Your smartphone gallery might include photographs and screenshots of essential info you retain there for security or comfort, comparable to paperwork, financial institution agreements, or seed phrases for recovering cryptocurrency wallets. All of this information will be stolen by a malicious app such because the SparkCat stealer we’ve found. This malware is presently configured to steal crypto pockets information, but it surely might simply be repurposed to steal every other helpful info.
The worst half is that this malware has made its approach into official app shops, with virtually 250,000 downloads of contaminated apps from Google Play alone. Though malicious apps have been present in Google Play earlier than, this marks the primary time a stealer Trojan has been detected within the App Retailer. How does this risk work and what are you able to do to guard your self?
Malicious add-ons to reputable apps
Apps containing SparkCat’s malicious parts fall into two classes. Some, comparable to quite a few related messenger apps claiming AI performance, all from the identical developer, had been clearly designed as bait. Some others are reputable apps: meals supply providers, information readers, and crypto pockets utilities. We don’t but understand how the Trojan performance bought into these apps. It might have been the results of a provide chain assault, the place a third-party part used within the app was contaminated. Alternatively, the builders might have intentionally embedded the Trojan into their apps.

The primary app the place we detected SparkCat was a meals supply service known as ComeCome, accessible within the UAE and Indonesia. The contaminated app was discovered on each Google Play and the App Retailer
The stealer analyzes photographs within the smartphone’s gallery, and to that finish, all contaminated apps request permission to entry it. In lots of instances, this request appears fully reputable — for instance, the meals supply app ComeCome requested entry for a buyer assist chat proper upon opening this chat, which seemed fully pure. Different functions request gallery entry when launching their core performance, which nonetheless appears innocent. In any case, you do need to have the ability to share photographs in a messenger, proper?
Nonetheless, as quickly because the person grants entry to particular photographs or your entire gallery, the malware begins going by all of the photographs it might attain, looking for something helpful.
AI-powered theft
To seek out crypto-wallet information amongst photographs of cats and sunsets, the Trojan has a built-in optical character recognition (OCR) module based mostly on the Google ML Equipment — a common machine-learning library.
Relying on the system’s language settings, SparkCat downloads fashions educated to detect the related script in photographs, whether or not Latin, Korean, Chinese language, or Japanese. After recognizing the textual content in a picture, the Trojan checks it in opposition to a algorithm loaded from its command-and-control server. Along with key phrases from the checklist (for instance, “Mnemonic”), the filter will be triggered by particular patterns comparable to meaningless letter combos in backup codes or sure phrase sequences in seed phrases.
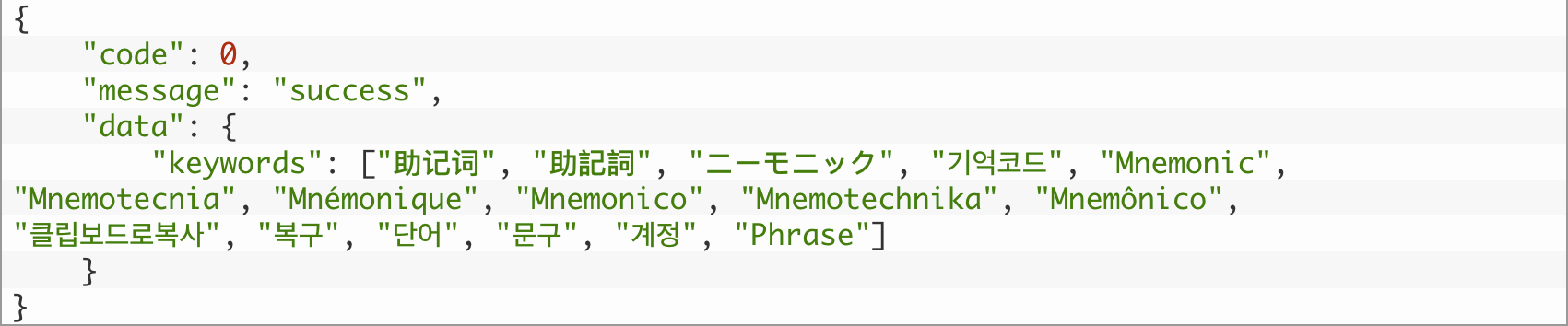
Throughout our evaluation, we requested an inventory of key phrases used for OCR looking from the Trojan’s C2 servers. The cybercriminals are clearly desirous about phrases used to recuperate entry to crypto wallets — referred to as mnemonics
The Trojan uploads all photographs containing doubtlessly helpful textual content to the attackers’ servers, together with detailed details about the acknowledged textual content and the system the picture was stolen from.
Scale and victims of the assault
We recognized 10 malicious apps in Google Play, and 11 within the App Retailer. On the time of publication, all malicious apps had been faraway from the shops. The full variety of downloads from Google Play alone exceeded 242,000 on the time of research, and our telemetry information means that the identical malware was accessible from different websites and unofficial app shops, too.

Among the many contaminated apps are well-liked supply providers and AI-powered messengers in each Google Play and the App Retailer
Judging by SparkCat’s dictionaries, it’s “educated” to steal information from customers in lots of European and Asian international locations, and proof signifies that assaults have been ongoing since at the least March 2024. The authors of this malware are seemingly fluent in Chinese language — extra particulars on this, in addition to the technical facets of SparkCat, will be discovered within the full report on Securelist.
How you can shield your self from OCR Trojans
Sadly, the age-old recommendation of “solely obtain highly-rated apps from official app shops” is a silver bullet not — even the App Retailer has now been infiltrated by a real infostealer, and related incidents have occurred repeatedly in Google Play. Subsequently, we have to strengthen the standards right here: solely obtain highly-rated apps with hundreds, or higher nonetheless, thousands and thousands of downloads, printed at the least a number of months in the past. Additionally, confirm app hyperlinks in official sources (such because the builders’ web site) to make sure they’re not faux, and browse the critiques — particularly detrimental ones. And, after all, you should definitely set up a complete safety system on all of your smartphones and computer systems.
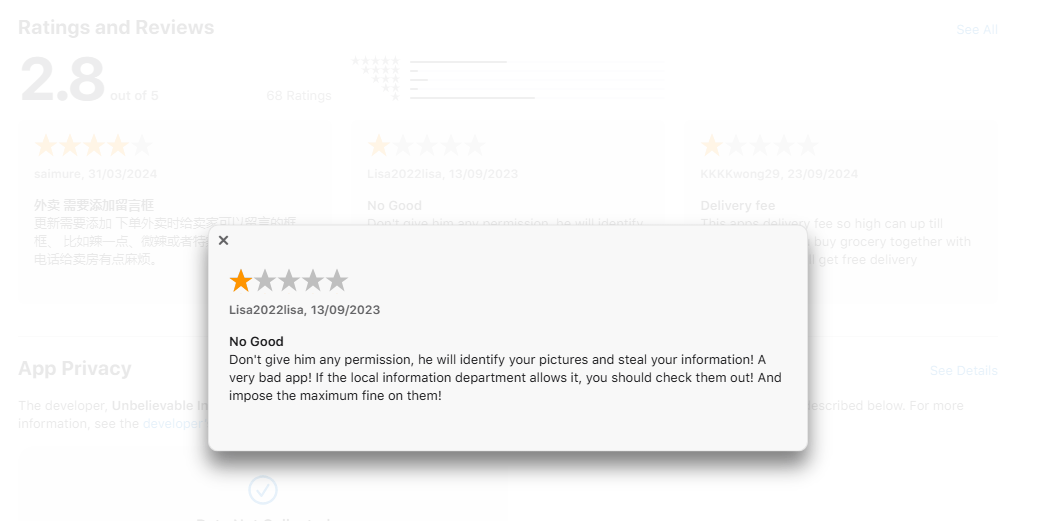
Checking detrimental critiques of the ComeCome app within the App Retailer might have put customers off downloading it
You must also be extraordinarily cautious about granting permissions to new apps. Beforehand, this was primarily a priority for “Accessibility” settings, however now we see that even granting gallery entry can result in the theft of non-public information. For those who’re not fully positive about an app’s legitimacy (for instance, it’s not an official messenger, however a modified model), don’t grant it full entry to all of your photographs and movies. Grant entry solely to particular photographs when mandatory.
Storing paperwork, passwords, banking information, or photographs of seed phrases in your smartphone’s gallery is extremely unsafe — in addition to stealers comparable to SparkCat, there’s additionally at all times the danger that somebody peeks on the photographs, otherwise you by chance add them to a messenger or file-sharing service. Such info ought to be saved in a devoted utility. For instance, Kaspersky Password Supervisor lets you securely retailer and sync not solely passwords and two-factor authentication tokens but additionally banking card particulars and scanned paperwork throughout all of your units — all in encrypted kind. By the way in which, this app comes with our Kaspersky Plus and Kaspersky Premium subscriptions.
Lastly, in the event you’ve already put in an contaminated utility (the checklist of them is on the market on the finish of the Securelist put up), delete it and don’t use it till the developer releases a set model. In the meantime, rigorously evaluation your picture gallery to evaluate what information the cybercriminals might have obtained. Change any passwords and block any playing cards saved within the gallery. Though the model of SparkCat we found hunts for seed phrases particularly, it’s potential that the Trojan could possibly be reconfigured to steal different info. As for crypto-wallet seed phrases, as soon as created, they will’t be modified. Create a brand new crypto pockets, and switch all of your funds from — after which abandon fully — the compromised one.



