested entry to the consumer’s gallery each time it launched — and that was the catch. This led us to find a malicious module that despatched photographs from the contaminated cellphone’s gallery, together with machine info, to the attackers. We additionally discovered its traces in different Android purposes. For the technical particulars of the story, take a look at our full report on Securelist.
Who’s in danger?
Our knowledge reveals that this marketing campaign primarily targets customers in Southeast Asia and China. That doesn’t imply, nonetheless, that different international locations are past the attain of SparkKitty’s claws. The malware has been spreading since no less than early 2024, and over the previous 12 months and a half attackers have seemingly thought-about upscaling their operation to different international locations and continents. There’s nothing stopping them. What’s extra, it’s not simply the TikTok mod it is best to fear about; we’ve additionally discovered malicious exercise inside numerous playing and grownup video games, and even crypto-related apps.
When you assume these attackers are simply inquisitive about admiring your trip photographs, assume once more. SparkKitty uploads every one in every of your snapshots to its command-and-control server. These photographs might simply embrace screenshots of delicate info like crypto pockets seed phrases, permitting these unhealthy actors to steal your cryptocurrency.
Find out how to shield your self from SparkKitty
This Trojan spreads in some ways, and defending your self from each single one is a troublesome problem. Whereas the golden rule of “obtain apps from official sources solely” nonetheless applies, we’ve discovered traces of this stealer in each Google Play and the App Retailer — locations the place apps are supposedly vetted and 100% protected. So what are you able to do about that?
We suggest specializing in securing your smartphone’s gallery. Naturally, probably the most foolproof methodology could be to by no means take photographs or screenshots of delicate info, however that’s just about unattainable these days. There’s an answer: retailer beneficial photographs in a safe vault. With Kaspersky Password Supervisor, you may solely view and ship protected, essential photographs after coming into the primary password, which solely you already know. Word that the protected content material just isn’t confined to only one machine. The password supervisor can sync info between smartphones and computer systems. This consists of bank-card knowledge, two-factor authentication tokens, and anything you select to retailer in Kaspersky Password Supervisor – together with your photographs.
It’s additionally essential to examine your smartphone proper now for any of the contaminated apps we’ve found; the prolonged record is accessible on Securelist. For Android, Kaspersky for Android may also help with this — it’ll discover and take away malware for you. On iPhone, because of the closed structure of iOS, our safety resolution can’t scan for and delete beforehand put in contaminated apps, however it’s going to stop any makes an attempt to ship knowledge to the attackers’ servers and warn you about them.
And should you go for a Kaspersky Premium or Kaspersky Plus subscription, you get Kaspersky Password Supervisor alongside together with your safety resolution.
Comply with our Telegram channel to remain updated on the most recent cyberthreats, and be sure to’re storing your photographs safely.
Study different malware you want to be careful for to maintain your smartphone protected: