For an e mail assault to succeed, the very first thing cybercriminals must do is get their messages in entrance of potential victims. In a latest submit, we coated how scammers leveraged notifications from GetShared — a totally authentic service for sharing giant information. At this time, we look at one other technique for delivering malicious emails. The operators behind this rip-off have discovered to insert customized textual content into real thank-you messages despatched by Microsoft 365 to its new enterprise subscribers.
A real Microsoft e mail with a nasty shock inside
The assault kicks off with a authentic e mail wherein Microsoft thanks the recipient for buying a Microsoft 365 Apps for Enterprise subscription. The e-mail does, in actual fact, arrive from the Redmond tech large’s authentic deal with: microsoft-noreply@microsoft.com. One could be hard-pressed to think about an e mail deal with with a extra trusted repute, so the message simply will get previous any e mail server filters.
Another time, simply so we’re clear: that is an honest-to-goodness e mail from Microsoft. The contents match a typical buy affirmation. Within the screenshot beneath, the corporate thanks the recipient for purchasing 55 Microsoft 365 Apps for Enterprise subscriptions price a complete of $587.95.
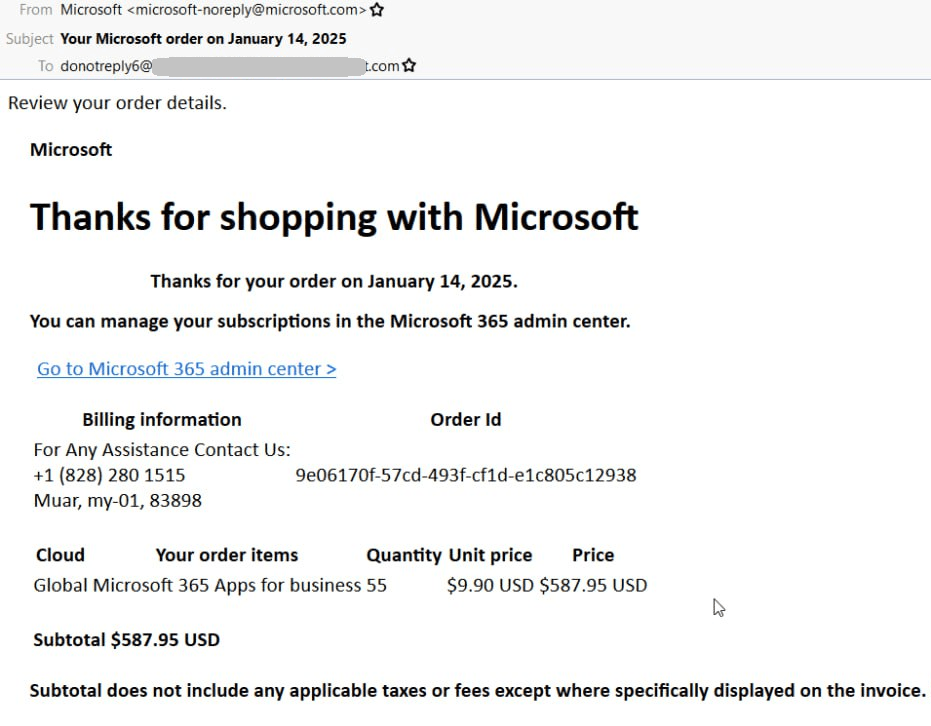
Instance of a Microsoft enterprise notification the place attackers inserted their message within the Billing info part
The crux of the rip-off lies within the textual content attackers add to the Billing info part. Sometimes, this part comprises the subscriber firm’s title and the billing deal with. Nevertheless, the scammers swap out that info for their very own cellphone quantity, plus a observe encouraging the recipient to name “Microsoft” in the event that they want any help. The varieties of “bought” subscriptions counsel that the scammers are concentrating on firm staff.
They prey on a standard worker concern: making an costly, pointless buy might trigger hassle at work. And since resolving the difficulty by e mail isn’t an possibility (the message comes from a no-reply deal with), the sufferer is left with little selection however to name the cellphone quantity supplied.
Who solutions the calls, and what occurs subsequent?
If the sufferer takes the bait and decides to name to inquire concerning the subscriptions they’ve supposedly bought, the scammers deploy social engineering methods.
A Reddit consumer, who’d obtained an analogous e mail and known as the quantity, shared their expertise. In line with the sufferer, the one that answered the decision insisted on putting in some help software program, and despatched an EXE file. The following dialog means that the file contained a RAT of some sort.
The sufferer didn’t suspect something was amiss till the scammer promised to refund cash to their checking account. That was a purple flag, as they shouldn’t have had entry to the sufferer’s banking particulars. The scammer went on to ask the sufferer to register to their on-line banking to test if the transaction had gone by.
The sufferer believes that the software program put in on their laptop was malware that will have allowed the attackers to intercept their login credentials. Fortuitously, they acknowledged the hazard early sufficient and hung up. Inside the similar thread, different Reddit customers reported related emails containing varied contact particulars.
How scammers ship phishing emails from a real Microsoft deal with
How, precisely, the attackers handle to ship Microsoft notifications to their victims remains to be one thing of a thriller. Probably the most believable clarification got here from one other Reddit consumer, who prompt that the rip-off operators had been utilizing stolen credentials or trial variations to entry Microsoft 365. By utilizing BCC or just getting into the sufferer’s e mail deal with when buying a subscription, they will ship messages just like the one proven within the screenshot above.
An alternate idea is that the scammers achieve entry to an account with an energetic Microsoft 365 subscription after which use the billing-information resend characteristic — specifying the goal consumer because the recipient.
Whichever is true, the attackers’ purpose is to interchange the billing info — the one a part of the Microsoft notification they will alter — with their very own cellphone quantity.
Tips on how to shield your self towards such assaults
Malicious actors hold discovering new loopholes in well-known, completely authentic companies to make use of for phishing campaigns and scams. That’s why, to maintain a corporation safe, you needn’t solely technical protections but in addition administrative controls. Right here’s what we suggest:


