Uncover how cybercriminals are utilizing pretend on-line kinds to steal private information. Learn the way phishing scams mimic trusted manufacturers and how one can defend your self.
On-line threats have develop into more and more subtle, and phishing assaults aren’t any exception. Among the many many techniques cybercriminals deploy, growing phishing campaigns by mimicking well-known corporations and duplicating their on-line kinds has emerged as a fast, cost-effective, and deceptively easy technique for stealing delicate person data. The alarming rise within the success of those campaigns, uncovered within the Q1 Gen Menace Report, speaks volumes about how cybercriminals are exploiting weaknesses in each know-how and human belief. This text explores how these assaults work, why they’re so efficient, and what you are able to do to guard your self.
Understanding phishing via on-line kinds
Phishing preys on the very human – and sometimes important – trait of belief. These assaults lure customers into offering private data by mimicking legit, and trusted, web sites or companies. Phishing via on-line kinds takes benefit of instruments like web site builders and dynamic DNS (DDNS) companies to create pretend login or information submission pages that seem real.
An unsuspecting person would possibly click on on a hyperlink in an e mail, claiming their account has been blocked or urging instant motion to keep away from service interruption. These emails direct customers to counterfeit kinds that ask for login particulars, fee data, or different delicate private information.
As soon as the sufferer enters their data, it’s collected by the attacker and used for functions similar to identification theft, monetary fraud, and even additional cyberattacks.
How attackers exploit on-line web site builders
On-line web site builders, like Weebly and Wix, are common instruments for creating web sites with out coding abilities. Their accessibility and user-friendly drag-and-drop interfaces make them interesting not solely to legit customers but additionally to cybercriminals.
Phishers exploit such legit platforms as a result of they provide benefits like trusted internet hosting domains and customizable subdomains. These components make phishing pages more durable to detect and permit them to bypass e mail spam filters or antivirus software program.
Attackers usually create subdomains that mimic well-known manufacturers to look extra legit. Frequent examples embrace:
- updatefacebookmeta[.]weebly[.]com
- outlookauthenticationmicrosoft[.]weebly[.]com
- myfmsbank[.]weebly[.]com
These URLs would possibly look legit at a look, particularly to somebody who’s busy or unfamiliar with recognizing phishing makes an attempt.
Past web site builders, attackers are more and more utilizing dynamic DNS (DDNS) companies and subdomain suppliers like DuckDNS. These companies permit the creation of subdomains that mimic main corporations in an try and deceive customers. By leveraging DDNS, attackers add flexibility to their campaigns, making it simpler to scale operations with minimal effort.
Why these pages are deceptively efficient
Some phishing pages are shockingly subtle, intently mimicking the legit login types of main corporations or establishments. Others are poorly constructed, with crimson flags like inconsistent layouts, mismatched fonts, or seen passwords. Nonetheless, even low-effort phishing pages can succeed as a result of they’re usually hosted on trusted domains, making them more durable for filters to detect.
Frequent warning indicators
Listed below are just a few indicators of a phishing web page to be careful for, even when hosted on trusted platforms:
- Mismatched or unprofessional design
- Login pages that don’t masks passwords
- Irrelevant or suspicious menu objects
- Subdomain names that appear odd or include typos
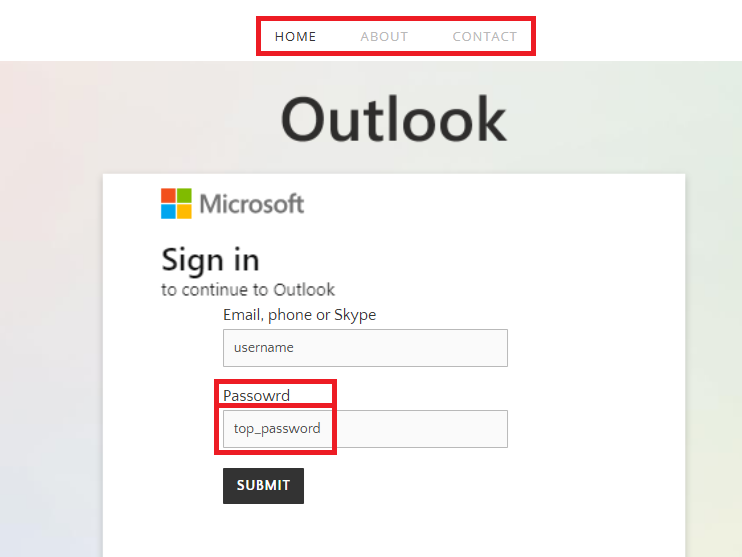
Instance of an apparent phishing web page, exhibiting frequent warning indicators
Defending your self from phishing assaults
Whereas phishing campaigns have gotten more durable to detect, there are clear steps you may take to guard your self and your private information:
- Study URLs fastidiously: Test subdomains and domains for typos or irrelevant components. A login web page hosted on one thing like “weebly.com” is a significant crimson flag.
- Allow two-factor authentication (2FA): Even when your credentials are compromised, 2FA provides a further layer of safety, stopping attackers from accessing accounts.
- Search for safe indicators: Be certain that the web site shows a padlock icon within the deal with bar and that the URL begins with “https.” Nonetheless, keep in mind that even safe connections don’t assure legitimacy.
- Be cautious with pressing emails: Most phishing emails depend on urgency to trick unsuspecting victims. Suppose twice earlier than clicking hyperlinks in emails that demand instant motion.
- Use dependable antivirus and anti-phishing instruments: Safety software program with up to date phishing detection capabilities might help establish malicious hyperlinks earlier than you fall sufferer.
- Report suspicious pages: In the event you come throughout a phishing web page, report it to the internet hosting platform or safety organizations.
Staying forward of rising threats
The underside line is that phishing campaigns leveraging on-line kinds will probably stay a well-liked tactic for cybercriminals on account of their pace, affordability, and effectiveness. Nonetheless, elevated consciousness, mixed with smarter safety measures, might help mitigate these threats and hold customers secure on-line.
Each person holds the facility to disrupt the success charge of phishing scams. By staying vigilant and knowledgeable, we are able to collectively make it more durable for attackers to take advantage of belief in an more and more digital world.
[ad_2]
Supply hyperlink


