In early 2025, the Chinese language chatbot, DeepSeek, burst onto the AI scene. It provoked a lot remark and controversy throughout the globe: we may hardly miss out on the similarity of its emblem to our personal, comparisons with ChatGPT had been plentiful, and in Italy, South Korea, Australia, and different nations, DeepSeek was blocked altogether. The hype was — and stays — intense, together with amongst cybercriminals.
We’ve found a number of teams of web sites mimicking the official chatbot web site and distributing malicious code beneath the guise of what seems to be a authentic shopper. To seek out out precisely how these cybervillains function, and the way to use AI safely, learn on…
Malicious scripts and geofencing
A number of malware distribution schemes had been detected, all of which had the usage of faux DeepSeek web sites because the widespread denominator. The distinction lies in what was distributed by way of these websites and the way. This publish totally explores one among these schemes; for particulars on the others, see our full report on Securelist.
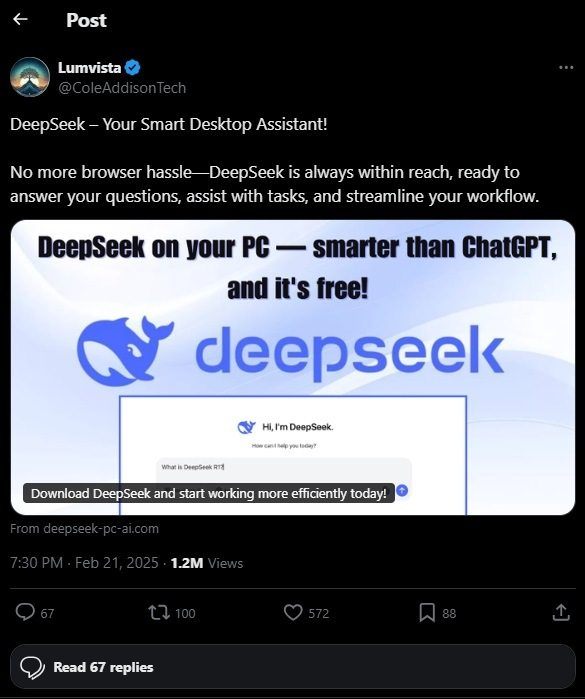
What would you assume when you landed on a web site with the area deepseek-pc-ai[.]com or deepseek-ai-soft[.]com? You’d in all probability assume you may discover there some DeepSeek-related software program. And what sort of software program may that be? A DeepSeek shopper, in fact! And certainly, you’ll shortly see the brilliant Obtain and barely duller Begin Now buttons that greet guests to the location.
Whichever of those buttons you click on, an installer begins downloading. However there’s a catch: as soon as initiated, as an alternative of putting in DeepSeek, the installer accesses malicious URLs, and manipulates scripts to activate the SSH service in Home windows to configure it to work with the attackers’ keys. This permits them to remotely hook up with the sufferer’s laptop, who doesn’t even get a DeepSeek Home windows shopper as comfort… which, by the best way, doesn’t exist.
Apparently, the faux websites use geofencing — limiting entry primarily based on the area of the IP handle. For instance, customers from Russia on these domains noticed a easy stub web site with empty texts about DeepSeek — most certainly generated by DeepSeek itself or a special massive language mannequin. Guests from different nations, nevertheless, had been taken to the malicious web site distributing the faux shopper.
1,000,000 views on X
The principle vector for distributing hyperlinks to the malicious URLs was posts on the social community X (previously Twitter). One of the vital widespread posts (now deleted) was revealed from the account of Australian startup Lumina Vista, which, open sources say, has not more than 10 workers. The corporate’s account itself is in its infancy: it solely bought the coveted blue check-mark in February 2025, and boasts only a dozen posts and fewer than 100 subscribers. But the publish selling the faux DeepSeek web site garnered 1.2 million views and greater than 100 reposts. Bit fishy? We investigated the accounts that reposted it and concluded that they may very well be bots, since all use the identical naming conference and identifiers within the bio part. By the way, it’s fairly doable that Lumina Vista’s account was merely hacked and used for paid promotion of the attackers’ advert publish.
Within the feedback, some customers identified that the hyperlink results in a malicious web site, however they had been within the minority — the remaining had been merely expressing views about DeepSeek, Grok, and ChatGPT. Nevertheless, not one of the commenters famous the apparent: DeepSeek has no native shopper for Home windows, and you may solely entry it in a browser. It’s also possible to run DeepSeek domestically however that requires specialised software program.
Tips on how to use AI safely
At current, it’s not simple to evaluate the dimensions of this and different malicious schemes involving faux DeepSeek pages. However one factor is for sure: these campaigns are large and never focused at particular customers. But they’re growing in a short time: quickly after the announcement of Grok-3, attackers started providing to obtain its shopper each from the area v3-grok[.]com, and from… v3-deepseek[.]com! Certainly, Grok, DeepSeek – what’s the distinction?…
With out dependable safety, any AI fanatic is in danger. That’s why it’s important to comply with the security guidelines and suggestions when utilizing AI.
- Examine the URLs of internet sites you go to. Particularly when it’s one thing new, widespread, and simple to spoof.
- Filter delicate knowledge. Keep in mind that what you write to a chatbot may very well be used towards you: as with different cloud providers, knowledge can leak as a result of safety flaws or account hacking.
- Defend your gadgets. Take a look at the critiques and select the finest resolution for you that may spot phishing websites and guard towards downloading malware.
- Restrict the usage of third-party plugins. Each add-on app creates new threats. Particular monitoring is required for execution plug-ins that may, for instance, run malicious code to purchase a airplane ticket at your expense.
Should you’re significantly interested by neural networks and need to discover ways to use them safely, take a look at these posts: